Category: Comcast
Comcast Ransomware Attack 2024: Overview and Implications
In a significant cybersecurity breach, telecom giant Comcast has reported that a ransomware attack has compromised the personal information of approximately 230,000 customers. This alarming revelation emerged from a recent filing with the Securities and Exchange Commission (SEC), highlighting the growing threat of cybercrime in the telecommunications sector.
The attack, which occurred in February 2024, was executed against a third-party debt collection agency, Financial Business and Consumer Solutions (FBCS), with which Comcast has had longstanding associations. Initial investigations suggest that the attackers infiltrated FBCS’s network first, subsequently gaining access to sensitive data linked to Comcast. This data breach reportedly involves information collected over the course of 2020 and 2021, raising serious concerns about the duration of the vulnerability.
The data compromised in this breach is particularly sensitive and includes customers’ names, addresses, Social Security numbers, dates of birth, and Comcast account numbers. The potential for identity theft and fraud is substantial, given the nature of the information that has been exposed. In response to the incident, Comcast has severed its ties with FBCS and is currently enlisting the expertise of cybersecurity professionals to navigate the fallout and bolster its defenses against future attacks.
American Water Cyber Attack: A Broader Threat to Infrastructure
In a related development, American Water, the largest water and wastewater utility company in the United States, has confirmed that it has fallen victim to a cyber attack. This incident has resulted in the suspension of its billing operations and certain application services, raising alarms about the security of critical infrastructure in the nation.
Headquartered in New Jersey, American Water has stated that it is actively investigating the nature of the attack. However, the company has refrained from labeling the incident specifically as ransomware, leaving open the possibility that it could involve a different form of cyber threat.
Given that American Water services over 13 million people across 14 states and supplies water to more than 18 military bases, the implications of this attack could be far-reaching. While initial reports indicate that the attack was detected in its early stages and contained before significant damage could occur, the potential for disruption to essential services remains a pressing concern.
The timing of this cyber incident is particularly noteworthy, as it coincided with preparations for the 2024 U.S. elections. Some analysts speculate that the attack may have been strategically aimed at creating public panic and undermining confidence in critical infrastructure during a politically sensitive period. The threat posed by such cyber attacks to the integrity of essential services is a stark reminder of the vulnerabilities that exist within the nation’s infrastructure.
Conclusion
Both the Comcast and American Water incidents underscore the increasing frequency and severity of cyber attacks on major companies and critical infrastructure in the United States. As cybercriminals continue to evolve their tactics, organizations must prioritize robust cybersecurity measures to protect sensitive customer information and ensure the uninterrupted delivery of essential services. The implications of these attacks extend beyond individual companies, posing a broader threat to national security and public trust in essential services.
The post Comcast Ransomware attack and American Water Cyber Attack shutdown appeared first on Cybersecurity Insiders.
A few days ago, Comcast hit the news headlines for increasing its service price so much that many of its customers weren’t ready for the surprise at all. Now, reports are in that the database of the Pennsylvania based digital services provider was hit by a cyber attack leading to a data breach, thus leaking details to hackers.
The attack reportedly took place on December 9th,2022(likely) when most of the IT staff were on a long Christmas leave or were about to take it to enjoy the festive season.
Going by the details, Xfinity email users started receiving email alerts that their account info was changed. And when they tried to access the account, their attempts failed as their passwords were changed. And after reporting the incident to the staff, the users discovered that a secondary email address was linked to their accounts without their knowledge.
Security analysts of the internet services provider stated that the attack could have taken place via credential stuffing and, as of now, Xfinity, the business subsidiary of Comcast has confirmed that the credentials were compromised.
Comcast is yet to officiate the attack, as it is waiting for the preliminary investigation to conclude.
NOTE- In the year 2018, an individual named Elizabeth putative class action suit was launched against the company for allowing cyber criminals to book new mobile phones on the name of customers without consent. Later it was revealed in the probe that the hackers got access to data of consumers using internet and TV cable accounts and used that stolen info to book smartphones on the website. However, the lawsuit went through arbitration and so wasn’t publicized much, as there was no clarity on who booked the smart phones and to which address they were mailed.
