The management of day-to-day cloud security operations presents a multifaceted challenge for organizations, requiring a delicate balance between technological, procedural, and human factors. Multi-cloud environments significantly increase the complexity and challenges of managing and securing cloud workloads. To effectively address these challenges, organizations should leverage integrated security solutions that offer visibility and control across multi-cloud environments, supporting consistent data protection and privacy standards. Emphasizing partnerships with vendors that provide comprehensive multi-cloud security capabilities and fostering skills development can empower businesses to overcome the complexity of securing multi-cloud architectures. This approach not only mitigates the identified challenges but also harnesses the full potential of multi-cloud environments for enhanced agility, scalability, and innovation.
What are your biggest challenges securing multi-cloud environments?
Multi-cloud environments significantly increase the complexity and challenges of securing cloud workloads. Ensuring data protection and privacy in each environment is identified as the most significant multi-cloud security challenge, with 55% of respondents highlighting it as a concern.
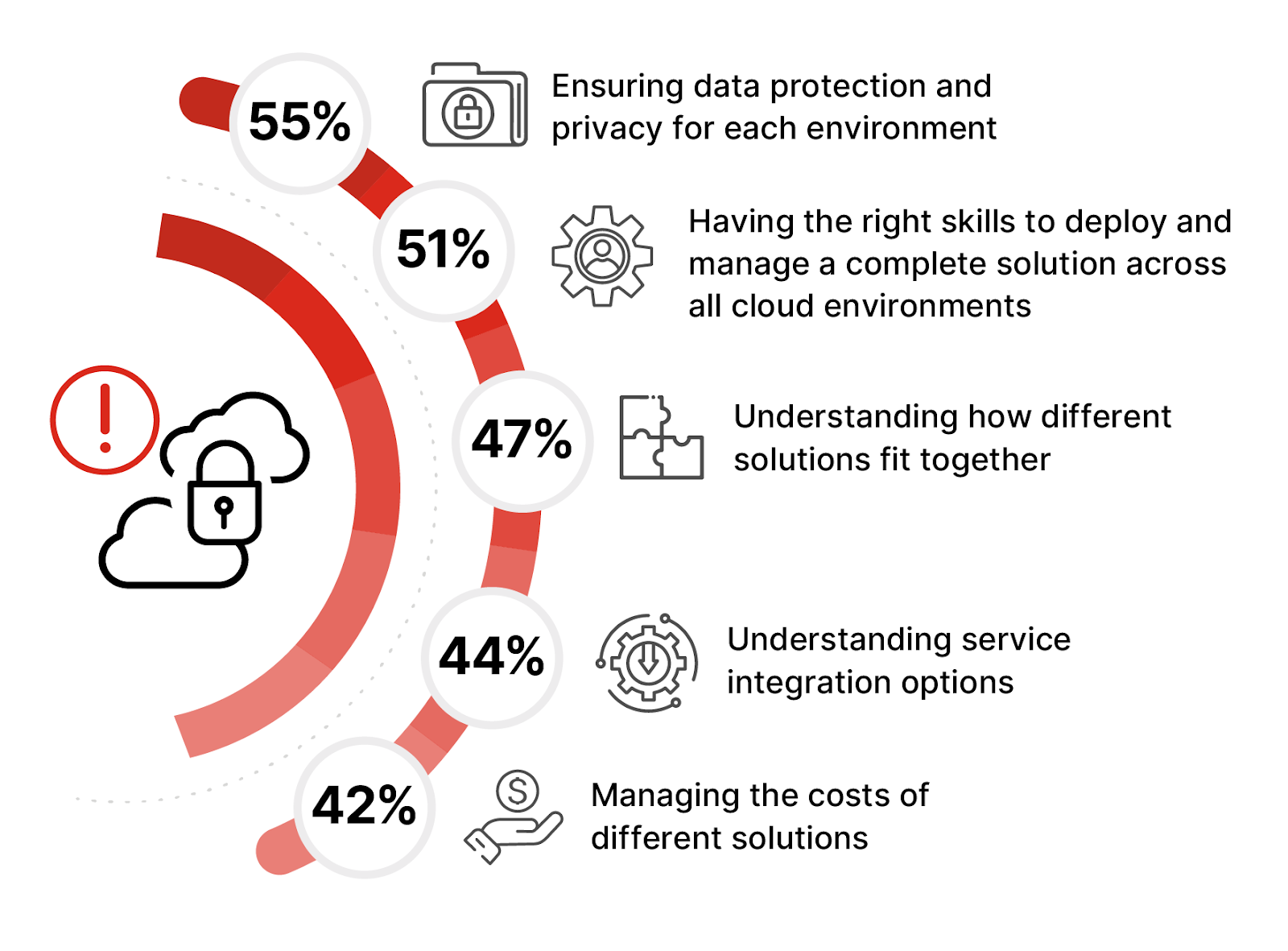
Source: 2024 Cloud Security Report produced by Cybersecurity Insiders
INTRODUCING THE FORTINET FORTIGATE CLOUD NATIVE FIREWALL (CNF)
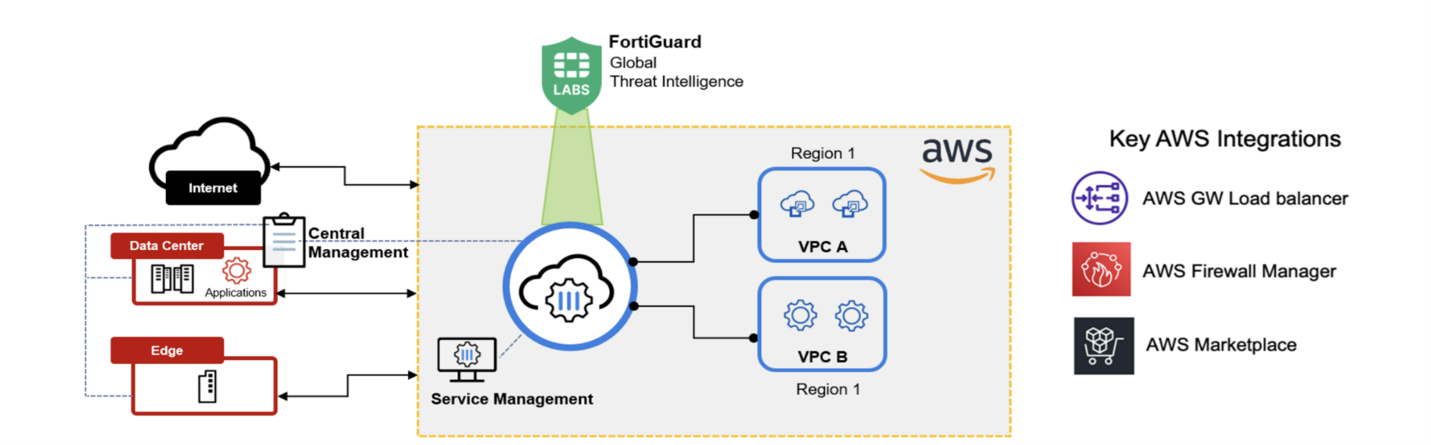
FortiGate Cloud-Native Firewall (CNF) is a SaaS delivered Next Generation Firewall (NGFW) service designed for cloud environments, offering scalable security for outbound traffic from multiple cloud networks without requiring network redesign or infrastructure management. It supports geolocation policies, malware protection, and compliance enforcement. Automatically scaling its network protection on AWS, FortiGate CNF meets the dynamic demands of cloud computing with ease.
“With FortiGate CNF, customers can build confidently, boost agility, and take advantage of everything AWS has to offer. As a fully managed cloud-native service, FortiGate CNF provides enterprise-level firewall services and network security that help reduce risk, improve compliance, and optimize customers’ security investments.”
–Dave Ward, GM, Application Networking, AWS
FortiGate Cloud-Native Firewall (CNF) confronts a broad spectrum of security challenges that plague modern cloud environments, focusing on mitigating threats associated with unsecured outbound traffic.
