Category: LinkedIn
LinkedIn Used by Scammers to Distribute Malware: A New Threat
LinkedIn, a leading platform for professional networking, is now being exploited by scammers to spread a malware known as Covertcatch. Mandiant, a security firm owned by Google, has uncovered that North Korean hackers are using LinkedIn to target individuals with fake job offers, leading them to download this malicious software.
The scheme is straightforward- scammers connect with potential victims, engage them in conversation, and then persuade them to download a file disguised as a Python Coding Challenge. While LinkedIn is a common target for various types of cybercrime, it’s noteworthy that many affected systems have been MacOS devices.
To combat these threats, LinkedIn is employing AI-based threat detection tools to alert users of potential risks. Despite these measures, some users still fall victim to these sophisticated scams.
Quishing Attacks Target Electric Vehicle Users
In addition to LinkedIn scams, there’s a rising threat known as “Quishing,” which affects electric vehicle (EV) users. As many EV charging stations offer QR codes for payment, fraudsters have begun placing counterfeit QR codes that redirect payments to their own accounts or lead users to fraudulent payment gateways. These fake QR codes can also download malware onto users’ devices.
With the increasing reliance on digital payments and QR codes, it’s essential to stay vigilant. Here are some tips to protect yourself from Quishing attacks:
1. Inspect EV Stations: Check for any signs of tampering at charging stations before scanning QR codes for payment.
2. Verify Payment Details: Ensure the banking name on the payment application matches the charging station’s information.
3. Avoid Sensitive Data: Refrain from entering personal or banking details on unfamiliar or suspicious websites.
4. Update Your App: Keep your EV charging app updated with the latest software patches.
5. Report Issues: Immediately report any discrepancies to the charging station authorities and law enforcement.
By following these precautions, you can better safeguard yourself against these emerging threats.
What are your thoughts on these evolving cybersecurity challenges?
The post Malware spread via LinkedIn and EV Charging Stations prone to Quishing Attacks appeared first on Cybersecurity Insiders.
Many organizations — including quite a few Fortune 500 firms — have exposed web links that allow anyone to initiate a Zoom video conference meeting as a valid employee. These company-specific Zoom links, which include a permanent user ID number and an embedded passcode, can work indefinitely and expose an organization’s employees, customers or partners to phishing and other social engineering attacks.

Image: @Pressmaster on Shutterstock.
At issue is the Zoom Personal Meeting ID (PMI), which is a permanent identification number linked to your Zoom account and serves as your personal meeting room available around the clock. The PMI portion forms part of each new meeting URL created by that account, such as:
zoom.us/j/5551112222
Zoom has an option to include an encrypted passcode within a meeting invite link, which simplifies the process for attendees by eliminating the need to manually enter the passcode. Following the previous example, such a link might look something like this:
zoom.us/j/5551112222/pwd=jdjsklskldklsdksdklsdkll
Using your PMI to set up new meetings is convenient, but of course convenience often comes at the expense of security. Because the PMI remains the same for all meetings, anyone with your PMI link can join any ongoing meeting unless you have locked the meeting or activated Zoom’s Waiting Room feature.
Including an encrypted passcode in the Zoom link definitely makes it easier for attendees to join, but it might open your meetings to unwanted intruders if not handled responsibly. Particularly if that Zoom link is somehow indexed by Google or some other search engine, which happens to be the case for thousands of organizations.
Armed with one of these links, an attacker can invite others using the identity of the authorized employee. And many companies using Zoom have made it easy to find recently created meeting links that include encrypted passcodes, because they have dedicated subdomains at Zoom.us.
Using the same method, KrebsOnSecurity also found working Zoom meeting links for The National Football League (NFL), Warner Bros, and Uber. And that was from just a few minutes of searching. And to illustrate the persistence of some of these Zoom links, Archive.org says several of the links were first created as far back as 2020 and 2021.
KrebsOnSecurity received a tip about the Zoom exposures from Charan Akiri, a researcher and security engineer at Reddit. In April 2023, this site featured research by Akiri showing that many public Salesforce websites were leaking private data, including banks and healthcare organizations (Akiri said Salesforce also had these open Zoom meeting links before he notified them).
