Virtual Private Networks (VPNs) have long been the standard technology for remote access, multi-site connectivity, and third-party access. However, recent trends in cloud adoption and remote work have exposed significant weaknesses in VPN security. This article examines the transition from VPNs to Zero Trust Network Access (ZTNA) and its implications for cybersecurity, drawing insights from the 2024 Zscaler VPN Risk Report and an in-depth interview with Deepen Desai, Chief Security Officer and SVP Security Engineering & Research at Zscaler.
The Decline of VPNs: A Vulnerable Legacy
VPNs have been the cornerstone of remote access for decades, allowing users to connect securely to corporate networks from anywhere in the world. They provide essential functionalities such as remote connectivity, multi-site connectivity, and third-party access.
“More than 70% of the use cases for VPNs are around remote access,” Desai noted. “In cases of mergers and acquisitions, companies often set up site-to-site VPNs, which can inherit security issues from the other side. Third-party access, although less common, poses even greater risks.”
However, as Desai pointed out in the interview, these legacy architectures are increasingly proving to be liabilities. According to the report, a whopping 56% of organizations experienced VPN-related cyberattacks in the past year, an 11% increase from the previous year. And more than half of enterprises breached via VPN vulnerabilities (54%) experienced lateral movement by threat actors.
“The legacy architecture of VPNs, which grants broad network access once credentials are verified, significantly increases the risk of lateral movement by attackers within the network,” says Deepen Desai. “This means that once an attacker gains access through a compromised VPN, they can move laterally across the network, accessing and exfiltrating sensitive data with relative ease.”
Critical Vulnerabilities: If You’re Reachable, You’re Breachable
One of the primary issues with VPNs is their susceptibility to zero-day vulnerabilities. Recent high-profile exploits, such as CVE-2023-46805 and CVE-2024-21887, have exposed critical weaknesses in VPN products. The recent Ivanti VPN attacks, for example, exploited zero-day vulnerabilities in Ivanti Connect Secure appliances, allowing threat actors to implant web shells and harvest credentials. These breaches enabled attackers to bypass authentication, execute commands with elevated privileges, move laterally within networks and maintain root-level persistence, even after device resets. In response, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued emergency directives for federal agencies to disconnect affected devices, highlighting the severity of these vulnerabilities. Forensic analysis revealed that attackers could even evade detection by modifying internal integrity checks, creating a false sense of security among users.
In general, VPNs are vulnerable to zero-day vulnerabilities and other attacks, in part, because they are externally exposed, internet-facing devices with public IP addresses. This means that attackers can easily scan for and exploit these vulnerabilities in exposed VPNs. As a result, VPNs exposure substantially increase the enterprise attack surface, while exposing enterprise servers and networks to the internet — all of which increases the chances of attacks like ransomware.
Ransomware and Other Threats
Ransomware actors are particularly adept at exploiting VPN vulnerabilities. Deepen explained that ransomware groups often target VPNs to gain initial access to a network, move laterally, and deploy their ransomware payloads. The 2024 VPN Risk Report identifies ransomware (56%), malware infections (35%), and DDoS attacks (30%) as the top threats exploiting VPN vulnerabilities. These statistics underscore the breadth of risks that organizations face due to the inherent weaknesses of traditional VPN architectures.
“In the last twelve months, we’ve seen more threat actors going after zero-day vulnerability exploits in some of the popular VPN providers,” Desai emphasized. “The zero-day vulnerabilities have become a prominent issue, with several CISA advisories also confirming this trend.”