These challenges include, but are not limited to:
- Malware: FortiGate CNF provides robust protection against connections to compromised servers, which could lead to unintentional malware downloads. By monitoring and controlling outbound traffic, it prevents malware from infiltrating the network.
- Data Exfiltration: The solution addresses the critical issue of data exfiltration by blocking compromised systems from communicating out and sending sensitive data to unauthorized systems. This is vital for safeguarding proprietary and personal data against external threats.
- Command and Control (C2) Communication: It effectively cuts off compromised workloads from communicating with C2 servers. By preventing these communications, FortiGate CNF disrupts the ability of attackers to execute commands or steal data, thus neutralizing the threat.
- Crypto Mining: By identifying and blocking connections to IPs known for exploiting cloud resources for crypto mining purposes, FortiGate CNF ensures that organizational resources are not siphoned off for malicious gain.
- Compliance Violations: The solution enforces compliance by preventing unauthorized communications with restricted or prohibited countries, systems, or entities. This feature is particularly crucial for organizations needing to adhere to strict regulatory and compliance guidelines.
KEY CAPABILITIES
FortiGate Cloud-Native Firewall (CNF) offers a suite of key features designed to fortify cloud environments against a wide range of cyber threats, ensuring seamless integration, dynamic scalability, and stringent compliance with regulatory standards.
1. Egress Security: In today’s landscape, where cloud adoption is ubiquitous, securing egress traffic has become paramount. Egress security from FortiGate CNF mitigates risks such as data exfiltration, malware propagation, and botnet activities. It enables organizations to control traffic leaving their cloud environments, ensuring that sensitive data remains protected and that malicious communications are effectively blocked.
2. Known Bad IP Filtering: Leveraging FortiGuard Labs IP Reputation Intelligence, this feature enhances security by preventing access to malicious IPs and Command and Control servers. This proactive measure significantly reduces the risk of security breaches and cyber attacks, ensuring that organizational resources are safeguarded against known threats.
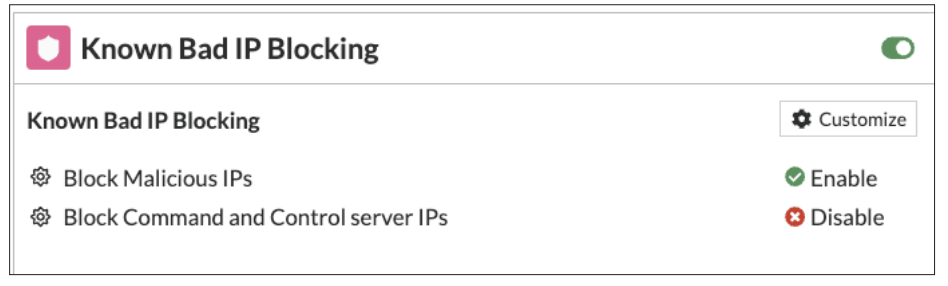
Figure 1 – Known Bad IP Blocking in FortiGate CNF
3. Geo Fencing: Geo Fencing provides the ability to enforce country-level security policies with ease, a crucial capability for organizations needing to comply with regulatory requirements or to implement geographic restrictions on their cloud resources. This feature simplifies the enforcement of geo-specific rules, aiding in compliance and data sovereignty efforts.
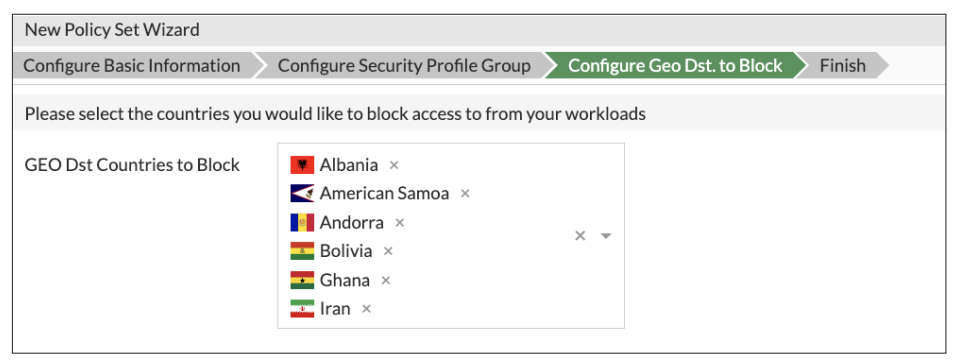
Figure 2 – Geo Fencing Example
4. East-West Security: Protecting cloud-based workloads— including dynamic objects like serverless resources, Kubernetes resources, and auto-scaling groups— is essential for maintaining the integrity of internal networks. By enforcing network security policies dynamically, FortiGate CNF ensures comprehensive protection, facilitating secure communication and data transfer within cloud environments.