The post Data Breach leads to Comcast Customer Data Leak appeared first on Cybersecurity Insiders.
The Department of Homeland Security (DHS) is urging states and localities to beef up security around proprietary devices that connect to the Emergency Alert System — a national public warning system used to deliver important emergency information, such as severe weather and AMBER alerts. The DHS warning came in advance of a workshop to be held this weekend at the DEFCON security conference in Las Vegas, where a security researcher is slated to demonstrate multiple weaknesses in the nationwide alert system.

A Digital Alert Systems EAS encoder/decoder that Pyle said he acquired off eBay in 2019. It had the username and password for the system printed on the machine.
The DHS warning was prompted by security researcher Ken Pyle, a partner at security firm Cybir. Pyle said he started acquiring old EAS equipment off of eBay in 2019, and that he quickly identified a number of serious security vulnerabilities in a device that is broadly used by states and localities to encode and decode EAS alert signals.
“I found all kinds of problems back then, and reported it to the DHS, FBI and the manufacturer,” Pyle said in an interview with KrebsOnSecurity. “But nothing ever happened. I decided I wasn’t going to tell anyone about it yet because I wanted to give people time to fix it.”
Pyle said he took up the research again in earnest after an angry mob stormed the U.S. Capitol on Jan. 6, 2021.
“I was sitting there thinking, ‘Holy shit, someone could start a civil war with this thing,”’ Pyle recalled. “I went back to see if this was still a problem, and it turns out it’s still a very big problem. So I decided that unless someone actually makes this public and talks about it, clearly nothing is going to be done about it.”
The EAS encoder/decoder devices Pyle acquired were made by Lyndonville, NY-based Digital Alert Systems (formerly Monroe Electronics, Inc.), which issued a security advisory this month saying it released patches in 2019 to fix the flaws reported by Pyle, but that some customers are still running outdated versions of the device’s firmware. That may be because the patches were included in version 4 of the firmware for the EAS devices, and many older models apparently do not support the new software.
“The vulnerabilities identified present a potentially serious risk, and we believe both were addressed in software updates issued beginning Oct 2019,” EAS said in a written statement. “We also provided attribution for the researcher’s responsible disclosure, allowing us to rectify the matters before making any public statements. We are aware that some users have not taken corrective actions and updated their software and should immediately take action to update the latest software version to ensure they are not at risk. Anything lower than version 4.1 should be updated immediately. On July 20, 2022, the researcher referred to other potential issues, and we trust the researcher will provide more detail. We will evaluate and work to issue any necessary mitigations as quickly as possible.”
But Pyle said a great many EAS stakeholders are still ignoring basic advice from the manufacturer, such as changing default passwords and placing the devices behind a firewall, not directly exposing them to the Internet, and restricting access only to trusted hosts and networks.

Pyle, in a selfie that is heavily redacted because the EAS device behind him had its user credentials printed on the lid.
Pyle said the biggest threat to the security of the EAS is that an attacker would only need to compromise a single EAS station to send out alerts locally that can be picked up by other EAS systems and retransmitted across the nation.
“The process for alerts is automated in most cases, hence, obtaining access to a device will allow you to pivot around,” he said. “There’s no centralized control of the EAS because these devices are designed such that someone locally can issue an alert, but there’s no central control over whether I am the one person who can send or whatever. If you are a local operator, you can send out nationwide alerts. That’s how easy it is to do this.”
One of the Digital Alert Systems devices Pyle sourced from an electronics recycler earlier this year was non-functioning, but whoever discarded it neglected to wipe the hard drive embedded in the machine. Pyle soon discovered the device contained the private cryptographic keys and other credentials needed to send alerts through Comcast, the nation’s third-largest cable company.
“I can issue and create my own alert here, which has all the valid checks or whatever for being a real alert station,” Pyle said in an interview earlier this month. “I can create a message that will start propagating through the EAS.”
