Introduction
Most people remain curious about digital security for medical records today. Blockchain is a pathbreaking technology that has been evolving as a technological security shield for the healthcare industry, the financial sector, and many others. The system provides maximum security because it relies on interconnected digital blocks within its decentralized structure.
Just as a digital fortress protects precious data, blockchain in healthcare has emerged as a game-changing solution for protecting sensitive medical information. A revolutionary healthcare technology now controls the patient data management process by building security measures to protect information levels while remaining transparent to users.
Importance of Data Security in Healthcare
Healthcare data security is a critical concern in modern medicine, as patient records contain sensitive personal and medical information. Recent breaches of traditional systems exposed their weaknesses; therefore, healthcare providers need adequate protection methods.
Blockchain Solutions for Security Challenges
Patient data security with blockchain offers an innovative approach to protecting medical records through encrypted, immutable ledgers. Data security through this technology forms an indestructible chain of information blocks that provides complete protection against unauthorized access during authorized personnel information distribution processes.
Growing Adoption and Future Potential
The medical industry has focused on blockchain technology, with healthcare organizations increasingly implementing blockchain development solutions. Medical industry professionals estimate that this encrypted, decentralized system for patient data management will become the normative practice by 2030.
Understanding Blockchain Technology in Healthcare
Definition of Blockchain
The technology functions as an unalterable digital record system. In healthcare data security, it’s a system that stores patient information in connected blocks, each containing medical records secured through advanced encryption.
How Blockchain Works in Healthcare
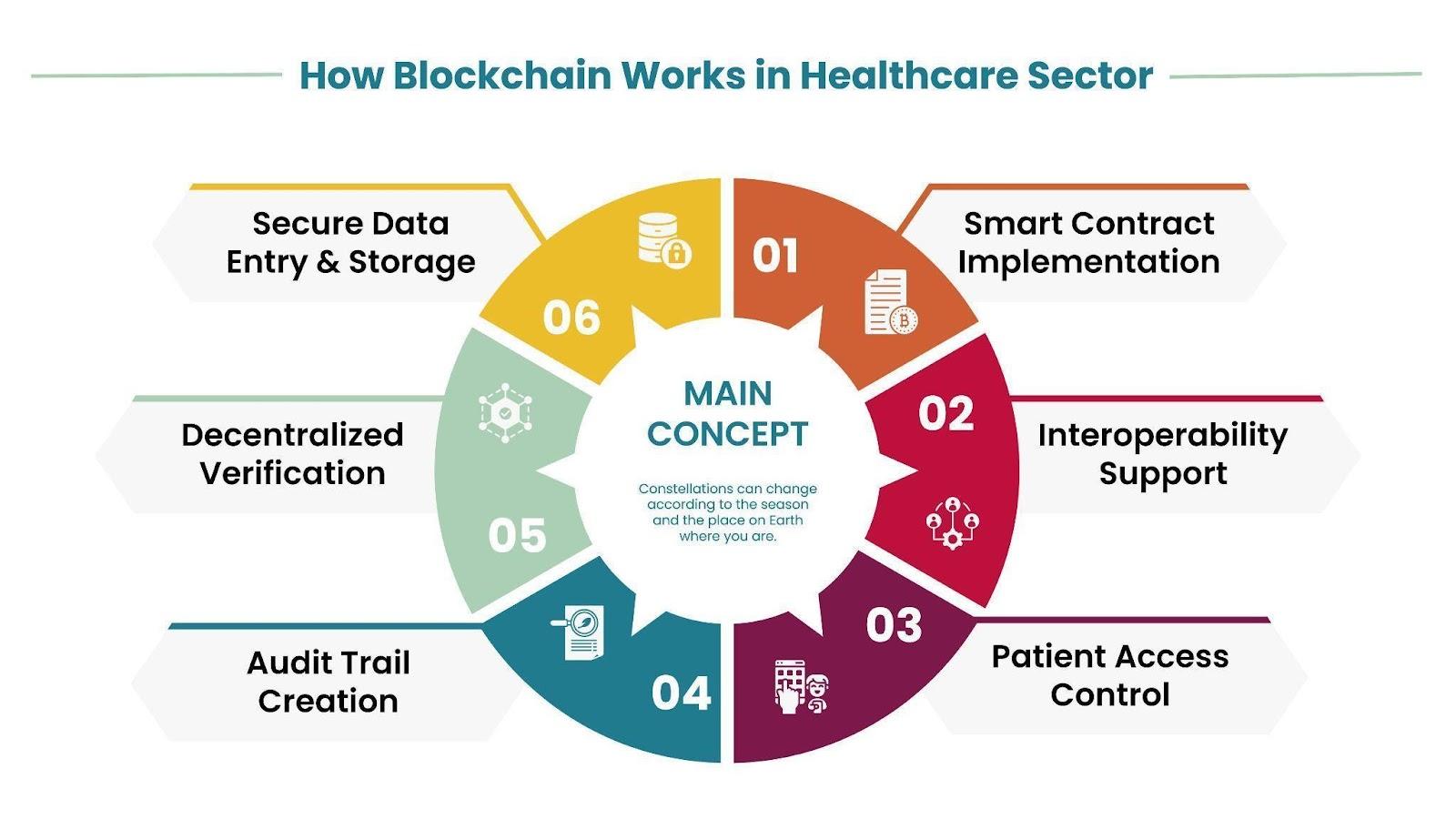
Secure Data Entry and Storage
Blocks receive patient information from healthcare providers, which is instantly encrypted and linked with previous medical documents. This ensures that blockchain for healthcare data protection remains tamper-proof.
Decentralized Verification
