In the summer of 2022, KrebsOnSecurity documented the plight of several readers who had their accounts at big-three consumer credit reporting bureau Experian hijacked after identity thieves simply re-registered the accounts using a different email address. Sixteen months later, Experian clearly has not addressed this gaping lack of security. I know that because my account at Experian was recently hacked, and the only way I could recover access was by recreating the account.
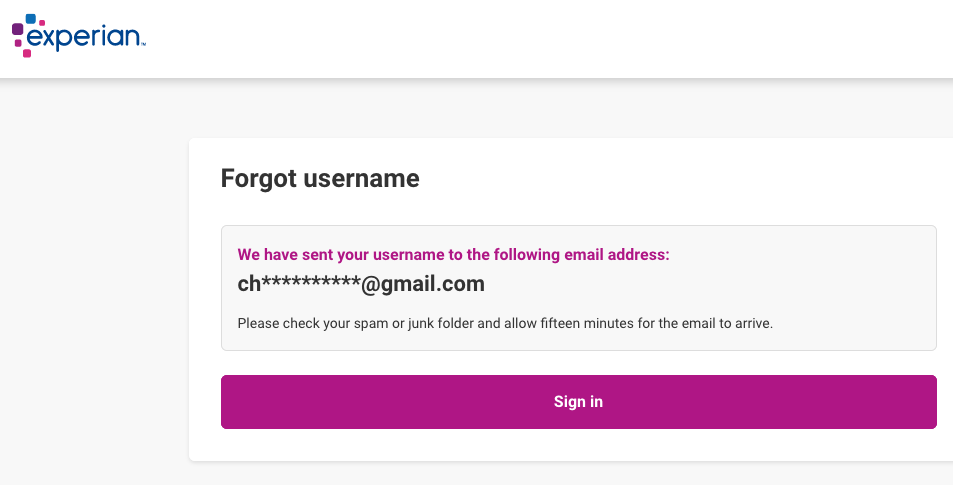
Entering my SSN and birthday at Experian showed my identity was tied to an email address I did not authorize.
I recently ordered a copy of my credit file from Experian via annualcreditreport.com, but as usual Experian declined to provide it, saying they couldn’t verify my identity. Attempts to log in to my account directly at Experian.com also failed; the site said it didn’t recognize my username and/or password.
A request for my Experian account username required my full Social Security number and date of birth, after which the website displayed portions of an email address I never authorized and did not recognize (the full address was redacted by Experian).
I immediately suspected that Experian was still allowing anyone to recreate their credit file account using the same personal information but a different email address, a major authentication failure that was explored in last year’s story, Experian, You Have Some Explaining to Do. So once again I sought to re-register as myself at Experian.
The homepage said I needed to provide a Social Security number and mobile phone number, and that I’d soon receive a link that I should click to verify myself. The site claims that the phone number you provide will be used to help validate your identity. But it appears you could supply any phone number in the United States at this stage in the process, and Experian’s website would not balk. Regardless, users can simply skip this step by selecting the option to “Continue another way.”
Experian then asks for your full name, address, date of birth, Social Security number, email address and chosen password. After that, they require you to successfully answer between three to five multiple-choice security questions whose answers are very often based on public records. When I recreated my account this week, only two of the five questions pertained to my real information, and both of those questions concerned street addresses we’ve previously lived at — information that is just a Google search away.
Assuming you sail through the multiple-choice questions, you’re prompted to create a 4-digit PIN and provide an answer to one of several pre-selected challenge questions. After that, your new account is created and you’re directed to the Experian dashboard, which allows you to view your full credit file, and freeze or unfreeze it.
At this point, Experian will send a message to the old email address tied to the account, saying certain aspects of the user profile have changed. But this message isn’t a request seeking verification: It’s just a notification from Experian that the account’s user data has changed, and the original user is offered zero recourse here other than to a click a link to log in at Experian.com.
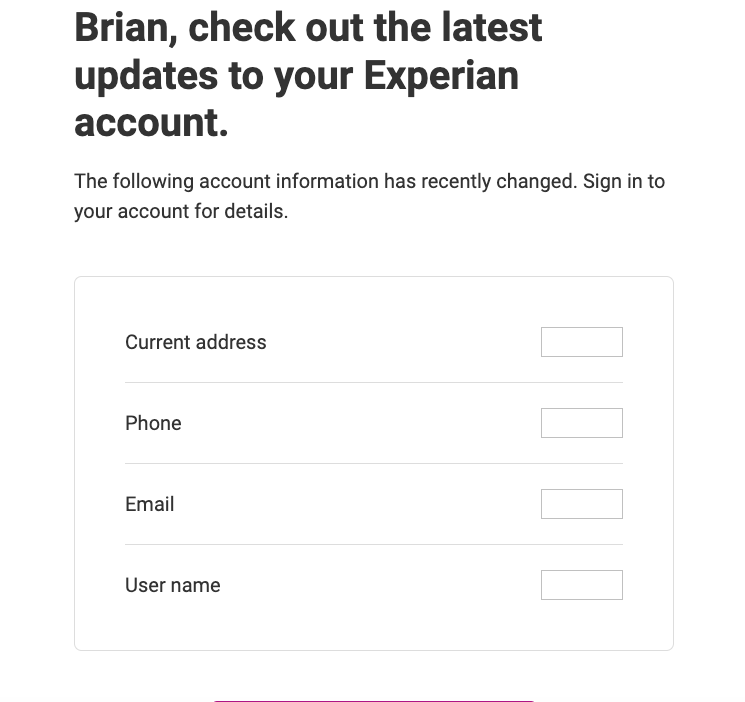
If you don’t have an Experian account, it’s a good idea to create one. Because at least then you will receive one of these emails when someone hijacks your credit file at Experian.