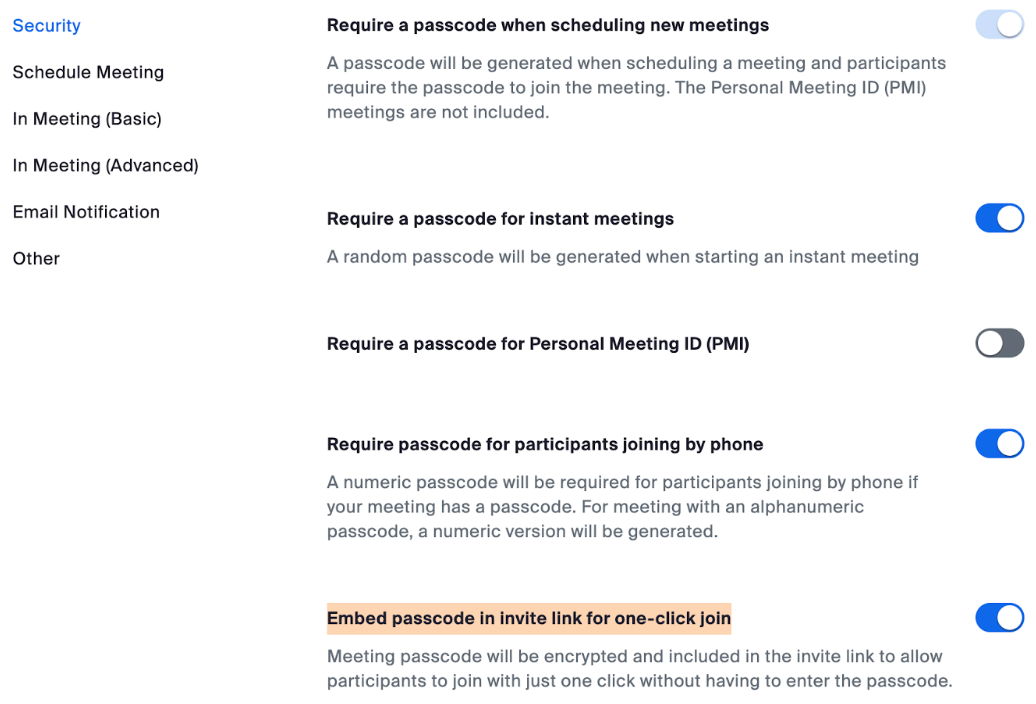
The Zoom links that exposed working meeting rooms all had enabled the highlighted option.
Charan said the misuse of PMI links, particularly those with passcodes embedded, can give unauthorized individuals access to meetings.
“These one-click links, which are not subject to expiration or password requirement, can be exploited by attackers for impersonation,” Charan said. “Attackers exploiting these vulnerabilities can impersonate companies, initiating meetings unknowingly to users. They can contact other employees or customers while posing as the company, gaining unauthorized access to confidential information, potentially for financial gain, recruitment, or fraudulent advertising campaigns.”
Akiri said he built a simple program to crawl the web for working Zoom meeting links from different organizations, and so far it has identified thousands of organizations with these perfectly functional zombie Zoom links.
According to Akiri, here are several tips for using Zoom links more safely:
Don’t Use Personal Meeting ID or Public Meetings: Your Personal Meeting ID (PMI) is the default meeting that launches when you start an ad hoc meeting. Your PMI doesn’t change unless you change it yourself, which makes it very useful if people need a way to reach you. But for public meetings, you should always schedule new meetings with randomly generated meeting IDs. That way, only invited attendees will know how to join your meeting. You can also turn off your PMI when starting an instant meeting in your profile settings.
Require a Passcode to Join: You can take meeting security even further by requiring a passcode to join your meetings. This feature can be applied to both your Personal Meeting ID, so only those with the passcode will be able to reach you, and to newly scheduled meetings. To learn all the ways to add a passcode for your meetings, see this support article.
Only Allow Registered or Domain Verified Users: Zoom can also give you peace of mind by letting you know exactly who will be attending your meeting. When scheduling a meeting, you can require attendees to register with their email, name, and custom questions. You can even customize your registration page with a banner and logo. By default, Zoom also restricts participants to those who are logged into Zoom, and you can even restrict it to Zoom users whose email address uses a certain domain.