Multiple network computers conduct parallel verification of new data, which provides blockchain medical records superior protection than centralized setups while abiding by HIPAA rules.
Smart Contract Implementation
Automated protocols protect patient data by defining system access permissions according to roles. They also enable operational efficiency in data management.
Interoperability Support
Blockchain technology in the medical industry enables seamless sharing of patient data between authorized healthcare providers while maintaining strict security protocols.
Audit Trail Creation
Every interaction with patient data creates an unchangeable record, making blockchain development solutions ideal for tracking and preventing unauthorized access.
Patient Access Control
Patients gain authority over medical record visibility through decentralized healthcare solutions, which increases safety measures in the healthcare sector.
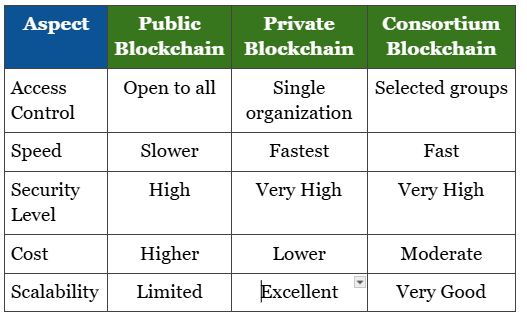
Types of Blockchain Networks
Public Blockchain
Bitcoin’s open network design allows anyone to participate. Blockchain systems provide maximum transparency in healthcare, although top-notch security systems are needed to guard patient data safety while upholding regulatory requirements.
Private Blockchain
Access to controlled networks is limited to additional healthcare providers who hold authorization. These systems use blockchain to enhance patient data security while maintaining strict access control and faster transaction processing.
Consortium Blockchain
These networks connect a group of healthcare institutions that choose to collaborate on restricted data. Blockchain applications in healthcare balance security and efficiency through shared governance.
Blockchain Comparison: Public Vs. Private Vs. Consortium
Blockchain as a Healthcare Game-changer
The healthcare industry benefits from blockchain development because it provides optimal security features for protecting patient data. Here’s why:
- Real-time tracking systems stop unauthorized users from accessing sensitive medical information at once.
- Multiple safeguards protect patient data from professional cyber threats at public and private health institutions.
- The decentralization of operations removes any weaknesses that could cause data storage system failures.
- Healthcare protection regulations become automated through smart contracts, which perform the necessary regulatory compliance.
- Transparency in audit tracks enables responsible tracking of medical record management activities.
