Introduction to Password Security
Password security has seen dramatic shifts driven by the escalation of cyber threats and advancements in technology. Initially, simple passwords sufficed, but as cyberattacks evolved in complexity so did the need for robust password strategies. The rise of credential stuffing, brute force, and dictionary attacks necessitated a rethink in password management practices.
Historically, password policies emphasized complexity—combinations of letters, numbers, and symbols thought to fortify security. These policies often mandated frequent changes, assuming this would mitigate breach risks. However, research revealed such practices often resulted in predictable and weak passwords, like “Password1!,” which did little to deter sophisticated cybercriminals.
This shift in strategies is embodied in the National Institute of Standards and Technology’s (NIST) Special Publication 800-63B, which moves away from complexity and frequency of changes. Instead, it emphasizes password length and uniqueness, aligning with practical user management and reflecting a balance between security and usability.
Moreover, the adoption of NIST’s latest recommendations aligns password policies with real-world use cases and threat scenarios. It acknowledges that security is not just about creating barriers to unauthorized access but about building sustainable practices that enhance an organization’s cybersecurity posture while supporting operational efficiency.
NIST Password Guidelines
The latest iteration of NIST’s password guidelines in SP 800-63B introduces key recommendations designed to enhance password security while improving usability:
•Length Over Complexity
NIST emphasizes that passwords should prioritize length over complexity. A longer passphrase, which can include any characters including all Unicode characters, is more secure and easier for users to remember. The minimum recommended length is eight characters for standard users, with longer passphrases encouraged.
•No Requirement for Character Complexity
NIST no longer mandates the use of specific mixtures of character types (uppercase, lowercase, numbers, symbols). This change is to prevent the creation of predictable passwords that meet complexity requirements but are easy to guess.
•Discouragement of Frequent Password Changes
NIST advises against mandatory periodic password changes, previously a staple of security policies, unless there is evidence of a breach or similar security threat. This guideline is aimed at reducing password fatigue and discouraging the creation of predictable passwords.
•Screening Against Dynamic Blacklists
To improve password security, NIST recommends ongoing screening of new passwords against blacklists of known compromised passwords. This helps ensure that users do not choose passwords that have already been exposed in breaches.
•Use of Password Managers
NIST supports the use of reputable password managers to help users generate, store, and manage complex passwords efficiently. This recommendation is twofold: it decreases the likelihood of password reuse across accounts and facilitates the use of longer, more complex passwords by allowing users to copy and paste them as needed. This approach reduces the burden on memory and enhances security by making it easier to use unique passwords for different accounts.
Rationale Behind the Current Guidelines
The updates to NIST’s password guidelines are based on extensive research into user behavior and password policy effectiveness. Studies have consistently shown that traditional complexity requirements often led to predictable, easily guessed passwords. For instance, the inclusion of mandatory alphanumeric and symbol combinations typically resulted in patterns like “Password1!,” which did not enhance security
Further, the frequent mandate to change passwords often resulted in minor variations of previous passwords, adding little security benefit while increasing user frustration. Notably, research, including findings from Google and the Verizon DBIR, highlights the widespread issue of password reuse across personal and professional accounts, significantly heightening security risks.
These insights prompted NIST to shift their focus from complexity and frequent changes to longer passphrases that are both easier to remember and harder to guess, thereby improving realworld security and reducing the cognitive load on users. This approach acknowledges the limitations of human memory and the practical aspects of password use, aiming to foster more secure and manageable password practices.
Benefits of Following NIST Guidelines
Adopting NIST’s revised password guidelines offers several benefits:
•Enhanced Security
By focusing on length and discouraging complex but common password formulas, policies based on these guidelines are more likely to withstand typical password attacks like brute force and dictionary attacks.
•Improved Usability
Simpler guidelines that prioritize memorable passphrases over arbitrary complexity help reduce user frustration and lower the chances of security shortcuts, such as writing down passwords.
•Reduced Operational Burden
Eliminating routine password changes reduces the administrative overhead associated with managing user accounts and handling issues related to password resets and account lockouts.
Incorporating NIST’s guidelines helps organizations align with proven best practices that not only enhance security but also improve the user experience and administrative efficiency. Advanced solutions that integrate seamlessly with systems like Active Directory provide tools for real-time monitoring of password integrity and compliance with these guidelines. This approach not only adheres to NIST’s standards but also empowers organizations to proactively manage their cybersecurity risks.
