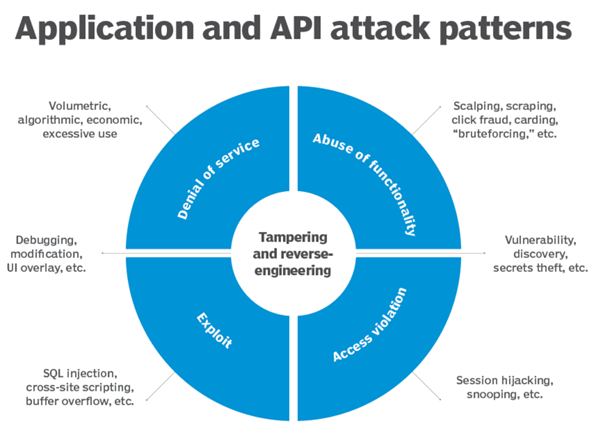
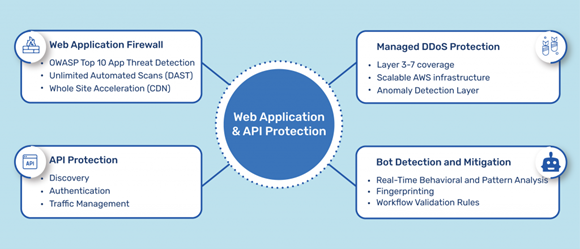
[ This article was originally published here by Indusface.com ]
Data from a recent report revealed that bots take up two-thirds of internet traffic. However, not all bots are safe and well-intentioned. Research further suggests that of all the web traffic, nearly 40% is bad bot traffic, and around 25% is good bot traffic. Given how destructive bad bots are, it is essential to use a bot protection solution to detect bad bots, manage bot traffic, and mitigate bot threats. Read on to know more about bot protection solutions and how they help organizations.
The Bot Problem: Why is it Necessary to Mitigate Bot Threats?
Bad bots harm your business in several ways, some of which are detailed below.
1. Leveraged in a Range of Attacks
From phishing, spamming, ad frauds, data harvesting to DDoS attacks, account takeovers, and brute force attacks, bad bots are leveraged by attackers to orchestrate a wide range of attacks. These attacks could cause downtimes, make the website/ application unavailable to legitimate human traffic, enable illegitimate access to critical assets, and/or lead to the loss of sensitive information, among others. Further, bad bots are also used by attackers to illicitly snoop and scan websites for vulnerabilities to exploit.
2. Content Scraping That Negatively Impacts SEO
Scraper bots are often deployed by attackers and even competitors to extract copyrighted/ trademarked/ proprietary content from a website and duplicate it elsewhere. This is often done by competitors or adversaries looking to negatively impact your SEO rankings as duplicated content diminishes your site’s authority over that content. Content scraping is also used by attackers to orchestrate phishing attacks and scams. They create fake websites by duplicating scraped content to trick visitors and do their bidding.
3. Price Scraping
Competitors looking to undercut prices typically deploy scraper bots to scrape prices from e-commerce and other websites. Competitors, thus, gain an edge in the marketplace and win the SEO war on price. You will find lower conversions, SEO ranking drops, and unexplained downtimes caused by aggressive scrapers.
4. Skewed Analytics That Lead to Poor Marketing Decisions
By leveraging botnets, attackers could orchestrate DDoS attacks to make your website unavailable to legitimate traffic while affecting your traffic metrics. Bad bots are also leveraged to create and abandon shopping carts on e-commerce sites, thereby, creating non-existent leads. Similarly, bad bots are leveraged by attackers/ competitors to commit click fraud, creating non-existent shoppers and driving up advertising costs. Such skewed metrics often lead to poor marketing decisions and a reduction in ROI from advertising and marketing.
5. Loss of Customer Trust and Confidence
Bad bots are used by attackers to spam the comments sections with malicious code/ provocative comments/ scathing reviews, inflate views, write false or biased content by creating fake social media accounts, write fake user reviews, and so on. Such activities lead to the loss of customer trust and confidence in your brand and drive customers away from your website.
Overall, bad bots cause revenue losses to organizations by negatively impacting the bottom line. Further, the attacks caused by bad bots bring massive financial losses, legal bills, penalties, and reputational damage. By mitigating bot threats, you save yourself millions of dollars.
Bot Protection Solution: Why it is Vital to Mitigate and Manage Bot Threats?
Bot protection solutions or bot management solutions enable organizations to effectively identify and manage bot traffic while mitigating threats. All this without affecting your legitimate and business-critical traffic.
1. Keep Your Website Protected
Bot protection solutions offer round-the-clock protection against bad bots. They are automated and capable of identifying and blocking malicious/bad bots in real time. They can automatically detect bad bots and block them. This enables organizations to keep their bot risk to a minimum and proactively protect their website from a range of known and emerging threats.
2. Make Your Website Always Available to Business-Critical Traffic
The best bot management solutions like AppTrana are equipped with global threat intelligence and insights on past attacks, and they have self-learning abilities as well. This gives them the ability to intelligently decide the action to be taken based on the context. Such a solution will be able to decide whether to allow, block, challenge or flag a particular request/ user. This way, unwanted traffic is kept at bay without affecting business-critical traffic.
3. Optimize Business Intelligence and Analytics
By identifying and mitigating bot threats, the bot protection solutions help to ensure that business analytics and intelligence are not skewed. So, you will get the right picture of your visitors and the state of your marketing and advertising campaigns. You can, thus, focus your time and resources on real customers and on engaging & converting real leads.
4. Accelerate Site Performance
Bad bots consume excessive bandwidth and create excessive load on servers. This impacts your website’s performance. By mitigating bad bots, you can accelerate your site’s performance and keep downtimes at bay.
The Way Forward
Malicious bots are everywhere and are more sophisticated than ever. Only blocking bots is not an efficient and long-term solution to a growing threat. Instead, it is vital to have a proactive bot protection approach to move forward.
By choosing a managed, intelligent, and advanced bot mitigation solution like AppTrana, you can ensure multi-layered, real-time protection against all kinds of bad bots. It also offers visibility into the threats to block ongoing attacks.
The post Why Do You Need a Bot Protection Solution for Your Business? appeared first on Cybersecurity Insiders.