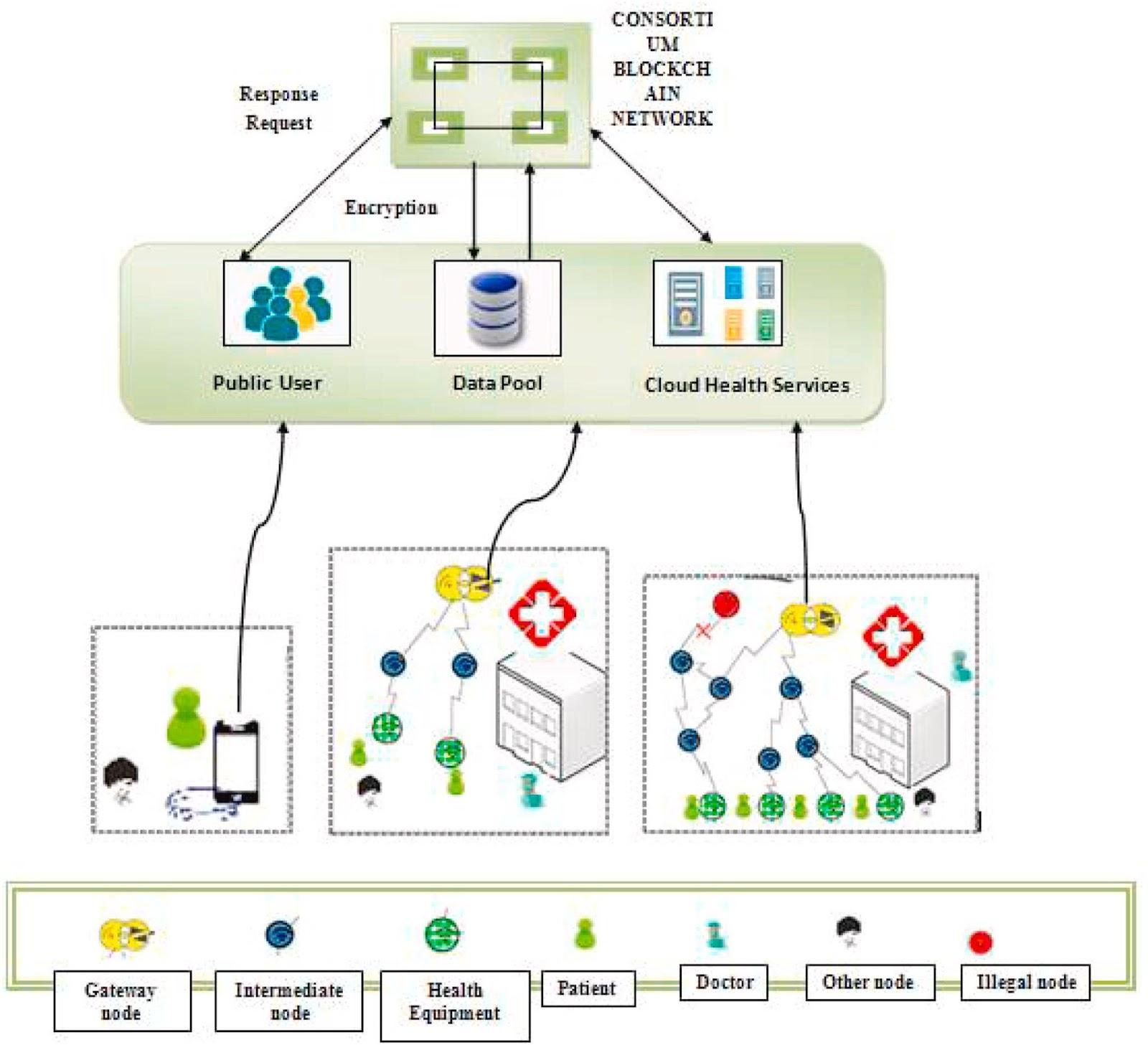
Proposed architecture for security authentication
Image Courtesy: ScienceDirect
The Importance of Patient Data Security in Healthcare
Healthcare data security forms the backbone of modern medical services, protecting sensitive patient information from growing cyber threats. Blockchain technology offers unique security methods to protect this critical patient information comprehensively.
Current Data Security Challenges
Medical organizations encounter unprecedented security threats when protecting their patient databases. Healthcare cybersecurity solutions must keep adapting to new threats that appear in the industry.
- Traditional healthcare IT systems fail to provide the updated security capabilities that modern medical practice requires.
- Organizations experience unauthorized data infiltration through their various entry points, which happens every day.
- The connection of multiple healthcare systems produces regular security weaknesses.
- Maintaining staff readiness regarding data security procedures proves to be an ongoing obstacle.
- High costs restrict healthcare organizations from deploying state-of-the-art security systems.