Best Practices For NIST Compliant Password Security
In an era where cyber threats are increasingly sophisticated and pervasive, it is imperative for organizations to reassess and fortify their password security strategies. As the first line of defense against unauthorized access, effective password management is fundamental to safeguarding sensitive information and maintaining business continuity. This section outlines essential practices derived from NIST guidelines that are designed to fortify your security posture significantly. By adopting these practices, organizations can ensure robust protection against both current and emerging threats, creating a resilient and adaptable security environment.
Password Policy Development And Updating
1.Review and Enhance Password Policies
Conduct a thorough review of your existing password policies and align them with NIST’s latest guidelines. Focus on adopting practices that enhance password strength without compromising usability.
2.Encourage Strong, UserFriendly Passphrases
According to NIST guidelines, the key to strong passwords lies in their length and uniqueness, rather than complex and hard-to-remember combinations of characters. To comply with these standards, encourage the use of passphrases—sequences of words or other easily remembered strings of characters—which are both longer and easier to recall for users than traditional passwords. A best practice is to guide users to choose passphrases that are meaningful to them but hard to guess for others, avoiding common phrases, famous quotations, or sequences from widely accessible sources.
Implementation of Advanced Security Solutions
1.Leverage Password Managers
Password managers play a crucial role in maintaining robust password security by generating and storing complex passwords for users. These tools create a unique, strong password for each account, which users do not need to memorize. NIST supports the use of password managers, as they significantly reduce the risk of password reuse across multiple sites, a common vulnerability in personal and organizational security.
2.Integrate Security into Access Management Systems
Integrating NIST password guidelines into existing identity and access management systems such as Active Directory (AD) is crucial for maintaining consistent and enforceable security policies across an organization. Active Directory, used by organizations worldwide to manage network resources and services, is often targeted by cybercriminals due to its ubiquity. While AD provides a robust framework, it alone may not fully comply with the latest NIST guidelines without additional enhancements.
Advanced password automation solutions, like Enzoic for Active Directory, offer seamless integration and are essential for bringing AD into compliance with NIST standards. The solution provides features such as real-time password screening and compliance checks without disrupting existing user workflows, ensuring uniform application of password security measures across all user accounts.
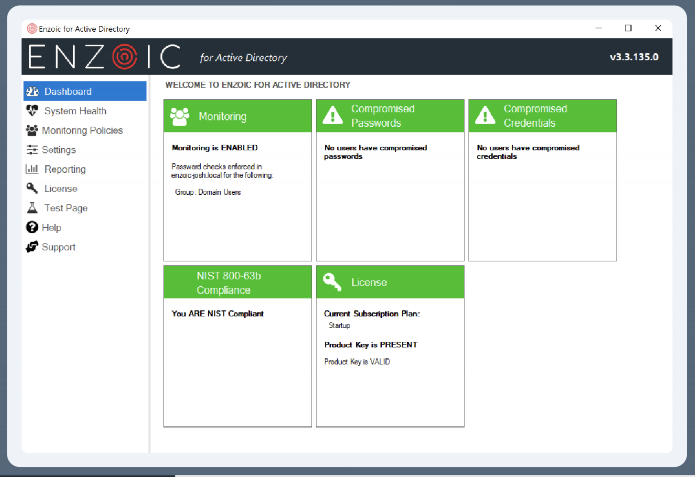
Enzoic actively checks if passwords are compromised at creation and continuously monitors them, updating checks against a daily-refreshed blacklist and automatically taking remediation steps when vulnerabilities are found. This ensures that compromised credentials are quickly addressed, significantly reducing security risks.
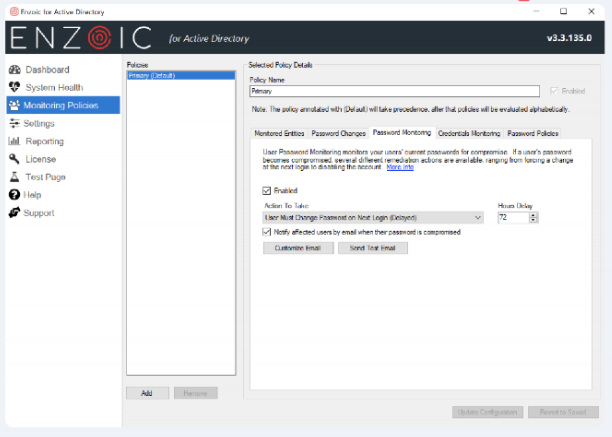
For organizations aiming to meet NIST requirements, solutions like Enzoic’s plugin make it possible to enforce a NIST-approved password policy effectively. With simple configurations such as a single checkbox to apply all NIST password policy options and a dashboard that alerts IT teams to any settings changes, these tools enhance security while improving the user experience within the Active Directory environment.
