The evolution of network environments towards distributed, cloud-centric architectures in the work-from-anywhere era has brought unique challenges to network security. The industry’s shift to comprehensive cloud-based services like Secure Access Service Edge (SASE), Security Service Edge (SSE), and Secure SD-WAN reflects the evolving needs of distributed workforces and cloud-centric IT environments in a rapidly evolving threat landscape.
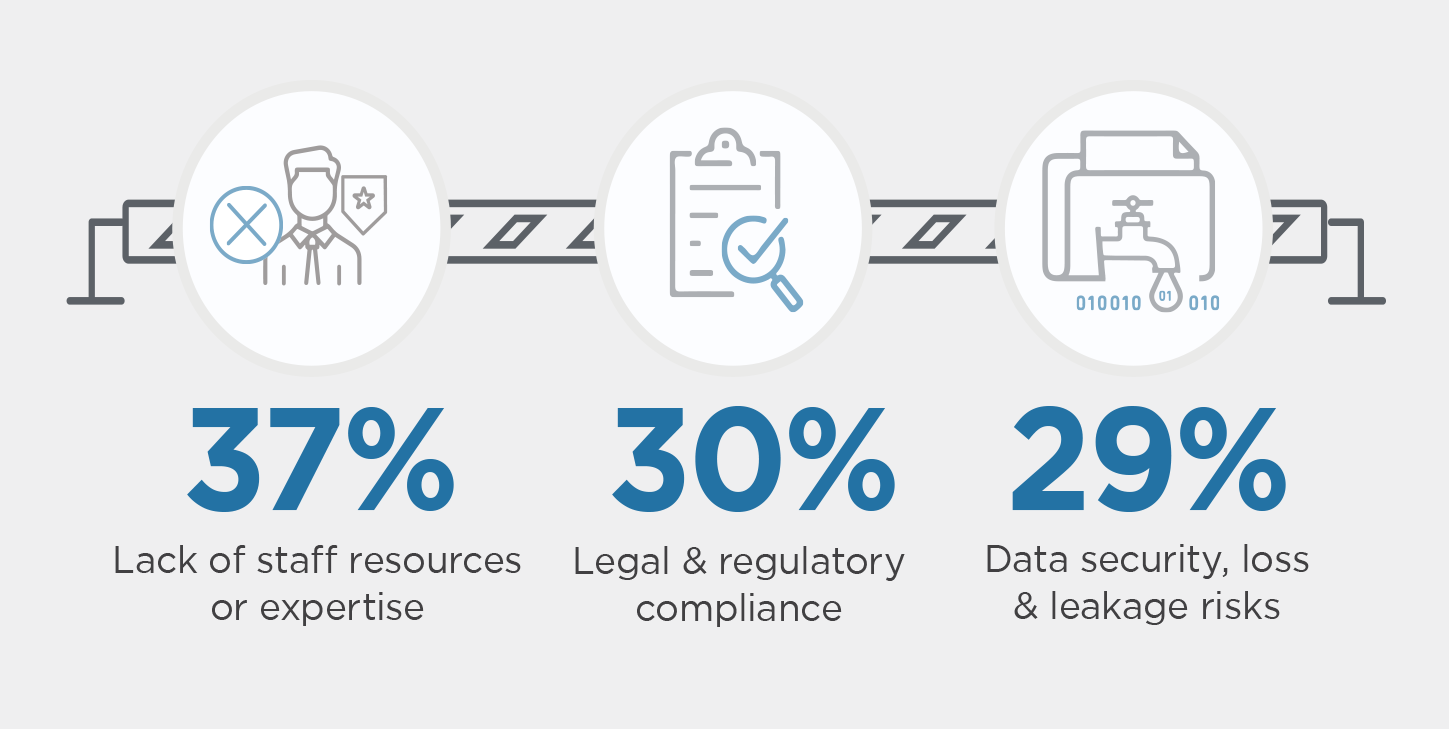
What are the biggest cloud security challenges?
