Category: LastPass
ConnectWise, a self-hosted, remote desktop software application that is widely used by Managed Service Providers (MSPs), is warning about an unusually sophisticated phishing attack that can let attackers take remote control over user systems when recipients click the included link. The warning comes just weeks after the company quietly patched a vulnerability that makes it easier for phishers to launch these attacks.

A phishing attack targeting MSP customers using ConnectWise.
ConnectWise’s service is extremely popular among MSPs that manage, protect and service large numbers of computers remotely for client organizations. Their product provides a dynamic software client and hosted server that connects two or more computers together, and provides temporary or persistent remote access to those client systems.
When a support technician wants to use ConnectWise to remotely administer a computer, the ConnectWise website generates an executable file that is digitally signed by ConnectWise and downloadable by the client via a hyperlink.
When the remote user in need of assistance clicks the link, their computer is then directly connected to the computer of the remote administrator, who can then control the client’s computer as if they were seated in front of it.
While modern Microsoft Windows operating systems by default will ask users whether they want to run a downloaded executable file, many systems set up for remote administration by MSPs disable that user account control feature for this particular application.
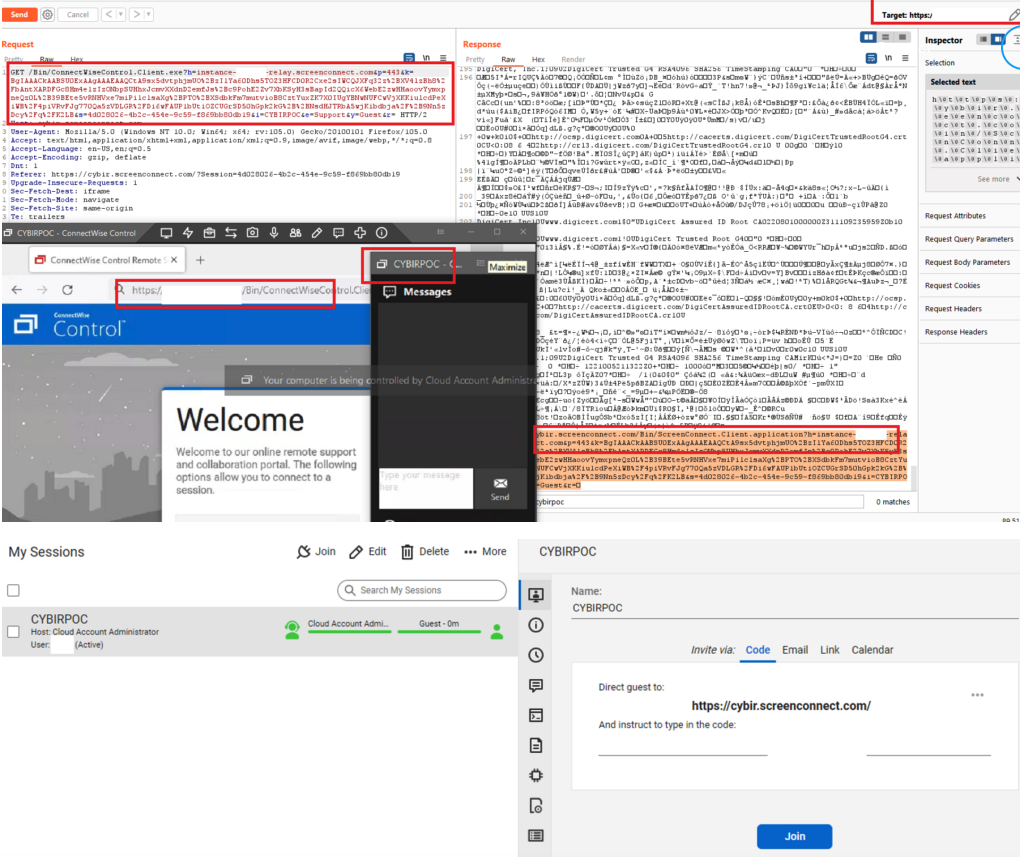
In October, security researcher Ken Pyle alerted ConnectWise that their client executable file gets generated based on client-controlled parameters. Meaning, an attacker could craft a ConnectWise client download link that would bounce or proxy the remote connection from the MSP’s servers to a server that the attacker controls.
This is dangerous because many organizations that rely on MSPs to manage their computers often set up their networks so that only remote assistance connections coming from their MSP’s networks are allowed.
Using a free ConnectWise trial account, Pyle showed the company how easy it was to create a client executable that is cryptographically signed by ConnectWise and can bypass those network restrictions by bouncing the connection through an attacker’s ConnectWise control server.
“You as the attacker have full control over the link’s parameters, and that link gets injected into an executable file that is downloaded by the client through an unauthenticated Web interface,” said Pyle, a partner and exploit developer at the security firm Cybir. “I can send this link to a victim, they will click this link, and their workstation will connect back to my instance via a link on your site.”
A composite of screenshots researcher Ken Pyle put together to illustrate the ScreenConnect vulnerability.
On Nov. 29, roughly the same time Pyle published a blog post about his findings, ConnectWise issued an advisory warning users to be on guard against a new round email phishing attempts that mimic legitimate email alerts the company sends when it detects unusual activity on a customer account.
“We are aware of a phishing campaign that mimics ConnectWise Control New Login Alert emails and has the potential to lead to unauthorized access to legitimate Control instances,” the company said.
ConnectWise said it released software updates last month that included new protections against the misdirection vulnerability that Pyle reported. But the company said there is no reason to believe the phishers they warned about are exploiting any of the issues reported by Pyle.