5. Dynamic Security: The ability to define security policies using intuitive objects (like countries, FQDNs, and AWS resource metadata) empowers organizations to adapt swiftly to changes in their cloud environments. This dynamic security approach reduces the need for constant manual policy updates, enhancing efficiency and responsiveness.
6. Regulatory Compliance: Assisting in meeting various regulatory compliance requirements, such as GDPR, HIPAA, and PCI-DSS, FortiGate CNF helps organizations protect sensitive data and maintain privacy standards. This capability is invaluable for businesses in highly regulated industries, providing a foundation for compliance and data protection strategies.
7. FortiGuard Labs Services: Integration with FortiGuard Labs ensures that FortiGate CNF benefits from up-to-date security intelligence, including multiple security signatures and IP reputation information. This integration enhances the overall security efficacy, offering proactive protection against emerging and existing threats.
8. AWS Firewall Manager Integration: The automation of VPC attachment and policy rollouts through AWS Firewall Manager underscores FortiGate CNF’s commitment to seamless integration and ease of use within the AWS ecosystem. This feature streamlines security management, allowing for more efficient and centralized control over cloud security policies.
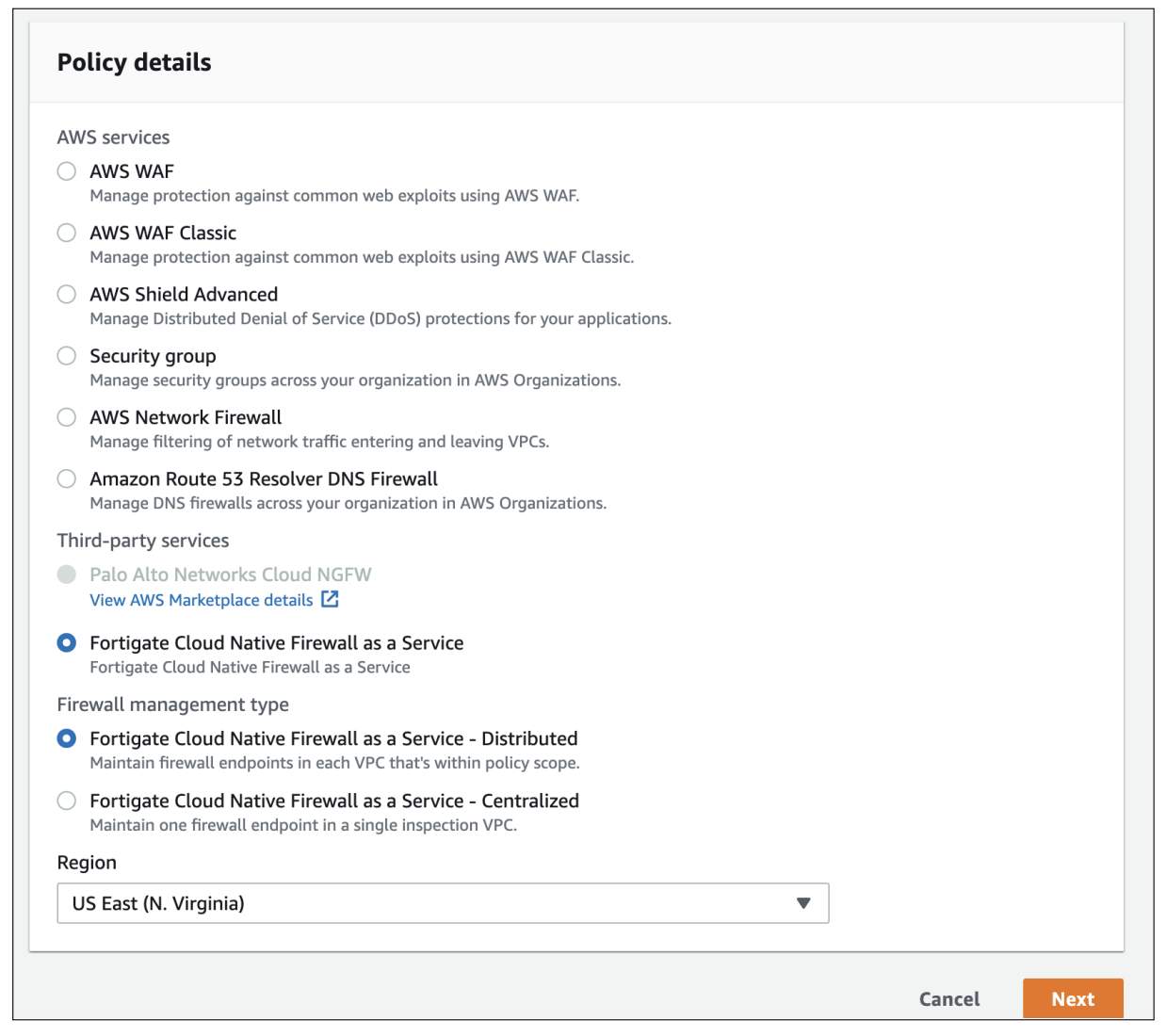
Figure 3 – AWS Firewall Manager Integration
9. Advanced Network Security: By offering the latest in network security functionalities, such as IPS, AV, and SSL inspection, managed through FortiManager, FortiGate CNF ensures that organizations can maintain a high level of security without compromising on performance. This comprehensive coverage is essential for defending against sophisticated cyber threats.
