In the modern digital landscape, organizations face an ever-increasing barrage of cyber threats. Cybercriminals continually adapt their tactics, making it challenging for businesses to defend against potential cyber incidents. As a result, cybersecurity risks have become a top concern for businesses of all sizes and industries. While implementing robust cybersecurity measures is essential, another vital component in managing cyber risks is cyber insurance. Cyber insurance provides financial protection and support in the aftermath of a cyber incident, offering a safety net against potential financial losses. In this article, we will delve into the role of cyber insurance in managing cybersecurity risks and how it complements other cybersecurity practices, including Security Operations Center as a Service (SOCaaS).
Understanding Cyber Insurance
Cyber insurance, also known as cyber liability insurance or data breach insurance, is a specialized insurance product designed to mitigate the financial impact of a cyber incident. It covers various aspects, including data breaches, network security failures, business interruption losses, extortion, and legal costs associated with cyber incidents. The coverage can be tailored to meet the unique needs of different organizations, offering a sense of security in an increasingly unpredictable digital landscape.
- Financial Protection against Cyber Incidents
The primary role of cyber insurance is to provide financial protection in the event of a cyber incident. A cyber incident can lead to substantial financial losses, such as data recovery costs, legal fees, and regulatory fines. Cyber insurance helps alleviate these burdens, ensuring that organizations can recover without enduring crippling financial consequences.
- Breach Notification and Customer Support
Data breaches often require organizations to notify affected individuals and authorities promptly. Cyber insurance policies may include coverage for the costs associated with notifying customers, providing credit monitoring services, and offering customer support to affected parties. These measures can help maintain customer trust and loyalty in the aftermath of a cyber incident.
- Legal and Regulatory Support
Cyber incidents can lead to legal actions and regulatory investigations, especially in cases of data breaches involving sensitive customer information. Cyber insurance can cover legal fees and expenses incurred during litigation and regulatory investigations, ensuring organizations have the necessary resources to defend their interests.
- Business Interruption Coverage
Cyberattacks can disrupt business operations, leading to significant revenue losses. Cyber insurance can include coverage for business interruption losses, compensating organizations for lost income during the downtime caused by a cyber incident.
- Extortion and Ransomware Coverage
Ransomware attacks have become increasingly prevalent, with cybercriminals demanding ransoms to restore access to encrypted data. Cyber insurance can cover ransom payments or extortion costs, assisting organizations in resolving such incidents without compromising their financial stability.
The Role of SOC as a Service (SOCaaS) in Cyber Insurance
As organizations continue to face sophisticated cyber threats, many are turning to SOCaaS for expert cybersecurity services. SOC as a Service offers continuous monitoring, threat detection, and incident response capabilities to safeguard organizations against cyberattacks. The combination of cyber insurance and SOCaaS plays a crucial role in comprehensive risk management.
- Proactive Risk Mitigation
SOC as a Service (SOCaaS) plays a vital role in cyber insurance by offering proactive risk mitigation. SOCaaS providers employ advanced technologies and skilled analysts to continuously monitor an organization’s network, systems, and applications in real-time. This early detection and prevention of potential cyber threats can reduce the likelihood of security incidents that may trigger cyber insurance claims.
- Timely Incident Response
In the event of a cyber incident, SOCaaS providers respond promptly to contain and mitigate the impact of the breach. Their swift actions can minimize the extent of damage and potentially prevent the need for a cyber insurance claim. SOCaaS empowers organizations to act quickly and decisively, limiting financial losses and protecting their reputation.
- Enhanced Cybersecurity Posture
SOCaaS enhances an organization’s overall cybersecurity posture by continuously identifying vulnerabilities and areas of improvement. By addressing these weaknesses, organizations can lower their overall cyber risk profile, potentially leading to reduced cyber insurance premiums. The collaborative efforts of SOCaaS and cyber insurance create a proactive approach to cybersecurity, ensuring organizations are well-prepared to handle cyber threats.
- Risk Assessment and Insights
SOCaaS providers can collaborate with cyber insurance companies to conduct risk assessments and provide valuable insights into an organization’s security preparedness. This information can assist insurance underwriters in accurately evaluating an organization’s risk profile and offering appropriate coverage. The data and analysis from SOCaaS contribute to a more comprehensive understanding of an organization’s cyber risk exposure, enabling insurance providers to tailor policies to meet specific needs.
