In the rapidly evolving iGaming industry, platforms such as online casinos, sportsbooks, and jackpot services have become prime targets for cybercriminals. These malicious actors aim to exploit vulnerabilities to steal funds, abuse promotional offers, and compromise both player and operator accounts.
To achieve their goals, attackers deploy a variety of techniques and tactics, each with its own level of sophistication and impact. While many traditional methods of attack – such as brute force, phishing, and trojans – continue to plague the industry, the growing prevalence of credential stuffing is particularly concerning. Over the past few years, we have identified a troubling trend: attackers are increasingly leveraging credential stuffing as one of the most effective vectors for targeting iGaming platforms. This type of attack thrives on the massive volume of leaked credentials available on the dark web, combined with widespread password reuse – a behavior that is alarmingly common.
At SOFTSWISS, we understand the critical challenges faced by iGaming operators and stakeholders in defending their platforms from increasingly sophisticated cyberattacks. With years of experience in the industry, we have observed firsthand how threats like credential stuffing not only jeopardize security but also impact reputation, player trust, and overall business performance.
Given its prevalence and impact, we believe it is essential to address credential stuffing directly and collaborate with the broader iGaming community to mitigate its risks. By sharing insights from our experience and practical solutions, we aim to empower operators, security professionals, and stakeholders to recognize, prevent, and effectively respond to these growing threats.
Key Cyber Threat Vectors in iGaming
To build a comprehensive understanding of how cybercriminals exploit weaknesses in iGaming platforms, it’s essential to analyze the primary methods they rely on. These approaches range from traditional tactics to increasingly sophisticated strategies, each presenting distinct challenges for operators:
- Account Theft: Exploiting stolen credentials to gain unauthorized access.
- Credential Stuffing: Using breached username and password pairs in bulk to automate login attempts.
- Brute Force Attacks: Systematically guessing passwords until one works.
- Trojans/Stealers: Infecting devices with malware designed to capture sensitive data.
Another common vector involves scams disguised as legitimate tools:
- Deceptive Third-Party Services: Fake platforms claiming to simplify data visualization – such as allegedly helpful “tracking software” for iGaming affiliates – but in reality collecting user credentials
- Fake Mirror Sites: Counterfeit versions of legitimate iGaming websites, used to deceive users into submitting their credentials.
Additionally, multi-accounting strategies pose a significant threat:
- Account Farming: Generating new accounts to exploit bonuses.
- Stolen Account Abuse: Using compromised accounts for fraudulent activities.
Among these, credential stuffing stands out as one of the most damaging attack vectors in 2024. By leveraging enormous troves of leaked credentials sourced from the dark web, attackers can infiltrate multiple user accounts with minimal effort. In the following sections, we will delve deeper into how credential stuffing works, why it is so effective in the iGaming environment, the specific damages it causes, and effective strategies for protection and mitigation.
Understanding Credential Stuffing
Credential stuffing is a cyberattack in which attackers rely on automated tools to test large volumes of stolen username/password pairs across multiple platforms. This method thrives on the common habit of password reuse: if a user’s credentials leak from one platform and they employ the same combination elsewhere, attackers can gain access to those other accounts with ease.
Rapid Growth and Availability of Credentials
The surge in data breaches has led to an abundance of compromised credentials available on dark web forums. These ready-made lists, often containing millions of username-password pairs, make it easier than ever for attackers to target iGaming platforms. The problem is exacerbated by the continuous discovery of new data leaks and the willingness of users to reuse passwords across different sites-allowing even relatively unsophisticated attackers to break into accounts on casinos, sportsbooks, and affiliate dashboards.
Double Risk for iGaming Industry
In iGaming, the stakes are higher. Unlike many mainstream services, compromised accounts here can grant direct access to funds, valuable loyalty rewards, or sensitive player information. Moreover, not only players but also operator employees and back-office administrators may be targeted, further increasing the impact of a successful attack.
Root Causes of Credential Stuffing Success
- Password Reuse: Users often employ the same password across multiple sites for convenience.
- Large-Scale Data Breaches: Massive databases of stolen credentials are readily available to malicious actors.
