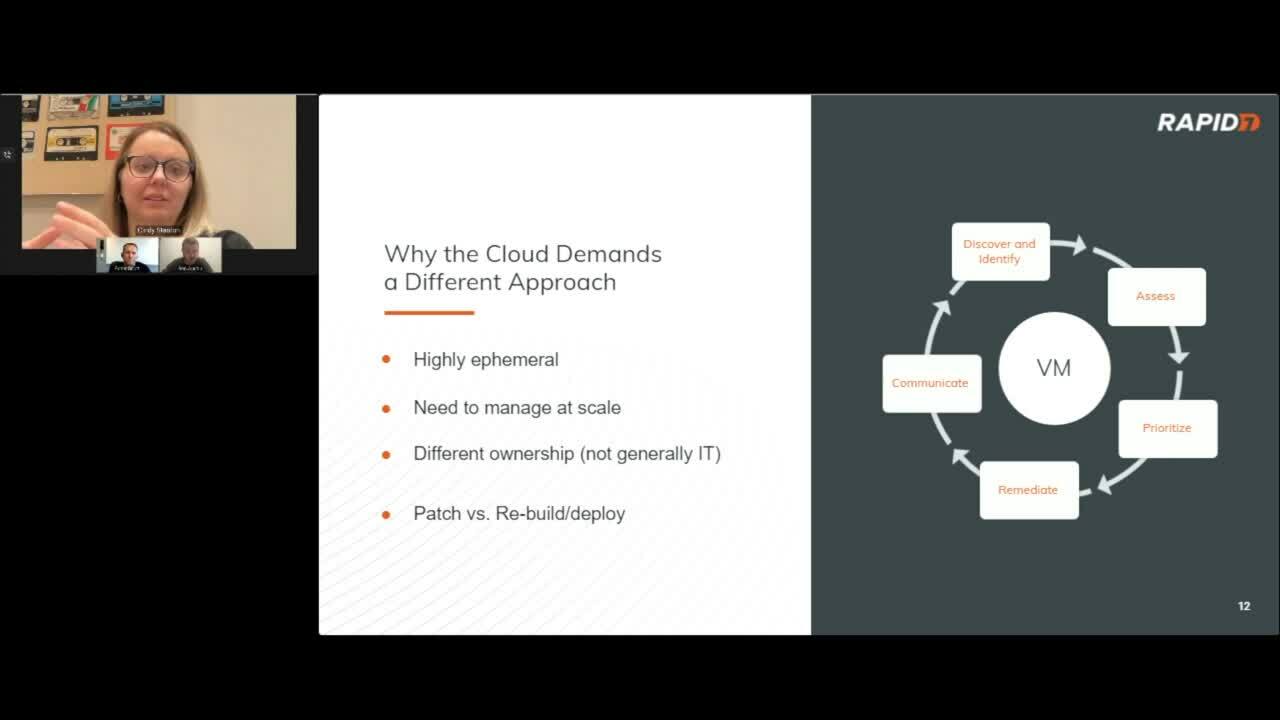
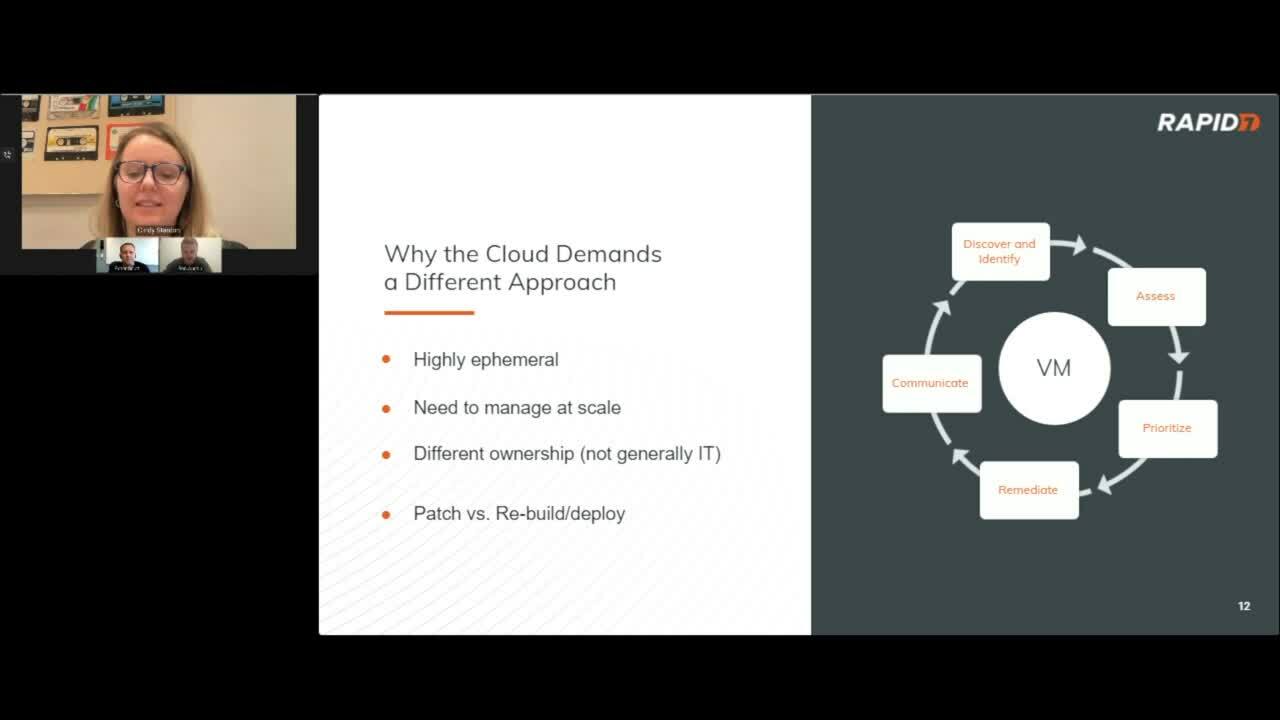
The cloud has become the backbone of modern innovation, powering everything from AI to remote work. But as organizations embrace the cloud, they also face an ever-expanding and increasingly complex attack surface. With purpose-built harvesting technology providing real-time visibility into everything running across multi-cloud environments, Exposure Command from Rapid7 ensures teams have an up-to-date inventory, mapping their cloud attack surface and enriching asset data with risk and business context.
To ensure teams can keep up with the torrid pace of innovation and overcome increased complexity, Rapid7 remains dedicated to investing in advancing the cloud security capabilities available within Exposure Command. To that end, we’ve made a few significant updates across AI resource coverage, third-party CNAPP enrichment and more. Let’s dive right in.
Extending coverage for securing AI/ML development in the cloud
AI and machine learning (ML) are transforming industries, but the speed of adoption can often leave organizations vulnerable. AI/ML workloads often process sensitive or proprietary data, requiring robust protections to ensure compliance with ever-evolving regulations. Safeguarding these environments isn’t just about securing the infrastructure; it’s about understanding the unique workflows and ensuring compliance at every step.
These workloads also introduce unique risks, such as model poisoning attacks or vulnerabilities in APIs, creating new vectors for data exfiltration and service disruption. Additionally, the dynamic nature of cloud-hosted AI services presents challenges in maintaining secure configurations as resources scale elastically, potentially exposing sensitive endpoints or misconfigured setups.
To that end, Exposure Command has expanded support for critical AI services like Amazon Comprehend and Polly, AWS’s natural language processing and text-to-speech services.This provides comprehensive visibility across an organization’s attack surface, aligning AI-specific risks with broader enterprise priorities.
Shifting left and securing the software supply chain
Developers are at the forefront of modern cloud environments, making “shift-left” strategies essential for effective security. By addressing risks during development rather than after deployment, teams can eliminate vulnerabilities before they become costly issues.