- Comprehensive Incident Reporting
SOCaaS generates detailed incident reports, documenting the nature and extent of cyber incidents. These reports can serve as essential documentation during the cyber insurance claim process, facilitating a smoother and more efficient resolution. The comprehensive incident reporting from SOCaaS ensures that cyber insurance claims are well-documented and supported by accurate and timely information.
- Continuous Monitoring and Detection
SOCaaS provides continuous monitoring and threat detection, significantly reducing the time between a cyber incident’s occurrence and its detection. This swift detection is critical for cyber insurance claims, as it allows organizations to respond promptly and minimize the impact of the breach. The proactive monitoring capabilities of SOCaaS bolster an organization’s ability to detect and address cyber incidents quickly and effectively.
- Regulatory Compliance Support
SOCaaS helps organizations stay in compliance with various regulatory requirements by monitoring and identifying potential security gaps that might result in non-compliance. Adhering to regulatory standards is crucial for maintaining insurance coverage, and SOCaaS ensures that organizations have the necessary security measures in place to meet regulatory obligations.
Conclusion
In the face of ever-evolving cyber threats, businesses must adopt a multi-faceted approach to cybersecurity. Cyber insurance and SOC as a Service (SOCaaS) form a powerful alliance, complementing each other to effectively manage cybersecurity risks. While cyber insurance provides financial