The Shift to Zero Trust Network Access
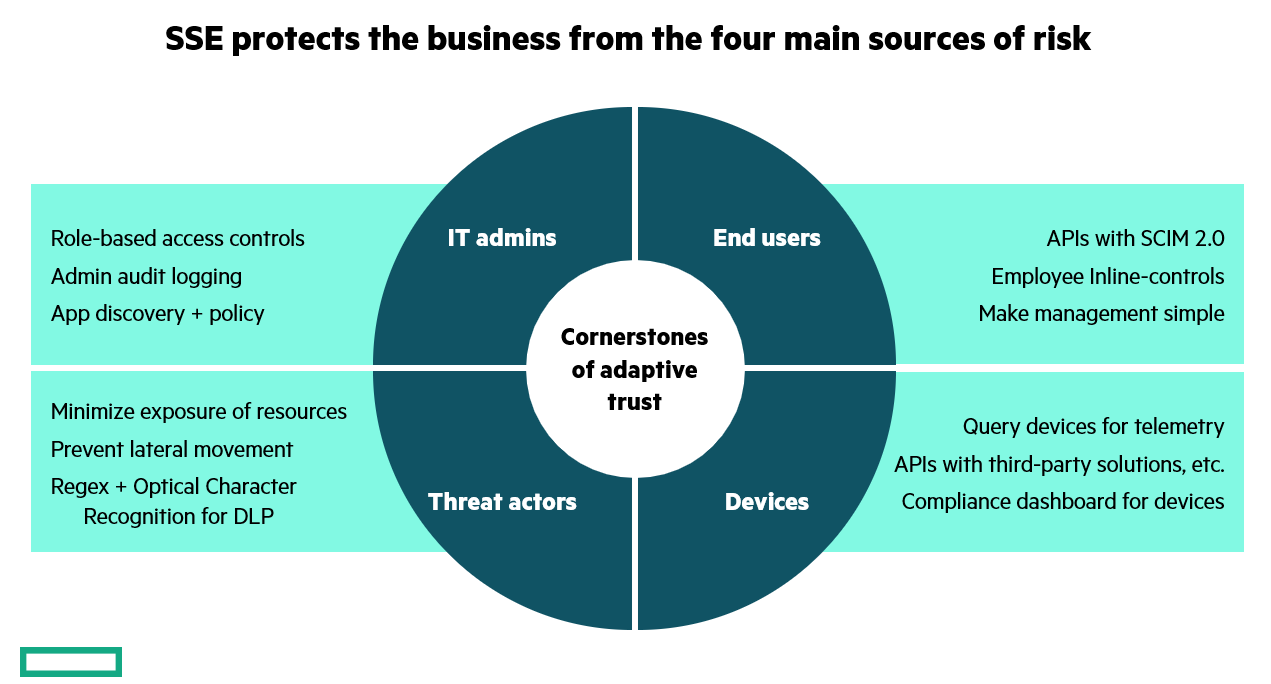
As the limitations and vulnerabilities of VPNs become increasingly apparent, more organizations are turning to Zero Trust Network Access (ZTNA) as a more secure and robust technology. Zero Trust is built on the principle of “never trust, always verify,” meaning that no user or device is trusted by default, whether inside or outside the network. Every access request is authenticated, authorized, and encrypted.
“Zero Trust is fundamentally different from VPNs in that it does not inherently trust any user or device,” Desai points out. “Every access request is scrutinized, authenticated, and authorized, which drastically reduces the attack surface.”
The 2024 VPN Risk Report reveals that 78% of organizations plan to implement Zero Trust strategies within the next 12 months, with 62% recognizing that VPNs are fundamentally anti-zero trust. This dramatic shift is driven by the need for a security framework that can effectively address the dynamic and evolving threat landscape and overcome the risks associated with legacy VPN technology.
Principles of Zero Trust
Zero Trust is a comprehensive security strategy built on several key principles:
1.Never Trust, Always Verify: Every access request, regardless of its origin, is subject to strict verification processes. This principle ensures that only authorized users and devices can access network resources.
2.Least Privilege Access: Users are granted only the minimum level of access necessary to perform their tasks. This minimizes the potential damage that could be caused by a compromised account.
3.Assume Breach: Zero Trust systems are designed with the assumption that breaches will inevitably occur. This approach focuses on limiting the blast radius of any potential attack by ensuring that even if an attacker gains access, their ability to move laterally within the network is severely restricted.
Granular Access Control
One of the most significant advantages of Zero Trust Network Access solutions over VPNs is the ability to provide smart, granular access control. Zero Trust also ensures that users connect directly to applications rather than the network, further reducing the risk of lateral movement and minimizing the potential impact of a breach. This level of control is crucial in today’s complex digital environments, where traditional perimeter-based security models are no longer sufficient.
