All businesses, both large and small, store data on servers or in the cloud. This includes business data and customer data. Since 2008, over one billion types of malware have been recognized. So, companies need robust data security in all areas, from Agile manifesto planning to email marketing.
Data security protects against unauthorized access, human error, corruption, and theft by cybercriminals. But with so many data security options to choose from, finding the right one can be challenging. In this article, we’ll compare two popular methods of safeguarding data: tokenization and encryption.
What is encryption and how does it work?
Encryption uses mathematical calculations to render data unreadable without the proper key. It is the most common method of protecting data, with 50% of companies applying encryption throughout the enterprise. 54% of businesses use encryption to protect customer data, such as:
- Cardholder and payment information.
- Personal data, including personally identifiable information.
- Account numbers and other financial data.
Most software that handles sensitive data uses encryption. For example, electronic signature software free on the internet. As long as you use a strong algorithm, encryption is almost impossible to break without the key.
Types of encryption
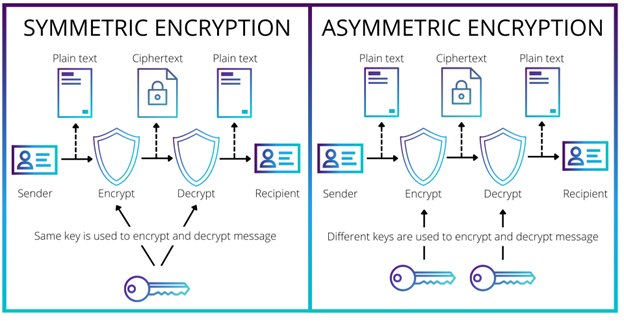
Symmetric encryption
Symmetrically encrypted data has a single key for encryption and decryption. It’s like a house key that locks and unlocks the door. The downside of symmetric encryption is that if the key gets in the wrong hands, it can unlock all the data.
Asymmetric encryption
Asymmetric encryption uses two mathematically related keys. Usually, these are two factors of a large number. One key (public) locks the data, and the other key (private) unlocks it. This makes asymmetric encryption much more secure than symmetric encryption.
Let’s say a cybercriminal intercepts the public key. Without the corresponding private key, they would have to factor large numbers to break the encryption. This is impossible in a realistic timeframe, even with a modern computer. Because of this, asymmetric encryption is commonly used in exchanges that take place over a public network, such as:
- Key exchanges
- Web security
- Email security
Advantages of encryption
- It’s easy to scale: 59% of businesses say scalability is one of the most important features of encryption technology. Because encryption uses keys, it’s easy to scale large volumes of data. In contrast, tokenization is harder to scale securely while maintaining performance.
- It works for structured and unstructured data: You can use encryption for structured and unstructured data. But tokenization only works for structured data like credit card numbers.
- It’s easy to exchange sensitive data: Most cloud providers encrypt data automatically, including by Instance Type. It’s easy to exchange this information with people who have the encryption key.
Disadvantages of encryption
The main aim of encryption is to stop hackers and other outside parties from gaining access to important business data. But it does have disadvantages, such as:
- Encryption can be broken
- Encrypted data requires extra security to comply with regulations
Encryption can be broken
Because encryption works by obscuring the original data, it is difficult, but not impossible, to break. And if a hacker did manage to steal the decryption key, they could immediately unlock the data.
To combat this, many businesses are using hardware security modules (HSMs). 41% of organizations use HSMs on-premises, and 39% use cloud-based HSMs. HSMs are external modules that plug into a computer or server. They perform cryptographic functions such as managing keys and encrypting and decrypting data. As such, they can protect transactions, apps, and identities.
Encrypted data requires additional security to comply with regulations
45% of businesses install encryption to comply with privacy or data security regulations. But governing entities, like the PCI Security Standards Council, class encrypted data as sensitive. This is because encryption is reversible, even without the key. So companies need extra security measures to meet regulations.