In recent times, our focus has been on reporting the aftermath of cyber attacks and the challenges faced by their victims. In this article, we will shift our attention to the cyber attacks that have left a significant impact on millions and billions of online accounts.
1.) Yahoo: Back in September 2018, Yahoo, a pioneer in the world of online search engines, made a troubling announcement. A cyber incident had occurred, resulting in a massive data breach that exposed information from over 3 billion user accounts. It was later revealed that hackers had gained access to data stored on the servers between August 2013 and December 2016. This breach dealt a severe blow to the company’s reputation, prompting its potential buyer, Verizon, to negotiate a lower acquisition price. This incident also led to the resignation of the then-CEO, Marissa Mayer, following the acquisition process.
2.) Aadhaar: Early in 2018, the Indian government faced a significant embarrassment when several media outlets reported that a hacking group had successfully infiltrated and stolen data from over 1.1 billion UIDAI (Unique Identification Authority of India) accounts. Although the Indian Parliament dismissed these claims as sensationalized journalism, some security experts corroborated that the incident had indeed exposed biometric information.
3.) Alibaba Data Theft: The year 2020 witnessed a troubling incident involving Chinese e-commerce giant Alibaba. A developer managed to illicitly access and steal information from a staggering 1.1 billion Alibaba customers using a crawler software. Reports circulated that the developer, in collusion with a marketing company, orchestrated this data collection over an 8-month period. However, it was later clarified that the compromised data pertained to the shopping website Taobao and had no direct connection to Alibaba itself.
4.) LinkedIn: Known as a professional networking platform, LinkedIn became the subject of headlines when data linked to approximately 700 million users appeared for sale on the dark web in June 2021. Subsequent investigations uncovered that the data originated from a marketing firm that had scraped information from LinkedIn users spanning the years 2009 to 2020. Contrary to initial reports, this dataset was not fresh, new information.
5.) Facebook: In May 2021, Facebook, under the leadership of Mark Zuckerberg, found itself in the news as data from 533 million users surfaced on the dark web. Troy Hunt of HaveIBeenPwned and his research team revealed that this information had been harvested between 2017 and 2019 from the platform. The compromised data encompassed account names, phone numbers, and Facebook IDs. The fate of this data—whether it was sold on the dark web for potential phishing attacks—remains uncertain.
6.) Marriott International: Luxury hotel chain Marriott International faced a significant breach in September 2018, as details emerged about hackers accessing data from over 500 million Starwood customers. This sophisticated attack, traced back to unauthorized parties since 2014, led to the exposure of information such as mailing addresses, names, phone numbers, email addresses, passport numbers, Starwood Preferred Guest account particulars, dates of birth, gender details, guest arrival and departure specifics, as well as reservation details including itineraries derived from transportation service data.
7.) Adult Friend Finder: Making headlines in October 2016, hackers executed an unexpected breach, compromising data from users of Adult Friend Finder across six databases that had been collecting information since 2001. In November 2016, LeakedSource.com published data relating to over 413 million accounts, which was subsequently purchased by a representative from an adult-oriented company in March 2020.
8.) MySpace: In 2016, MySpace came under scrutiny as hackers successfully exfiltrated data from more than 360 million accounts. The stolen data was later sold for 6 BTC in 2017, a fact confirmed by LeakedSource.com.
9.) NetEase: The year 2015 witnessed a significant data breach affecting email service provider NetEase. It was estimated at that time that the company suffered a loss of data pertaining to approximately 235 million accounts. This compromised data was ultimately procured by a vendor named DoubleFlag from the dark web.
10. Adobe: In October 2013, American software services provider Adobe issued a disconcerting statement. Hackers had managed to pilfer information from over 153 million user accounts, including some credit card data and login credentials. The company faced consequences for failing to safeguard user data, resulting in a penalty of $1.1 million for violating customer records regulations. In an effort to avert legal complications, Adobe subsequently released an official statement confirming a settlement of $1 million with its affected customers.
