With the increasing need for online privacy and security, Virtual Private Networks (VPNs) have become a popular solution for internet users. VPNs allow users to access the internet securely and privately by encrypting their internet traffic and hiding their IP addresses. However, with so many VPN providers available, it can be challenging to choose the best VPN for your needs. In this article, we will guide you through the process of choosing the best VPN for your needs.
The first step in choosing the best VPN is to determine your needs. Do you need a VPN for streaming, torrenting, or online gaming? Or do you need a VPN for general internet use? Different VPNs specialize in different areas, and it’s essential to choose a VPN that caters to your specific needs. Additionally, you need to consider the number of devices you want to connect to the VPN and the level of security you require.
Once you have determined your needs, the next step is to research the available VPN providers. Look for VPNs that offer a high level of security, a large number of servers in multiple locations, and fast connection speeds. Check the VPN’s logging policy to ensure that they do not keep logs of your internet activity. You can also read reviews and check the VPN’s reputation to ensure that they are reliable and trustworthy.
What is a VPN?
A Virtual Private Network (VPN) is a service that allows you to connect to the internet through a secure and encrypted connection. When you use a VPN, your internet traffic is routed through an encrypted tunnel, which makes it difficult for anyone to intercept or monitor your online activities.
VPNs are commonly used to protect your privacy and security online. They can help you avoid government surveillance, protect your personal data from hackers and cybercriminals, and allow you to access content that may be restricted in your region.
VPNs work by creating a secure connection between your device and the VPN server. This connection is encrypted, which means that all of your internet traffic is protected from prying eyes. When you connect to a VPN server, your IP address is masked, which makes it difficult for websites and online services to track your location or identity.
Many VPNs also offer additional features, such as ad-blocking, malware protection, and the ability to access content from other countries. Some VPNs are also optimized for specific activities, such as streaming or torrenting.
Why You Need a VPN
Virtual Private Networks (VPNs) are becoming increasingly popular as people become more aware of the importance of online privacy and security. A VPN can help protect your online activity from prying eyes and ensure that your sensitive information is kept safe from hackers and other malicious actors. Here are some of the main reasons why you need a VPN:
- Security: A VPN encrypts your internet traffic, making it virtually impossible for anyone to intercept or steal your data. This is especially important when using public Wi-Fi networks, which are often unsecured and vulnerable to hacking.
- Privacy: A VPN masks your IP address and location, making it difficult for websites and advertisers to track your online activity. This can help prevent targeted ads, profiling, and other forms of online surveillance.
- Access: A VPN can help you bypass geo-restrictions and censorship, allowing you to access content that may be blocked in your country or region. This is particularly useful for streaming services, which often have different content libraries depending on your location.
While a VPN is not a silver bullet for online security and privacy, it can certainly help improve your overall online experience. However, it’s important to choose the right VPN for your needs and use it properly to maximize its benefits.
Factors to Consider When Choosing a VPN
Security Features
One of the most important factors to consider when choosing a VPN is the security features it offers. Look for a VPN that uses strong encryption protocols like AES and Blowfish. Additionally, check if the VPN has a kill switch, which will automatically disconnect you from the internet if the VPN connection drops, preventing your IP address from being exposed. Also, consider if the VPN has a no-logs policy, which means that it does not keep any records of your online activities.
Speed and Performance
Another important factor to consider when choosing a VPN is speed and performance. Look for a VPN that offers fast speeds and low latency. Additionally, check if the VPN has servers in locations that are close to your location, as this will help reduce latency and improve performance. Also, consider if the VPN offers unlimited bandwidth, which will allow you to stream and download content without any restrictions.
Server Locations
When choosing a VPN, it’s important to consider the number and location of the VPN’s servers. Look for a VPN that has servers in the locations you need, such as the country or region you want to access content from. Additionally, consider if the VPN has servers in locations that are close to your physical location, as this will help improve performance and reduce latency.
Ease of Use
Another important factor to consider when choosing a VPN is ease of use. Look for a VPN that has an easy-to-use interface and is user-friendly. Additionally, check if the VPN has a mobile app, which will allow you to use the VPN on your smartphone or tablet. Also, consider if the VPN offers customer support, which will help you troubleshoot any issues you may encounter.
Compatibility
When choosing a VPN, it’s important to consider compatibility. Look for a VPN that is compatible with the devices and operating systems you use, such as Windows, macOS, iOS, and Android. Additionally, check if the VPN can be used on multiple devices simultaneously, which will allow you to protect all your devices with a single VPN subscription.