Rising Security Threats
Patient data security with blockchain has become crucial as cyberattacks increase. Clinical organizations have expressed severe concerns about data breaches that target private medical records.
- Hospital ransomware attacks dramatically increased during the previous year.
- The valuable medical records of patients receive special attention from hackers who aim to make financial gains.
- Authorized employee activities cause frequent internal breaches in healthcare systems.
- Advanced cyber attacks circumvent security systems that were installed using outdated technology methods.
- Mobile device systems that contain weaknesses represent potential threats to patient information security.
Regulatory Compliance Requirements
Blockchain for healthcare data protection helps meet strict regulatory standards. Implementing blockchain for HIPAA compliance ensures the correct management of critical medical data.
- Organizations in healthcare face substantial financial consequences whenever they violate HIPAA guidelines.
- The protection of patient data needs to follow the requirements set by worldwide privacy laws.
- Security documentation and proof must provide comprehensive details for regular compliance audits.
- The management of patient consent faces increasing complexity because digital records exist.
- Multiple regulations must be followed during the process of sharing data across national borders.
Centralized Storage Risks
Traditional centralized data storage poses significant risks, making blockchain development solutions increasingly attractive. Patient data security demands new management methods.
- The entire healthcare database becomes instantly affected when a single-point failure occurs.
- Centralized systems regularly draw attacks from cyber offenders who target their operations.
- A single disruption of the system simultaneously affects patient care delivery in different healthcare facilities.
- The recovery of lost data becomes extremely difficult after security incidents occur.
- Healthcare organizations face challenges in deploying security measures because of their restricted growth potential.
How Blockchain Enhances Patient Data Security
Blockchain for healthcare data protection revolutionizes how medical institutions safeguard sensitive information. Healthcare providers achieve exceptional security protection with unprecedented ease of accessing critical patient data through the implementation of this advanced technology.
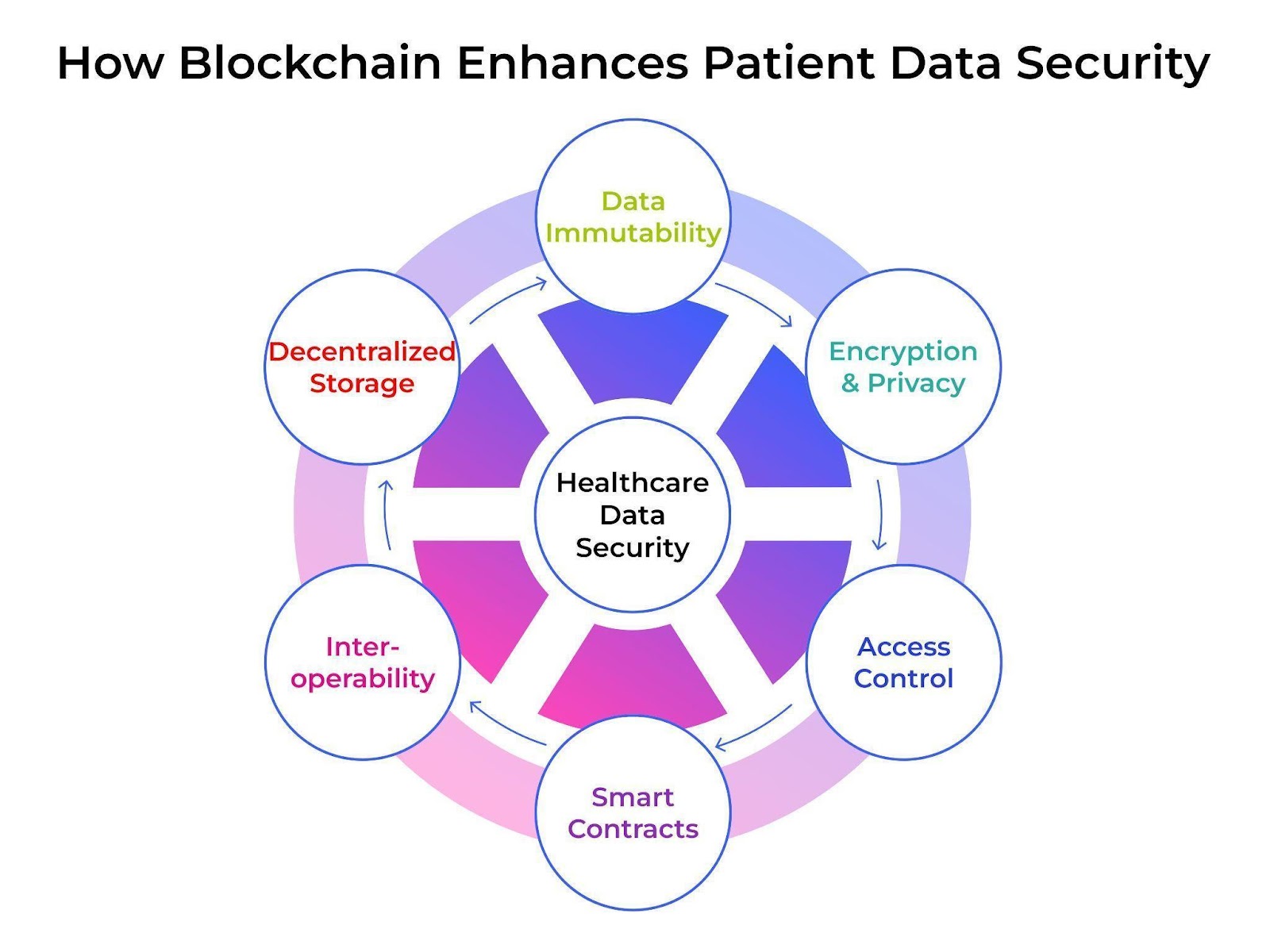
Decentralized Storage
Patient data security with blockchain utilizes distributed storage across multiple secure nodes, eliminating vulnerable central points of failure. This healthcare solution’s extensive distributed nature makes it almost impossible for hackers to breach the entire system, as the information is spread across numerous network locations.
Data Immutability
Through blockchain medical records systems, medical information maintains an uneditable historical record of all patient documentation. Recorded medical data becomes unalterable and tamper-proof by cryptographic methods that apply permanent sealing techniques to data when it enters the blockchain.
Encryption & Privacy