The post Cyber Attacks that impacted billions and millions of online accounts appeared first on Cybersecurity Insiders.
LinkedIn users are advised to prioritize enhancing the security of their accounts, given recent incidents in which several individuals in the tech community have experienced unauthorized access by hackers over the past two months. Hackers are showing no restraint in selecting targets, as any successfully compromised account can lead to financial gains for them.
Typically, such breaches result in account takeovers, granting cybercriminals the ability to alter contact information such as phone numbers and email addresses. This enables them to exploit the compromised accounts for malicious intentions.
According to a report released by Cyberint, a considerable number of LinkedIn users in the western regions are expressing their dissatisfaction on X (formerly known as Twitter) concerning account lock-downs and the lack of access to LinkedIn’s customer support.
Historically, LinkedIn has taken 1-2 business days to address such issues, but since July of this year, the resolution time-frame has elongated to 4-5 working days, and some users have had their accounts locked for as long as a week.
Interestingly, these account lockouts have led to instances where scammers are coercing certain LinkedIn users into paying ransoms to prevent permanent account deletion.
Technically speaking, aside from LinkedIn’s engineers, only authorized personnel possess the capability to deactivate an account, unless the account is involved in illicit activities. Typically, accounts are suspended if fraudulent access is detected or if the content posted violates the platform’s posting policies. However, account deletion isn’t part of this process, nor does LinkedIn demand ransoms to prevent deletion.
A senior employee at a reputable banking institution in Newark recently posted a warning on Reddit regarding this matter. Within the last 72 hours, the post has garnered substantial attention, resulting in numerous comments, responses, and technical suggestions.
So, in the event of suspicion surrounding a LinkedIn account breach or restricted login access, consider the following steps:
1.) Initiate contact with LinkedIn’s customer support, and disregard any claims made in emails or messages requesting payment for issue resolution. The company does not engage in such campaigns, and those making such requests are fraudulent and not associated with LinkedIn.
2.) Await a response and communicate all pertinent details through the appropriate channels, such as the company’s designated webpage.
3.) Refrain from sharing login credentials with individuals on other social media platforms who promise temporary access in exchange for help.
4.) Given the extended response time due to heightened request volumes, exercise patience when interacting with the support team.
5.) Exercise caution and accept connection requests only from individuals within your industry. Be cautious of attractive profiles and avoid falling victim to their deceptive tactics.
The post LinkedIn account hacks increased in the past couple of weeks appeared first on Cybersecurity Insiders.
One frustrating aspect of email phishing is the frequency with which scammers fall back on tried-and-true methods that really have no business working these days. Like attaching a phishing email to a traditional, clean email message, or leveraging link redirects on LinkedIn, or abusing an encoding method that makes it easy to disguise booby-trapped Microsoft Windows files as relatively harmless documents.
KrebsOnSecurity recently heard from a reader who was puzzled over an email he’d just received saying he needed to review and complete a supplied W-9 tax form. The missive was made to appear as if it were part of a mailbox delivery report from Microsoft 365 about messages that had failed to deliver.
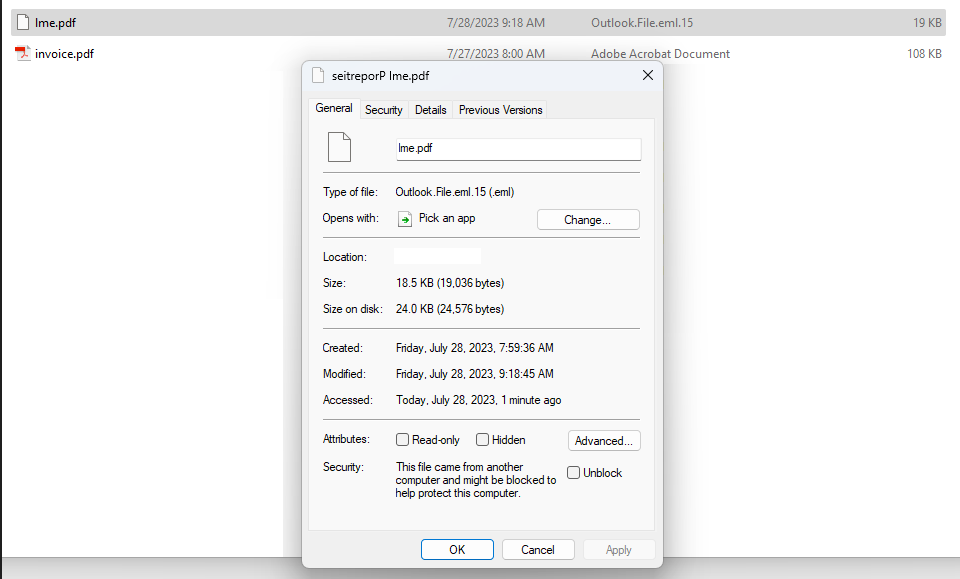
The reader, who asked to remain anonymous, said the phishing message contained an attachment that appeared to have a file extension of “.pdf,” but something about it seemed off. For example, when he downloaded and tried to rename the file, the right arrow key on the keyboard moved his cursor to the left, and vice versa.