- Low Barrier to Entry: Credential stuffing tools are inexpensive, widely available, and easy to use, making these attacks attractive even to low-skilled cybercriminals.
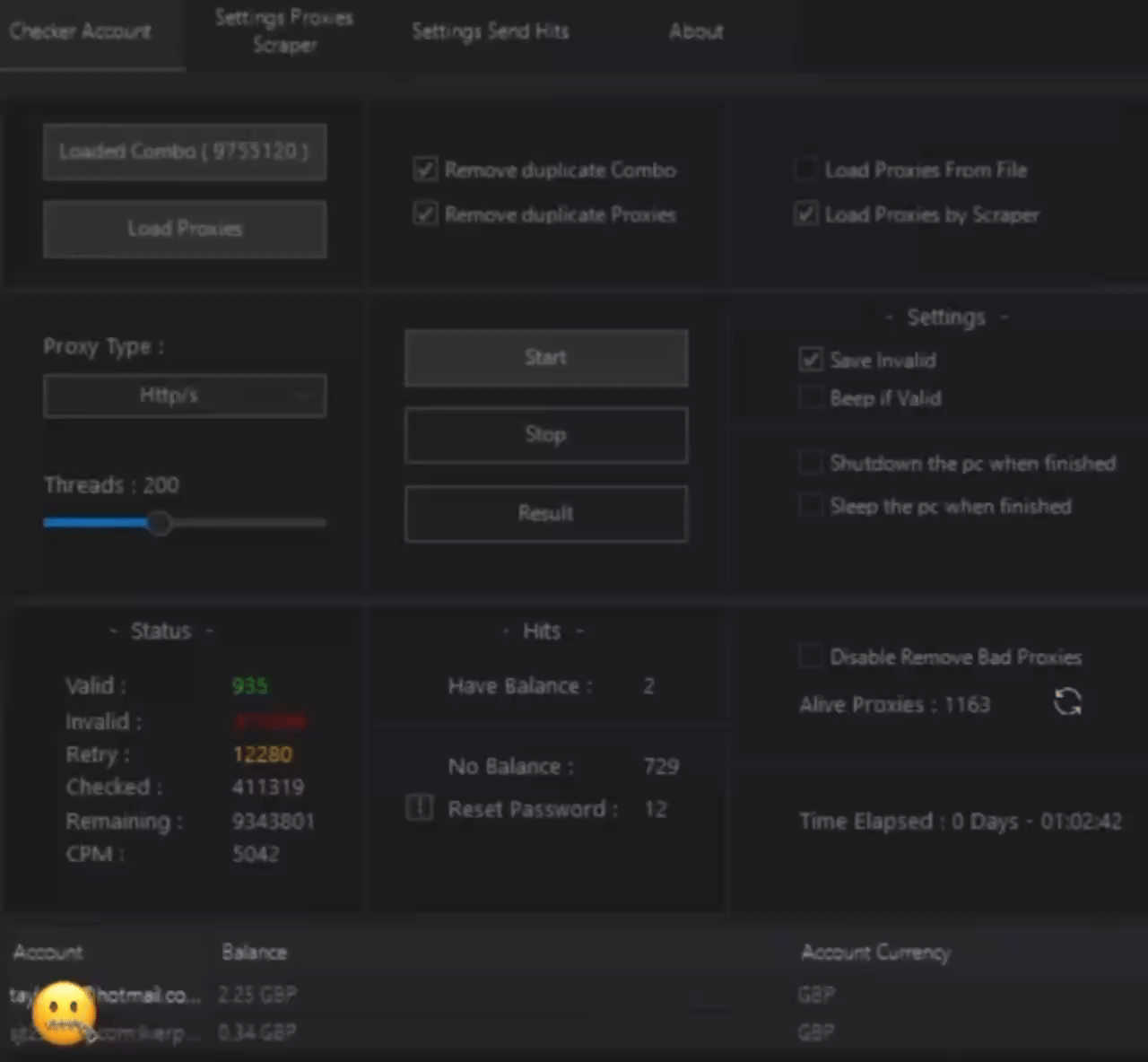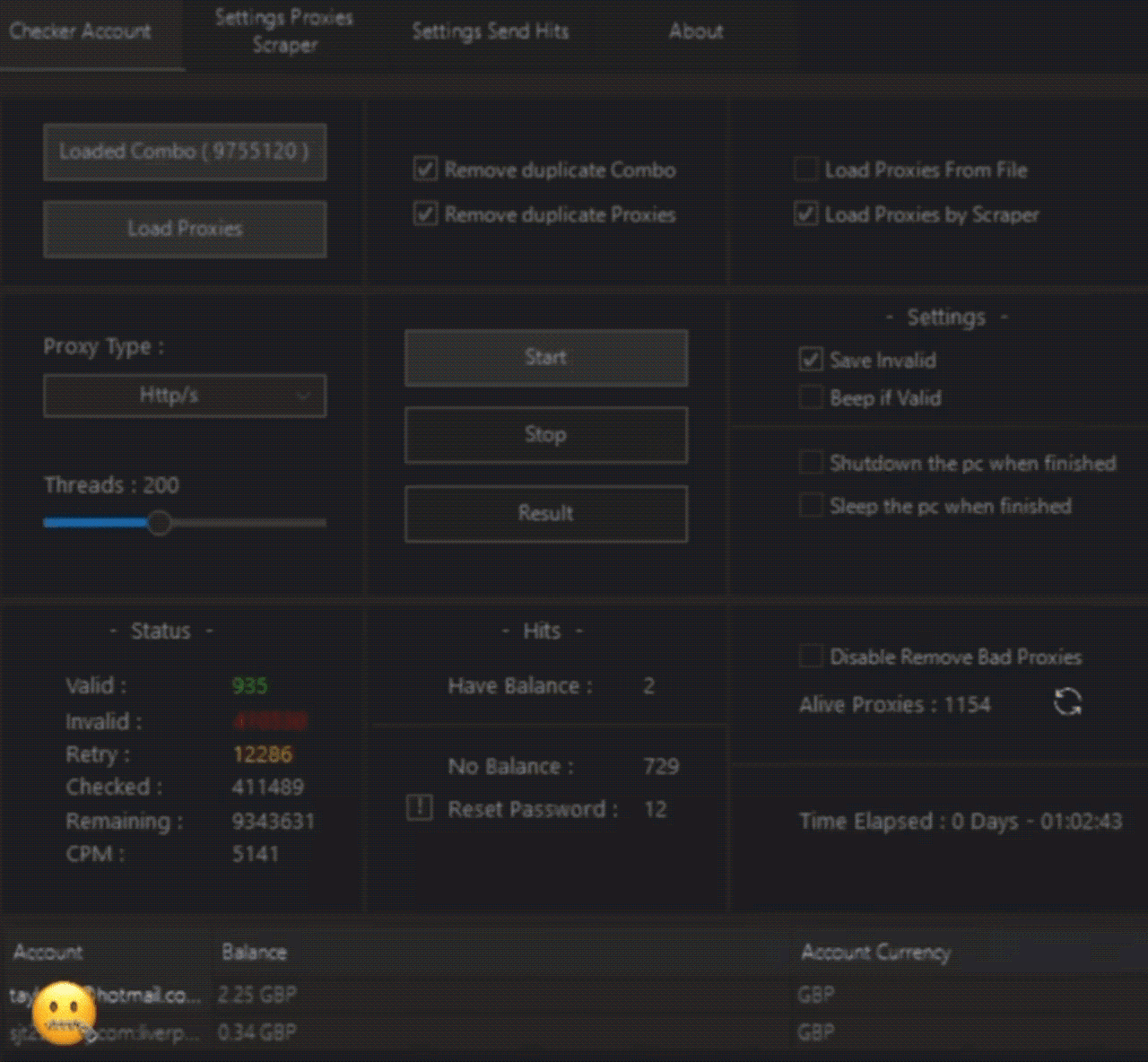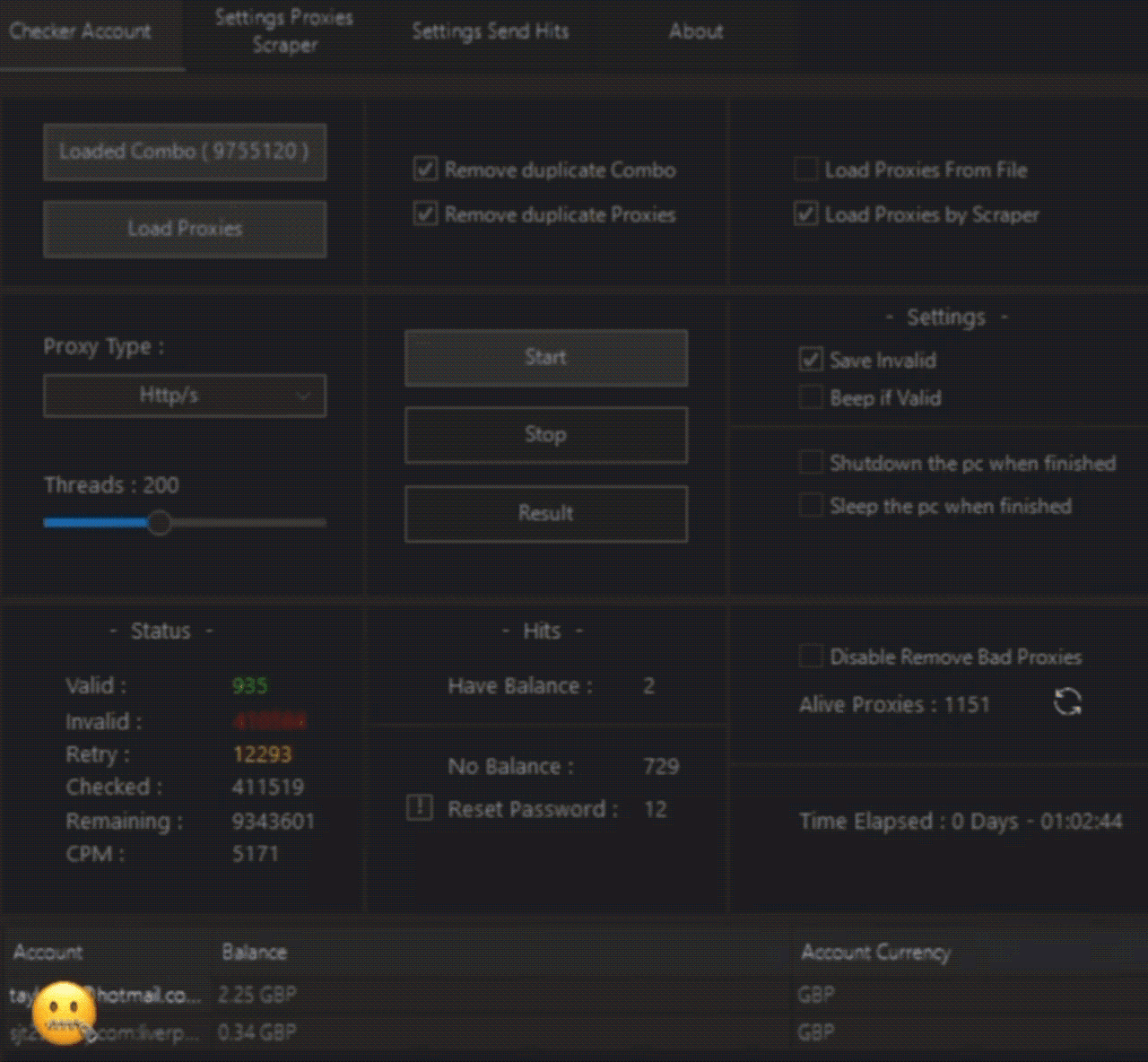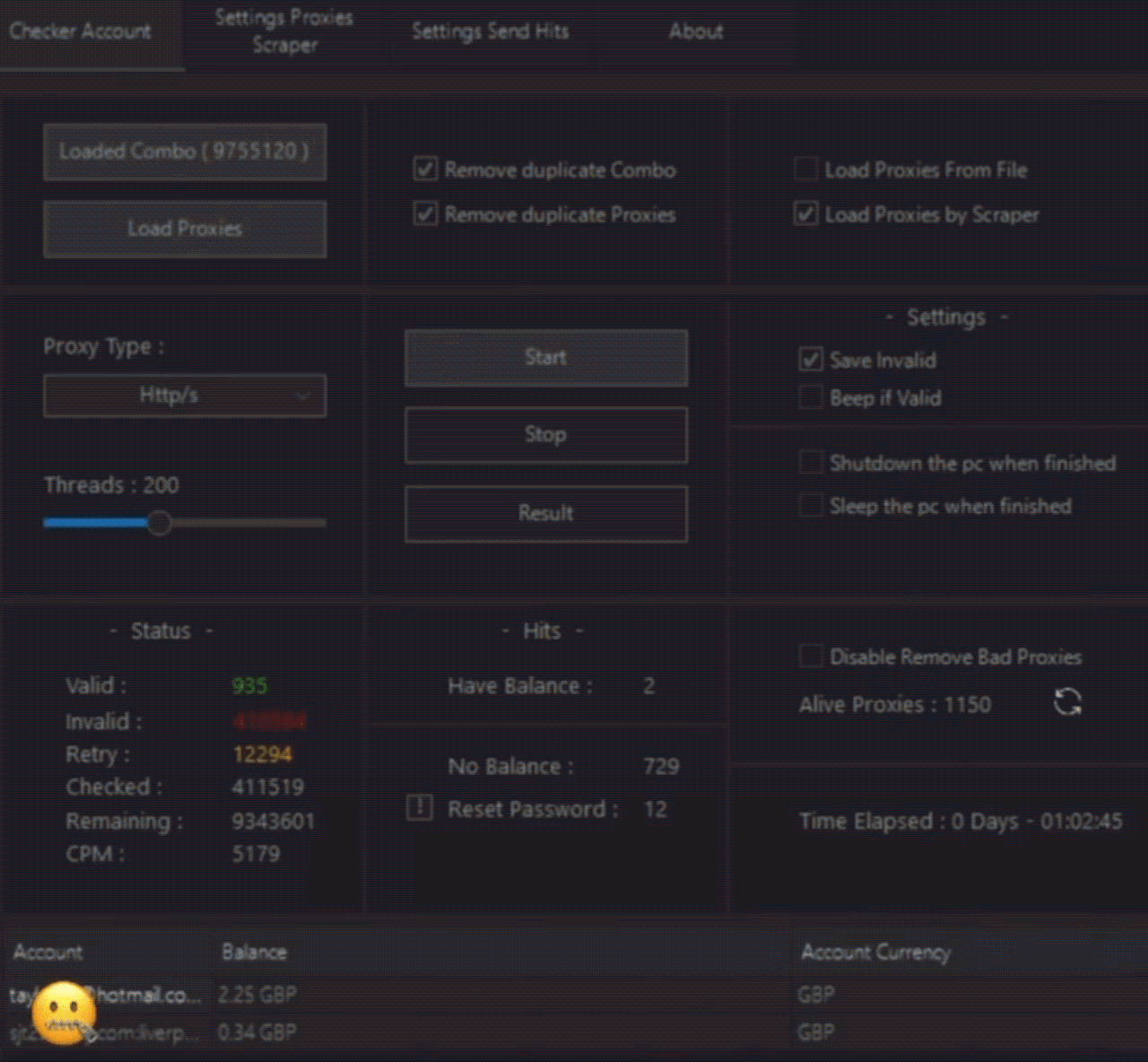
Picture 1. How credential checkers for different services work
Consequences for Players and Operators
For compromised account holders:
- Financial Losses: Attackers can empty balances, steal winnings, and redeem promotional credits.
- Personal Exposure: Sensitive information (e.g., names, emails, addresses) may be leaked or sold.
- Further Fraud: Account hijacking can lead to extortion or blackmail, threatening to expose personal details or gambling habits.
For iGaming service operators:
- Reputational Damage: Breached casinos and betting platforms risk losing player trust, resulting in churn and reduced revenue.
- Legal and Financial Liability: Operators may face regulatory fines, chargebacks, and lawsuits from aggrieved customers.
- Competitive Disadvantage: Stolen accounts can be resold to competitors or used to infiltrate affiliate programs, skewing marketing campaigns and incentives.
Common Misdiagnoses and Pitfalls
A frequent mistake in combating credential stuffing is misidentifying it as a DDoS attack.

Because credential stuffing can generate large volumes of login attempts, it’s easy to focus solely on the surge in requests and mistake it for a conventional overload attempt. If the platform remains operational, a support team might assume it’s merely a failed DDoS or a user traffic spike due to a marketing campaign. This misunderstanding can prevent the implementation of necessary countermeasures, allowing attackers to continue compromising accounts undetected.
Infrastructure Overloads and Operational Strain
In addition to the risk of incorrect classification, large-scale automated login attempts can impose heavy loads on authentication systems and backend infrastructures. Sudden surges in credential validation requests degrade performance, cause production incidents, and can lead to downtime. Under these conditions, engineers scramble to restore normalcy, while users face delays, errors, or outages. Over time, repeated incidents erode player trust, harm brand reputation, and diminish user satisfaction-all of which can negatively impact critical business metrics like conversions, registrations, and first-time deposits (FTDs).
