Welcome to the world of data privacy, where safeguarding your digital life takes center stage! Every year, on the 28th of January, we celebrate Data Privacy Day – a global initiative dedicated to spreading awareness and championing best practices in privacy and data protection. This international event resonates in the United States, Canada, Nigeria, Israel, and across 47 European countries.
The roots of Data Privacy Day can be traced back to the European Data Protection Day, marking the historic signing of Convention 108 on January 28, 1981 – the first-ever international treaty addressing privacy and data protection. Fast forward to 2009, when the U.S. House of Representatives and the Senate officially recognized National Data Privacy Day. More recently, in 2023, the National Cybersecurity Alliance extended the celebration into Data Privacy Week, themed “Take Control of Your Data.”
Beyond the festivities, Data Privacy Day and Week serve as dynamic platforms for collaboration and education. These events cover various topics, from webinars and workshops to panel discussions, including data privacy laws, security tips, ethics, innovation, and trust. Emphasizing individuals’ proactive role in securing their data, these initiatives encourage us all to make informed decisions, adjust privacy settings, and navigate the digital landscape responsibly. After all, data privacy isn’t just a right – it’s a shared responsibility for every internet user. So, let’s embark on this journey to empower ourselves and shape a more secure online world!
Terry Storrar, Managing Director, Leaseweb
“In recent years, cloud trends have changed significantly – from the initial gold rush to the cloud and the additional push during the pandemic to the cloud repatriation we’ve been seeing more recently. However, although people are continuing to change how and to what extent they are utilizing cloud technologies, one thing is certain: the cloud is continuing to grow. In fact, this year, global spending on cloud computing infrastructure is forecasted to exceed $1 trillion for the first time.
“With this uptake, the priority for 2024 needs to be ensuring that the data held within – and transferred between – these platforms is secure. Thankfully, there are many things businesses can do to ensure a comprehensive data recovery program is in place. For example, by choosing a trusted hosting provider, customers can gain access to 24/7 security-related support services, standard security training for all employees, and robust disaster recovery solutions.
“In an age where the risks of data loss are broad and in many cases inevitable, it’s essential that organizations make sure they have the right tools to back up and recover quickly and effectively should this take place. Data Protection Day is a great opportunity to take stock of how secure your data is and remember it’s always worth going the extra mile when it comes to putting plans in place before you need to execute them.”
Kevin Cole, director, product and technical marketing, Zerto, an HPE company
“Data is one of the most valuable assets that an organization has. For this Data Privacy Day, it’s critical to consider data protection and recovery as part of any comprehensive privacy strategy. When data is compromised, operations can be halted for extended periods of time, and there is a significant risk of financial loss or brand impact. Protecting both customer and company data should be the top priority for all organizations, especially in light of growing ransomware threats. And yet, shockingly, more than one-third of companies still do not have a well-rounded, holistic ransomware strategy in place, according to a Zerto survey. This is in a digital environment where, as reported by SpyCloud, over 80% of organizations have been impacted by ransomware in the past 12 months. With ransomware attacks on the rise, better data protection is desperately needed.
To address this need, a cyber vault should be an important part of any organization’s data protection plan. Having an isolated data vault containing an untouchable, immutable copy of company data ensures that even during a ransomware attack, a safe data copy will remain. However, vault storage is only one piece of the data protection pie: disaster recovery is also essential to reduce downtime and get organizations back up and running before significant financial consequences are incurred. Combining disaster recovery and cyber recovery together helps ensure data integrity, data protection, and ultimately, data privacy.”
Carl D’Halluin, CTO, Datadobi
“On January 28, we celebrate Data Privacy Day. Initiated in the United States and Canada in 2008 by the National Cyber Security Alliance, its aim is to raise awareness and promote privacy and data protection best practices.
I would say the number one data privacy best practice is pretty simple: make sure you can get the right data to the right place at the right time. Wherever the data is in its lifecycle, it should be protected and only accessible as needed. Of course, this tends to be easier said than done. But, there is perhaps nothing more critical and imperative than implementing the right strategies and technologies to do so. After all, while data is an organization’s most valuable asset (in addition to its people), it also represents its greatest potential risk.
Balancing these two aspects is key. In other words, effective data management enables you to optimize your business intelligence, make faster and smarter decisions, and gain a competitive edge, as well as better meet business requirements such as internal governance and legal mandates, external regulations, and financial obligations and goals.”