Exposure Command now offers more robust Infrastructure-as-Code (IaC) scanning and deeper CI/CD integration, with Terraform and CloudFormation support across hundreds of resource types. For development teams, integrations like GitLab, GitHub Actions, AWS CloudFormation, and Azure DevOps bring security checks directly into their workflows. Whether it’s identifying misconfigurations in AWS Glue Catalogs or assessing risks in SES configurations, these tools help teams secure their code without breaking their stride.
Bridging the hybrid cloud gap with native and third-party CNAPP connectors
For many organizations, the challenge isn’t just securing the cloud – it’s securing everything holistically. Hybrid environments that span on-prem systems and multiple cloud providers can create silos, leading to gaps in visibility and risk management. To tackle this, we’ve integrated InsightCloudSec data directly into Surface Command, empowering security teams with a unified view of their entire attack surface in one place.
But we didn’t stop at consolidating our own native CNAPP capabilities. Teams now get out-of-the-box integrations with popular cloud security tools like Wiz and Orca as well as CSP-native services like AWS Inspector, all making it easier than ever to identify risks across cloud-native and hybrid environments. Everything can now be seen in one place – from endpoint vulnerabilities to cloud misconfigurations and overly permissive roles – allowing for faster action with clarity and precision.
Tackling virtual desktop risks with custom registry keys
With the rise of remote work, virtual desktop infrastructures (VDIs) like AWS Workspaces have become essential. Yet, their dynamic nature makes tracking vulnerabilities a challenge. Exposure Command addresses this with features like custom registry keys for golden images, ensuring you can trace a risk back to its source and effectively prioritize remediation.
Commanding the cloud attack surface
The challenges of securing modern environments aren’t going away. Attack surfaces will continue to expand, threats will grow more sophisticated, and organizations will face increasing pressure to innovate securely.
Keep an eye out for more updates coming soon as we continue to invest in helping organizations effectively manage exposures from endpoint to cloud.