The problem? Companies have to spend money on extra security to protect encrypted data. This could be why 43% of organizations say deploying encryption technology is a significant challenge. Even tasks like how to set up voicemail could be cumbersome if companies have to encrypt and protect customer voicemails. Plus, if companies fail to follow regulations or have a data breach, they face hefty fines.
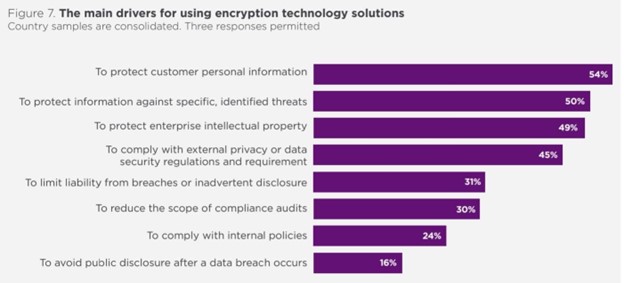
Image Source
What is tokenization and how does it work?
Tokenization replaces each individual character with a random character. These random characters are tokens, and a token engine performs tokenization. Unlike encryption, you cannot break tokenized messages. This makes tokenization ideal for protecting structured data like:
- Credit card and account numbers.
- Email addresses and phone numbers.
- Social security numbers.
Because tokens are so secure, many customers are using them for online payments instead of credit cards. For instance, 78% of Americans are willing to use tokens with companies they already buy from. But tokens aren’t only useful for ecommerce. You can now buy domain name tokens like domain checker NZ addresses or tokens for online gaming. So, tokenization is likely to become more widespread in the future.
Types of tokenization
Vaulted tokenization
Vaulted tokenization maps tokens to the corresponding untokenized data. The untokenized data is stored in a secure database, called a vault. The vault can be in-house or offsite at a tokenization firm.
The problem with vaulted tokenization is two-fold. First, the process of authenticating tokens takes time as the system must compare the tokens to the plain text in the vault. Second, vaults are a high-risk target for cyberattacks.
Vaultless tokenization
Instead of using a mapping database, vaultless tokenization uses an algorithm to tokenize the data. The use of algorithms eliminates the need to store the plain text. This makes vaultless tokenization cheaper, more efficient, and more secure than vaulted tokenization.
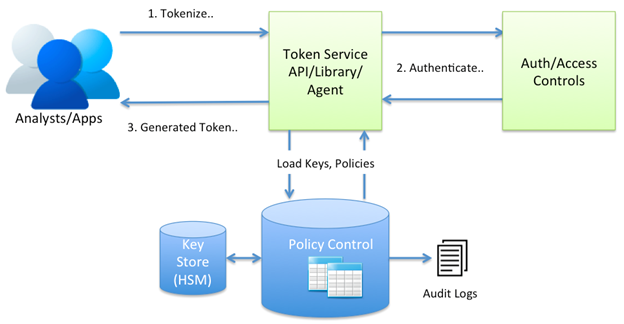
Image Source
Tokenization-as-a-Service (TaaS)
The latest tokenization developments combine vaultless tokenization with cloud computing to provide tokenization-as-a-service. In TaaS, the tokenization engine is usually part of an Enterprise Cloud Service. What is Enterprise Cloud Services? ECS is a cloud-based unified analytics platform that provides security and automation at scale.
With TaaS, neither the tokenization engine nor the business needs to store plain text. Also, like other forms of tokenization, TaaS preserves the format of the data. This makes the data easier to process and analyze.
Advantages of tokenization
The tokenization market is predicted to grow globally from $2.3 billion in 2021 to $5.6 billion in 2026. Why? Tokenization has many advantages over encryption, including:
- Tokenized data is much more secure.
- Tokenized data can be processed without revealing sensitive information.
- Tokenized data comply with regulations without extra security.
Tokenized data are much more secure
Tokenization is more secure than encryption since tokens don’t contain the original information. Even if a hacker managed to steal your tokens, they can’t detokenize them to reveal your sensitive data. Tokens are placeholders; the original data is stored off-site in a secure token vault.