Comcast told KrebsOnSecurity that “a third-party device used to deliver EAS alerts was lost in transit by a trusted shipping provider between two Comcast locations and subsequently obtained by a cybersecurity researcher.
“We’ve conducted a thorough investigation of this matter and have determined that no customer data, and no sensitive Comcast data, were compromised,” Comcast spokesperson David McGuire said.
The company said it also confirmed that the information included on the device can no longer be used to send false messages to Comcast customers or used to compromise devices within Comcast’s network, including EAS devices.
“We are taking steps to further ensure secure transfer of such devices going forward,” McGuire said. “Separately, we have conducted a thorough audit of all EAS devices on our network and confirmed that they are updated with currently available patches and are therefore not vulnerable to recently reported security issues. We’re grateful for the responsible disclosure and to the security research community for continuing to engage and share information with our teams to make our products and technologies ever more secure. Mr. Pyle informed us promptly of his research and worked with us as we took steps to validate his findings and ensure the security of our systems.”
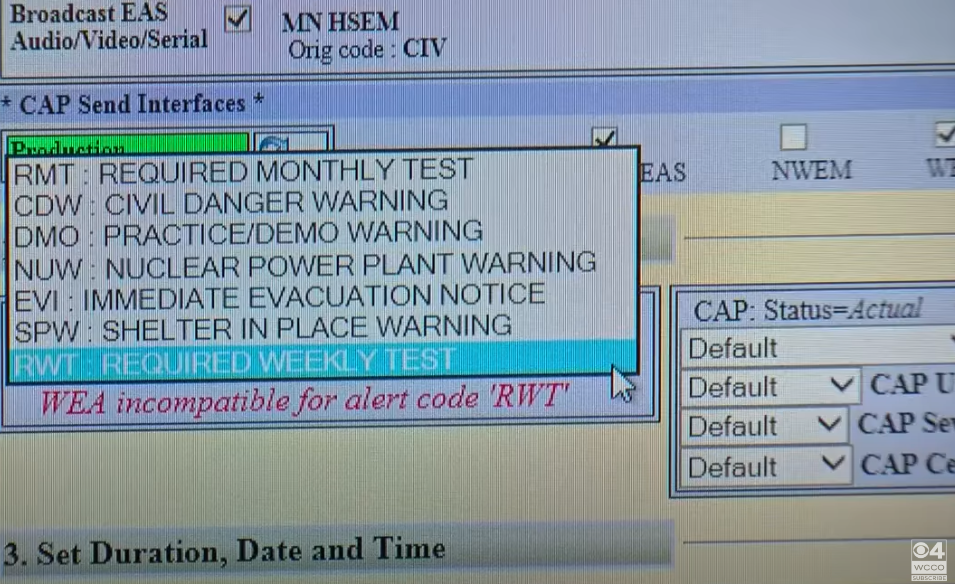
The user interface for an EAS device.
Unauthorized EAS broadcast alerts have happened enough that there is a chronicle of EAS compromises over at fandom.com. Thankfully, most of these incidents have involved fairly obvious hoaxes.
According to the EAS wiki, in February 2013, hackers broke into the EAS networks in Great Falls, Mt. and Marquette, Mich. to broadcast an alert that zombies had risen from their graves in several counties. In Feb. 2017, an EAS station in Indiana also was hacked, with the intruders playing the same “zombies and dead bodies” audio from the 2013 incidents.
“On February 20 and February 21, 2020, Wave Broadband’s EASyCAP equipment was hacked due to the equipment’s default password not being changed,” the Wiki states. “Four alerts were broadcasted, two of which consisted of a Radiological Hazard Warning and a Required Monthly Test playing parts of the Hip Hop song Hot by artist Young Thug.”
In January 2018, Hawaii sent out an alert to cell phones, televisions and radios, warning everyone in the state that a missile was headed their way. It took 38 minutes for Hawaii to let people know the alert was a misfire, and that a draft alert was inadvertently sent. The news video clip below about the 2018 event in Hawaii does a good job of walking through how the EAS works.