Source
Cyber attackers, fraudsters, and hackers target both small-scale, midsized, and large online ecom enterprises.
In fact, the frequency of small businesses fraud is at 28% compared to larger organizations at 22-26%.
This portrays a grim picture for ecommerce businesses — filled with data breaches and irate customers. Again, if you don’t secure your clients’ data, you can end up losing their trust, income, and maybe have your brand tarnished.
Whenever it concerns protecting your company against frauds, though, there’s no shortage of activities to watch out for.
However, the multitude of cyber threats, along with a massive cost to address cyber-crimes, would be enough to scare you from quitting.
To avoid being attacked, ensure that your workers are well-informed and trained on the most frequent kinds of attacks that could harm your company’s reputation.
With this insight, your staff can take additional actions to guarantee that your clients’ personal information is protected to the best of their ability.
5 powerful approaches to protect your ecom business from online fraud
According to research, frauds and cyber attacks are among the top three threats weighing on the US business environment – with a weightage of 65%.
As per our research, here are five tried-and-tested techniques to protect your ecommerce digital business from dangerous online frauds.
-
Share your online store’s policies and run a test payment
To guarantee that both your business and your buyers will be in agreement right from the beginning, clearly publish your shipping terms, return guidelines, and service terms and conditions on your site before you begin accepting conversions and sales.
By answering these questions, a return guideline can help manage client expectations:
-
What is the time limit for a customer to return items?
-
The process for returning or exchanging items. How do clients get in touch with your team and how much time does it take?
-
Who is responsible for returning stuff to you?
-
Are any things, like discounted items or products which have been damaged or used, not returnable?
-
Is it possible to get a complete refund, an alternative, or a shop credit?
Again, make a trial payment to see what data you have access to. Prior to shipping out items, you should evaluate your user’s details to ensure that the transaction is genuine.
Understanding where to look for refused eCommerce payments and client data ahead of time will help you speed up the review procedure.
-
Create strong passwords
Although it is your firm’s obligation to keep user data secure at the back-end, there are several ways you can use to assist customers by mandating a minimal level of special characters, as well as the usage signs or numerals.
The usage of complex passwords on a terminal network security can impede or even defeat different attack tactics. Short and easy passwords, for instance, are fairly effortless for hackers to ascertain, which might lead to your business becoming a target of fraud.
Such attacks typically entail business, manufacturing, ecologic, or economic disciplines that drop beyond the standard bounds of a fraud. The following are some of the most popular techniques fraudsters use to find a victim’s passcodes:
-
Guessing – When an intruder attempts to log into a customer’s profile by predicting probable words or phrases frequently.
-
Online attacks — Automatic programs that try to log into the system over and over again, utilizing different terms from the word documents each time.
Internet scammers are cunning criminals. They take full advantage of folks who might not be aware of how to safeguard themselves using their tremendous computer skills. As already explained, user passwords are one of their preferred sources of data.
Fraudsters have equipment that can break a 6-digit passcode in seconds. Try using an 8-character or longer alphanumeric passcode with a minimum one uppercase character plus a special character to ensure that your password is as secure as possible.
-
Use fraud prevention software
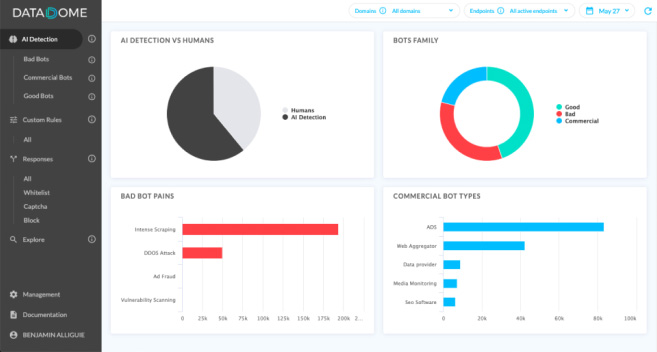
Source
Bot traffic to mobile applications account for a huge chunk of all bot traffic worldwide. Bots and fraudsters will locate the weak points in your architecture.
Hence, protecting your firm from internet scams as well as bot attacks necessitates a coherent layer of safety across all of your end nodes — your mobile app, internet site, and APIs all need to be protected at the very same level.
eCommerce fraud prevention tools process information from clients and servers in real time. Each request into your mobile applications, webpages, and APIs is evaluated and forced to submit to a mix of AI and ML software to decide if access should really be allowed or not.
