Category: Disney
Disney Drops Slack Following Data Breach Allegations
In July, Slack, the widely-used corporate communication platform, suffered a cyberattack that resulted in the breach of terabytes of data. Consequently, the Walt Disney Company, which utilized Slack for internal communications, has decided to discontinue its use of the platform. By early next year, Disney will transition to an alternative solution.
Hugh Johnston, Disney’s CFO, confirmed this decision to CNBC, noting that all employees will be instructed to migrate to the new platform and will receive training by the end of the year.
Hacking Group Targets UK Parliament and WHO Officials on X
In recent days, a hacking group has compromised the X (formerly Twitter) accounts of several British parliamentarians and officials from the World Health Organization (WHO). The hackers displayed a promotional banner for various cryptocurrencies on these accounts, aiming to generate illicit profits. Among those affected were Justice Secretary Shabana Mahmood, Labour MP Chris Elmore, and Carolyn Harris, all of whom have since regained control of their accounts.
Implementing multi-factor authentication could significantly reduce the risk of such breaches.
United States company hacks Indian Supreme Court
In a troubling incident, the YouTube channel of the Supreme Court of India was hacked by cybercriminals who replaced its content with promotions for XRP, a cryptocurrency developed by Ripple Labs in North America. This incident raises questions about whether it was an advertising error or a genuine hack. Since 2018, the Supreme Court has been live-streaming cases of public interest, making this breach particularly concerning. The Indian government’s cyber teams swiftly regained control of the channel within 50 minutes and are currently working to restore it and identify the attackers.
The post Top data breach news headlines trending on Google appeared first on Cybersecurity Insiders.
Over the past few days, AT&T, a major American telecom company, has made headlines due to a sophisticated cyber-attack that exposed the details of over 109 million mobile customers dating back to 2022.
According to updates received by our Cybersecurity Insiders, the data breach occurred in 2022 and affected customers who used AT&T’s telecom services between March and October of that year. This includes users of their cellular network, virtual mobile network, and landline services.
Fortunately, the hackers did not access sensitive information such as social security numbers (PII). As of now, there is no evidence that the information gleaned from calls and text messages has been used for social engineering attacks against affected customers.
AT&T has set up a dedicated web portal for customers to check if their number was impacted by the breach. Those affected will be notified digitally for further clarification.
In a separate incident, hackers have reportedly stolen a massive 1TB dataset from Disney’s Slack servers. The stolen data allegedly includes details about upcoming projects, conceptual art for Disney Games, and personal information of employees. Among the leaked details are plans related to projects like “Marvel 1943: The Rise of the Hydra” and the Deadpool movie, generating anticipation among fans eager for glimpses of future episodes.
It remains unclear whether the hacking group “Nullbulge” breached Disney’s servers for financial gain or to sell the stolen data on the dark web.
In recent years, cybercriminals have increasingly targeted technology and gaming companies, knowing they can demand hefty ransom payments to disrupt operations. For instance, CDK Group, which provides software services to the automotive industry in America, recently faced a ransomware attack and reportedly paid a ransom of $22 million.
The FBI has criticized the practice of paying ransom, arguing that it does not guarantee a decryption key and can incentivize further crime. Instead, they recommend victims contact law enforcement and share details to aid in stopping the spread of malware to other businesses. In some cases, victims may even receive decryption assistance from authorities at no cost.
The post Details of AT&T data breach and 1TB data steal belonging to Disney appeared first on Cybersecurity Insiders.
When the marital infidelity website AshleyMadison.com learned in July 2015 that hackers were threatening to publish data stolen from 37 million users, the company’s then-CEO Noel Biderman was quick to point the finger at an unnamed former contractor. But as a new documentary series on Hulu reveals [SPOILER ALERT!], there was just one problem with that theory: Their top suspect had killed himself more than a year before the hackers began publishing stolen user data.
The new documentary, The Ashley Madison Affair, begins airing today on Hulu in the United States and on Disney+ in the United Kingdom. The series features interviews with security experts and journalists, Ashley Madison executives, victims of the breach and jilted spouses.

The series also touches on shocking new details unearthed by KrebsOnSecurity and Jeremy Bullock, a data scientist who worked with the show’s producers at the Warner Bros. production company Wall to Wall Media. Bullock had spent many hours poring over the hundreds of thousands of emails that the Ashley Madison hackers stole from Biderman and published online in 2015.
Wall to Wall reached out in July 2022 about collaborating with Bullock after KrebsOnSecurity published A Retrospective on the 2015 Ashley Madison Breach. That piece explored how Biderman — who is Jewish — had become the target of concerted harassment campaigns by anti-Semitic and far-right groups online in the months leading up to the hack.