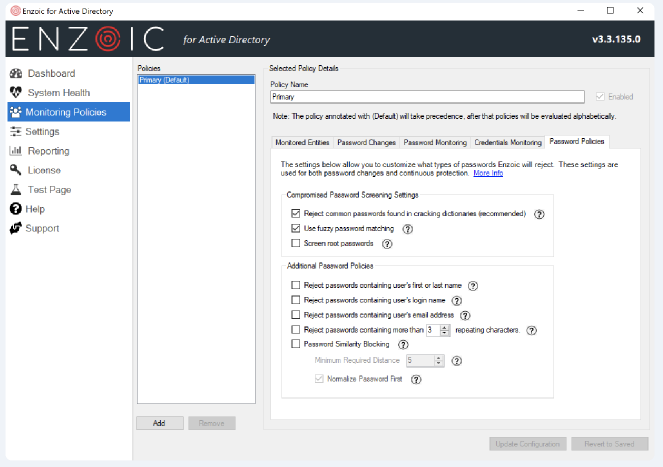
3.Activate Real-Time Password Screening
Screening passwords against known compromised credentials is crucial to maintaining the integrity of passwords. Utilizing dynamic blacklists that update in near real-time allows for the reflection of the latest data breaches and leaks, providing a robust defense against the rapidly changing landscape of exposed credentials. Real-time screening technology automates this process, checking new or changed passwords against continuously updated databases of compromised credentials to prevent the accidental use of already exposed passwords, thereby maintaining robust security standards and ensuring compliance with NIST guidelines.
4.Customize Password Screening with CompanySpecific Blacklists
In addition to using dynamic blacklists, organizations should enhance their password screening processes with context-specific terms, such as company names, product names, and industry-specific jargon that are likely to be used in passwords.
This list of highly predictable passwords can then be incorporated into the screening process, providing another layer of personalized security that anticipates potential attacker strategies. This targeted approach helps prevent the use of predictable passwords that attackers might exploit, thus fortifying the organization’s defenses against targeted attacks.
It’s also crucial to screen passwords not only against exact matches on blacklists but also for ‘fuzzy’ variations. Humans are highly predictable, and attackers know the typical patterns people use to satisfy complexity requirements. For example, a user might change ‘baseball’ to ‘Baseball1990!’ to meet complexity demands, mistakenly thinking this variation is secure. Advanced screening technology includes the capability to detect these common variations, further enhancing password security.
5.Implement Advanced Encryption for Password Storage
Secure password storage by employing advanced encryption methods like bcrypt, scrypt, or Argon2. These hashing functions incorporate salt and key stretching techniques to safeguard passwords stored in databases, rendering them useless to attackers even in the event of a data breach.
Ongoing Security Monitoring and Response
1.Implement Multi-Factor Authentication (MFA)
Adopt MFA to add an additional layer of security by requiring two or more verification methods, which significantly decreases the risk of unauthorized access. NIST recommends the use of MFA, as it complements strong password practices, providing an additional barrier against the exploitation of stolen or weak passwords. While MFA is an excellent compensating control, it should not be a replacement for securing passwords directly. As outlined in Microsoft’s 2023 Digital Defense Report, MFA is only successful at stopping 76% of targeted attacks, leaving a significant vulnerability.
2.Implement Continuous Password Monitoring
Continuous monitoring of passwords against breach databases is vital for maintaining secure credentials. With the vast array of credentials available on the dark web, it’s crucial that monitoring is not just periodic but ongoing.
Password security automation can provide continuous monitoring by checking passwords at least once every 24 hours against the latest breach databases, ensuring that any compromised passwords are quickly identified. This monitoring is essential for meeting the NIST guideline that mandates changing passwords following a compromise. Such proactive monitoring can significantly mitigate the risk of a data breach, maintaining the integrity of user credentials at all times.
Ensure the solution offers real-time password monitoring and screening, which checks passwords against updated threat intelligence as they are set or changed. This should include the capability to intercept passwords at the moment of creation or reset, comparing them against an extensive database of exposed credentials. The ideal solution sends only hashed parts of passwords to maintain privacy and security, using efficient algorithms to reduce latency in checks.
3.Automate Remediation for Compromised Credentials
When compromised credentials are detected, the speed of response is crucial to minimize potential damage. Advanced password security platforms enable organizations to customize the remediation actions taken. These actions might include alerting the user, forcing a password reset, or temporarily disabling the account and flagging the issue for IT team intervention.