Lack of Preventative Measures and Business Trade-Offs
Another pitfall is the absence of proactive security measures-such as CAPTCHAs, MFA, or advanced bot protection. In our experience, this reluctance often stems from concerns that additional security steps may introduce friction into the carefully optimized Customer Journey Map. Every extra authentication prompt or verification challenge potentially elongates the path from a visitor’s first interaction with the site to their initial deposit. In highly competitive markets, operators frequently prioritize maximizing conversion rates of their marketing campaigns and ensuring a seamless onboarding flow. The fear is that any added friction-be it a CAPTCHA at sign-up or MFA at login-could deter new players, reduce promotional effectiveness, and ultimately lower the ratio of players who reach that critical first-time deposit milestone.
From a unit economics perspective, each additional step in the user journey can influence key performance indicators like Customer Acquisition Cost (CAC) and Lifetime Value (LTV). While more robust security measures offer long-term benefits in terms of trust and brand reputation, operators may weigh these gains against the potential short-term downturn in conversions, registrations, or FTDs. As a result, they may opt for fewer preventative measures to maintain business agility and immediate competitiveness, even though this choice leaves the platform more vulnerable to credential stuffing attacks.
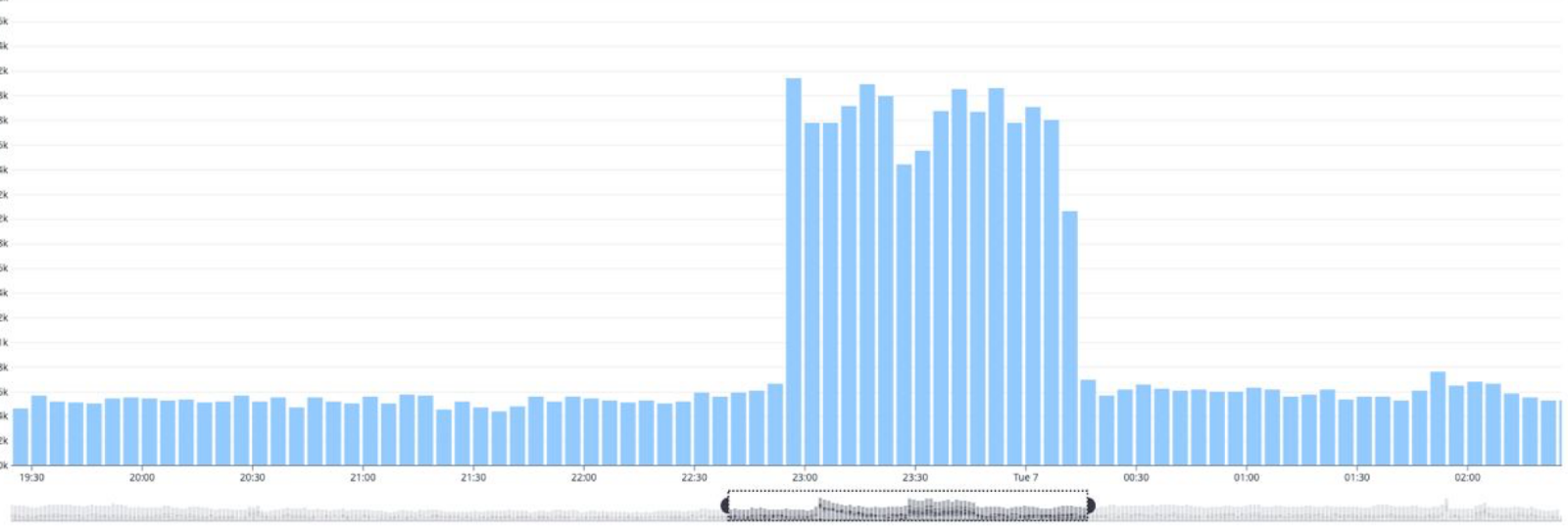
Picture 2. This is what a successful Credentials stuffing attack pattern looks like on the charts – if you don’t take preventive defense measures
Importance of Post-Attack Analysis
Halting an ongoing credential stuffing attack is not the end of the story. If attackers have successfully accessed a range of accounts, they may now possess information allowing them to exploit these compromised credentials over the long term. Even if no suspicious transactions are immediately apparent, adversaries can silently observe these accounts, waiting for favorable conditions to strike again. They might periodically revisit accounts to check for newly deposited funds, watch for incoming promotional credits, or leverage accrued loyalty points and bonuses. Without thorough post-incident analysis, operators risk overlooking these hidden threats, ultimately giving attackers the opportunity to profit when circumstances are most advantageous.
Informed by our experience with iGaming operators and incident analysis, we believe that continuous monitoring and targeted countermeasures may sometimes be more suitable than drastic, broad-stroke responses. For example, operators may consider forced password resets as an emergency measure – an action that can potentially prompt negative reactions and impact player trust. However, in some scenarios it may be more effective to explore alternative approaches, such as implementing advanced anomaly detection, scrutinizing unusual withdrawal requests, or temporarily flagging suspicious accounts for further review.
Additionally, analyzing patterns in attacker behavior, user activity logs, and infrastructure metrics can yield valuable insights. By identifying which accounts were compromised, understanding how credential pairs were tested, and recognizing common characteristics of such attacks (e.g., patterns in geolocation or timing), operators can more accurately adjust and refine their preventive measures. Over time, this data-driven approach enhances platform resilience without imposing unnecessary burdens on legitimate players. By maintaining vigilant oversight after an incident, operators can find the right balance between bolstering security and preserving a seamless player experience. Continuous evaluation, pattern analysis, and selective verification ensure that even after stopping an attack, the platform remains prepared to detect and deter future attempts at abuse-thereby sustaining player confidence and satisfaction.