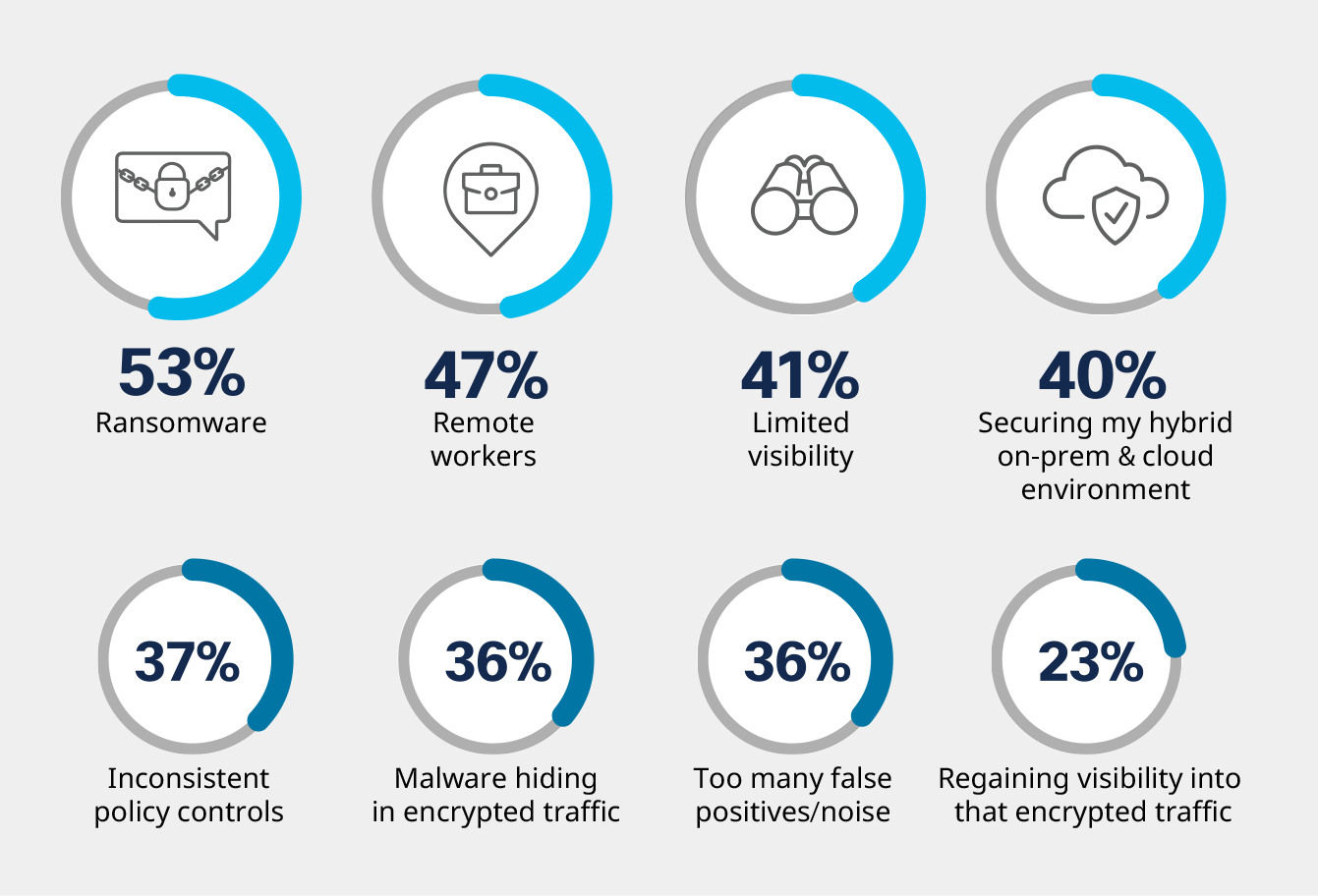
Ransomware (53%) tops list of cloud security challenges, following the recent rise in ransomware attacks. The next biggest security challenge is the shift to remote work and the resulting risks (47%), introduced in the wake of the Covid-19 pandemic. Limited visibility into cyber threats (41%) rounds out the top three security challenges experienced by cybersecurity professionals. [Source: 2022 Security Visibility Report produced by Cybersecurity Insiders]
This shift necessitates a reevaluation of network-based defenses, positioning Intrusion Detection and Prevention Systems (IDS/IPS) as key components in this new ecosystem. The Qosmos Threat Detection Software Development Kit (TD SDK) is Enea’s innovative solution to the demand for more robust, adaptable, and high-performance network threat detection platforms.