The file included in this phishing scam uses what’s known as a “right-to-left override” or RLO character. RLO is a special character within unicode — an encoding system that allows computers to exchange information regardless of the language used — that supports languages written from right to left, such as Arabic and Hebrew.
Look carefully at the screenshot below and you’ll notice that while Microsoft Windows says the file attached to the phishing message is named “lme.pdf,” the full filename is “pdf.eml” spelled backwards. In essence, this is a .eml file — an electronic mail format or email saved in plain text — masquerading as a .PDF file.
“The email came through Microsoft Office 365 with all the detections turned on and was not caught,” the reader continued. “When the same email is sent through Mimecast, Mimecast is smart enough to detect the encoding and it renames the attachment to ‘___fdp.eml.’ One would think Microsoft would have had plenty of time by now to address this.”
Indeed, KrebsOnSecurity first covered RLO-based phishing attacks back in 2011, and even then it wasn’t a new trick.
Opening the .eml file generates a rendering of a webpage that mimics an alert from Microsoft about wayward messages awaiting restoration to your inbox. Clicking on the “Restore Messages” link there bounces you through an open redirect on LinkedIn before forwarding to the phishing webpage.
As noted here last year, scammers have long taken advantage of a marketing feature on the business networking site which lets them create a LinkedIn.com link that bounces your browser to other websites, such as phishing pages that mimic top online brands (but chiefly Linkedin’s parent firm Microsoft).
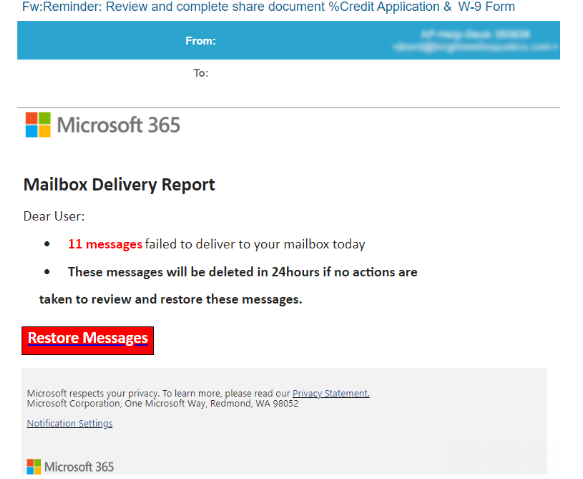
The landing page after the LinkedIn redirect displays what appears to be an Office 365 login page, which is naturally a phishing website made to look like an official Microsoft Office property.
In summary, this phishing scam uses an old RLO trick to fool Microsoft Windows into thinking the attached file is something else, and when clicked the link uses an open redirect on a Microsoft-owned website (LinkedIn) to send people to a phishing page that spoofs Microsoft and tries to steal customer email credentials.
According to the latest figures from Check Point Software, Microsoft was by far the most impersonated brand for phishing scams in the second quarter of 2023, accounting for nearly 30 percent of all brand phishing attempts.
An unsolicited message that arrives with one of these .eml files as an attachment is more than likely to be a phishing lure. The best advice to sidestep phishing scams is to avoid clicking on links that arrive unbidden in emails, text messages and other mediums. Most phishing scams invoke a temporal element that warns of dire consequences should you fail to respond or act quickly.