Scalability and Performance
Unlike VPNs, which often struggle to scale and maintain performance under the load of a fully remote workforce, Zero Trust architectures are designed to be inherently scalable. Desai highlighted that during the COVID-19 pandemic, many organizations found their VPNs unable to handle the sudden shift to 100% remote work. With remote and hybrid work becoming the norm, Zero Trust solutions, in contrast, can scale seamlessly to support a distributed workforce without the performance bottlenecks associated with VPNs.
Zscaler’s Approach to Zero Trust
Zscaler’s Zero Trust Exchange platform is a prime example of how Zero Trust can be effectively implemented to protect modern enterprises and provide secure, direct connections between users and applications, eliminating the need for traditional network-based access. Desai outlined Zscaler’s phased approach to implementing Zero Trust, which involves four key stages:
1.Reduce Attack Surface: The first step in the Zero Trust journey is to reduce the external attack surface by making applications invisible to the internet. Zscaler achieves this by hiding applications behind the Zero Trust Exchange, ensuring that they are not directly accessible from the internet and can’t be discovered by probing missions. This significantly reduces the risk of external attacks.
2.Prevent Compromise: The next step is to prevent initial compromises by applying consistent security policies across all user environments. Whether users are remote, in the office, or traveling, the same set of security controls and policies should always follow them. Zscaler provides advanced threat protection and full TLS inspection to detect and block threats before they can cause harm.
3.Prevent Lateral Movement: To prevent attackers from moving laterally within the network, Zscaler employs granular user-to-application segmentation. This ensures that users are never placed on the same network as the applications they access. By doing so, Zscaler eliminates the risk of lateral movement, as there are no network paths for attackers to exploit.
4.Prevent Data Loss: Finally, Zscaler’s Data Loss Prevention (DLP) solutions ensure that sensitive data does not leave the organization. By performing inline DLP policy controls and full TLS inspection, Zscaler can detect and block attempts to exfiltrate sensitive information.
Implementing Zero Trust: Best Practices
Transitioning from VPN to Zero Trust requires careful planning and execution. Desai recommends a phased approach, starting with the most critical applications and high-risk users. Here are some best practices he recommends for implementing Zero Trust:
1. Identify Mission-Critical Applications: Begin by securing the applications that are most critical to your organization. These ‘crown jewel’ applications should be the first to be protected by Zero Trust principles.
2. Focus on High-Risk Users: High-risk users, such as those who frequently fail phishing simulations or have access to sensitive information, should be given priority in the Zero Trust implementation process. Implement strict access controls and continuous monitoring for these users.
3. Apply Zero Trust Principles Consistently: Ensure that Zero Trust policies are consistently applied across all environments, whether users are remote, in-office, or mobile. This uniformity is crucial for maintaining a robust security posture.
4. Educate and Train Users: Finally, user education is a critical component of any security strategy. Ensure that users understand the principles of Zero Trust and the importance of adhering to security policies.
“Zero Trust is a journey, rather than a starting place, particularly for large organizations with diverse IT environments,” Desai acknowledges. “However, a phased approach, starting with mission-critical applications and high-risk users or use cases, like VPN replacement, can help manage this complexity and ensure a smoother transition.”
The Future of Secure Access
The evolution from traditional VPNs to Zero Trust Network Access marks a significant shift in the cybersecurity landscape. As organizations face increasingly sophisticated cyber threats, the limitations of VPNs have become evident. Zero Trust offers a comprehensive approach to security by meticulously verifying access requests, enforcing least privilege principles, providing granular access control, and continuously monitoring user activity while mitigating long-term costs and increasing ROI.
By adopting Zero Trust, organizations can enhance their security posture and protect sensitive data. As Deepen Desai summarized, “Organizations must move away from remote access VPN solutions, especially for crown jewel applications, to reduce risk and enhance security. Zero Trust is not a single technology but a strategy that requires comprehensive implementation across all user environments.”
The post The Evolution of Secure Access: The Shift from VPNs to Zero Trust Network Access appeared first on Cybersecurity Insiders.