“Modern cybersecurity models such as zero-trust networking access and extended detection response pivot around DPI, a trusted technology we all know, but one that’s evolved to meet the needs of the threat landscape today. A strong DPI engine is central to high-performance threat detection. Not only does it enable visibility into network traffic, but it also provides the intelligence around which to base custom rules that customers can tailor to their specific environments.” – Roy Chua, Founder and Principal at AvidThink
ADVANCED THREAT DETECTION WITH SUPERIOR TRAFFIC VISIBILITY
Integrating with Enea’s Qosmos ixEngine®, the market leading deep packet inspection (DPI) engine, the Qosmos TD SDK enables developers to create threat detection solutions with unmatched traffic visibility and sophisticated analysis. Recognizing over 4300 protocols and extracting 5900 metadata types, it provides comprehensive network activity insights to support in-depth, nuanced threat analysis.
Furthermore, the Qosmos ixEngine’s advanced parsers and dissectors significantly help reduce false negatives in threat detection thanks to a much better protocol detection rate compared to standard solutions. This capability is crucial for detecting known and emerging security threats.
In addition, the Qosmos ixEngine is able to identify and classify encrypted and evasive traffic while detecting network anomalies. This extended visibility enables solutions built with the Qosmos TD SDK to more effectively identify complex threats that systems based on traditional IDS might miss, and helps reduce false negatives and positives for more reliable threat detection.
UNMATCHED PERFORMANCE AND SCALABILITY FOR THREAT DETECTION
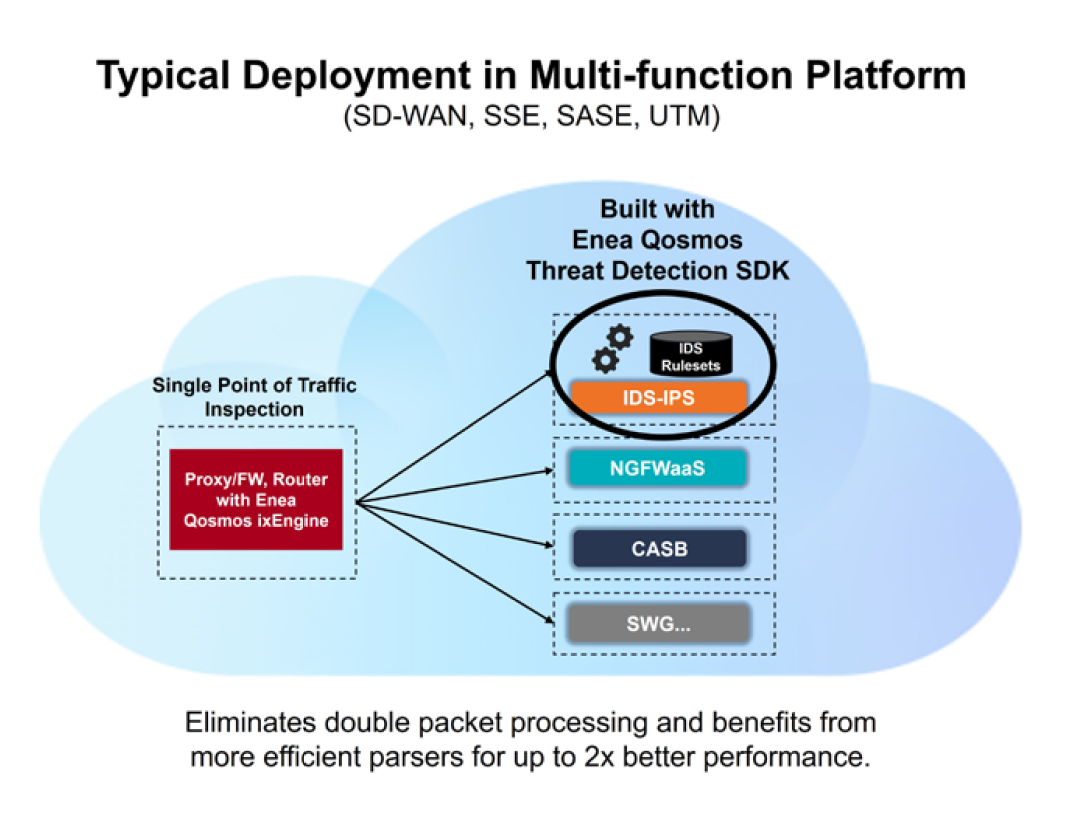
Network-based intrusion detection capabilities have become increasingly important as traditional network perimeters disappear, but open-source IDS are not natively engineered to meet the scalability and performance requirements of modern cloud environments. In addition, as contemporary security solutions require both DPI processing and IDS capabilities, performance is impacted by double packet processing.
