WithSecure, previously F-Secure for Business, has established itself as a leader in the cybersecurity sector since its inception in 1988. With a global footprint spanning Europe, North America, and Asia Pacific, the company has shown robust growth, especially in its cloud solutions segment, which saw a 34% increase in ARR from 2020 to 2021. Catering to over 100,000 corporate customers through a network of more than 7,000 partners, WithSecure has honed its focus on corporate security, a strategic shift from its previous broader scope that included consumer security under the F-Secure brand. This reorientation aligns with the rapidly changing cyber threat landscape and the growing importance of digitization in business.
This review will focus on WithSecure’s innovative approach to tackling current and emerging cybersecurity challenges. We will examine its suite, encompassing Elements Vulnerability Management, Elements Cloud Security Posture Management, Elements Collaboration Protection, Elements Detection and Response, and Elements Endpoint Protection, and how these align with the critical cybersecurity framework of Predict, Prevent, Detect, and Respond. By doing so, we will highlight how WithSecure’s solutions not only respond to immediate threats but also proactively adapt to protect against future vulnerabilities in an increasingly dynamic digital world.
WithSecure’s Comprehensive Cybersecurity Services
WithSecure™ offers a diverse array of cybersecurity solutions tailored for modern business needs, encompassing managed services, consulting, the Elements suite, and cloud protection.
- WithSecure Elements – The Elements suite is a modular and comprehensive cybersecurity solution offering end-to-end protection. It includes applications for endpoint protection, detection and response, vulnerability management, and cloud security, adaptable to specific business needs.
- Managed Services – WithSecure’s managed services and managed detection and response handle cybersecurity operations, including continuous monitoring, threat detection, and incident response, relieving businesses from the intricacies of cybersecurity management.
- Consulting Services – The consulting division provides expert guidance in cybersecurity strategy, risk management, and compliance, helping businesses navigate complex cybersecurity landscapes and regulatory requirements.
- Cloud Protection – Specializing in cloud security, WithSecure’s services focus on securing cloud environments, managing cloud security posture, and ensuring compliance, crucial for businesses utilizing cloud-based operations. WithSecure also offers a Cloud Protection for Salesforce solution, designed to prevent attacks via files and URLs uploaded to Salesforce Clouds.
WithSecure’s range of services reflects its commitment to delivering versatile and robust cybersecurity solutions, catering to the diverse and evolving needs of the business landscape.
A Deep Dive into WithSecure Elements
The WithSecure™ Elements product suite is a comprehensive cybersecurity solution including vulnerability management, patch management, endpoint protection, endpoint detection and response technologies, Microsoft 365 coverage, and cloud security posture management. The Elements product suite offers end-to-end business and cloud coverage, aiming to provide a resilient business environment in today’s dynamic business landscape.
Key solutions in the WithSecure™ Elements suite include:
- Elements Endpoint Protection: This platform offers multi-layer anti-malware and anti-ransomware technology, integrated and automated patch management, application control, hardware encryption management, and enhanced ransomware protection with rollback capabilities.
- Elements Endpoint Detection and Response: This includes automated threat identification and analysis, access to expert assistance from WithSecure’s threat hunters, identification of fileless attacks, automated response actions, and advanced investigation and response tools.
- Elements Vulnerability Management: This involves agent and network-based vulnerability scanning, consolidated reporting, industry-standard vulnerability lists enhanced by WithSecure’s consultants, service configuration checks, and risk scoring for prioritization.
- Elements Collaboration Protection: This secures M365 collaboration tools such as email, Sharepoint, Teams and OneDrive with features like seamless cloud integration, continuous scanning, advance email security and compromised account detection which securely checks users’ email addresses and instantly notifies of compromised accounts in the wild. Collaboration Protection also provides information about the severity of the compromised accounts, based on the type of information that was compromised.
- Elements Cloud Security Posture Management: This offers efficient detection of misconfigurations, threat model-informed checks, end-to-end use cases, intuitive views for understanding risk and security posture, and support for multi-cloud IT environments such as AWS and Azure.
Moreover, WithSecure™ Elements features flexible pricing models and a modular structure, allowing businesses to tailor their cybersecurity packages to their specific needs.
WithSecure Elements Endpoint Protection Platform
WithSecure’s Endpoint Protection platform is a key component of the WithSecure Elements suite, designed to provide comprehensive protection against a wide range of cyber threats, including malware, ransomware, and sophisticated attacks. This platform embodies a blend of advanced technology, ease of use, and integration with broader cybersecurity measures, making it a robust solution for modern businesses.