Whoever hacked Ashley Madison had access to all employee emails, but they only released Biderman’s messages — three years worth. Apropos of my retrospective report, Bullock found that a great many messages in Biderman’s inbox were belligerent and anti-Semitic screeds from a former Ashley Madison employee named William Brewster Harrison.

William Harrison’s employment contract with Ashley Madison parent Avid Life Media.
The messages show that Harrison was hired in March 2010 to help promote Ashley Madison online, but the messages also reveal Harrison was heavily involved in helping to create and cultivate phony female accounts on the service.
There is evidence to suggest that in 2010 Harrison was directed to harass the owner of Ashleymadisonsucks.com into closing the site or selling the domain to Ashley Madison.
Ashley Madison’s parent company — Toronto-based Avid Life Media — filed a trademark infringement complaint in 2010 that succeeded in revealing a man named Dennis Bradshaw as the owner. But after being informed that Bradshaw was not subject to Canadian trademark laws, Avid Life offered to buy AshleyMadisonSucks.com for $10,000.
When Bradshaw refused to sell the domain, he and his then-girlfriend were subject to an unrelenting campaign of online harassment and blackmail. It now appears those attacks were perpetrated by Harrison, who sent emails from different accounts at the free email service Vistomail pretending to be Bradshaw, his then-girlfriend and their friends.
[As the documentary points out, the domain AshleyMadisonSucks.com was eventually transferred to Ashley Madison, which then shrewdly used it for advertising and to help debunk theories about why its service was supposedly untrustworthy].
Harrison even went after Bradshaw’s lawyer and wife, listing them both on a website he created called Contact-a-CEO[.]com, which Harrison used to besmirch the name of major companies — including several past employers — all entities he believed had slighted him or his family in some way. The site also claimed to include the names, addresses and phone numbers of top CEOs.
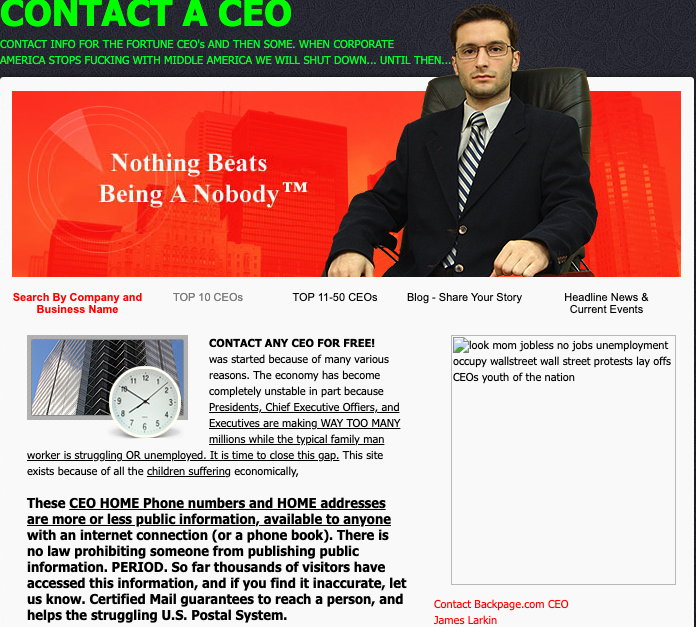
A cached copy of Harrison’s website, contact-the-ceo.com.
An exhaustive analysis of domains registered to the various Vistomail pseudonyms used by Harrison shows he also ran Bash-a-Business[.]com, which Harrison dedicated to “all those sorry ass corporate executives out there profiting from your hard work, organs, lives, ideas, intelligence, and wallets.” Copies of the site at archive.org show it was the work of someone calling themselves “The Chaos Creator.”
Will Harrison was terminated as an Ashley Madison employee in November 2011, and by early 2012 he’d turned his considerable harassment skills squarely against the company. Ashley Madison’s long-suspected army of fake female accounts came to the fore in August 2012 after the former sex worker turned activist and blogger Maggie McNeill published screenshots apparently taken from Ashley Madison’s internal systems suggesting that a large percentage of the female accounts on the service were computer-operated bots.
Ashley Madison’s executives understood that only a handful of employees at the time would have had access to the systems needed to produce the screenshots McNeill published online. In one exchange on Aug. 16, 2012, Ashley Madison’s director of IT was asked to produce a list of all company employees with all-powerful administrator access.
“Who or what is asdfdfsda@asdf.com?,” Biderman asked, after being sent a list of nine email addresses.