Blockchain’s advanced encryption methods have elevated healthcare data security to new heights. Individual cryptographic key encoding secures the storage of patient information and protects sensitive data from unauthorized access.
Access Control & Permissioned Sharing
Blockchain technology in the medical industry empowers patients with granular control over their health records. Patients gain authority over their medical records by giving and taking away access to healthcare providers through protected database systems that monitor all user activities.
Smart Contracts
Blockchain development solutions incorporate automated smart contracts that enforce security protocols without human intervention. The self-executing agreements enforced by blockchain technology maintain HIPAA compliance through the automatic execution of specified security rules as well as access permissions.
Interoperability
Healthcare organizations benefit from blockchain applications, which provide safe data interoperability between various healthcare systems. Healthcare security solutions through blockchain technology develop systematic information-sharing standards together with high-strength data protection against computer attacks and breaches.
Real-world Applications of Blockchain in Healthcare Security
Medical institutions utilize blockchain-based solutions to enhance their abilities to protect patient information and its management systems. With blockchain development solutions, healthcare data security has evolved significantly, creating more efficient and secure systems for handling sensitive medical data.
Electronic Health Records (EHRs)
Patient data security with blockchain revolutionizes electronic health record management by creating an immutable, secure system for storing and accessing medical information. Healthcare records remain safeguarded, yet authorized providers can quickly obtain them through this protection method.
- The tamper-resistant security of blockchain medical records reveals an entire patient history at all times.
- Medical records become instantly available to authorized healthcare personnel through the different service facilities.
- The system automatically ensures HIPAA compliance for every access request through smart contracts.
Medical Data Sharing
Blockchain for healthcare data protection enables the secure sharing of medical information between providers and researchers. Decentralization in healthcare also enables secure information sharing between sources to enhance treatment results without infringing on patient rights to privacy.
- Medical patients maintain active oversight over people who need access to their medical records at all times.
- Through blockchain healthcare technology, doctors gain automatic access to vital patient information while in emergencies.
- Researchers gain secure access to health data for medical discovery purposes.
Clinical Trials & Research
Blockchain technology in the medical industry ensures the integrity of clinical trial data. Healthcare cybersecurity options safeguard research data by securing it while keeping complete transparency in all research stages.
- Scientists must refrain from modifying trial data because they have already logged the first results.
- Medical research operations safeguard patient privacy throughout every critical stage of each study.