Core Features of WithSecure Endpoint Protection
- Continuous Threat Protection: The platform ensures ongoing defense against known and unknown ransomware, malware, and viruses. This includes real-time monitoring and prevention of threats, ensuring uninterrupted protection of endpoints.
- AI-Powered Security: Utilizing artificial intelligence, WithSecure’s Endpoint Protection can identify and counteract the most sophisticated forms of malware and ransomware. This AI capability enhances the platform’s effectiveness in recognizing and responding to new and evolving threats.
- Automated Patch Management: An integral part of the platform is its automated patch management system. This feature keeps OS patches and third-party software up-to-date, addressing vulnerabilities promptly and reducing the window of opportunity for attackers to exploit outdated software.
- Layered Ransomware Protection: The platform offers multi-layered defense mechanisms specifically against ransomware. This includes enhanced control over data and applications, ensuring that critical assets are safeguarded even in the event of an attack. WithSecure Rollback provides a further layer of protection to Elements Endpoint Protection, allowing you to restore original files and settings on a device in the rare event that defenses are unable to prevent a successful attack.
- Autonomous Operation: Designed for minimal manual intervention, the Endpoint Protection platform automates many of the routine tasks associated with cybersecurity. This reduces the workload on IT staff and ensures a consistent security posture.
- Broad Platform Coverage: WithSecure’s solution covers a wide range of operating systems and devices, including Mac, Windows, Linux computers and servers, and mobile devices. This broad coverage ensures that organizations can protect all their endpoints, regardless of the underlying platform.
- Integration with Third-Party Solutions: The Endpoint Protection platform can connect easily with third-party SIEM (Security Information and Event Management) management or reporting solutions. This interoperability allows for seamless integration into an organization’s existing cybersecurity infrastructure. WithSecure Elements API provides an interface to access the WithSecure products through the REST API endpoints.
- Advanced Attack Detection: The platform can swiftly and accurately detect advanced and targeted attacks, reducing the noise of false alerts and focusing on genuine threats.
- Clear Attack Visualizations
WithSecure’s Endpoint Protection platform stands out for its comprehensive protection capabilities, AI-powered security, and automated operations. Its integration with the wider Elements suite and third-party solutions, along with its broad platform coverage, makes it a versatile and effective solution for safeguarding endpoints in today’s complex cybersecurity landscape.
WithSecure Elements Endpoint Detection and Response
WithSecure Elements Endpoint Detection and Response (EDR) is a critical component of the WithSecure Elements suite, designed to provide advanced capabilities for detecting, analyzing, and responding to cybersecurity threats, particularly sophisticated and targeted attacks. This solution is tailored to offer fast, efficient, and accurate responses to cyber incidents, making it a vital tool in the cybersecurity arsenal of modern organizations.
Key Features of WithSecure Elements EDR
- Advanced Threat Detection: WithSecure EDR is engineered to detect sophisticated cyber threats that might evade traditional security measures. It specializes in identifying complex attack patterns and advanced threats, ensuring that organizations can respond to incidents that would otherwise go unnoticed.
- Noise Reduction and Accuracy: A significant advantage of WithSecure EDR is its ability to minimize false positives (‘alert noise’), allowing security teams to focus on genuine threats. This accuracy ensures that the resources are dedicated to countering real, impactful threats.
- Clear Visualization of Threats: Understanding the nature and scope of an attack is crucial. WithSecure EDR provides clear and intuitive visualizations of attack chains, making it easier for security teams to comprehend complex incidents and plan their response strategies accordingly.
- Broad Set of Response Actions: The platform offers a wide array of response options to address various types of threats. This includes capabilities like automated host isolation, which enables organizations to quickly contain threats and prevent them from spreading across the network.
- Swift and Accurate Response: The EDR platform is designed for rapid and precise action, ensuring that threats are addressed quickly and effectively. This rapid response capability is crucial in minimizing the potential damage from cyber incidents.
- Comprehensive Protection: When combined with other Elements offerings, such as Endpoint Protection, Vulnerability Management, and Collaboration Protection, EDR provides a more holistic approach to cybersecurity.
- Centralized Management: Managed through the One Security Center, it allows for streamlined control and oversight of cybersecurity operations across an organization.
WithSecure’s EDR platform offers a range of services designed to enhance threat detection and response capabilities for organizations, including:
- Co-Monitoring Service
- Expert Threat Investigation and Response: The platform “Elevate to WithSecure” provides on-demand access to WithSecure’s elite threat hunters and incident response experts. This team can offer in-depth analysis and actionable guidance for incidents detected by the EDR tool, ensuring that organizations have the expertise needed to respond effectively to complex threats.