And of course, a user who receives one of these notices will find that the credentials to their Experian account no longer work. Nor do their PIN or account recovery question, because those have been changed also. Your only option at this point is recreate your account at Experian and steal it back from the ID thieves!
In contrast, if you try to modify an existing account at either of the other two major consumer credit reporting bureaus — Equifax or TransUnion — they will ask you to enter a code sent to the email address or phone number on file before any changes can be made.
Reached for comment, Experian declined to share the full email address that was added without authorization to my credit file.
“To ensure the protection of consumers’ identities and information, we have implemented a multi-layered security approach, which includes passive and active measures, and are constantly evolving,” Experian spokesperson Scott Anderson said in an emailed statement. “This includes knowledge-based questions and answers, and device possession and ownership verification processes.”
Anderson said all consumers have the option to activate a multi-factor authentication method that’s requested each time they log in to their account. But what good is multi-factor authentication if someone can simply recreate your account with a new phone number and email address?
Several readers who spotted my rant about Experian on Mastodon earlier this week responded to a request to validate my findings. The Mastodon user @Jackerbee is a reader from Michican who works in the biotechnology industry. @Jackerbee said when prompted by Experian to provide his phone number and the last four digits of his SSN, he chose the option to “manually enter my information.”
“I put my second phone number and the new email address,” he explained. “I received a single email in my original account inbox that said they’ve updated my information after I ‘signed up.’ No verification required from the original email address at any point. I also did not receive any text alerts at the original phone number. The especially interesting and egregious part is that when I sign in, it does 2FA with the new phone number.”
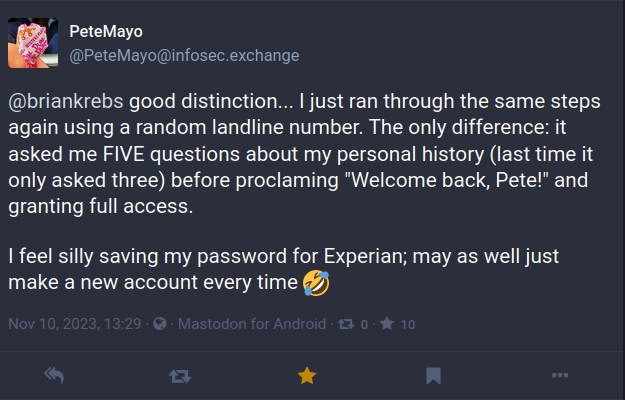
The Mastodon user PeteMayo said they recreated their Experian account twice this week, the second time by supplying a random landline number.
“The only difference: it asked me FIVE questions about my personal history (last time it only asked three) before proclaiming, ‘Welcome back, Pete!,’ and granting full access,” @PeteMayo wrote. “I feel silly saving my password for Experian; may as well just make a new account every time.”
I was fortunate in that whoever hijacked my account did not also thaw my credit freeze. Or if they did, they politely froze it again when they were done. But I fully expect my Experian account will be hijacked yet again unless Experian makes some important changes to its authentication process.
It boggles the mind that these fundamental authentication weaknesses have been allowed to persist for so long at Experian, which already has a horrible track record in this regard.
In December 2022, KrebsOnSecurity alerted Experian that identity thieves had worked out a remarkably simple way to bypass its security and access any consumer’s full credit report — armed with nothing more than a person’s name, address, date of birth, and Social Security number. Experian fixed the glitch, and acknowledged that it persisted for nearly seven weeks, between Nov. 9, 2022 and Dec. 26, 2022.
In April 2021, KrebsOnSecurity revealed how identity thieves were exploiting lax authentication on Experian’s PIN retrieval page to unfreeze consumer credit files. In those cases, Experian failed to send any notice via email when a freeze PIN was retrieved, nor did it require the PIN to be sent to an email address already associated with the consumer’s account.
A few days after that April 2021 story, KrebsOnSecurity broke the news that an Experian API was exposing the credit scores of most Americans.
More greatest hits from Experian:
2022: Class Action Targets Experian Over Account Security
2017: Experian Site Can Give Anyone Your Credit Freeze PIN
2015: Experian Breach Affects 15 Million Customers
2015: Experian Breach Tied to NY-NJ ID Theft Ring
2015: At Experian, Security Attrition Amid Acquisitions
2015: Experian Hit With Class Action Over ID Theft Service
2014: Experian Lapse Allowed ID Theft Service Access to 200 Million Consumer Records
2013: Experian Sold Consumer Data to ID Theft Service