10. FortiManager and FortiAnalyzer Integration: The seamless integration with FortiManager and FortiAnalyzer provides advanced management and analytics capabilities. This cohesive integration allows for the centralized management of security policies and insightful analytics, enhancing operational efficiency and security visibility across the network.
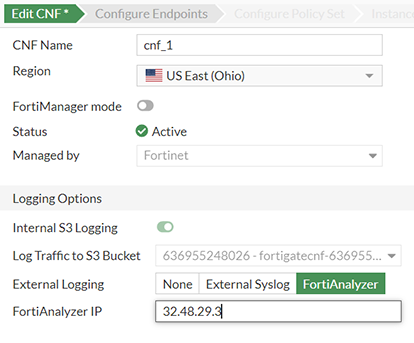
Figure 4 – Configuring FortiGate CNF to Send Logs to FortiAnalyzer
“We have been using FortiGate Cloud-Native Firewall for a few years now. It is the most stable and recommended firewall. Users with less technical knowledge can easily manage complex network and security components using it.” -Senior System Administrator
KEY BENEFITS
FortiGate Cloud-Native Firewall (CNF) stands out as a comprehensive solution for securing cloud environments, combining advanced technology and user-centric features to deliver unparalleled security. Here’s an overview of the key benefits that underscore its unique position in the market:
1. Market-Leading Security: FortiGate CNF is powered by Fortinet’s cutting-edge Next Generation Firewall (NGFW) technology, including intrusion prevention systems (IPS) and advanced threat intelligence from FortiGuard. This robust security framework ensures real-time protection against emerging and sophisticated threats.
2. Frictionless Deployment: Designed with cloud first principles, FortiGate CNF offers a seamless deployment experience, optimizing protection for cloud networks. Its cloud-native architecture ensures that it integrates effortlessly with existing cloud infrastructures, making it an ideal solution for modern digital enterprises.