This level of automation ensures that compromised credentials are dealt with promptly, reducing the window of vulnerability and risk of data breaches. This flexibility allows organizations to balance security needs with user convenience, ensuring that security measures do not unduly hinder productivity.
Workforce Education and Empowerment
1.Educate Employees on Secure Password Practices
Regularly educate your employees about the importance of secure password practices and highlight the specific steps they can take to protect both their personal and professional information.
2.Embrace User-Centric Password Policies
Many organizations find that switching from frequent password changes to more user-centric models is remarkably smooth and requires no adjustment period.
This transition is not just a technological update but also a positive shift in organizational culture and user behavior.
User-centric password policies focus on creating a more intuitive and user-friendly security environment. Instead of imposing frequent password changes that can be cumbersome and frustrating for users, these policies advocate for more memorable and secure password practices. According to NIST’s guidelines, encouraging the use of longer, more complex passwords (that do not require regular changes unless there is evidence of compromise) can significantly enhance both security and user satisfaction.
Implementing this change can be seamless, with minimal disruption to user workflows. A direct shift can be made wherein users no longer need to reset their passwords periodically. Most users will likely not notice the change, yet they will benefit from the elimination of periodic resets. This approach not only enhances user convenience but also improves overall security compliance by reducing the likelihood of predictable password patterns and password fatigue.
By taking these steps, organizations can ensure they are not only compliant with the highest standards of password security but are also equipped to defend against the evolving landscape of cyber threats. Review, update, and fortify—your proactive steps today will define your security posture tomorrow.
“After deploying Enzoic for Active Directory, Hylan was able to follow NIST standards, and eliminate all compromised passwords from our Active Directory environment. The installation process took only one hour across our eight domain controllers. This project allowed us to improve enterprise security and reduce helpdesk resources dedicated to passwords by 90%” -NZOIC CUSTOMER: Ramon Diaz Director of IT Hyla
Key Benefits of Automating Password Policies
Password security automation brings a host of benefits that enhance the overall security framework, ensure compliance, and streamline operations:
Real-Time Protection – Automating the screening of passwords against updated blacklists and other security rules means that new and reset passwords are immediately checked for vulnerabilities. This reduces the window of opportunity for attackers to exploit weak or compromised credentials
Consistency and Compliance – Automated enforcement of password policies ensures that all users consistently follow the same security guidelines across an organization. This uniformity helps maintain high security standards and simplifies compliance with industry regulations.
Enhanced Detection and Response – Automated systems can quickly identify and respond to security issues without waiting for manual intervention. For instance, if a password is found on a blacklist, the system can automatically prompt the user to change it, thus minimizing potential security risks.
Operational Efficiency and Cost Savings – Automation significantly reduces the manual effort required to enforce password policies and monitor compliance. By automating routine tasks such as password resets, organizations can allocate resources more effectively, potentially leading to cost savings in IT operations. It lowers administrative costs by reducing the number of password reset calls and automating remediation, further enhancing operational efficiency.
Improved User Experience – By eliminating complex password composition rules and reducing the frequency of mandatory password resets, automation greatly enhances user satisfaction. This leads to smoother interaction with IT systems and encourages better compliance with security practices, making security management both user-friendly and effective.
The broader impact of automating NIST-compliant password policies is substantial, offering both operational advantages and significant enhancements to an organization’s cybersecurity posture. By reducing administrative overhead, improving user satisfaction, and strengthening defenses, policy automation not only supports compliance but also drives better security practices that protect organizations against emerging cyber threats.
As organizations continue to face a landscape marked by sophisticated cyberattacks, adopting and implementing NIST’s password guidelines with the support of automated password security tools can provide a critical edge in maintaining robust, effective defenses.
CONCLUSION
Fortify Your Cybersecurity with Proactive Password Security Management
As we wrap up this CISO guide on NIST-compliant password security, it’s evident that robust password policies are crucial for safeguarding digital assets against sophisticated cyber threats. Adopting NIST guidelines enhances security and usability by prioritizing password length and uniqueness over complexity, which increases user compliance and reduces administrative burdens.
The integration of advanced security solutions like real-time monitoring, dynamic blacklisting, and seamless Active Directory integration ensures practical enforceability of these policies. Furthermore, a culture of continuous improvement—supported by regular audits, user education, and phased practice updates—helps organizations stay ahead of emerging threats and create a resilient and adaptable security environment.
Commit to these best practices today to safeguard your digital assets tomorrow, ensuring your cybersecurity measures evolve with the threat landscape.
The post Ciso Guide To Password Security – How to Implement and Automate Key Elements of NIST 800-63B appeared first on Cybersecurity Insiders.