Apple has introduced a powerful new data security feature, Lockdown Mode, for iPhone users running iOS 16 and later versions. This feature aims to provide heightened protection against cyber threats, particularly for individuals who are at a higher risk of being targeted by advanced attacks. While Lockdown Mode offers enhanced security, it does come with certain limitations that users should be aware of before enabling it.
What is Lockdown Mode?
Lockdown Mode is a security feature designed primarily for individuals who may be vulnerable to sophisticated cyberattacks, such as journalists, activists, or high-profile targets. It is intended to help protect users from spyware and other types of malicious activity. Although initially developed for a limited group of people, Apple has now made this feature available to all iOS users with devices running iOS 16 and above.
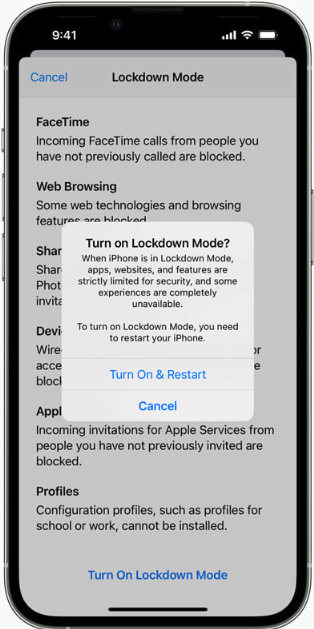
The feature limits certain device functionalities in exchange for heightened security. When enabled, Lockdown Mode restricts the use of certain apps, limits web browsing capabilities, and disables specific features in order to prevent the installation or exploitation of spyware like Pegasus, which is known for targeting high-risk individuals.
How to Enable Lockdown Mode?
Activating Lockdown Mode is straightforward. To do so, users should navigate to the Settings app on their iPhone. From there, they should select Privacy & Security, where the option to enable Lockdown Mode can be found. After selecting it, the iPhone will prompt the user to restart the device to activate the feature effectively. Once enabled, Lockdown Mode will function automatically, providing the added layer of protection.
What Does Lockdown Mode Disable?
While Lockdown Mode boosts security, it does so by limiting the functionality of certain apps and services. Here are some of the most notable effects of enabling Lockdown Mode:
Messaging Apps: Apps like WhatsApp will experience restrictions. Users will no longer be able to send or receive attachments such as photos, videos, documents, or links. Link previews are also disabled, meaning that when links are shared, the user will only see the raw URL instead of a preview of the content.
FaceTime: FaceTime calls will not function as they normally would, with some features being disabled or affected. For instance, it might not support video calls or could restrict other interactive elements of the service.
Web Browsing: Web browsing will be significantly impacted. When using Safari or other browsers, pages may load only in plain text, removing images, scripts, and other media that could potentially be used for malicious purposes. This could result in slower browsing experiences, with certain websites appearing incomplete or broken.
App and Website Functionality: In general, many apps and websites will experience a reduction in functionality. By limiting JavaScript and other active features, Lockdown Mode prevents harmful exploits from being executed via these platforms. This also protects against spyware that could otherwise compromise the device.
Emergency Features Remain Unaffected
One of the significant benefits of Lockdown Mode is that it does not interfere with critical emergency features. Functions like the Emergency SOS mode and Find My iPhone will continue to operate normally. These features are vital for user safety and are essential for situations where users need to access emergency help or locate their device.
Limitations on Location Sharing
Another side effect of Lockdown Mode is that location-sharing features may be restricted. While the Find My iPhone feature remains unaffected, the ability to share location information via apps like Messages or third-party apps may be limited or disabled entirely, depending on the specific app in question. This is another security measure to ensure that location data is not exploited by malicious actors.
Conclusion
In summary, Lockdown Mode is a valuable feature for iPhone users who are concerned about advanced cyber threats and spyware attacks. Although it may limit the functionality of some apps and services—such as messaging apps, FaceTime, and web browsing—the trade-off is the added security it provides against highly sophisticated malware. While it may not be suitable for everyday users due to the limitations it imposes, for those who need heightened protection, Lockdown Mode is an important tool to safeguard their personal data and privacy.
The post Here’s the little known iPhone data security secret, the Lockdown Mode appeared first on Cybersecurity Insiders.

 Not to be outdone, Apple fixed at least two zero-day vulnerabilities when it released updates for iOS, iPadOS, macOS and Safari. CVE-2022-32984 is a problem in the deepest recesses of the operating system (the kernel). Apple pushed
Not to be outdone, Apple fixed at least two zero-day vulnerabilities when it released updates for iOS, iPadOS, macOS and Safari. CVE-2022-32984 is a problem in the deepest recesses of the operating system (the kernel). Apple pushed