- Research protocols, together with their results, stay available to maintain regulatory transparency.
Drug Supply Chain Security
Clinical data security takes form through pharmaceutical tracking, which ensures original drugs stay in the supply stream and maintains continuous medication history records.
- The identification and tracking system exists for each medicine package through blockchain technology.
- All members of the supply chain confirm drug authenticity throughout the distribution process.
- Patients should find it easy to validate medications prior to taking them.
Insurance & Billing Fraud Prevention
The use of blockchain solutions provides visibility into claim processing to stop insurance fraud occurrences and data breaches. The system builds an unalterable database that monitors every healthcare transaction.
- Smart contracts use automatic systems to both check insurance claims and stop duplicated payments.
- The system preserves billing records permanently as unchangeable records for auditing requirements.
- Any healthcare organization can monitor its financial transactions and claim processing in real-time.
Benefits of Blockchain for Healthcare Data Security
Blockchain technology protects medical industry data through its unattackable protective mechanism for sensitive healthcare information. This innovative system elevates healthcare data security to new heights, offering multiple advantages for providers and patients alike.
Reduced Data Breaches
Patient data security with blockchain provides unprecedented protection against cyber threats. Through networked information spreading, blockchain protects medical systems from instant simultaneous hacking attempts.
Enhanced Patient Trust
The security solutions built with blockchain empower patients to manage their health records at every level. Secure patient data management systems enable individuals to follow data access while they obtain and revoke access permissions instantly, which builds trust among patients.
Regulatory Compliance
Blockchain technology for healthcare data protection automatically ensures compliance with complex regulations. The system’s built-in protocols support HIPAA compliance with the blockchain network and evolve with worldwide privacy requirements to minimize costly noncompliance risks.
Streamlined Operations
Blockchain development solutions eliminate unnecessary intermediaries in healthcare processes. Healthcare providers can access medical information directly from decentralized systems, which increases operational speed and safeguards data security.
Cost Reduction
Healthcare institutions reduce their operational costs by using blockchain technology for automated record maintenance. The system’s digital maintenance of blockchain medical records decreases paperwork while creating possibilities for cost savings from storage expenses and removing verification manual tasks.
Challenges and Limitations of Blockchain in Healthcare
While blockchain technology in the medical industry offers revolutionary benefits, implementing these systems presents several significant hurdles. Healthcare organizations must carefully consider these challenges when adopting blockchain development solutions for their security needs.
Implementation Costs
Patient data security with blockchain requires a substantial initial investment. Healthcare buildings need to upgrade their physical framework, then provide continuous training for their workforce, and sustain new operating systems. Because of their limited resources, the establishment of blockchain medical records systems puts financial pressure on clinics and small hospitals.
Scalability Concerns
Healthcare data security faces growing pains as blockchain networks expand. More medical records inserted into the system tend to reduce processing speed and efficiency. Blockchain for healthcare data protection must balance increasing data volumes with maintaining efficient access speeds.
Regulatory Compliance
The deployment of decentralized healthcare requires organizations to solve multiple challenges arising from diverse regulatory requirements. Healthcare providers must establish blockchain applications in healthcare systems that observe evolving legal frameworks and HIPAA compliance requirements for blockchain standards.
Institutional Resistance
Standard organizations avoid adopting blockchain development for healthcare. Many fear that implementing new workflows would interrupt current business operations and want to use what is already familiar. Institutions’ unwillingness to embrace new patient data security initiatives causes delays in deploying secure management solutions.
System Integration
To succeed, healthcare cybersecurity solutions based on blockchain technology need to operate smoothly with existing legacy infrastructures. However, healthcare entities face technical hurdles when they combine new blockchain systems with their current infrastructure. Complex system requirements are a significant factor discouraging healthcare providers from implementing blockchain solutions for data breaches.
Future of Blockchain in Healthcare
Blockchain technology in the medical industry stands poised to revolutionize healthcare security and data management over the next decade. As patient data security with blockchain matures, we’ll see transformative changes in how healthcare organizations protect and share sensitive information.
2030 Adoption Predictions
- Over 60% of US hospitals will implement blockchain for healthcare data protection as their primary security solution.
- In 2030, blockchain medical records will be the standard storage solution for medical patient data, replacing traditional electronic health records.
