The cybersecurity landscape is constantly evolving, with bad actors finding new and creative ways to exploit weaknesses. The threat from Malware continues to escalate with infostealers, an increasingly popular variant. Research found that 24% of malware is now infostealers, and it’s now one of the most popular topics on the cybercriminal underground. The malicious software allows cyber criminals of limited means and technical knowledge to deploy it and start accessing networks and stealing data.
Infostealers Snapshot
Infostealers is a type of malware-as-a-service (MaaS) that extracts data from infected devices. Unlike ransomware, where information is held hostage, these attacks happen covertly, and the growth has been driven by the explosion in connected devices coupled with the ease of trading information on Dark Web sites.
The MaaS model has lowered the barrier to entry, driving up the risk. Bad actors lease malicious software from the Dark Web to carry out cyber-attacks. Once installed, the infostealer stealthily gathers data, including usernames, passwords, date of birth, home address, bank account numbers, credit card information, cell number, cookies and session IDs. The information is then sold and published as logs on the Dark Web.
The threat from info stealers shows no signs of slowing, and hackers are continuing to expand their tactics to infect machines. These include:
- Phishing emails that entice people to open an attachment with the software embedded in the document.
- Adding the code to an application such as a mobile app, a web browser, or a browser extension and then making that app available for download from popular app stores
- Advertising on Google and Facebook Ads to dupe people into downloading the malware. This tactic is so effective the FBI issued a PSA warning against it.
Hybrid Work Environments Increasing Vulnerabilities
Hybrid work introduces new risks as many people rely on one device for professional and personal. Therefore, an employee might download infostealer malware via a gaming site that would then expose all of the corporate data contained on the device.
This is partly why infostealers are so difficult to prevent because they exploit the weakest link in cybersecurity – human behavior. Instead of relying on complex multi-step attacks to compromise a system, they wait for the user to open the door for them!
The Password Manager Problem
Once a device is infected, password managers are the most valuable target. The malware can exploit vulnerabilities in these solutions, gaining access to all saved credentials and monitoring and stealing new ones as they are entered. In addition, password managers link the URL where the respective credential is used, so infostealers expose the credential in not only plain text but also all of the websites and services associated with it. This can then ignite credential stuffing and password spraying attacks. Additionally, the pervasive problem of password reuse means that if a manager is used for personal accounts, it’s very likely that the credentials are shared with work accounts.
MFA is not Bullet Proof
When it comes to infostealers, multi-factor authentication (MFA) is far from a failsafe. For example, MFA is often bypassed if a device has logged into an account before and is trusted–which is done by dropping a cookie. These cookies can then be stolen by the infostealer and reused by threat actors, thereby rendering MFA ineffective. In addition, active login session IDs can also be stolen using this method.
Threat Intelligence Key to Preventing Infostealer Attacks
With infostealers, organizations must remain vigilant and modernize their security strategies to enhance and strengthen their defenses against the ever-changing cyber threat landscape. Monitoring the Dark Web provides enterprises with the intelligence to stay in front of the latest trends. Early detection is essential as any delay can result in the compromise of important accounts and, from there, the exposure of sensitive data.
With the risks from the malicious software showing no sign of slowing, it’s essential that companies integrate a proactive threat intelligence solution to strengthen their security posture. This will help mitigate the risks and ensure that if sensitive information or credentials are exposed in third-party breaches or infostealers logs, they can take quick action to prevent a breach.
Enzoic’s Approach
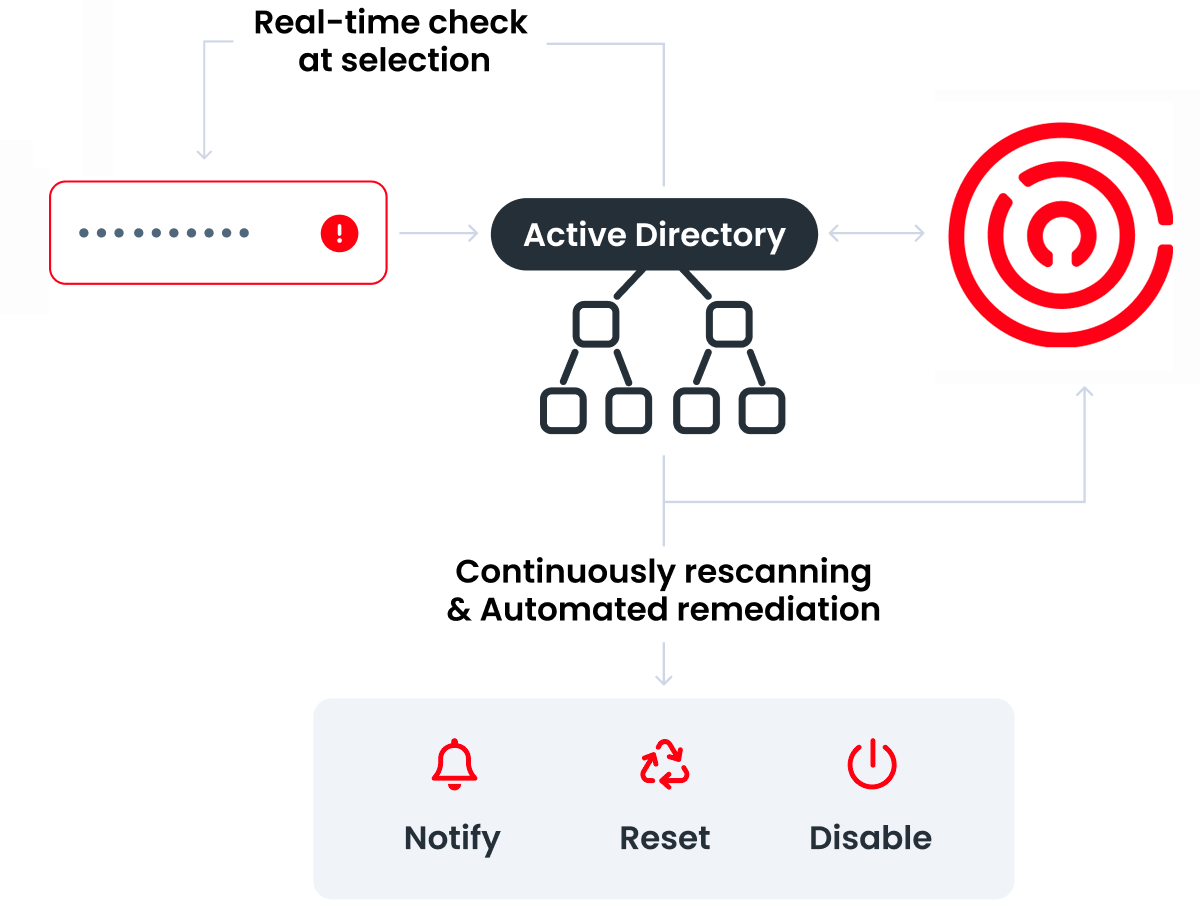
Enzoic offers a proprietary Dark Web monitoring solution that combines its dynamic threat database with extensive Dark Web research capabilities. This gives companies an automated and intelligent way to prevent credentials or other sensitive information from being used for financial gain, fraud, or account takeover.
Enzoic’s solutions combine the most comprehensive, complete, and actionable threat research data with automated remediation to help every enterprise strengthen its security posture. Critically, through its proprietary Dark Web monitoring capabilities, Enzoic can collect infostealers logs as soon as they are posted, allowing companies to stay a step ahead of threat actors.
The post Why Infostealers are Stealing the Security Spotlight appeared first on Cybersecurity Insiders.