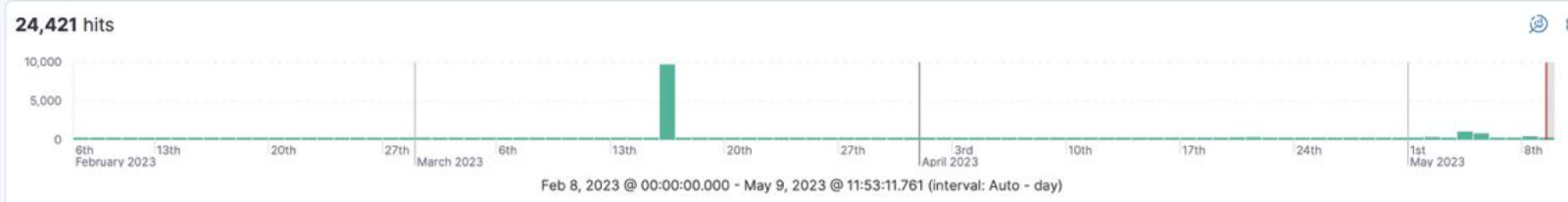
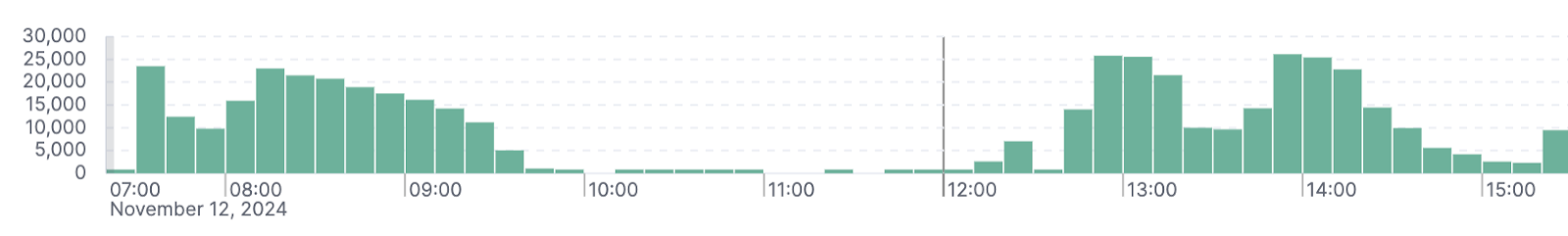
Picture 3. How the beginning and fading of an attack can be displayed on charts
In essence, effective post-incident strategy extends beyond simply ending the attack. A proactive, well-considered approach-based on our own experience and observations-not only safeguards player interests but also reinforces confidence in the platform’s long-term reliability and integrity.
By acknowledging these pitfalls – misidentifying attacks, underestimating infrastructure stress, downplaying proactive security due to perceived business trade-offs, and neglecting post-attack analysis-operators can take a more informed and balanced approach. Implementing user-friendly yet effective security measures not only mitigates credential stuffing risks but also supports long-term stability, player trust, and sustainable growth.
How SOFTSWISS Combated Credential Stuffing
This fall, one of our clients experienced a credential stuffing attack that leveraged more than 1,000,000 IP addresses originating from diverse geolocations. By utilizing such a vast and globally distributed pool of IPs, the attackers effectively bypassed rate limits and other basic technical safeguards.
Once the incident was detected, our response teams promptly stepped in. Through careful analysis, we identified a specific attack pattern and implemented targeted measures to block it. Leveraging our tailored approaches and extensive experience in combating similar attacks, we uncovered behavioral patterns characteristic of a botnet network. By analyzing these patterns, such as synchronized login attempts and traffic anomalies, we dynamically adjusted our response to neutralize the ongoing threat.
After some time, the attackers adjusted their approach and launched another attempt. Our systems quickly recognized the altered behavior – including changes in IP distribution and user-agent strings – and proactively refined our defenses by introducing additional smart restrictions tailored to high-risk geolocations. These adjustments ensured that legitimate users could continue to access the platform without interruption while significantly raising the barriers for attackers.
The result was a successful defense, illustrating the importance of continuous monitoring, timely intervention, and the ability to adapt strategies in response to evolving threats. This case demonstrates the value of combining advanced threat detection methodologies, big data analytics, and a tailored incident response framework to stay ahead of evolving cyberattacks.
How to Protect Against Credential Stuffing
Defending against credential stuffing attacks calls for a strategic blend of measures. Operators must balance security requirements with usability, performance, and business goals. While implementing additional safeguards can introduce friction and potentially affect certain metrics, it is often preferable to address these trade-offs early rather than face more severe consequences later. By selecting and combining the right measures – and adjusting them over time – operators can significantly reduce the risk and impact of credential stuffing attacks.
1. CAPTCHA
Introducing CAPTCHA at the authentication stage is an effective way to complicate and increase the cost of executing credential stuffing attacks for cybercriminals. This approach significantly raises the difficulty threshold for large-scale automated authentication attempts.
•Limitations:
- CAPTCHAs can inconvenience legitimate users, potentially reducing conversion rates.
- Some players may fail CAPTCHAs due to technical issues, accessibility challenges, or user error, impacting user satisfaction and key performance indicators.
•Bypassing Techniques:
Human or automated solver services and advancing AI-based solvers mean CAPTCHAs aren’t foolproof.
•Targeted Use Cases:
Consider deploying CAPTCHAs selectively, for example, only in suspicious geolocations that do not align with your primary market. This approach preserves a smooth experience for most players while limiting automated attacks from non-targeted regions.
CAPTCHAs can also be enabled as an emergency measure during an ongoing attack, buying valuable time for the incident response team to identify and block the underlying pattern.
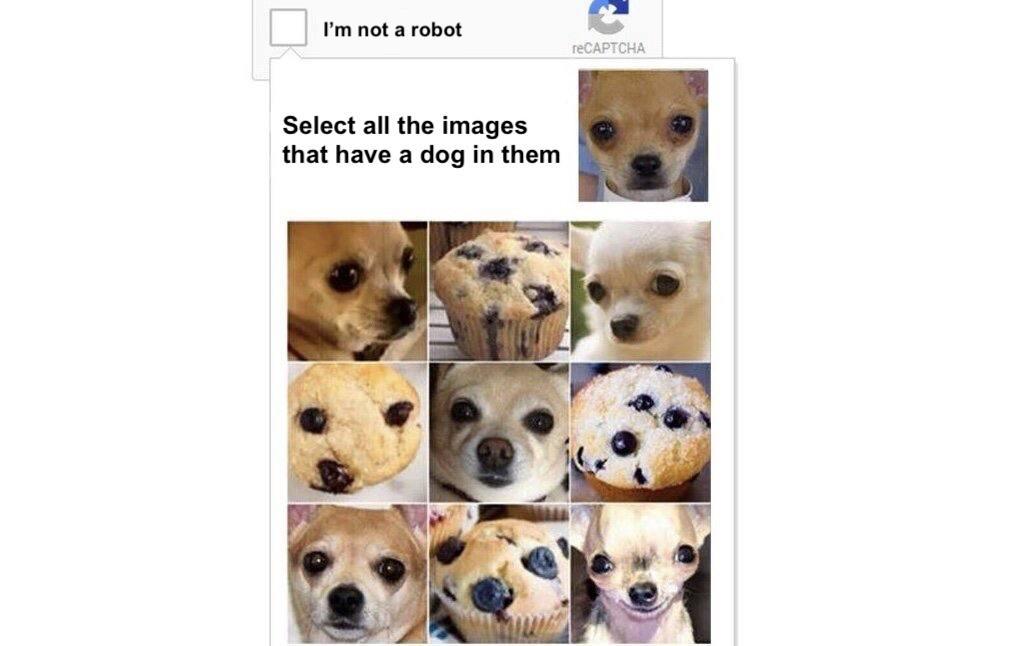
Picture 4. What a CAPTCHA that is positioned to be AI-proof looks like
Although perhaps in reality AI wouldn’t be able to bypass this kind of CAPTCHA 
2. Rate Limits
Rate limiting the number of requests from a single IP, ASN, or other fingerprints can curb automated attacks by slowing down login attempts. This is a relatively simple measure but may be insufficient on its own.
•Challenges:
Attackers use large botnets and compromised devices to rotate through many IP addresses, easily circumventing simple rate limits.
