Compromised credentials stand as the predominant cause of data breaches, underscoring the urgency for organizations to bolster their defenses. It’s crucial to acknowledge that, often, the only barrier separating an attacker from an organization’s most precious resources is the strength and security of its passwords. These compromised passwords not only pose a security risk but also jeopardize regulatory compliance, leading to potential operational and reputational damage.
Enzoic for Active Directory addresses this pressing issue head-on. It enhances initial and ongoing password security to meet compliance standards like NIST 800-63b, thereby mitigating risks and elevating an organization’s overall security stance. This solution review explores how Enzoic serves as a foundational tool for organizations, focusing on an often-underestimated vector of cyber vulnerability.
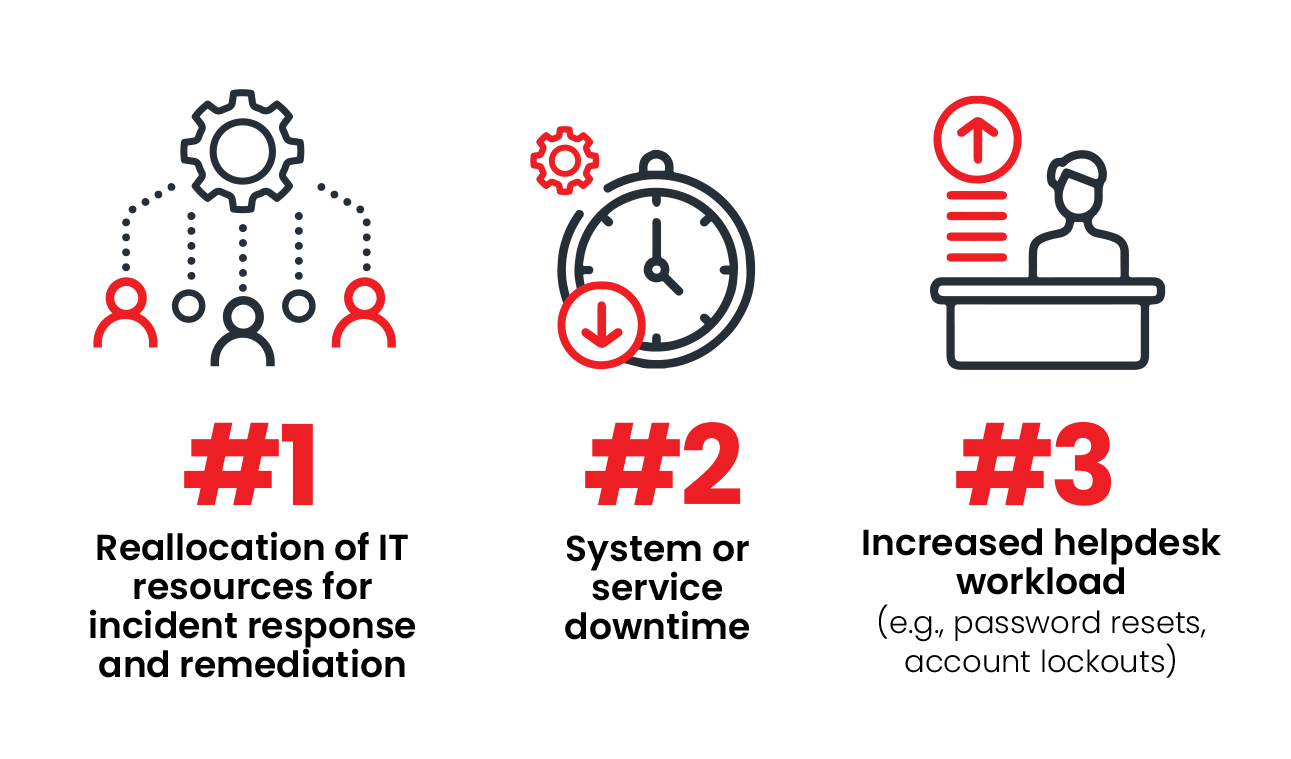
What negative consequences have organization experienced due to unauthorized access to sensitive data, applications, or systems in the past 12 months? In the State of Authentication Security Report, cybersecurity professionals reported that the reallocation of IT resources for incident response and remediation was the most immediate negative impact (28%), followed by system or service downtime (26%) and increased helpdesk workload (24%).