WithSecure’s Elements Endpoint Detection and Response is a sophisticated and integral part of an organization’s cybersecurity strategy. It excels in detecting advanced threats, reducing false alerts, and providing clear visualizations of attack chains, all while offering a broad array of responsive actions. The integration with the broader Elements suite and the availability of expert support through co-monitoring and incident response services underscore its role as a comprehensive tool for modern cyber threat management.
WithSecure Elements Vulnerability Management
WithSecure Elements Vulnerability Management is a pivotal component of the WithSecure Elements suite, designed to address the critical aspect of identifying and managing vulnerabilities in an organization’s digital infrastructure. This solution plays a key role in preempting cyber threats by systematically identifying, assessing, and guiding the remediation of vulnerabilities.
Key Features of WithSecure Elements Vulnerability Management
The WithSecure Elements Vulnerability Management platform is equipped with several advanced features aimed at enhancing cybersecurity measures for organizations. Key features include:
- Comprehensive Vulnerability Scanning: The platform provides thorough scanning capabilities, covering both agent-based and network-based assessments. This dual approach ensures that vulnerabilities are identified across a wide range of devices and environments.
- Consolidated Reporting: It offers detailed, consolidated reports on each asset or device. This feature aids in providing a clear understanding of the security posture of various components within the network and highlights areas that require attention.
- Enhanced Vulnerability Lists: Utilizing industry-standard vulnerability lists, further enhanced by WithSecure’s own research and consulting expertise, the tool ensures that the most current and relevant vulnerabilities are being tracked and addressed.
- Service Configuration Checks: Beyond software vulnerabilities, the platform also checks for misconfigurations in services, a critical aspect often overlooked but essential for comprehensive security.
- Risk Scoring and Prioritization: WithSecure Elements Vulnerability Management incorporates risk scoring, enabling organizations to prioritize remediation efforts based on the severity and potential impact of each identified vulnerability.
- Integration with Elements Suite: As a part of the broader Elements suite, this vulnerability management tool benefits from seamless integration with other components like Endpoint Protection and Endpoint Detection and Response. This integration enhances the overall security strategy by providing a holistic approach to cyber defense.
Streamlined Management and Remediation
WithSecure Elements Vulnerability Management streamlines the management and remediation process of vulnerabilities, offering features that are designed to enhance efficiency and clarity in handling cybersecurity threats. Key aspects of this streamlined approach include:
- Efficient Detection and Response: The tool facilitates efficient detection of vulnerabilities, saving time and resources for organizations.
- Actionable Insights for Remediation: WithSecure Elements Vulnerability Management not only identifies vulnerabilities but also provides actionable insights for their remediation. This feature is crucial for quickly addressing security gaps and enhancing the overall cybersecurity posture.
- Visual Reports for Administrators: The platform offers visual reporting tools that empower administrators to make informed decisions about security improvements. These reports can also serve as valuable evidence for auditors and regulators, demonstrating proactive vulnerability management.
WithSecure’s Elements Vulnerability Management is an essential tool in the cybersecurity toolkit of any modern organization. It excels in providing comprehensive vulnerability scanning, enhanced vulnerability tracking, and effective risk management and prioritization. Integrated within the WithSecure Elements suite, it works in conjunction with other cybersecurity components to offer a layered and robust defense against potential cyber threats. This solution not only identifies and assesses vulnerabilities but also guides organizations in efficiently remediating them, thereby strengthening their overall security posture.
WithSecure Elements Collaboration Protection
WithSecure Elements Collaboration Protection is a specialized component within the WithSecure Elements suite, focusing on securing collaborative environments, particularly those utilizing Microsoft 365. In an era where collaboration tools are integral to business operations, this solution plays a crucial role in safeguarding against threats that specifically target these platforms.
Elements Collaboration Protection is designed with several key functionalities to ensure comprehensive security for collaborative tools:
- Phishing and Malware Defense: It is equipped to block phishing attempts and malicious content in Microsoft 365 environments, particularly targeting Outlook emails, tasks, and SharePoint. This feature is critical in preventing the most common vectors of cyber attacks in collaborative spaces.
- Sandboxing and Analysis: Suspicious content is analyzed in an isolated sandbox environment. This approach allows for safe examination and neutralization of potential threats without risking the integrity of the actual operational environment.