Konrad Fellmann, VP, IT Infrastructure & Chief Information Security Officer, Cubic Corporation
“Data Privacy in 2024 must look at the unique security and privacy considerations for organizations that partner with the public sector. In response to the recent surge in security and privacy mandates within public sector contracts, it is imperative that our security and privacy teams collaborate closely with our contracts department. This joint effort is essential to ensure a comprehensive understanding and assessment of these new requirements, as well as to evaluate the resources needed for compliance. Proactive engagement and deep knowledge of these stipulations will not only streamline contract execution but also optimize both time and financial investments throughout the duration of the contract. Embracing this approach is key to navigating the evolving landscape of public sector agreements with efficiency and expertise.
For our colleagues in the Defense Industrial Base, there is a growing anticipation that the Department of Defense (DoD) might finalize the Cybersecurity Maturity Model Certification (CMMC) 2.0 rule in 2024. Given this potential development, it’s crucial to initiate or advance our compliance assessments against the CMMC framework. Conducting a thorough gap analysis now will position us strategically, ensuring we are fully prepared and compliant when CMMC requirements start being integrated into DoD contracts. This proactive measure is not just about meeting compliance standards; it’s about reinforcing our commitment to cybersecurity excellence and maintaining our competitive edge in the defense sector.
Additionally, when it comes to various U.S. state privacy laws, it becomes evident that one of the key differences among them often lies in the timelines for reporting incidents. It’s my perspective that organizations can effectively navigate the complexity of these varying state regulations by embracing Generally Accepted Privacy Principles (GAPP). Adhering to GAPP can provide a robust framework, enabling compliance with a wide array of state privacy regulations. While the idea of a unified federal privacy standard is appealing for its potential to simplify compliance processes, the uncertainty surrounding its enactment means that for now, leveraging GAPP stands as a practical and comprehensive approach for organizations seeking to meet diverse state requirements in the U.S. data privacy landscape.”
Tom Ammirati, CRO, PlainID
“This year’s theme is ‘take control of your data,’ and the key to that is an organization protecting its data and the applications from cyberattacks. If a bad actor, which can include an employee, has gained access credentials, ensure that they don’t have automatic access to any or all data.
We know now that smart security solutions must be “identity-aware,” but they also call for a smart, dynamic authorization solution. One of the most significant benefits of zero trust is the process of granting an authenticated entity access to resources. Authentication helps ensure that the user accessing a system is who they claim to be; authorization determines what that user has permission to do. Arming your IT team with smart security solutions can be the key difference between a full-blown security incident and a security alert.”
Richard Bird, Chief Security Officer, Traceable AI
“Data privacy faces significant challenges at both consumer and federal levels. Many companies overlook the risks associated with seemingly harmless data, focusing instead on its value for user services and revenue growth. However, the data that is valuable to companies is also valuable to malicious actors, and failing to acknowledge this can lead to devastating lapses in data security.
In addition, companies today have no incentive to honor data privacy. Fines and lawsuit settlements clearly aren’t changing their behaviors or forcing these organizations to be good stewards of their customers’ trust.
Consumers must also exercise caution in oversharing data with companies, approaching privacy settings with a worst-case scenario mindset, as historical patterns reveal companies often neglect user privacy and safety concerns.
In addition, the recent executive order on artificial intelligence by the Biden administration enumerates a laundry list of digital privacy rights that the US government has already shown its inability to protect. This can be seen in incidents like the OPM hack, PPP loan fraud, and IRS refund processing, which raises doubts about the effectiveness of these guidelines and standards.
As we observe Data Privacy Day, let’s turn awareness into action. Advocate for stronger data protection measures, demand transparency from companies, and stay informed about your digital rights. It’s a collective effort to safeguard our privacy in an increasingly interconnected world.”
Dave Hoekstra, Product Evangelist, Calabrio
“Data Privacy Week reminds us of the critical need to protect sensitive information. Dave Hoekstra, Product Evangelist at Calabrio, emphasizes that now more than ever, securing customer-related information—a company’s most valuable assets—is a key strategic initiative.
In the realm of contact centers, where copious amounts of customer information and inquiries are processed, Calabrio places immense care in protecting this data. The commitment extends beyond Calabrio’s operations, as they actively encourage privacy consciousness among their partners. This dedication becomes even more vital in a landscape witnessing a surge in AI integrations.
As we navigate a world increasingly shaped by artificial intelligence, Calabrio’s proactive approach to data privacy meets industry standards and sets a benchmark for fostering trust. By prioritizing privacy consciousness, they can help secure information and contribute to building a foundation of trust in an evolving technological landscape.”