Regular tuning is essential: large marketing campaigns, new market entries, or spikes in legitimate traffic can trigger false positives and degrade user experience if rate limits are set too aggressively.
•Adjustments and Contextual Rules:
Consider dynamic rate limits that adapt based on user behavior patterns, geolocation, device type, or referral source. This approach reduces the risk of blocking genuine players while still hindering attackers.
3. Bot Management Solutions
Advanced bot management tools offered by providers like HUMAN, Cloudflare, Imperva, and Datadome use multiple attributes-HTTP headers, browser fingerprints, user interactions, behavioral analysis-to distinguish legitimate users from automated scripts.
•Pros:
High accuracy in detecting and filtering out malicious traffic.
Can significantly reduce the volume of credential stuffing attempts that reach the authentication endpoint.
•Drawbacks:
- Additional cost and complexity.
- False positives may occur, blocking real players, and require fine-tuning.
•Continuous Improvement:
Maintaining and updating these solutions regularly ensures that as attackers evolve their techniques, the bot management system remains effective.
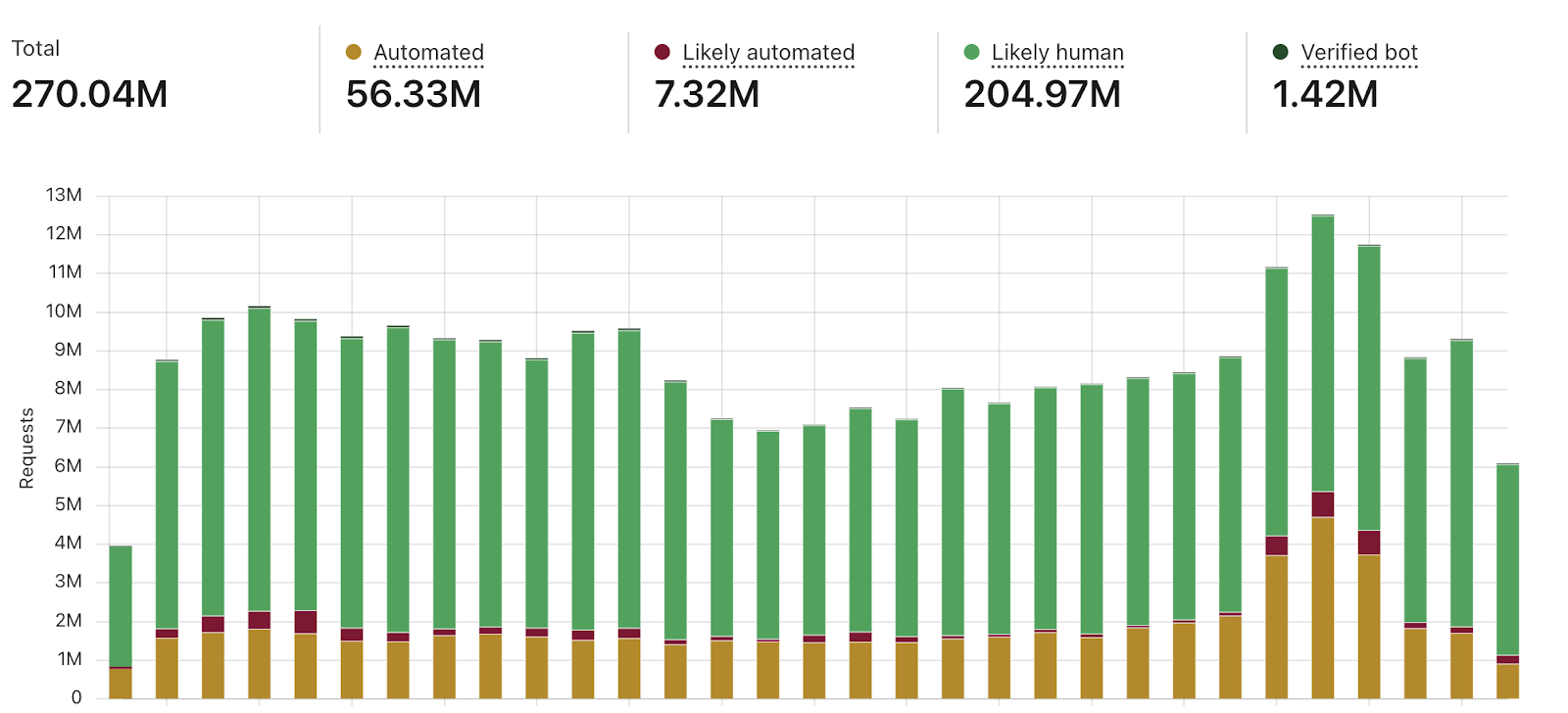
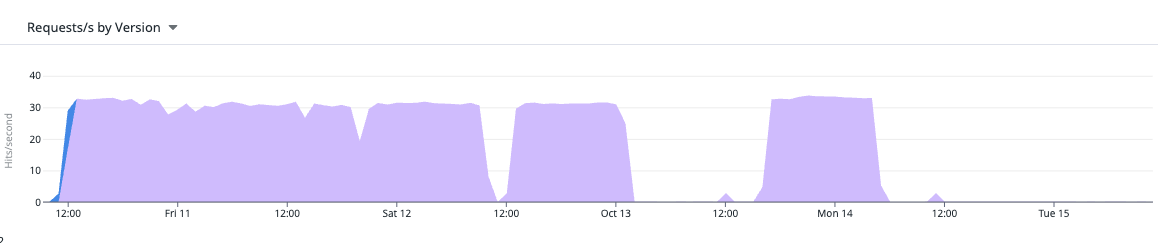
Picture 5. Total amount of traffic in the Bot Management solution interface
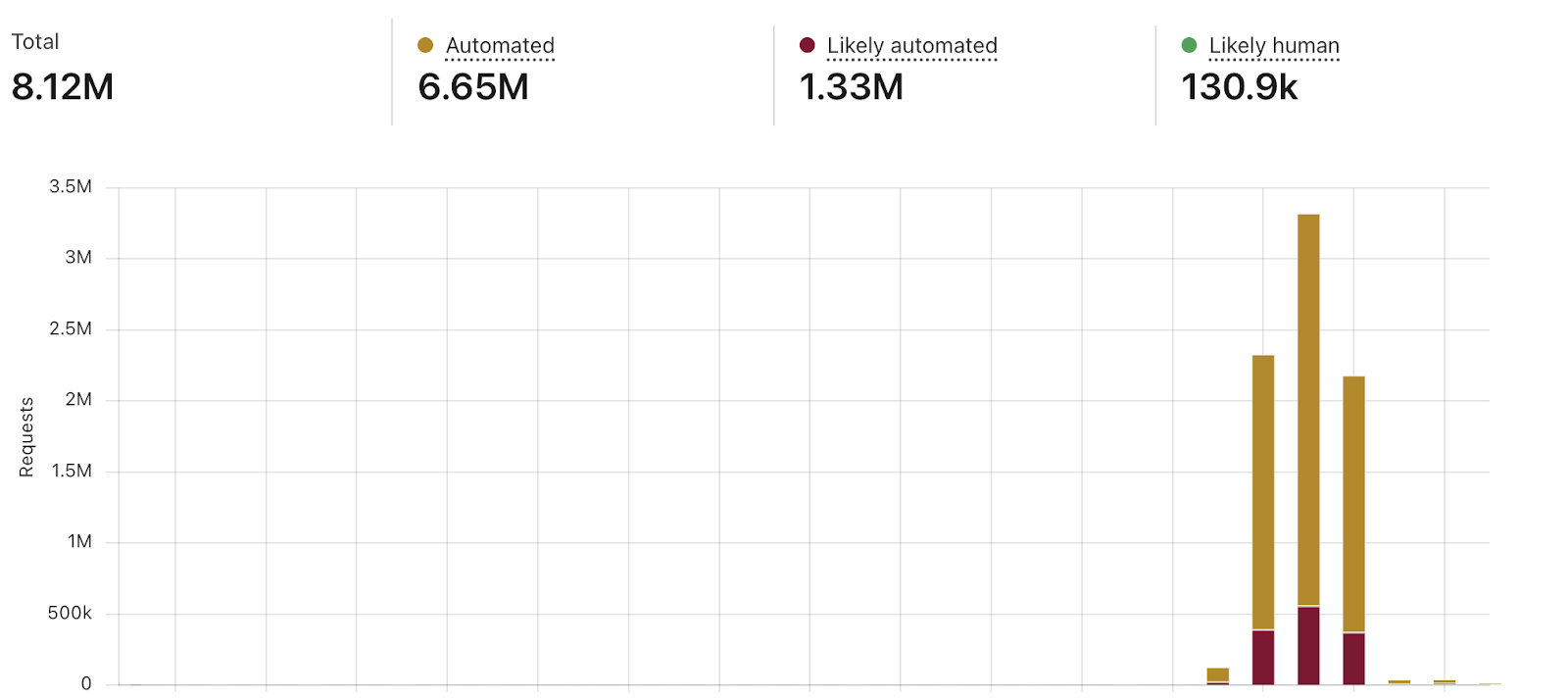
Picture 6. The volume of traffic to the authorization form in the Bot Management solution interface, where a huge rate of automatic connections during the attack
4. Multi-Factor Authentication (MFA)
Implementing MFA – such as one-time passwords delivered via email or authenticator apps – can drastically reduce the success rate of credential stuffing attacks. By requiring more than just a username and password, you significantly raise the barrier for attackers. Once they realize that additional factors are needed to gain access, the value of their stolen credentials diminishes.
Considerations:
- Usability vs. Security: Triggering MFA only after a correct username/password entry enhances the user experience, though it may reveal the account’s existence to potential attackers.
- Adaptive Scenarios: To minimize friction, consider prompting MFA only when a user logs in from a new device or an unfamiliar environment. Supporting modern authentication methods like passkeys can further streamline the process, offering an alternative to traditional OTPs.
In practice, balancing security and convenience may require different approaches for various user segments. For example, in our products, MFA is integrated by default. While it remains optional – albeit strongly recommended – for players, we make it mandatory for operator back-office accounts. This flexible model ensures that critical backend operations receive the highest level of protection, while players retain control over their login experience.
5. Monitoring and Mitigation
Effective monitoring and ongoing mitigation efforts are critical. Simple yet informative metrics can quickly alert operators to unusual login activity, enabling a prompt response before attackers achieve their goals.