If you’re unsure whether a message is legitimate, take a deep breath and visit the site or service in question manually — ideally, using a browser bookmark to avoid potential typosquatting sites.
Nikita Kislitsin, formerly the head of network security for one of Russia’s top cybersecurity firms, was arrested last week in Kazakhstan in response to 10-year-old hacking charges from the U.S. Department of Justice. Experts say Kislitsin’s prosecution could soon put the Kazakhstan government in a sticky diplomatic position, as the Kremlin is already signaling that it intends to block his extradition to the United States.

Nikita Kislitsin, at a security conference in Russia.
Kislitsin is accused of hacking into the now-defunct social networking site Formspring in 2012, and conspiring with another Russian man convicted of stealing tens of millions of usernames and passwords from LinkedIn and Dropbox that same year.
In March 2020, the DOJ unsealed two criminal hacking indictments against Kislitsin, who was then head of security at Group-IB, a cybersecurity company that was founded in Russia in 2003 and operated there for more than a decade before relocating to Singapore.
Prosecutors in Northern California indicted Kislitsin in 2014 for his alleged role in stealing account data from Formspring. Kislitsin also was indicted in Nevada in 2013, but the Nevada indictment does not name his alleged victim(s) in that case.
However, documents unsealed in the California case indicate Kislitsin allegedly conspired with Yevgeniy Nikulin, a Russian man convicted in 2020 of stealing 117 million usernames and passwords from Dropbox, Formspring and LinkedIn in 2012. Nikulin is currently serving a seven-year sentence in the U.S. prison system.
As first reported by Cyberscoop in 2020, a trial brief in the California investigation identified Nikulin, Kislitsin and two alleged cybercriminals — Oleg Tolstikh and Oleksandr Vitalyevich Ieremenko — as being present during a 2012 meeting at a Moscow hotel, where participants allegedly discussed starting an internet café business.
A 2010 indictment out of New Jersey accuses Ieremenko and six others with siphoning nonpublic information from the U.S. Securities & Exchange Commission (SEC) and public relations firms, and making $30 million in illegal stock trades based on the proprietary information they stole.
[The U.S. Secret Service has an outstanding $1 million reward for information leading to the arrest of Ieremenko (Александр Витальевич Еременко), who allegedly went by the hacker handles “Zl0m” and “Lamarez.”]
Kislitsin was hired by Group-IB in January 2013, nearly six months after the Formspring hack. Group-IB has since moved its headquarters to Singapore, and in April 2023 the company announced it had fully exited the Russian market.
In a statement provided to KrebsOnSecurity, Group-IB said Mr. Kislitsin is no longer an employee, and that he now works for a Russian organization called FACCT, which stands for “Fight Against Cybercrime Technologies.”
“Dmitry Volkov, co-founder and CEO, sold his stake in Group-IB’s Russia-based business to the company’s local management,” the statement reads. “The stand-alone business in Russia has been operating under the new brand FACCT ever since and will continue to operate as a separate company with no connection to Group-IB.”
FACCT says on its website that it is a “Russian developer of technologies for combating cybercrime,” and that it works with clients to fight targeted attacks, data leaks, fraud, phishing and brand abuse. In a statement published online, FACCT said Kislitsin is responsible for developing its network security business, and that he remains under temporary detention in Kazakhstan “to study the basis for extradition arrest at the request of the United States.”
“According to the information we have, the claims against Kislitsin are not related to his work at FACCT, but are related to a case more than 10 years ago when Nikita worked as a journalist and independent researcher,” FACCT wrote.
From 2006 to 2012, Kislitsin was editor-in-chief of “Hacker,” a popular Russian-language monthly magazine that includes articles on information and network security, programming, and frequently features interviews with and articles penned by notable or wanted Russian hackers.
“We are convinced that there are no legal grounds for detention on the territory of Kazakhstan,” the FACCT statement continued. “The company has hired lawyers who have been providing Nikita with all the necessary assistance since last week, and we have also sent an appeal to the Consulate General of the Russian Federation in Kazakhstan to assist in protecting our employee.”