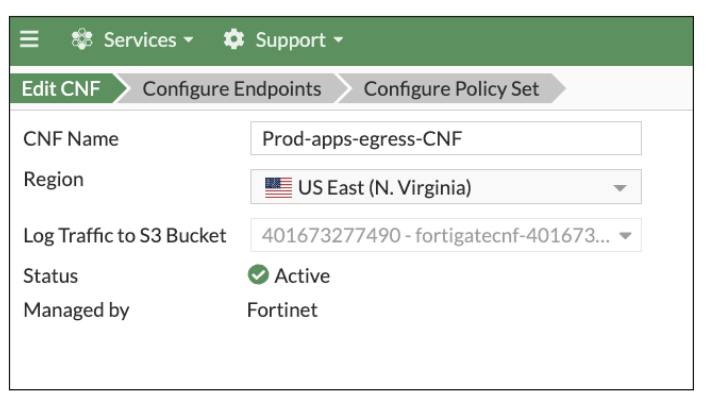
Figure 5 – The Easy-To-Use Deployment Wizard in FortiGate CNF
3. Cost-Effective Security: With its pay-for-use security model, FortiGate CNF allows organizations to only pay for the traffic that is secured across their cloud accounts, networks, and workloads. This flexible pricing ensures that businesses can maintain robust security without incurring unnecessary costs.
4. Simplified Security Management: The intuitive dashboard and predefined policies of FortiGate CNF streamline the security setup process. Customers can easily specify their security policies and network preferences, while FortiGate CNF handles the complex aspects of security management, offering a hands-off approach to network protection.
5. Consolidated Security Architecture: A single FortiGate CNF instance can protect multiple AWS accounts, networks, VPCs, and availability zones within a region. This capability provides significant economic advantages by reducing the need for multiple security solutions and simplifying the security architecture.
6. Dynamic Security Policies: FortiGate CNF’s dynamic security policies offer consistent protection that adapts to changes in cloud workloads. This eliminates the need for manual updates to security policies when IP addresses or workloads change, ensuring continuous and effective security coverage.
7. Flexible Management Options: With integration options for FortiManager and AWS Firewall Manager, FortiGate CNF provides unified control over security policies across cloud and hybrid environments. This flexibility allows for consistent security management, regardless of the deployment model or environment.
QUICK DEPLOYMENT AND FLEXIBLE PRICING OF FORTIGATE CNF
FortiGate CNF is a cloud-delivered SaaS solution that can be deployed rapidly, often within 15 minutes, offering a swift enhancement to security postures with minimal downtime. It utilizes a flexible, pay-as-you-go pricing model, billed monthly based on actual consumption, ensuring cost efficiency and scalability for organizations. This approach, combined with the option for procurement through private offers or partnerships, makes FortiGate CNF a highly accessible and adaptable security solution for modern cloud environments.
OUR VERDICT
In conclusion, FortiGate CNF is set to revolutionize how organizations approach cloud security. By streamlining security operations through the automation of infrastructure management and the deployment of predefined policies, it significantly reduces the time to protection, enabling security teams to concentrate on higher level strategic initiatives. Furthermore, FortiGate CNF’s comprehensive coverage across outbound, east-west, and inbound traffic fortifies customers’ security posture, ensuring thorough protection against a broad spectrum of threats.
The blend of enhanced security, operational efficiency, and cost-effectiveness positions FortiGate CNF as a cornerstone of modern cloud security frameworks, underscoring its value for businesses aiming to navigate the complexities of today’s digital landscape safely.
ABOUT FORTINET
Fortinet (NASDAQ: FTNT) is a driving force in the evolution of cybersecurity and the convergence of networking and security.
Our mission is to secure people, devices, and data everywhere, and today we deliver cybersecurity everywhere you need it with the largest integrated portfolio of over 50 enterprise grade products.
Well over half a million customers trust Fortinet’s solutions, which are among the most deployed, most patented, and most validated in the industry.
FOR MORE INFORMATION: aws.fortigatecnf.com
The post FORTIGATE CLOUD NATIVE FIREWALL (FORTIGATE CNF) appeared first on Cybersecurity Insiders.