“It appears to be the email address Will used for his profiles,” the IT director replied.
“And his access was never shut off until today?,” asked the company’s general counsel Mike Dacks.
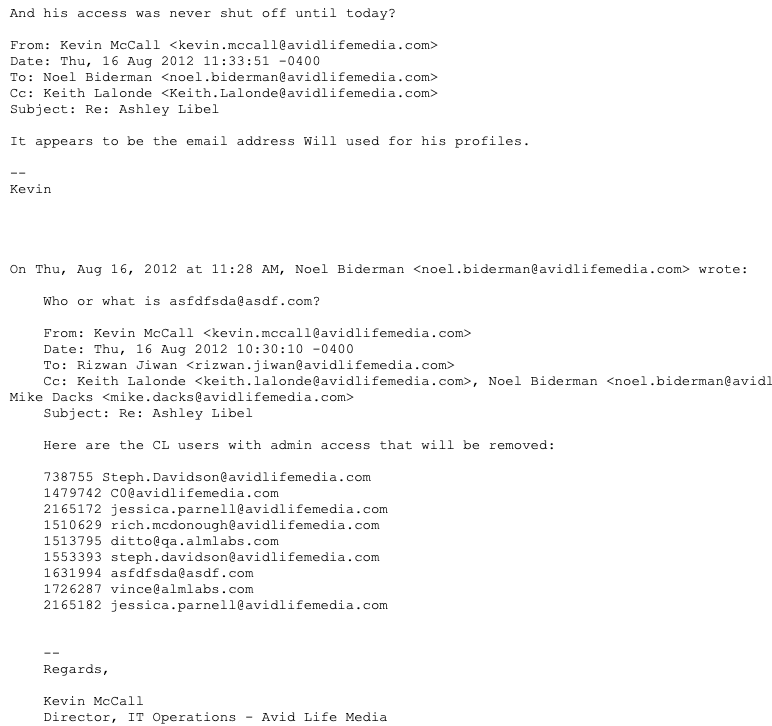
A Biderman email from 2012.
What prompted the data scientist Bullock to reach out were gobs of anti-Semitic diatribes from Harrison, who had taken to labeling Biderman and others “greedy Jew bastards.”
“So good luck, I’m sure we’ll talk again soon, but for now, Ive got better things in the oven,” Harrison wrote to Biderman after his employment contract with Ashley Madison was terminated. “Just remember I outsmarted you last time and I will outsmart and out maneuver you this time too, by keeping myself far far away from the action and just enjoying the sideline view, cheering for the opposition.”
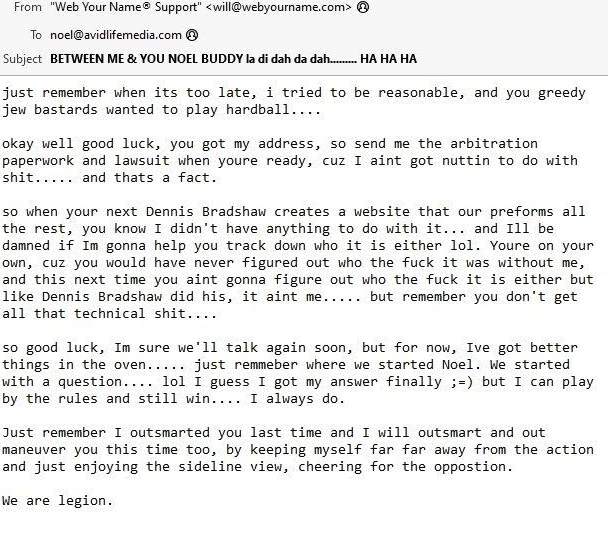
A 2012 email from William Harrison to former Ashley Madison CEO Noel Biderman.
Harrison signed his threatening missive with the salutation, “We are legion,” suggesting that whatever comeuppance he had in store for Ashley Madison would come from a variety of directions and anonymous hackers.
The leaked Biderman emails show that Harrison made good on his threats, and that in the months that followed Harrison began targeting Biderman and other Ashley Madison executives with menacing anonymous emails and spoofed phone calls laced with profanity and anti-Semitic language.
But on Mar. 5, 2014, Harrison committed suicide by shooting himself in the head with a handgun. This fact was apparently unknown to Biderman and other Ashley Madison executives more than a year later when their July 2015 hack was first revealed.
Does Harrison’s untimely suicide rule him out as a suspect in the 2015 hack? Who is The Chaos Creator, and what else transpired between Harrison and Ashley Madison prior to his death? We’ll explore these questions in Part II of this story, to be published early next week.