- Seamless Integration: The solution offers seamless integration with Microsoft 365, requiring no extra middleware or software. Its cloud-to-cloud deployment means it can be set up quickly and managed easily.
- Behavioral Anomalies and Account Breach Detection: Trust in communication and collaboration tools is paramount. This feature of WithSecure Elements Collaboration Protection detects behavioral anomalies and identifies breached company accounts, enhancing the security of digital identities within an organization.
- Rapid Cloud Deployment: The solution can be deployed from the cloud in just a few minutes, leveraging cloud-to-cloud integration. This rapid deployment is not only efficient but also minimizes disruptions to business operations.
- Comprehensive Collaboration Coverage: It provides protection across all key Microsoft 365 collaboration capabilities, including Email (Exchange Online), SharePoint, Teams, and OneDrive.
- Continuous File and URL Analysis: The solution continuously analyzes files and URLs within the Microsoft 365 ecosystem using sandboxing and machine learning-based heuristics. This continuous analysis is vital for detecting and neutralizing threats in real-time.
- Compromised Account Monitoring: Collaboration Protection monitors external information sources to swiftly notify organizations of breached accounts, ensuring quick response to potential security incidents.
WithSecure’s Elements Collaboration Protection is a vital component for businesses leveraging collaborative tools, especially within the Microsoft 365 framework. Its blend of phishing and malware defense, advanced sandboxing techniques, seamless integration, and comprehensive coverage across collaboration platforms makes it an indispensable tool for safeguarding collaborative workspaces. This solution not only enhances the security of these environments but also instills confidence in their safe and secure use for daily business operations.
WithSecure Elements Cloud Security Posture Management
WithSecure Elements Cloud Security Posture Management (CSPM) is a critical component of the WithSecure Elements suite, specifically designed to enhance the security posture of cloud environments. As businesses increasingly migrate to the cloud, managing and securing these environments becomes paramount. Elements CSPM addresses this need by offering tools to identify and remediate potential security risks and misconfigurations in cloud infrastructures.
Elements CSPM is structured to provide comprehensive management and security oversight of cloud infrastructures:
- Efficient Misconfiguration Identification: The solution enables efficient detection of misconfigurations in cloud settings, a common source of security vulnerabilities. By identifying these issues swiftly, it helps in preventing potential data leaks or attacks.
- Risk Complexity and Inefficiency Reduction: WithSecure CSPM prioritizes remediation efficiently based on the level of risk and effort required. This feature assists organizations in focusing their resources on the most critical issues first.
- Intuitive Views and Visual Reports: The platform provides intuitive views and visual reports, summarizing the security posture of cloud environments. These reports are not only useful for administrators in enhancing security measures but also serve as evidence for auditors and regulators.
Enhancing Cloud Security Management
Elements CSPM is designed to streamline and improve the management of cloud security risks:
- Spotting Mistakes Before Attackers Do: By covering end-to-end use cases, the solution makes the daily job of managing cloud security easier. It helps organizations stay one step ahead by identifying potential security lapses before they can be exploited by attackers.
- Actionable Insights for Quick Remediation: The solution offers actionable insights to quickly remediate identified misconfigurations. This proactive approach is key in maintaining a robust security posture in dynamic cloud environments.
- Multi-Cloud and Multi-Company Management: Recognizing the complexity of modern IT environments, WithSecure CSPM is capable of managing multiple cloud infrastructures, including AWS and Azure, as well as offering multi-company management. This makes it a versatile tool for organizations operating in diverse and complex cloud environments.
WithSecure’s Elements Cloud Security Posture Management is an essential solution for businesses operating in the cloud. It addresses the critical need for continuous monitoring and management of cloud security risks. By providing tools for efficient detection, prioritization, and remediation of misconfigurations, coupled with intuitive reporting and insights, Elements CSPM plays a vital role in strengthening an organization’s cloud security posture. This solution not only helps in safeguarding cloud environments but also ensures that businesses can confidently leverage the benefits of cloud computing while minimizing security risks.
WithSecure Cybersecurity Management
A standout feature of the WithSecure Elements suite is its streamlined approach to cybersecurity management, exemplified by the Single Agent and One Security Center functionalities. These features are designed to simplify and enhance the efficiency of security operations for businesses.
Single Agent Architecture
The Single Agent architecture in WithSecure Elements represents a significant advancement in endpoint security. This approach minimizes the complexity typically associated with deploying multiple security agents on each endpoint. Instead, a single agent is responsible for various security functions, including real-time threat detection, response, and prevention. This unified agent architecture not only reduces the system overhead but also simplifies management and deployment, ensuring that endpoints are consistently protected without compromising performance.