Cris Grossmann, CEO and founder, Beekeeper
“When we celebrate ‘Data Privacy Day,’ we can’t overlook our frontline workforce who don’t traditionally sit behind a computer, yet still need their personal information and sensitive data protected. Frontline industries can tend to depend on outdated processes of communications, ranging from pen and paper to personal text chains that leave workers vulnerable to data leaks. Companies need to prioritize leveraging technology that allows for secure messaging and takes their workers’ privacy into account.
As AI continues to find its way into the workforce, companies need to be mindful of using these tools to empower their workers, not exploit them. A first step employers can take is making sure their tech is GDPR compliant.
Supplying your frontline workers with an updated and secure frontline success system is a crucial step in fostering a culture of trust and security within the organization. By embracing modern technologies that prioritize data privacy, companies not only safeguard sensitive information but also empower frontline workers to perform their roles confidently, knowing that their personal data is handled with the utmost care.”
Steve Moore, Vice President & Chief Security Strategist, Exabeam
“Data Privacy Day presents an opportunity to reflect on the question ‘who is in charge of data privacy, the individuals sharing their data or the organizations in charge of protecting it?’
An individual’s digital identity — their username and password — will always be stolen, traded, sold, and reused. One of the easiest ways for threat actors to conduct these attacks is credential stuffing — where adversaries leverage account information from prior breaches. It’s important that both organizations and individuals understand what these attacks are, and just how prevalent they can.
So, who takes the blame when cyberattackers abuse reused customer passwords but companies don’t push for better hygiene? While an unsatisfying answer, the liability in these scenarios is often shared across both parties.
A key takeaway here is that companies could, and should, exert more of their own power and security tools to protect customers against increasingly aggressive adversaries. And individuals can make these attempts more difficult just by following best practices like implementing multi-factor authentication (MFA) and not recycling the same passwords.