The Qosmos TD SDK offers an innovative approach to these performance challenges. Delivered as a software development kit, it leverages Suricata’s industry-leading core IDS functionalities and combines them with the advanced packet inspection capabilities of the Qosmos ixEngine, thereby eliminating the need for double packet parsing. It also significantly accelerates packet processing through linear scaling across multiple CPU cores, and through more efficient packet acquisition and parsing systems.
For example, an IDS built with the Qosmos TD SDK and the Qosmos ixEngine can execute efficient parsing of extracted metadata values – rather than full packets – in order to check for threat signature matches. As a result, solutions built with the Qosmos TD SDK deliver up to double the performance of traditional solutions built using conventional IDS systems.
FLEXIBLE INTEGRATION AND CUSTOMIZABILITY
The availability of threat detection in a software development kit (SDK) is unique in the industry. The Qosmos TD SDK is the first to offer core IDS capabilities as a software component and provides cybersecurity software developers with greater flexibility and improved network protection through tight integration with third party solutions. This means that IDS capabilities can now be one function within a full toolchain, underlying the flexibility offered to security solution developers. The Qosmos TD SDK supports standard open source rulesets and industry available rulesets with Suricata syntax, making
deployment easier and reducing false positives/false negatives.
KEY BENEFITS
• Achieve significantly better performance compared to standard IDS/IPS architectures
• Scale linearly across multiple CPU cores
• Eliminate double packet processing for DPI and IDS in multi-function platforms
• Reduce false positives through extended Enea Qosmos DPI-based network visibility
• Reduce false negatives through improved matching enabled by better parsers
• Create custom rules and improve results through the extended visibility of the Qosmos ixEngine, including recognition of enterprise protocols like LDAP, industrial IIoT/OT protocols, unique security metadata, and much more
• Focus the ruleset matching process on the relevant metadata instead of all packets
TECHNOLOGY
• C library designed to be embedded into applications
• Dedicated APIs for native integration with the Qosmos ixEngine
• Support for standard open source and industry rulesets with Suricata syntax
• Regular updates through open source and industry-recognized Suricata ruleset providers
• Lightweight: ~3 MB & ~15 KB per loaded rule
• Highly configurable to meet CPU and memory requirements
• YAML configuration file for optimal flexibility
• Cloud ready: Manage rulesets per tenant
OUR VERDICT
Enea’s Qosmos Threat Detection SDK is not merely an incremental upgrade to existing security solutions; it is a strategic evolution tailored for the complexities of modern network architectures. Its introduction to the market is timely, addressing the critical needs of agility, precision, and scalability in protecting against threats in both on premises and cloud-centric networks. With the integration of the Qosmos TD SDK, double packet processing is eliminated, parsing speed is accelerated, and traffic insights are vastly expanded to fuel next-generation threat detection and custom rule development.
ABOUT ENEA
Enea is a world-leading specialist in software for telecom and cybersecurity. The company’s cloud-native solutions connect, optimize, and secure services for fixed and mobile subscribers, enterprises, and the Internet of Things. More than 100 communication service providers and 4.5 billion people rely on Enea technologies every day. Enea’s Qosmos technology is the most widely deployed Deep Packet Inspection (DPI) technology in cybersecurity and networking solutions. With 75% market share, it is the de facto industry standard for embedded Traffic Intelligence in cybersecurity and networking. Enea Qosmos products classify traffic in real-time and provide granular information about network activities. Enea also offers IDS-based threat detection capabilities as an SDK, enabling easy and tight integration with cybersecurity solutions while remaining highly flexible and scalable. Enea is headquartered in Stockholm, Sweden, and is listed on Nasdaq Stockholm.
Learn more at www.enea.com
The post PRODUCT REVIEW: ENEA QOSMOS THREAT DETECTION SDK appeared first on Cybersecurity Insiders.