protection in the aftermath of a cyber incident, SOCaaS offers proactive monitoring and incident response capabilities to prevent and detect security breaches. Together, these solutions create a robust defense against cyber threats, empowering organizations to navigate the digital landscape with confidence and resilience. As cyber risks continue to evolve, embracing both cyber insurance and SOCaaS becomes imperative for organizations seeking comprehensive cybersecurity risk management.
Image by Freepik
The post Cyber Insurance and SOC as a Service – Adapting to New Cybersecurity Challenges appeared first on Cybersecurity Insiders.
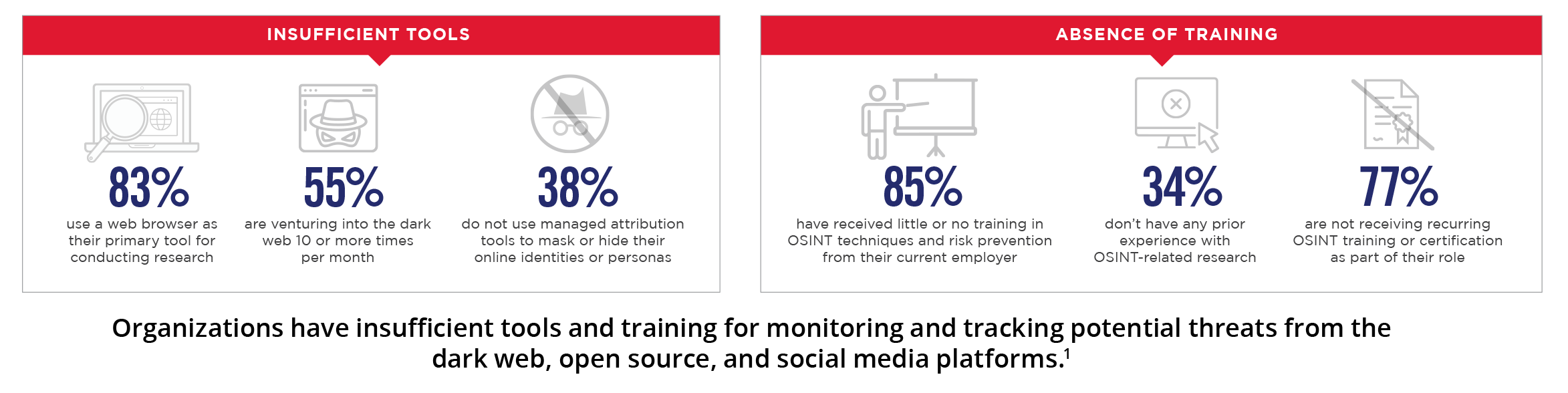
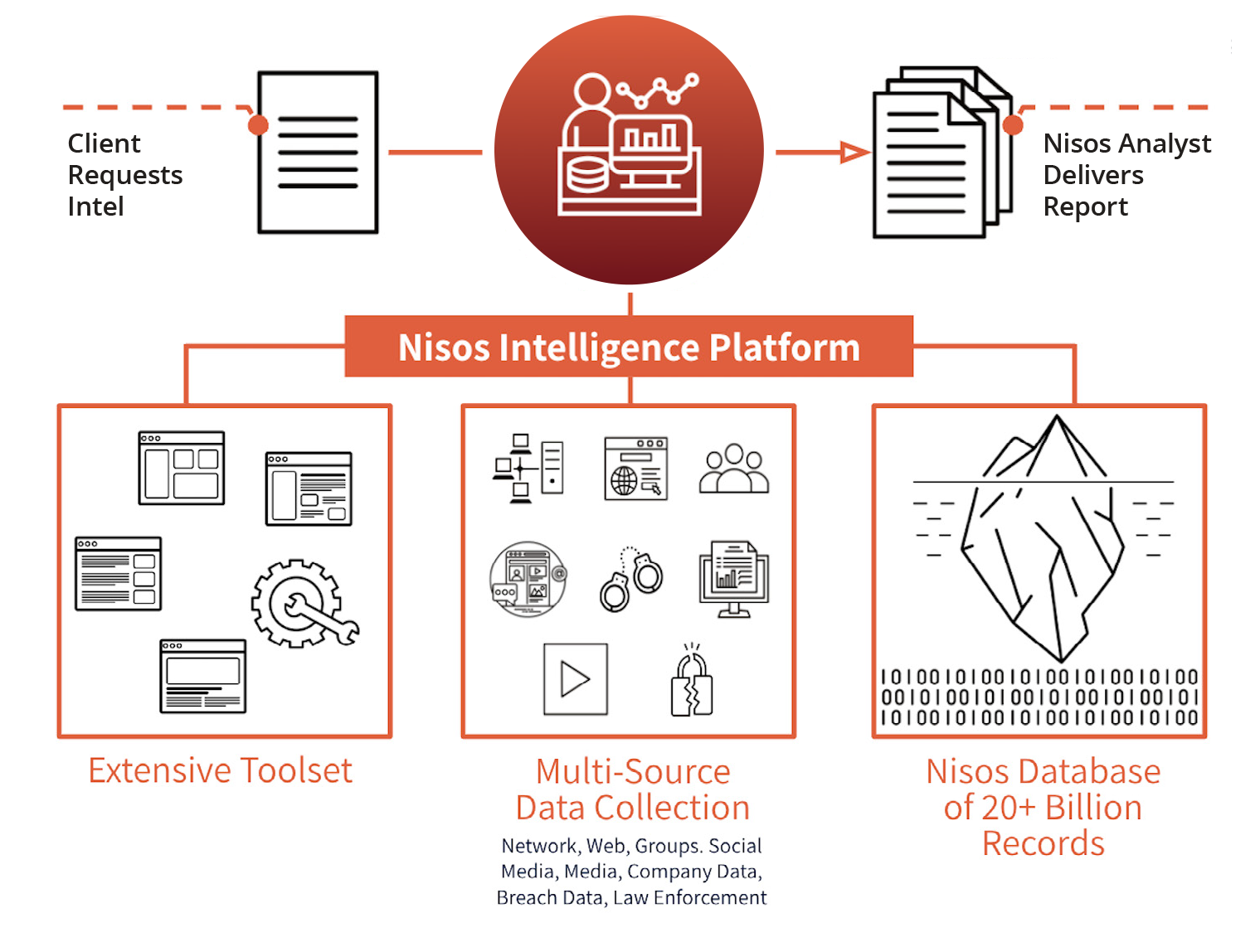
 . Their services enable security, intelligence, and trust & safety teams to leverage a world-class intelligence capability tailored to their needs. They fuse robust data collection with a deep understanding of the adversarial mindset delivering smarter defense and more effective response against advanced cyber attacks, physical threats to personnel or facilities, disinformation and reputational attacks, and the abuse and fraud of digital platforms.
. Their services enable security, intelligence, and trust & safety teams to leverage a world-class intelligence capability tailored to their needs. They fuse robust data collection with a deep understanding of the adversarial mindset delivering smarter defense and more effective response against advanced cyber attacks, physical threats to personnel or facilities, disinformation and reputational attacks, and the abuse and fraud of digital platforms.