This makes tokenization ideal for ecommerce companies, global gaming solutions, and other businesses that store sensitive customer data.
Tokenized data can be processed without revealing sensitive information
A major advantage of tokenization is it preserves the format of the original data without revealing the information. Most encrypted data is a different size or format from the original. This means you can’t analyze or process it without first decrypting it.
In contrast, you can process tokenized records. This allows companies to store customer data like credit card information for future use. Also, since tokens are individual characters, you can leave certain characters untokenized. For instance, the last four digits of your credit card number. This allows customers to confirm their card without exposing it to criminals.
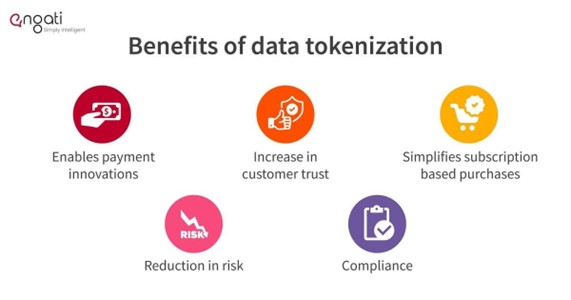
Image Source
Tokenized data comply with regulations without extra security
Since tokens don’t contain the original data, they aren’t classed as sensitive. In other words, tokenization meets PCI and other data security regulations automatically. This means businesses don’t need to buy extra security. Also, if you only store the tokenized data on your servers, you won’t have to worry about data breaches.
What effect will quantum computing have?
Once quantum computers are readily available, they will revolutionize how companies protect data. It would take current computers thousands of years to break the strongest encryption. Whereas quantum computers could break it in a matter of minutes. So, in the future, encrypted data could be vulnerable.
The solution? Businesses should include quantum-proofing in their long-term business plan. Tokenization is quantum-proof by nature, and quantum-proof encryption is already available. If you start preparing now, you will be ready when regulators finalize quantum-safe cryptography standards in the future.
The future: tokenization and encryption
Businesses could make cloud-based tokenization part of their legacy modernization. After all, tokenization is ideal for securing structured data and complying with regulations. But it’s unlikely tokenization will ever completely replace encryption. For instance, organizations may use encryption to protect important archives that are rarely used.
To combat the threat from quantum computing, businesses could combine tokenization and encryption. For instance, you could tokenize parts of a message before encrypting it. This would render the data meaningless while keeping your existing cartographic infrastructure.
Bio:
Pohan Lin – Senior Web Marketing and Localizations Manager #1:
Pohan Lin is the Senior Web Marketing and Localizations Manager at Databricks, a global Data cybersecurity analytics platform and AI provider connecting the features of data warehouses and data lakes to create lakehouse architecture. With over 18 years of experience in web marketing, online SaaS business, and ecommerce growth. Pohan is passionate about innovation and is dedicated to communicating the significant impact data has in marketing. Pohan Lin also published articles for domains such as SME-News.
The post Comparing The Key Differences Between Tokenization vs Encryption appeared first on Cybersecurity Insiders.
 self-encrypting drives with pre-boot authentication by introducing PBA to its Citadel C Series lineup. The new drives, powered by Cigent®, add the critical PBA function to their existing DIGISTOR C Series of self-encrypting drives.
self-encrypting drives with pre-boot authentication by introducing PBA to its Citadel C Series lineup. The new drives, powered by Cigent®, add the critical PBA function to their existing DIGISTOR C Series of self-encrypting drives. and its CSfC-listed PBA (EE), which have been adopted widely with military and government agencies. The Citadel family rounds out the DIGISTOR secure SSD product line that includes FIPS-certified and TCG Opal-compliant SSDs, all of which are TAA-compliant, and are suitable for a wide range of security solutions.
and its CSfC-listed PBA (EE), which have been adopted widely with military and government agencies. The Citadel family rounds out the DIGISTOR secure SSD product line that includes FIPS-certified and TCG Opal-compliant SSDs, all of which are TAA-compliant, and are suitable for a wide range of security solutions.