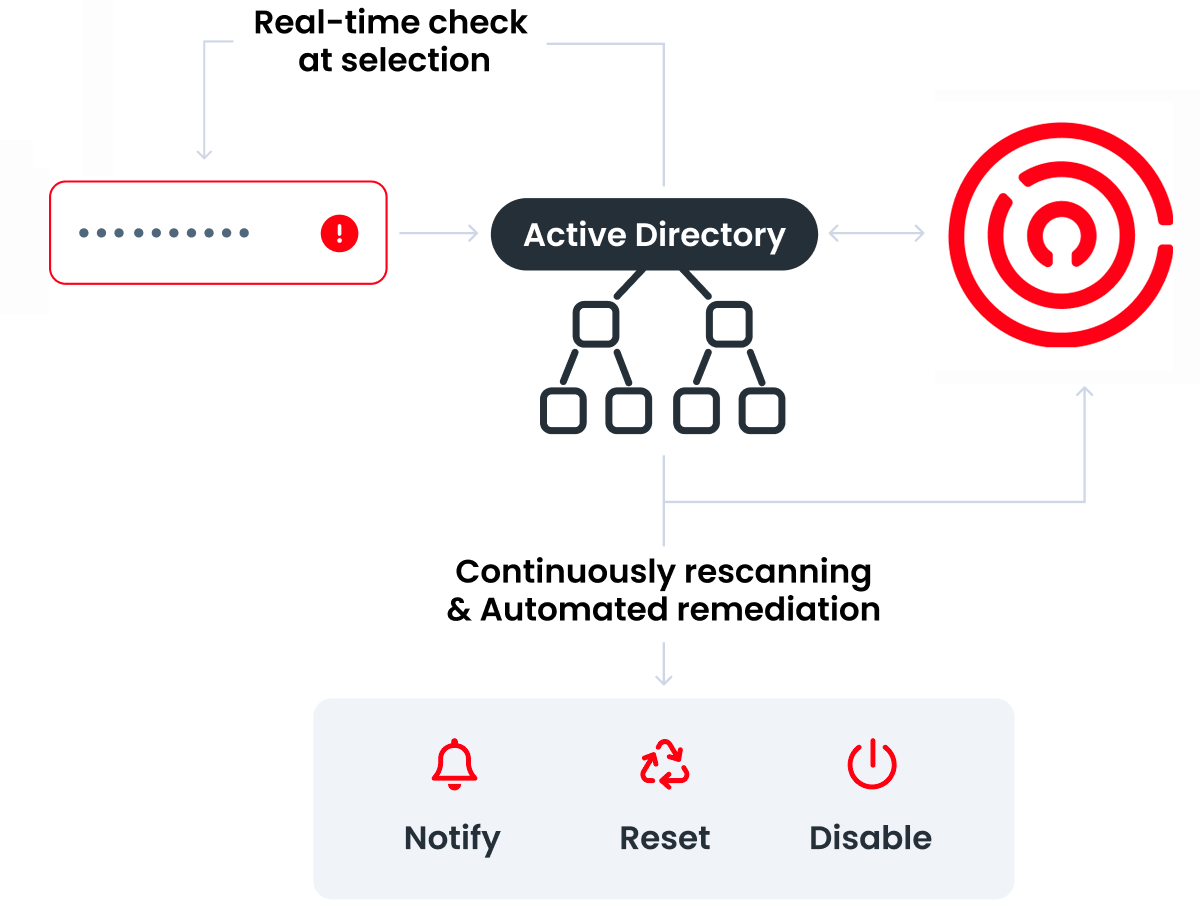
Enzoic for Active Directory goes beyond traditional password filters and security measures by offering a real-time, dynamic solution for maintaining password integrity within an Active Directory (AD) environment. By integrating directly with your existing AD infrastructure, it offers an additional layer of security that is often missing. What sets it apart is the power of an in-house threat intelligence team backed by machine learning, which continuously updates a massive database of compromised credentials.