“Our team quickly triaged the report and determined the risk to partners to be minimal,” ConnectWise spokesperson Tarran Street said. “Nevertheless, the mitigation was simple and presented no risk to partner experience, so we put it into the then-stable 22.8 build and the then-canary 22.9 build, which were released as part of our normal release processes. Due to the low severity of the issue, we didn’t (and don’t plan to) issue a security advisory or alert, since we reserve those notifications for serious security issues.”
Pyle said he doubts the issue he reported is unrelated to the phishing attacks ConnectWise is warning about.
“They don’t want to talk about my work (no advisory), and they recommend applying the patch they issued in response to my work,” Pyle wrote when asked to comment on ConnectWise’s response.
The ConnectWise advisory warned users that before clicking any link that appears to come from their service, users should validate the content includes “domains owned by trusted sources,” and “links to go to places you recognize.”
But Pyle said this advice is not terribly useful for customers, because in his attack scenario the phishers can send emails directly from ConnectWise, and the short link that gets presented to the user is a wildcard domain that ends in ConnectWise’s own domain name — screenconnect.com. What’s more, examining the exceedingly long link generated by ConnectWise’s systems offers few insights to the average user.
“It’s signed by ConnectWise and comes from them, and if you sign up for a free trial instance, you can email people invites directly from them,” Pyle said.
ConnectWise’s warnings come amid breach reports from another major provider of cloud-based remote support technologies: GoTo disclosed on Nov. 30 that it is investigating a security incident involving “unusual activity within our development environment and third-party cloud storage services. The third-party cloud storage service is currently shared by both GoTo and its affiliate, the password manager service LastPass.
In its own advisory on the incident, LastPass said they believe the intruders leveraged information stolen during a previous intrusion in August 2022 to gain access to “certain elements of our customers’ information.” However, LastPass maintains that its “customer passwords remain safely encrypted due to LastPass’s Zero Knowledge architecture.”
In short, that architecture means if you lose or forget your all-important master LastPass password — the one needed to unlock access to all of your other passwords stored with them — LastPass can’t help you with that, because they don’t store it. But that same architecture theoretically means that hackers who might break into LastPass’s networks can’t access that information either.
1.) From the past few hours, a news piece related to Wi-Fi vulnerability on Android phones is doing rounds on the internet and security analysts state that the threat could be larger than what is being projected. A TikTok star(tatechtips) having fascination towards technology has revealed in one of his videos that just by turning of Wi-Fi feature on an android phone doesn’t save from prying eyes. As even when the feature is turned on, the device is constantly sending requests to get Wi-Fi, as it is seen constantly running in the background scanning for networks.
2.) Second is the news related to Baton Rouge General Health System (GHS), a healthcare service provider that disclosed yesterday that it was hit by a cyber attack in June this year leaking patient details to hackers.
GHS confirmed the incident took place on June 28th,2022 and concluded that an unauthorized access took place on its servers leaking patient data to hackers and locking down the systems with encryption- meaning it was a ransomware attack.
3.) Third is the news related to Napa Valley College, which released a press statement admitting a ransomware attack. Preliminary inquiries revealed the ransomware attack propelled breach resulted in the leak of names, social security numbers and some student details that might lead to identify thefts and other kind of cyber frauds.
4.) Baker & Taylor, the largest distributor of books and study material worldwide, has admitted that it became a victim of a ransomware attack on August 23rd,2022 and the outage affected offices, service centers and phone lines.
The library having a history of existing in business from the past 100+ years is busy in restoring the services and is confident that it can recover easily from the malware incident as it has an efficient business continuity plan.
5.) The other news that is trending is related to the midterm elections that are on the way shortly. Citing security reasons, the US Cyber Command has joined hands with the NSA to curb fake news spread and to block any hacking efforts during and before the upcoming midterm elections scheduled at the end of November this year.
Thus, the Election Security Group (ESG) will function under the US Cyber Command and NSA to conduct upcoming elections smoothly, with no interference from adversaries.
6.) Sixth is the news related to a penalty imposed by the California’s Consumer Privacy court. Rob Bonta, the state’s attorney general, imposed a $1.2 million penalty on cosmetics giant Sephora for selling personal info of its customers to third parties without informing them in prior. The court pronounced the statement after reviewing the evidence that the company sold the information such as shopping contents, precise location and devices used by customers for a lucrative price.
7.) Group IB, a security firm by profession, has discovered that a new phishing campaign is targeting Okta Identity Credentials of those victims, mainly in Canada, UK and United States. And the affected companies are mostly from IT and software development sector.
8.) LastPass, a password management firm having about 33 million global users, has revealed that it leaked some sensitive details pertaining to the company in a security incident that took place on August 15th of this year. So, it is urging all its users to change their passwords ASAP and is probing further on whether the criminals had access to the master password/s.
9.) On the occasion of World Video Game Day, CheckPoint researchers have revealed that almost all gamers across the world are on the verge of being hacked to steal games from inventory, to gain access to the device from the user is playing and to conduct identity thefts and bank frauds. So, the company has issued an advisory for gamers to stay away from phishing links, be cautious about false promises and to implement a 2FA in order to stay well protected.
The post Nine cyber-attack news headlines trending on Google appeared first on Cybersecurity Insiders.
LastPass, the popular password manager used by millions of people around the world, has announced that it suffered a security breach two weeks ago that saw attackers break into its systems and steal information. But don’t panic just yet – that doesn’t mean that all of your passwords are now in the hands of internet […]… Read More
The post LastPass attackers steal source code, no evidence users’ passwords compromised appeared first on The State of Security.