Introducing... Threader3000
by Matt Johnson
Offensive security as the red team, Defensive security as the blue team, or even a network administrator, you will undoubtably know the network mapper, or Nmap for short. I’m sure most know this tool but for the few that may not, Nmap is an open-source tool used by all sorts of professionals in the information technology field for network discovery and security auditing. You can perform a variety of tasks when using the right arguments found here: https://nmap.org/book/man-briefoptions.html
Visiting that page, you are presented with a list of possibilities and uncertainties for some. What helped me the most when I was just starting out as an ethical hacking enthusiast? A tool that I think deserves some bit of spotlight.
Threader3000
This is a tool is a project by TCM Security’s red team lead, Joe Helle “The Mayor”. Joe even said that this tool helped him pass the OSCP exam because that exam is all about time management and enumeration.
Here is how it helped me. When I would work on TryHackMe and Hack the box I would often stumble trying to get the scan to work properly with all the right switches. I would forget to add -Pn, or I would make sure to scan all the ports using -p- and just get up and walk away for a good 10 minutes and come back hoping the scan completed. Can’t forget -sV and -sC, and -T4 for speed. You have a lot of options, and it might take you some time to remember and come up with your own go to Nmap scan. Using Threader3000 saved me time and helped me remember the more common switches till I started coming up with my own depending on the situation. I have not tested this on a live target as of the time of writing this, but I think it would still be effective for some cases as this is more for single target. I’m still in training myself after all.
Threader3000 is just python script that allows multi-threaded port scanning. Very simple to install you have a few options, you can install with pip3
pip3 install threader3000
or you can also install with git
git clone https://github.com/dievus/threader3000.git
Choose your method and type that into your terminal and it will install very fast. Once installed on your Kali box you just type threader3000 and you will be prompted to input an IP address or a full qualified domain name.

Type in the IP address you have permission to scan, or the fully qualified domain name and let it go to work. The scans will typically only take a few seconds and you will be presented with a recommendation of what Nmap scan to perform on your target.
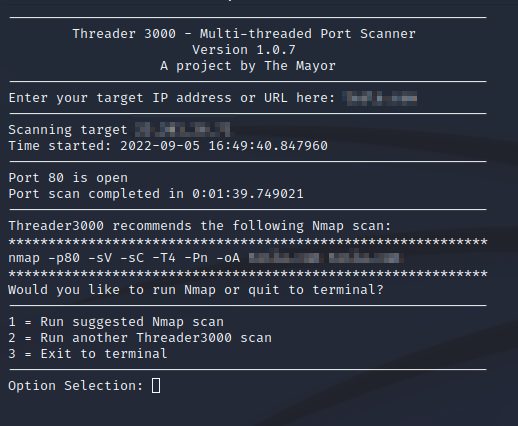
Select the option you want, and you’re done. Please remember to only scan targets to that you have permission from the respective owner.
Now let’s try it on something with that should be a little more vulnerable.
Just as before we start off with typing threader3000 and type in the IP address you want to scan, and it will begin. This scan pictured below only took about 15 seconds.

Now I want to run the suggested Nmap scan so I will select option 1.
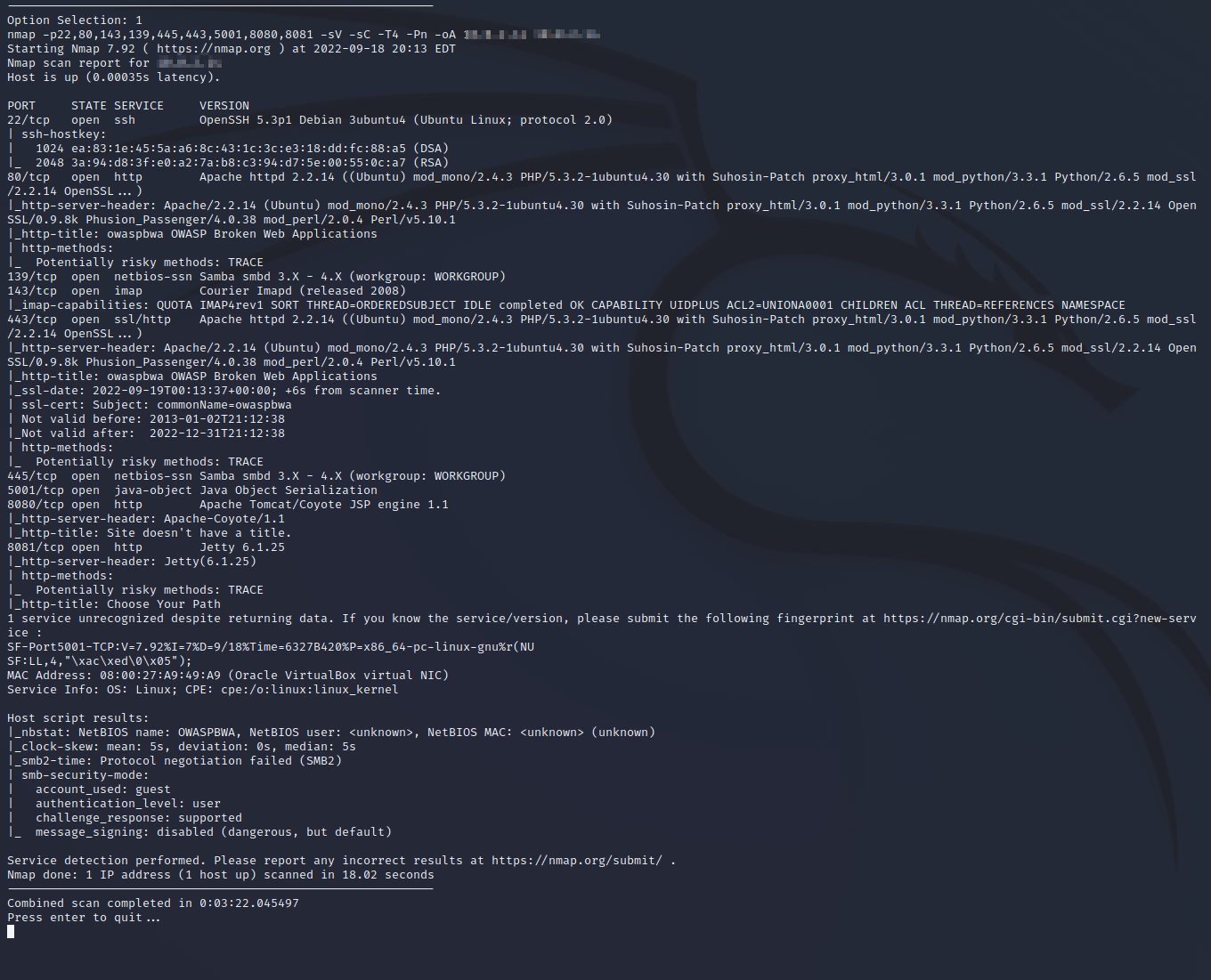
As you may have guessed I ran this scan on the OWASP Broken Web Application from the results of the nmap scan. Now don’t get me wrong this tool is not going to win anyone awards and I don’t think I lot experienced people will use threader3000 but it does save time and that matters in my opinion. Saving time during the enumeration can help out greatly. Might even help you when you go for your OSCP. Best of luck out there my fellow enthusiasts, and cybersecurity professionals.
Links used in the making of this article.
Check out Threader3000 at https://github.com/dievus/threader3000
Check out Nmap at https://nmap.org/
 John Iwuozor
John Iwuozor