- Healthcare insurance claims processing will be 90% automated through blockchain development solutions.
- Using blockchain for patient data management ensures a reduction of health data breaches below the 80% level.
- The implementation of decentralized healthcare models will reduce administrative expenses for the industry to an annual savings amount of $100 billion.
Emerging Trends
- A future version of smart contracts enables real-time detection of unauthorized intrusions through AI implementation.
- Quantum-resistant blockchain encryption will emerge to protect healthcare data security against future threats.
- Blockchain systems will be implemented in healthcare and synchronized with medical devices that are part of the Internet of Medical Things (IoMT).
- Such algorithms will help make drug supply chain verification systems based on blockchain more effective.
- Typical biometric authentication methods working with blockchain technology will improve organization-level access administration procedures.
Government Policy Development
- Federal government regulations will apply blockchain solutions to protect all healthcare facilities from data breaches.
- Medicare demands all its participating providers incorporating blockchain solutions must comply with HIPAA requirements.
- The implementation of healthcare cybersecurity solutions will receive motivation through governmental incentives operated at state and local levels.
- The Food and Drug Administration desires to develop standardized blockchain specification requirements for monitoring pharmaceutical distribution networks.
- Congress will define the national development standards of healthcare blockchain systems.
Global Healthcare Ecosystem
- International medical data-sharing protocols will use blockchain technology in the medical industry.
- Medical services provided across borders will utilize single blockchain infrastructures for operation.
- Standards-based blockchain frameworks serve to store and distribute worldwide clinical trial information.
- Drug verification systems operating at a global level will stop the circulation of counterfeit medication.
- A universal identification solution for patients will provide smooth global healthcare services.
Conclusion
Blockchain in healthcare revolutionizes patient data security by creating an unbreakable shield of protection. Healthcare data security reaches new heights through decentralized systems, while blockchain technology in the medical industry ensures transparent and tamper-proof record-keeping, transforming how we protect sensitive information.
Building a Safer Healthcare System
Blockchain Development Solutions empower healthcare organizations to create robust security frameworks, making patient data breaches virtually impossible while streamlining secure medical operations.
Exploring Blockchain Solutions
Healthcare organizations need to accept blockchain applications for healthcare purposes because these capabilities secure their cybersecurity systems and meet HIPAA requirements through blockchain system deployment.
Future Innovation Call
The medical sector needs to allocate resources to research on blockchain medical records development to establish new, secure patient data handling solutions and improve healthcare cybersecurity safeguards.
FAQs
How does blockchain technology improve patient data security in healthcare?
The patBlockchain protects patient data that is distributed through tamper-resistant ledger systems. The encryption system used in transactions creates registers that hackers cannot modify because of their extreme security. Smart contracts grant authorized users access to specific data by enforcing privacy and meeting all requirements established in HIPAA regulations. Healthcare systems build higher trust levels because blockchain reduces the occurrence of data breaches.
Benefits of using blockchain for healthcare data protection
The blockchain system delivers better security measures, transparent data operations, and unaltered record integrity. Its encryption methods and decentralized storage functionality stop unwanted intruders. Patients who access medical record control decrease their vulnerability to identity theft. The system also provides better data collaboration between healthcare providers, which results in superior medical diagnoses and improved treatment results.
What are the challenges of implementing blockchain in healthcare?
Implementing blockchain technology is problematic because it requires high prices to execute programs, struggles with large-scale operations, and requires compliance with health regulations. Integrating blockchain systems remains complicated because healthcare facilities operate with old infrastructure. Data interoperability and privacy issues require resolution to enable easy acceptance of the blockchain system.
How blockchain technology is revolutionizing healthcare data management
Blockchain technology facilitates healthcare evolution by creating secure data-sharing capabilities between healthcare organizations, insurers, and patients. The technology guarantees precise data information and prevents duplicate entries to combat fraud. Automating processes improves patient care, delivers better operational efficiency, and decreases operational expenses.
Future of blockchain in healthcare and patient data security
With advancements in AI-driven smart contracts and interoperability solutions, blockchain is extremely promising for the healthcare industry. As regulations advance, blockchain implementation will increase among healthcare institutions and insurance providers. Over the next few years, blockchain technology will standardize patient data protection and seamless healthcare operations.
The post Blockchain in Healthcare: Improving Patient Data Security appeared first on Cybersecurity Insiders.