Key benefits of the Single Agent include:
- Simplified Deployment and Management: By consolidating multiple functionalities into a single agent, WithSecure Elements reduces the time and effort required for deployment and ongoing management.
- Enhanced Performance and Reduced Overhead: A single, lightweight agent means less strain on endpoint resources, maintaining system performance while ensuring robust security.
- Consistent Security Posture: With all security functions integrated into one agent, there’s a uniformity in security policies and response mechanisms across all endpoints.
Elements Security Center
The Elements Security Center is the central management console of the WithSecure Elements suite, offering a unified view and control over the entire cybersecurity landscape of an organization. This centralized platform streamlines the management of security policies, threat intelligence, incident response, and reporting.
Features of the Elements Security Center include:
- Centralized Control and Visibility: Administrators can oversee and control the security posture of the entire organization from a single dashboard, enhancing decision-making and response times.
- Simplified Incident Management: Elements Security Center allows for efficient tracking, investigation, and response to security incidents, all from a centralized location.
In summary, the Single Agent and Elements Security Center are foundational elements of the WithSecure Elements suite, embodying a philosophy of streamlined and efficient cybersecurity management. These features not only reduce the complexity of security operations but also empower organizations with enhanced visibility and control over their security infrastructure.
WithSecure Co-Security Services
WithSecure’s Co-Security Services are an integral part of their cybersecurity offerings, designed to extend and enhance the capabilities of organizations in managing and responding to cyber threats. These services represent a collaborative approach to security, where WithSecure works alongside the organization’s internal team, providing expert support and additional resources to bolster their cybersecurity efforts.
WithSecure Co-Security Services encompass several critical functions that collectively strengthen an organization’s security posture:
- 24/7 Monitoring and Vigilance: Recognizing that cyber threats do not adhere to typical office hours, WithSecure offers round-the-clock monitoring of severe-risk detections. This continuous vigilance ensures that threats are identified and addressed promptly, providing comprehensive protection at all times.
- Expert Threat Investigation: The service includes detailed validation and investigation of severe-risk detections by human threat analysts. This expert analysis is crucial for accurately identifying true positives that require immediate action, thereby reducing the time to respond to genuine threats.
- Incident Escalation and Containment Advice: Confirmed attacks are escalated directly to the relevant representatives within the customer’s organization. The threat analyst also provides containment advice for fast and effective remediation, crucial for minimizing the impact of security incidents.
- Flexible Escalation to Incident Response Services: Organizations have the option to escalate incidents to WithSecure’s Incident Response services, with or without a retainer. This flexibility ensures that businesses can access the level of support they need, tailored to the specific incident at hand.
Enhancing Organizational Security Capabilities
WithSecure’s Co-Security Services are designed to complement and extend the capabilities of an organization’s internal security team, delivering a range of benefits:
- Extend the Security Team: The services effectively augment the organization’s security team by providing constant and instant access to WithSecure’s team of seasoned cybersecurity experts. This collaboration ensures that organizations are not alone in their cybersecurity endeavors.
- Provide On-Demand Threat Response: With the option for 24/7 on-demand threat response, organizations can rely on WithSecure for expert threat investigation and response guidance whenever needed via the Elevate to WithSecure option. This immediate access to expertise is especially valuable in handling complex or rapidly evolving threats.
- Minimize Attack Impact: With the support of elite threat hunters and incident response experts, organizations can stop even the most challenging attacks in their tracks, significantly minimizing potential damage.
WithSecure’s Co-Security Services represent a proactive and collaborative approach to cybersecurity, offering organizations the expertise and support needed to effectively manage and respond to cyber threats. By providing continuous monitoring, expert analysis, and flexible response options, these services enable organizations to enhance their security posture and respond more effectively to incidents, ensuring a more resilient and secure operational environment.
Conclusion
In conclusion, WithSecure™ emerges as a formidable player in mid-market cybersecurity, with a robust portfolio of products designed to address the complex and evolving challenges in the digital landscape.
At a time where cyber threats evolve rapidly, WithSecure’s holistic cybersecurity approach, encapsulating the core principles of Predict, Prevent, Detect, and Respond, provides a robust and comprehensive defense strategy. With elements like Vulnerability Management and Cloud Security Posture Management for prediction, Collaboration Protection and Endpoint Protection for prevention, and Endpoint Detection and Response for both detection and rapid response, WithSecure offers an integrated suite that not only anticipates and shields against potential threats but also swiftly identifies and mitigates any breaches, ensuring a resilient and secure digital ecosystem for organizations navigating the complex cyber landscape.