Scraping, identity fraud, vulnerability analysis, Layer 7 DDoS (Distributed Denial of Service), and other methods are used by fraud prevention software as well.
They provide unrivaled visibility into all of these risks, with dedicated KPIs, the capacity to evaluate live traffic statistics, as well as real-time attack findings and alerts for all interested parties.
The false positive percentage for full-fledged fraud protection software is extremely low. This proportion is visible on the dashboards for each end – point: mobile apps, sites, and APIs, and it’s analyzed in real time.
By nature, each endpoint’s responding approach and blocking plus challenging methods are customized. Your company is safe, and your genuine customers have a great time.
-
Incorporate strong verification protocols
Although digital purchases do not necessitate a sign for verification, a good way to ensure that the transaction is genuine is to verify that the customer’s shipping and billing addresses are identical.
In the case of a conflict, the card provider might also want to verify that the payment was finished by the appropriate account holder on your online platform. They may request evidence that the purchased product was delivered to the right billing address.
If you get an order with incorrect addresses, contact the client to find out why. It could be a practical cause, including a present being sent.
Anything out of the ordinary, like a gifting order with multiple sets of the same product or a massive commercial order getting transported to a household, should be questioned.
Consumers who request that a purchase be rushed should be approached with caution; it could imply that they are in a rush to wrap up the purchase prior to the stolen card details being reported.
You can choose how much risk you’re prepared to take. Some suppliers refuse foreign deliveries or odd orders, whereas others look at each transaction individually.
Keep in mind that you’re fully responsible for all online payments made via your accounts, so double-checking orders ahead of time might save you money in the long run.
Verify that there are no software injection, encryption, and authentication attacks.
-
Injection frauds
Injection frauds can result in loss of data, corruption of data, suspension of service, and even total host invasion. Injection issues are relatively straightforward for fraudsters to identify and occur often.
First, unverified data is entered into a web app and then it tricks that software into accepting commands. In this manner, the attacker gains access to your personal data. you ca address this issue by embedding an API software.
Also, regularly update your web applications since outdated software are specifically prone to injection threats.
-
Encryption treats
To safeguard personal details from phishing scams, all information that passes between a firm’s web server and a site for consumers should always be encrypted. For e-com sites, Secure Sockets Layer (SSL) verification is a must-have.
SSL encrypts personal data like credit card numbers and credentials and safeguards it while it moves across the internet. The SSL certificate protects the information from cyber-attacks and thieves by making it inaccessible to everyone except the intended receiver.
-
Authentication frauds
Authentication frauds are common, and they can give hackers a legitimate user on whom to launch an attack.
To mimic users, fraudsters make use of unprotected user profiles, weak passcodes, or verification weaknesses. The password policy, logout, privacy, and account upgrade functions, among other things, all have issues.
To keep your sensitive data safe from hackers, you’ll need a solid combination of verification and administrative abilities. Furthermore, several services monitor your logs for unsuccessful login attempts and will restrict Ips with a high number of failed tries.
-
Monitor paper trails and card declines
Keeping solid records is always a good idea in organizations, but it’s more important when products and/or services are traded on the internet.
If a consumer files a complaint, your only option is to show documentation that the purchase was completed.
Prepare all supporting documentation for a questioned purchase so that you are able to fight the allegation with the recipient’s bank on their behalf.
Keep records of your shipment and delivery data. Use built-in ecom tools to preserve shipping and fulfillment information for quick retrieval. Big orders should need a sign upon delivery.
Keep any emails between your business and your buyer for 24 months and itemize your invoices to demonstrate conclusively what was bought.
Again, purchases that appear out of place, either spatially or thematically, versus other card activities are declined through credit card providers.
You can look into your personal denied payment history to see whether there’s an issue.
When you obtain a new purchase request — especially if it’s a sizable payment — go to your sales history and check the status. Search for payments that have been denied for the same sum in a brief span of time.
Multiple declines could indicate that your credit card details have been hacked and are being utilized in a fraud. If you receive repeated rejections on separate cards, you should wait to mail the item until you can contact the buyer and confirm their identification.
Conclusion
Finally, make sure that you and whoever else is managing your website is following it up plus that you have a disaster strategy in place if things do not go as planned.
To ensure that your website is correctly managed, perform regular backups or verify that your web host does so.
The post 5 Ways to Protect Your Ecommerce Business appeared first on Cybersecurity Insiders.