By Holger Schulze, Cybersecurity Insiders
As the proliferation of APIs continues unabated, the importance of robust API security measures cannot be overstated. In a recent interview, Richard Bird, Chief Security Officer at Traceable AI, offered valuable insights into the increasing risks associated with APIs and how companies can defend against these threats.
The Escalating API Security Challenge
In Bird’s view, the rise of APIs, and with them, the security risk exposure, is linked to a number of factors. Firstly, the digital transformation efforts of organizations have led to the widespread adoption of APIs to enable seamless interactions between different software applications. This, coupled with the increasing use of cloud services and microservices architectures, has led to an explosion in the number of APIs in recent years, thereby significantly expanding the attack surface for potential cyber threats. At the same time, APIs have in the past not received the same attention from security teams and product vendors as other aspects of IT environments, leaving APIs vulnerable to innovative attacks.
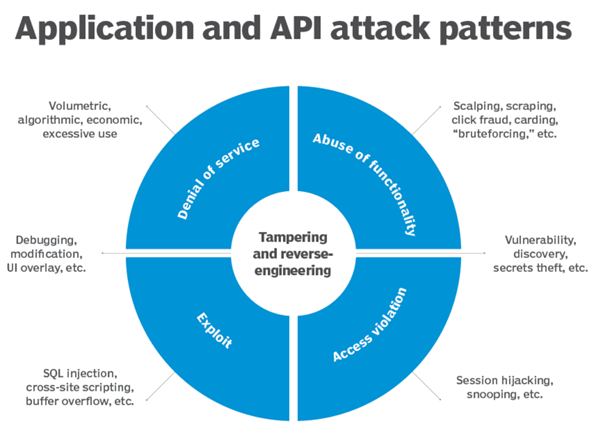
Types of API Attacks
APIs, by nature, expose application functionality and data, which makes them an enticing target for cyber attackers. Several types of attacks target APIs, including:
- Injection Attacks: These occur when an attacker sends malicious data as part of a command or query, tricking the interpreter into executing unintended commands or accessing unauthorized data. SQL Injection is a notable example of this type.
- Broken Authentication: APIs that don’t properly enforce authentication can allow attackers to impersonate other users or even gain administrative privileges.
- Sensitive Data Exposure: APIs may inadvertently expose sensitive information like personal identifiers, financial information, or security credentials, which can be exploited by attackers.
- Security Misconfiguration: Poorly configured security settings for APIs can leave them vulnerable to attackers who can exploit the defaults left in place.
- Mass Assignment: APIs that bind client-provided data (like JSON request payloads) directly to data models may inadvertently expose any properties not explicitly listed in a binding exclusion list.
- Broken Access Control: APIs must properly validate users’ permissions before granting them access to data. Failure to do so can allow unauthorized access to sensitive data.
- Server-Side Request Forgery (SSRF): These attacks trick the server into making requests it didn’t intend to, possibly bypassing access controls and gaining access to internal resources.
Each of these attacks presents a significant threat to APIs and the applications and data behind them, and it’s essential for organizations to use a robust API security solution, like Traceable AI, to protect against these common API vulnerabilities and threat vectors.
The Impact of API Attacks
The consequences of API attacks can be severe. From data breaches to service disruptions, the impact on an organization’s reputation, operations, and bottom line can be significant. As Richard Bird pointedly noted, “When APIs are attacked, it’s not just about data being lost. It’s about trust being eroded, it’s about operations being hindered.”
The Limitations of Traditional Security Tools
Traditional security tools and techniques often fall short in protecting against API attacks, primarily because they were not designed to deal with the unique challenges that APIs present. In many instances, these tools lack the necessary visibility into API-related traffic and cannot adequately track or analyze API behavior. This leaves organizations vulnerable to attacks.