For more information, visit https://www.withsecure.com/en/home
The post Future-Proofing Cybersecurity: A Deep Dive into WithSecure’s Innovative Mid-Market Security Solutions appeared first on Cybersecurity Insiders.
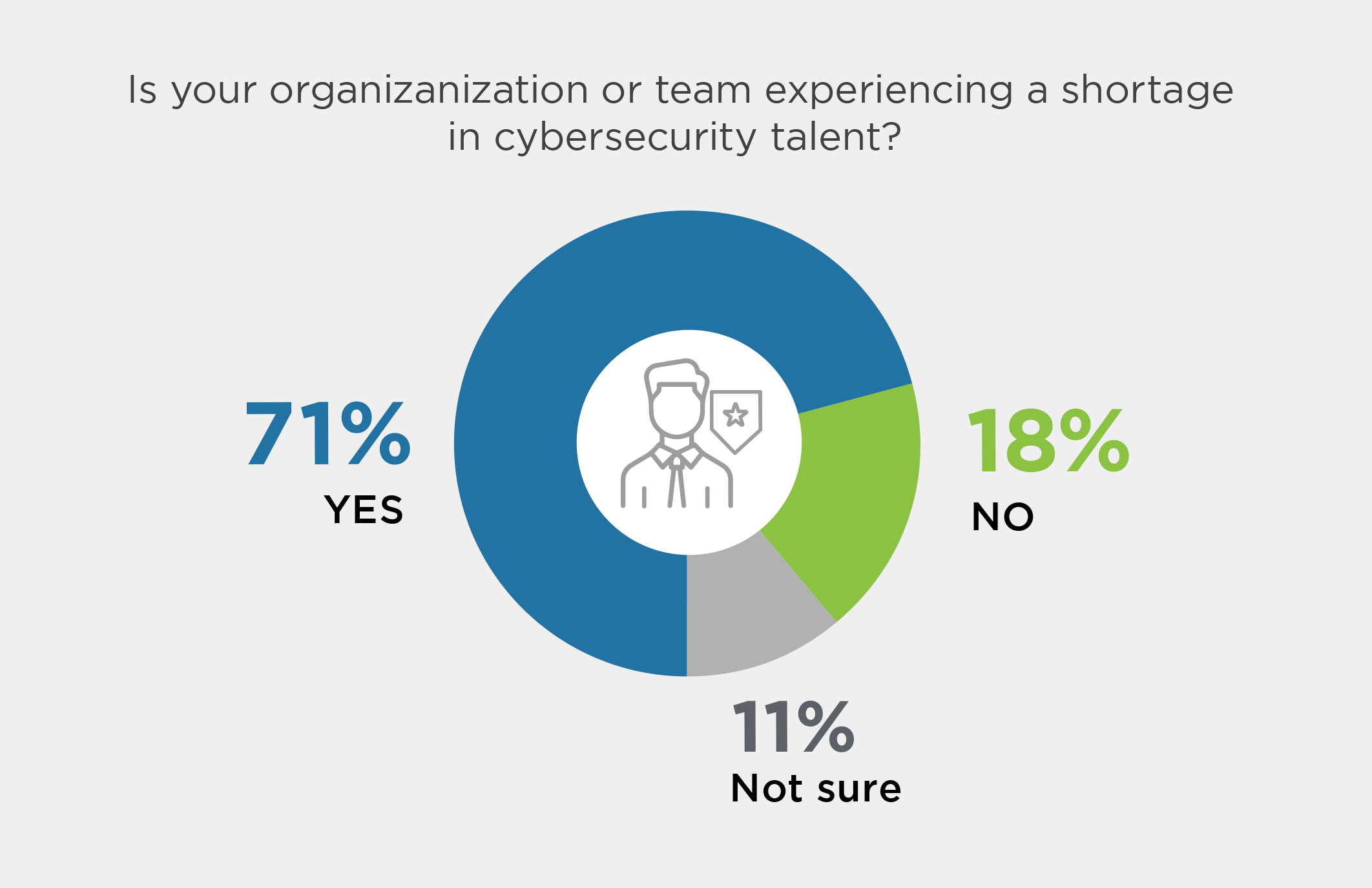 Source: 2023 Cloud Security Report produced by Cybersecurity Insiders
Source: 2023 Cloud Security Report produced by Cybersecurity Insiders