In the end, high-profile data breaches are only getting more frequent. Data privacy isn’t just a one-day ordeal; it’s a year-round endeavor that requires the participation of both companies and their customers to combat cyber adversaries.”
Or Shoshani, Co-Founder and CEO, Stream.Security
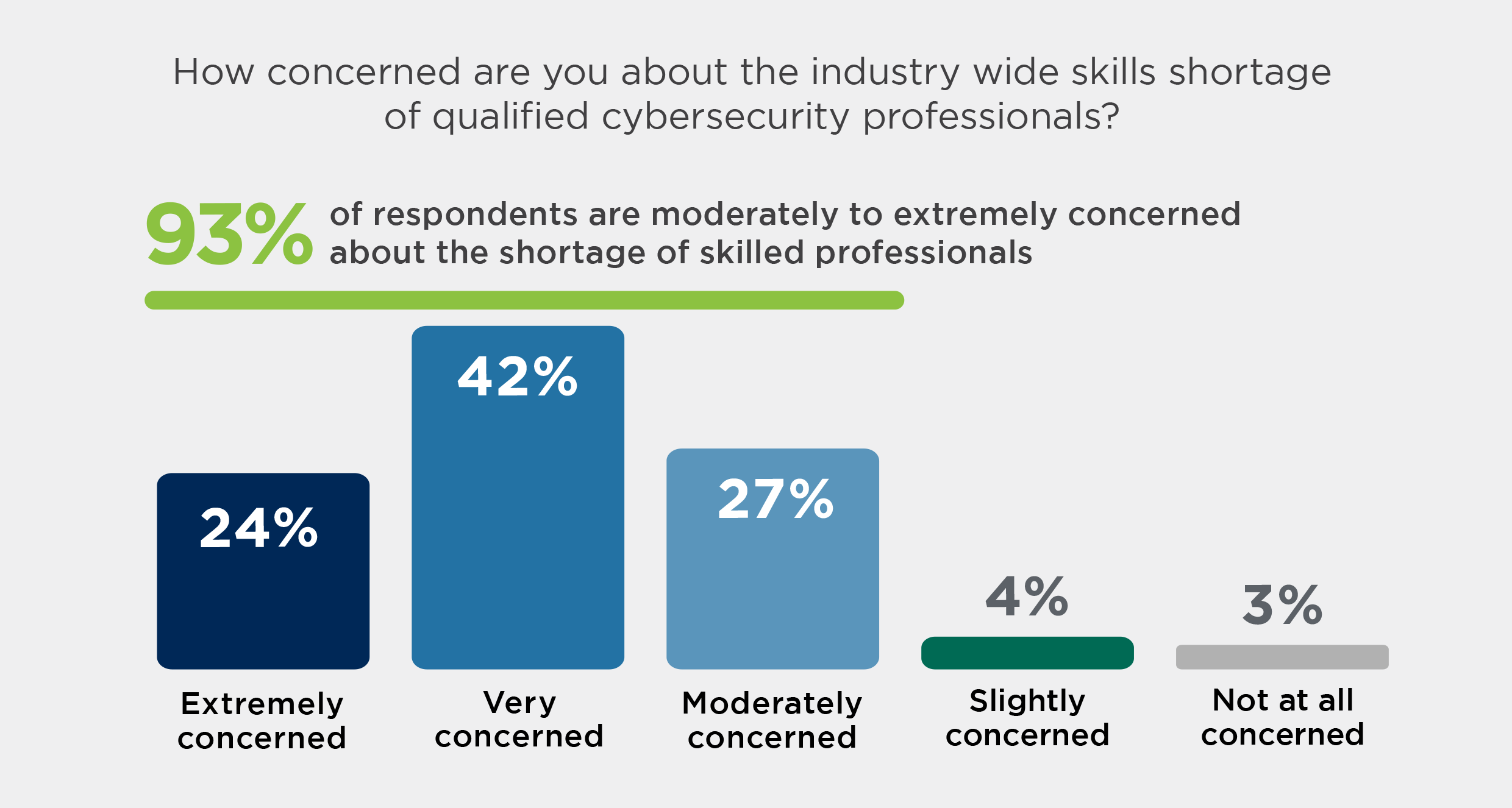
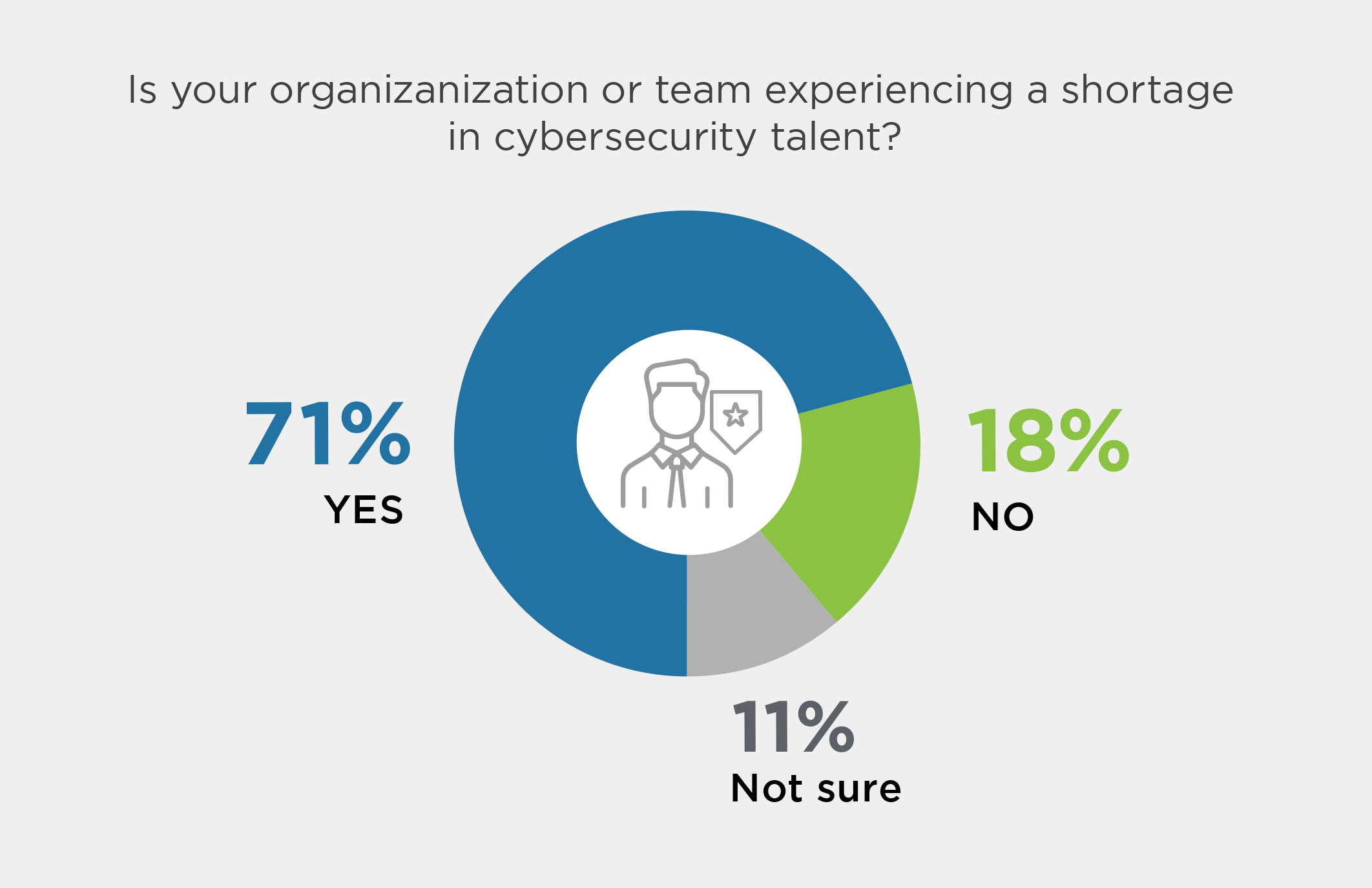
Especially considering the rise of AI-driven social engineering, Data Privacy Day reminds us of the urgency in maintaining our security structure to protect our data both on-prem and in the cloud. 72% of organizations are defaulting to cloud-based services when upgrading their tech. So it’s not surprising that recent surveys show cloud security incidents on the rise with 27% of organizations having experienced a public cloud security incident, up 10% from 2022.
Effectively managing your cloud security processes is the most crucial step in protecting your data. You can successfully prevent threat activity by fine-tuning and enhancing the steps associated with securing your cloud environment. Promote security awareness, follow compliance procedures, and educate yourself and your team to maintain the security of your data with the latest versions of your cloud security tools. Protecting your data in the cloud starts with education and ends with action.
Connie Stack, CEO, Next DLP
“Data privacy has taken on increased importance in the last few years. According to Gartner, by the end of this year, 75% of the world’s population will have its data covered under modern privacy regulations, meaning organizations have a duty – and quickly – to instill compliant procedures, technologies, and culture. Customers will be far more vigilant of how their data is being protected when choosing vendors in the coming years (if they aren’t already). What a vendor does to ensure a potential customer’s sensitive data is appropriately protected will become a key selling point. For these vendors, this means enacting compliant privacy solutions that protect customer data and provide businesses with behavior separate from the users.
What’s more, we’re also seeing intensifying pressure on CISOs to streamline their cybersecurity tools. The adoption of consolidated solutions from major tech companies stems from two primary challenges – the scarcity of skilled cybersecurity professionals and the internal drive for cost efficiency. While this move towards consolidation is becoming a norm, it’s vital to remember that depending on a single solution provider for all security requirements can be risky.