•Key Metrics:
- Ratio of successful to failed logins.
- Spikes in failed logins from non-target geolocations.
- Sudden increases in failed logins from mobile devices or specific referral links (e.g., marketing campaigns).
•Contextual Understanding:
Marketing promotions or campaigns to re-engage inactive players can cause traffic surges and false alarms. Refining alert thresholds and analyzing patterns in traffic can help distinguish legitimate marketing-induced spikes from malicious automation.
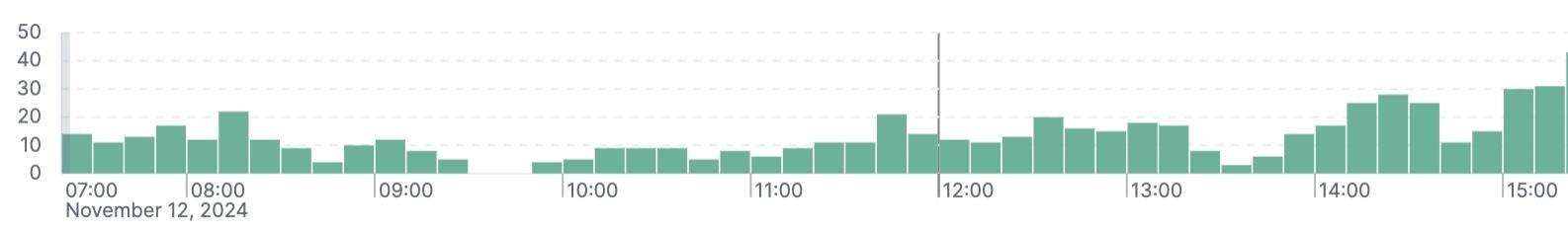
Picture 7. Number of successful logins
Picture 8. Number of unsuccessful logins
6. Infrastructure Load Management
By closely monitoring login attempts and user activity, operators can quickly detect abnormal authentication spikes indicative of a credential stuffing campaign. Early detection allows for timely measures – such as introducing CAPTCHAs or blocking suspicious IP ranges – before performance is seriously impacted. Continuous monitoring also prevents attackers from leveraging automated login attempts as a kind of “mini-DDoS,” straining authentication systems and degrading the overall player experience.
7. AI-Driven Detection and Prevention of Attacks
Based on our expertise, we believe that artificial intelligence (AI) is not only one of the most effective tools in combating credential stuffing and gaming fraud, but also the foundation upon which the future of protection against such threats will evolve. AI offers dynamic, adaptive defenses capable of addressing the constantly evolving tactics of attackers and the emerging challenges within the gaming industry.
How AI helps prevent attacks:
- Adaptive Learning: AI algorithms continuously evolve by training on new data. This enables them to recognize both known and emerging attack patterns, keeping pace with changes in attackers’ methods.
- Precision and Scalability: Automated analysis of vast data volumes allows AI to detect subtle connections and patterns that might go unnoticed during manual review. This scalability enables systems to process millions of requests without compromising performance.
- Behavioral and Pattern Analysis: AI leverages big data to identify connections between devices, accounts, and their activity history. For instance, if a device has previously been involved in fraudulent activities, it can be flagged as suspicious and its access restricted. This reduces the burden on security teams, minimizes the risk of compromise, and ensures seamless access for legitimate users.
- Reduction of False Positives: Instead of imposing broad restrictions that could inconvenience legitimate users, AI responds to specific behavioral signals. This minimizes disruptions for genuine players and protects key business metrics by preserving trust and loyalty.
Benefits for iGaming Platforms:
- Enhancing Player Trust: Targeted blocking of suspicious devices eliminates false positives, providing seamless access for legitimate users.
- Reducing Operational Risks: Proactive threat blocking reduces the need for manual analysis and response, allowing teams to focus on addressing more significat threats to the operational business.