Traditional password security solutions, such as Microsoft’s Entra ID, typically focus on enforcing strong password policies at the time of password creation, but they often miss the forest for the trees. The real issue is keeping up with the ever-changing landscape of compromised credentials, and this is where Enzoic shines. Their solutions fills a critical gap by continuously monitoring and validating not just newly set passwords, but also existing ones, thus securing the very foundational layer of your cybersecurity framework. This feature is a prerequisite for meeting leading compliance standards.
KEY FEATURES
Enzoic offers a cutting-edge solution for safeguarding your credentials with a range of exceptional features. Let’s explore how Enzoic stands out with continuous credential security, broad threat intelligence, and a seamless user experience.
1 – Continuous Credential Security: Enzoic sets itself apart by offering continuous screening against a database containing billions of compromised username and password pairs found on the Dark Web. This not only addresses newly created passwords but also identifies and remediates any existing vulnerable passwords that become compromised over time.
2 – Expansive Threat Intelligence: A dedicated in-house threat research team utilizes proprietary, powerful tools to scour the surface internet and Dark Web. This allows Enzoic to capture the most in-depth data sets, making its threat detection one of the most robust in the market. Moreover, this database is continually updated, ensuring that users can remediate swiftly before breaches occur.
3 – Great User Experience: While some solutions add friction at the user and admin level by incorporating more layers of authentication, Enzoic operates invisibly behind the scenes. This not only enables users to select stronger, more secure passwords but also reduces the workload for help desk support.
KEY BENEFITS
Enzoic’s continuous scanning and automated alerting system ensures that compromised or weak passwords are identified in real time. This contributes to a tangible enhancement in the overall security posture, fulfilling both compliance requirements and internal security benchmarks. The real power of Enzoic for Active Directory is in its simplicity and efficiency.
Within minutes of deployment, it starts offering:
• Streamlined Compliance: Companies striving to meet NIST 800-63b, HITRUST, or other leading industry compliance standards can automatically enforce compliance within their environment using Enzoic.
• Proactive ATO Prevention: By continuously monitoring passwords against a live database, Enzoic actively prevents Account Takeover (ATO) attacks, one of the leading causes of data breaches.
• Audit Efficiency: Real-time reports and alerting make it significantly easier to comply with auditing requirements.
• Resource Optimization: By automating the most labor-intensive aspects of password security, IT departments find a significant reduction in the time and resources needed for maintenance.
SOLUTION DELIVERY
The Enzoic solution is offered as a software-based plugin that integrates seamlessly into existing AD Domain Controllers. Optional endpoint agents are also available that provide users with specific instructions during password resets. If a user attempts to set a password that doesn’t meet policy requirements, they are guided on what adjustments need to be made for their password to align with policy, thereby enhancing the user experience and ensuring compliance.
In most cases, Enzoic for Active Directory can be up and running in under an hour, a testament to its userfriendly design. Enzoic for Active Directory operates on a subscription model, including a self-serve option with a free startup plan covering up to 20 users. The subscription cost is directly tied to the number of accounts that need protection. For specific pricing, you can refer to the official pricing page.
FINAL THOUGHTS
In a rapidly evolving cybersecurity landscape, Enzoic for Active Directory offers an agile, robust, and user-friendly solution to the ever-present challenge of compromised credentials. Its standout features like continuous credential security, expansive threat intelligence, and a minimalistic approach to user experience make it a highly recommended choice for any organization looking to fortify its first line of defense—passwords.
ABOUT ENZOIC
Enzoic is an enterprise-focused cybersecurity company committed to preventing account takeover and fraud through threat intelligence monitoring. Organizations can use Enzoic solutions to screen customer and employee accounts for exposed passwords, credentials, and PII to identify accounts at risk and mitigate
unauthorized access.
Learn more about Enzoic at: info@enzoic.com | www.enzoic.com
The post SOLUTION REVIEW: Enzoic for Active Directory appeared first on Cybersecurity Insiders.