While cost reduction will always be top of mind for executive teams (especially CFOs), organizations should be looking to implement robust Data Loss Prevention (DLP) and Insider Threat Management (IRM) controls, which become essential when consolidating. No organization runs solely on the likes of Microsoft applications, Microsoft file types, and nothing else, for example. In an era where data security and privacy are paramount, DLP and IRM solutions safeguard data regardless of location. By keeping a vigilant eye on data movements and access patterns, these solutions ensure that while the organization benefits from the efficiencies of a streamlined security infrastructure, data privacy requirements are not compromised.”
Kayla Underkoffler, Lead Security Technologist, HackerOne
“Data Privacy Day serves as a reminder that it’s the collective responsibility of businesses, governments, and individuals to protect sensitive data. As cyber threats continue to become more sophisticated and pervasive, we all must stay vigilant and proactive.
This is particularly crucial amidst the whirlwind of excitement around advancements like generative artificial intelligence (AI). As AI simplifies tasks that were previously highly technical, it is imperative humans remain at the center of shaping and monitoring this automation. Without oversight, overreliance on these tools can exacerbate data security and privacy challenges with flawed code and outputs. Basic security hygiene and human-in-the-loop processes help us remain proactive about reducing this risk in new eras of innovation. Basic tenets such as robust patch management, stringent password policies, and meticulous access control are non-negotiable components in safeguarding organizational data.
As we celebrate Data Privacy Day, organizations must remember following the fundamentals of security ensure the protection of data, our resilience against evolving threats, and a safer internet for everyone.”
The post Navigating the Digital Frontier: Insights from Leading Experts on Data Privacy Day appeared first on Cybersecurity Insiders.
 Source: 2023 Cloud Security Report produced by Cybersecurity Insiders
Source: 2023 Cloud Security Report produced by Cybersecurity Insiders