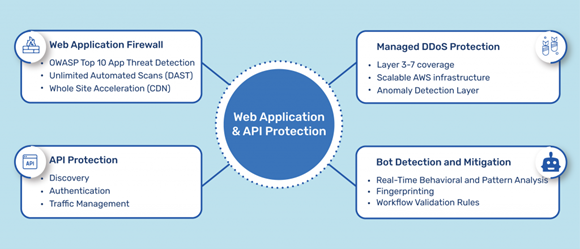
Stopping API Attacks with Traceable AI
In the complex and continuously evolving landscape of API security, solutions like Traceable AI stand out. This platform combines end-to-end distributed tracing, cloud-native integrations, and advanced machine learning-driven behavioral analytics to deliver API and application security from user to code. Furthermore, it offers robust protection capabilities, with automatic detection and blocking of both known and unknown API attacks.
One notable feature of Traceable AI is its dynamic API catalog. This provides automatic and continuous API discovery, giving security teams comprehensive visibility of all APIs, sensitive data, and risk posture, even in rapidly changing environments. Coupled with real-time topology maps showing API flows and interconnectivity between services, businesses are offered accurate insights into actual application usage and infrastructure vulnerabilities.
API Security Testing for Proactive Threat Mitigation
Beyond protection, Traceable AI is designed for proactive threat mitigation. Its API Security Testing (AST) enables businesses to test their APIs against various vulnerabilities and security gaps before deployment in a production environment. This not only helps in prioritizing threats but also aids in building resilient systems.
Navigating the Complexities of API Security
With API attacks becoming increasingly sophisticated, it is paramount for organizations to have a deep understanding of their API environment and the potential vulnerabilities that exist. Traceable AI provides this understanding through a range of features designed to provide in-depth visibility, protection, and testing. As Bird summarized, “Traceable AI is focused on providing customers with the visibility and control they need to manage their APIs effectively and protect their digital assets.”
Best Practices for Robust API Protection
To help organizations strengthen their defenses, here are best practices for enhancing API security, incorporating the effective use of API security platforms such as Traceable.
- API Security by Design: It is essential to integrate security from the initial stages of API design and development. This includes defining proper authorization and authentication protocols, ensuring data validation, and incorporating the least privilege principle.
- Inventory APIs: To mitigate the risk of unsecured APIs, it’s essential to have a complete inventory of all the APIs deployed in your organization. This includes knowing what they do, who has access to them, and how they interact with other elements in your system. Automated platforms can assist in this task, offering tools for automatic and continuous API discovery, providing comprehensive visibility into your API landscape.
- API Monitoring and Anomaly Detection: Use AI-powered tools to monitor API usage continually. These tools can identify unusual patterns and potential threats based on machine learning algorithms. This proactive monitoring is key to preventing attacks before they cause damage.
- Encryption and Data Protection: Encrypt all data in transit using HTTPS to maintain data confidentiality and integrity. Additionally, validate all data passing through your APIs to prevent injections and data leaks.
- Regular Security Testing: Conduct regular security testing, including vulnerability assessments and penetration testing. Platforms like Traceable offer API Security Testing (AST) features that can test your APIs against various vulnerabilities and security gaps before deployment.
- Rate Limiting and DoS Protection: Implement rate limiting to prevent Denial of Service (DoS) attacks or brute force attempts on your APIs. Tools like Traceable also offer DDoS protection by rate-limiting the number of requests to your APIs.
- Continuous Training and Education: Regularly update your teams on the best practices in API security. It’s essential to stay informed about the latest security risks and how to avoid them. Empower your development and security teams with the knowledge they need to build secure APIs from the ground up.
Conclusion
API security is a complex and evolving challenge that requires a sophisticated and adaptable approach. The insights shared by Richard Bird underline the importance of adopting advanced solutions like Traceable AI that can provide comprehensive visibility, robust protection, and proactive testing capabilities. As the number of APIs continues to grow, so too does the need for effective API security measures. Organizations that take the time and resources to understand and address this risk will be better positioned to protect their operations and maintain the trust of their customers in the digital age.
The post Advancing API Security: An Interview with Richard Bird of Traceable AI appeared first on Cybersecurity Insiders.