- Preemptive Advantage: AI-driven systems not only react to attacks but also prevent them, ensuring stable and secure platform operations.
By integrating AI into security frameworks, iGaming platforms gain a powerful tool to safeguard against credential stuffing and gaming fraud. This intelligent and adaptive approach not only protects existing infrastructure but also actively prevents future threats, preserving player trust and maintaining key business performance metrics.
In practice, no single measure can fully prevent credential stuffing, but a layered, adaptive approach – combination of thoughtful rate limits, selective CAPTCHA usage, sophisticated bot management, and vigilant monitoring – significantly strengthens defenses. Over time, continuous analysis and refinement of these strategies help operators maintain platform security, protect player interests, and uphold the trust and integrity that form the backbone of the iGaming industry.
Basic Steps to Stop a Credential Stuffing Attack
1.Analyze the Attack and Identify the Pattern:
Look for specific indicators that define the attack’s characteristics. These can include automated user agents (e.g., “Go-http-client/1.1” or “python-requests/2.28.2”), identical or uncommon user agents, JS3-JS4 browser fingerprints, large pools of IP addresses generating a high volume of connections, abnormal HTTP headers, or insights derived from bot management analytics.
2.Implement Blocking Rules or Adjust Security Measures:
Once the pattern is identified, create rules or refine existing defenses – such as adjusting rate limits, enabling CAPTCHA or JS challenges, or tuning bot management settings – to block the malicious traffic effectively.
3.Monitor the Results:
Continuously observe the platform’s behavior, confirming whether the implemented countermeasures have successfully mitigated the attack and ensuring no unintended impact on legitimate users.
4.Assess Impact and Take Remedial Actions:
After stabilizing the environment, evaluate the overall damage caused by the attack. Identify compromised accounts and carefully consider whether it’s appropriate to inform affected players about the unauthorized access resulting from the credential stuffing incident. Additionally, review which additional protective measures might be implemented to enhance the platform’s resilience against future attacks.
Insights from SOFTSWISS Experience
Drawing on many years of involvement in the iGaming industry, we have identified key principles applicable to defending against credential stuffing attacks. The following concise insights combine brief headings with detailed context, guiding operators toward more efficient and data-driven protective strategies.
1.Simple Signals, Tangible Results
Detecting and blocking straightforward indicators – such as suspicious user agents, malicious IP addresses, or anomalous geolocations-can significantly impede attackers’ progress at minimal cost.
2.Balancing Effort and Expense
By increasing the complexity and cost of attacks (e.g., CAPTCHAs or adaptive rate limits), you make credential stuffing less profitable for adversaries, prompting them to seek less fortified targets. It’s important to proceed methodically, ensuring you don’t invest more in defense than the potential damage warrants. The goal is not perfect security at any cost, but an optimal balance between protection and core business metrics.
3.Trend Awareness and Data Leaks
Continuously monitoring reports of large-scale data leaks, such as Combolists – a database with millions of passwords from leaked data collected from thousands of Telegram feeds, and staying informed about emerging credential stuffing tactics allows you to strengthen defenses in a timely manner. When attackers gain access to millions of fresh credential pairs, they rapidly test them on iGaming platforms. Anticipating such events helps you raise the security bar before attacks intensify.
4.Process Over Panic
Well-defined principles and data-driven analysis help avoid hasty, radical measures like forcing all players to reset their passwords. Instead, a thorough evaluation of the situation, in-depth log analysis, temporary tagging of suspicious accounts, and implementing additional checks enable measured decisions. This approach maintains player trust, lowers operational risks, and ensures more effective, evidence-based threat mitigation.
5.Alignment with the Business
Knowing in advance about “explosive” marketing campaigns or expected traffic spikes enables you to adjust protective measures – perhaps relaxing certain filters temporarily-without harming conversion rates, first-time deposit (FTD) metrics, or overall player experience. In this way, security measures support, rather than hinder, business growth.
6.The Mini-DDoS Effect
Credential stuffing can overwhelm authentication systems, effectively mimicking a mini-DDoS. Timely scaling of resources, the introduction of CAPTCHAs, or other protective barriers help maintain platform stability and minimize delays or disruptions.
7.Considering Attack Timing
Attacks often begin during periods of reduced vigilance, such as Friday evenings or weekends. Thoughtful scheduling of on-call staff, enhanced monitoring, and readiness for rapid response during these intervals help operators promptly address incidents.
8.Botnets as a Tool for Credential Stuffing
An emerging tactic in credential stuffing attacks is the use of botnets – large networks of compromised devices that automate and scale login attempts. By distributing these attempts across numerous IP addresses and locations, botnets bypass traditional rate-limiting measures and overwhelm authentication systems. Their ability to mimic legitimate traffic complicates detection and mitigation, requiring advanced AI-driven solutions and behavioral analysis to effectively counteract their impact.
9.No Silver Bullets
No single technology guarantees 100% security. A layered, adaptive strategy – combining multiple measures, continuous fine-tuning, and ongoing analysis of attacker behavior – substantially reduces risk. While technical controls cannot eliminate threats entirely, they can make attacks considerably less profitable for cybercriminals.
By following these insights, iGaming operators can not only anticipate and contain credential stuffing attacks, but also do so rationally – avoiding excessive expenditures and safeguarding key performance indicators, all while maintaining player trust.
Conclusion
As the iGaming industry continues to expand, credential stuffing remains a persistent threat, driven by abundant leaked credentials and widespread password reuse. Operators who implement layered security measures – CAPTCHAs, adaptive rate limits, advanced bot management, and vigilant monitoring – can significantly reduce the success and profitability of such attacks.
The objective is not to achieve absolute security at the expense of player experience, but to establish an optimal balance. By making attacks more costly and less attractive, while preserving core business metrics, operators create conditions where adversaries are more likely to move on. Data-driven decision-making, ongoing trend analysis, and continuous refinement of defense strategies help maintain player trust, protect revenue, and ensure a stable, enjoyable environment for everyone involved.
Final Note
As cyber threats continue to evolve, SOFTSWISS remains at the forefront of cybersecurity in the iGaming industry. By continuously monitoring rapidly shifting attack trends and analyzing large-scale data, our team identifies emerging threat vectors and develops tailored protection strategies. We leverage cutting-edge technologies and proprietary innovations to safeguard our clients not only from credential stuffing attacks but also from other modern threats.
However, our mission goes beyond merely protecting platforms. SOFTSWISS is dedicated to advancing the iGaming industry as a whole by raising awareness among all stakeholders about emerging threats, sharing practical recommendations, and highlighting the most effective defense measures. By openly sharing our unique experience and fostering a collaborative approach to cybersecurity, we aim to ensure the long-term growth and integrity of the global iGaming ecosystem.
Cybersecurity is not a static solution but a continuously evolving process. At SOFTSWISS, we take pride in contributing to this journey by equipping operators, players, and the broader iGaming community with the tools, knowledge, and resilience necessary to thrive in a rapidly changing digital world.
The post From Dark Web to Jackpot: How Cybercriminals Exploit Stolen Credentials in iGaming appeared first on Cybersecurity Insiders.
