BullWall, global leaders in ransomware containment, and researchers with Cybersecurity Insiders, today published the Cybersecurity Insiders 2023 Ransomware Report. Based on a survey of 435 cybersecurity professionals, the findings identified gaps, misunderstandings and obstacles in organizational security posture, attack prevention and ransomware remediation.
These findings emphasize the importance of shifting from a purely preventative approach, such as relying on EDR, to a layered, comprehensive strategy that includes rapid containment of ongoing attacks to limit the damage inflicted and reduce recovery time.
Cybersecurity Insiders CEO and Founder Holger Schulze will join Steve Hahn, BullWall EVP at 11:00am ET on June 15, 2023, to review the findings and share recommendations during the webinar “Why EDRs And Other Preventative Measures Cannot Stop Ransomware and What To Do Instead.”
Among the 2023 Ransomware Report’s key findings:
- Overconfidence about attack detection: 77 percent of respondents incorrectly believe their endpoint security solution (EDR) can sufficiently protect their servers against malware attacks.
- Substantial gap in confidence between detection and remediation: while 76 percent were highly confident in the organization’s ability to prevent an attack, only 35 percent were confident in the organization’s current ability to remediate ransomware after it locks or encrypts data within their systems.
- Recovery time expectations are overly optimistic: 35 percent of respondents believe they can recover from an attack in a few days, despite research showing that recovery averages weeks or even months.
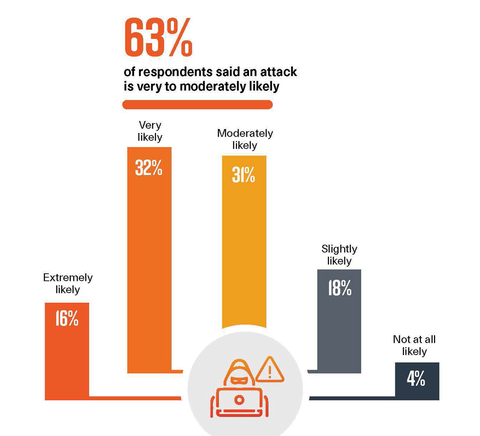
- Troubling expectations: 79 percent of respondents said a threat is moderately to extremely likely to happen to their organization within the next year.
- Data at risk: 69 percent report that financial information is at risk, 61 percent report that customer information is at risk, and 56 percent say employee information is at risk.
- Ransomware’s biggest negative impacts: 82 percent cite downtime, 75 percent cite financial losses, and 68 percent cite reputational damage.
- Main obstacles in enhancing defense strategies: 47 percent cite the evolving sophistication of attacks and 45 percent cite budget constraints.
“This research was very interesting for us,” said Holger Schulze. “We’ve been researching the state of ransomware for years, but a new trend is now starting to emerge. Organizations are becoming almost resigned to the eventuality of a ransomware attack, and are starting to indicate that the golden standards of prevention are not enough. These findings emphasize the importance of shifting from a purely preventative approach, such as relying on EDR, to a more layered, comprehensive strategy that includes rapid containment of ongoing attacks. By implementing solutions that can quickly shut down active attacks, organizations can limit the damage inflicted and reduce recovery time, better protecting their valuable data, operations and reputation.”
“The Cybersecurity Insiders team is providing invaluable insight that’s clearly needed now more than ever,” added Steve Hahn. “Ransomware is capable of infecting over 45,000 files per minute per infected device, and last year there were over 217 million attacks in the U.S. alone according to experts. A last line of defense when ransomware gets in – and it almost always does – is absent in most organizations, and urgently needed in all.”
To receive the full Cybersecurity Insiders 2023 Ransomware Report, please visit: https://bullwall.com/2023-ransomware-report/?utm_source=2023-ransomware-report&utm_medium=press-release&utm_campaign=2023-ransomware-report
To register for the webinar “Why EDRs And Other Preventative Measures Cannot Stop Ransomware And What To Do Instead” on 11:00am ET, June 15, please visit: https://register.gotowebinar.com/register/5763097225180979552?source=BW
BullWall Enters North American Market:
The findings follow BullWall’s May, 2023 expansion into North America following dramatic success in Europe. Its fully automated, patented last line of defense against ransomware is used in many European mission-critical enterprises across industries such as healthcare, education and government.
BullWall continuously monitors file shares, application servers and database servers in the cloud and in the data center, preventing server data encryption within seconds and thwarting attempts to both encrypt and exfiltrate data.
For more information about Bull Wall’s solutions and services, visit the company’s website at www.bullwall.com.
About BullWall
BullWall is a cybersecurity solution provider with a dedicated focus on protecting data and critical IT infrastructure during active ransomware attacks. We are able to contain both known and zero day ransomware variants in seconds, preventing both data encryption and exfoliation. BullWall is the last line of defense for active attacks.