FACCT indicated that the Kremlin has already intervened in the case, and the Russian government claims Kislitsin is wanted on criminal charges in Russia and must instead be repatriated to his homeland.
“The FACCT emphasizes that the announcement of Nikita Kislitsin on the wanted list in the territory of the Russian Federation became known only today, June 28, 6 days after the arrest in Kazakhstan,” FACCT wrote. “The company is monitoring developments.”
The Kremlin followed a similar playbook in the case of Aleksei Burkov, a cybercriminal who long operated two of Russia’s most exclusive underground hacking forums. Burkov was arrested in 2015 by Israeli authorities, and the Russian government fought Burkov’s extradition to the U.S. for four years — even arresting and jailing an Israeli woman on phony drug charges to force a prisoner swap.
That effort ultimately failed: Burkov was sent to America, pleaded guilty, and was sentenced to nine years in prison.

Alexei Burkov, seated second from right, attends a hearing in Jerusalem in 2015. Image: Andrei Shirokov / Tass via Getty Images.
Arkady Bukh is a U.S. attorney who has represented dozens of accused hackers from Russia and Eastern Europe who were extradited to the United States over the years. Bukh said Moscow is likely to turn the Kislitsin case into a diplomatic time bomb for Kazakhstan, which shares an enormous border and a great deal of cultural ties with Russia. A 2009 census found that Russians make up about 24 percent of the population of Kazakhstan.
“That would put Kazakhstan at a crossroads to choose between unity with Russia or going with the West,” Bukh said. “If that happens, Kazakhstan may have to make some very unpleasant decisions.”
Group-IB’s exodus from Russia comes as its former founder and CEO Ilya Sachkov remains languishing in a Russian prison, awaiting a farcical trial and an inevitable conviction on charges of treason. In September 2021, the Kremlin issued treason charges against Sachkov, although it has so far refused to disclose any details about the allegations.
Sachkov’s pending treason trial has been the subject of much speculation among denizens of Russian cybercrime forums, and the consensus seems to be that Sachkov and Group-IB were seen as a little too helpful to the DOJ in its various investigations involving top Russian hackers.
Indeed, since its inception in 2003, Group-IB’s researchers have helped to identify, disrupt and even catch a number of high-profile Russian hackers, most of whom got busted after years of criminal hacking because they made the unforgivable mistake of stealing from their own citizens.
When the indictments against Kislitsin were unsealed in 2020, Group-IB issued a lengthy statement attesting to his character and saying they would help him with his legal defense. As part of that statement, Group-IB noted that “representatives of the Group-IB company and, in particular, Kislitsin, in 2013, on their own initiative, met with employees of the US Department of Justice to inform them about the research work related to the underground, which was carried out by Kislitsin in 2012.”
Microsoft has made an official announcement that it will pay a $20m penalty to the US Federal Trade Commission (FTC) as it was found guilty of collecting children info via gaming consoles without their valid consent.
Digging deep into the context, a lawsuit was slapped against the technology giant for collecting information of children playing games on Xbox Gaming Consoles. As it was against the Chil-dren’s Online Privacy Protection Act (COPPA) Protection rules and was being shared with the 3rd parties, a case was filed against the Windows OS giant in the court.
Upon launching an enquiry, the data watch dog of United States found that the Redmond based giant was collecting info related to avatars of kids, their biometrics and health related details.
So, the FTC’s Bureau of Consumer Protection issued a penalty on the Satya Nadella led com-pany and after few hearings, the company agreed to take steps to bolster privacy protections to shield Xbox users who are aged below 13.
Meanwhile, on a separate note, Microsoft has announced that it will keep $425 million in re-serve to pay a latent penalty to the Irish Data Protection Commissioner (DPC) for violation of GDPR rules by its business subsidiary LinkedIn.
A spokesperson from the company added that the company has decided to set aside the amount in the 4th quarter of this fiscal year 2023. Till then, news is out that the company is intending to defend its stand on complying with the GDPR and will try to negotiate and reduce the penalty.
The post Microsoft to pay $20m penalty for collecting children info without consent appeared first on Cybersecurity Insiders.