Price and Plans
Finally, when choosing a VPN, consider the price and plans offered by the VPN provider. Look for a VPN that offers affordable pricing and a range of plans to choose from. Additionally, check if the VPN offers a free trial or money-back guarantee, which will allow you to test the VPN before committing to a subscription.
Top VPN Providers
There are numerous VPN providers in the market, and it can be challenging to choose the right one. To help you make an informed decision, we have compiled a list of the top VPN providers based on our research and analysis.
ExpressVPN
ExpressVPN is a top choice for its excellent privacy protection and speed. It offers an intuitive user interface and is known for its reliable performance. The pricing is competitive when signing up for a 12-month plan, which includes 3 free months.
NordVPN
NordVPN is a popular choice for its range of features and multi-year plan pricing. Known for its enhanced security options, NordVPN also offers add-ons to customize the user experience. It’s a strong runner-up contender in the best VPN list.
Surfshark
Surfshark is ideal for budget-conscious users who do not want to compromise on features. It provides a high level of privacy, speed, and unlimited device connections, making it a top choice for families and small businesses alike.
IPVanish
IPVanish offers an intuitive user experience with its easy-to-navigate interface. The VPN provides strong security features and customizable settings for optimal privacy protection. Its competitive pricing makes it a favorite among users.
VPN Unlimited (aka KeepSolid)
VPN Unlimited is ideal for users requiring a multi-device connection. It offers a smooth app interface and user-friendly customization options. Additionally, the pricing is affordable when considering the features provided.
CyberGhost
CyberGhost VPN is a great option for users who want a balance between speed and security. With a user-friendly interface and multiple server locations, CyberGhost is a reliable choice for users seeking an all-around robust VPN experience.
These VPN providers are among the best in the market and offer excellent value for money. However, it is essential to choose a VPN provider that meets your specific needs and requirements. Consider factors like server locations, security features, speed, and pricing before making a decision.
Frequently Asked Questions
Here are some common questions and answers related to VPN services and their features:
- Which VPN has the best overall performance?
ExpressVPN is often considered the best all-around VPN, thanks to its impressive speed, strong security, and user-friendly interface. It consistently performs well in various categories like speed, streaming, and security. Learn more at ExpressVPN.
- Is there a reliable budget-friendly VPN option?
Surfshark is known for offering an affordable yet reliable VPN service. With low subscription fees and unlimited device connections, it provides excellent value for your money. Visit Surfshark for more details.
- Which VPN has the most extensive server network?
NordVPN is a popular choice when it comes to a vast server network, as it has over 5,000 servers in more than 60 countries. This extensive coverage allows for stable connections and better performance. Find out more at NordVPN.
- Are there any VPNs particularly suitable for streaming?
CyberGhost is a popular option for streaming, as it can unblock several streaming services such as Netflix, Hulu, and BBC iPlayer, and it has a user-friendly interface with dedicated streaming profiles. Discover more at CyberGhost.
- What is a crucial consideration when selecting a VPN?
One of the essential factors to consider when choosing a VPN service is its commitment to privacy and security. Look for features like strong encryption, a strict no-logs policy, and a transparent privacy policy. It’s also essential to evaluate the VPN’s performance, compatibility with different devices, and customer support.
Conclusion
Choosing the best VPN can be a daunting task, but it’s important to take the time to evaluate your options and find the right fit for your needs. Here are some key takeaways to keep in mind:
- Consider your primary concerns, such as privacy, security, or accessing geo-restricted content.
- Look for a VPN with strong encryption and a reliable server network.
- Consider the cost and any additional features, such as a kill switch or split tunneling.
- Read reviews and do your research to ensure the VPN you choose has a good reputation and a track record of protecting user privacy.
Remember that no VPN is perfect, and there may be trade-offs depending on your specific needs. However, by taking the time to evaluate your options and choose a reputable provider, you can enjoy greater privacy and security online.
Ultimately, the best VPN for you will depend on your individual needs and priorities. By considering the factors outlined in this guide, you can make an informed decision and find a VPN that meets your needs and budget.
The post Secure Your Online Privacy: How to Choose the Best VPN in 2023 appeared first on Cybersecurity Insiders.
 . Their services enable security, intelligence, and trust & safety teams to leverage a world-class intelligence capability tailored to their needs. They fuse robust data collection with a deep understanding of the adversarial mindset delivering smarter defense and more effective response against advanced cyber attacks, physical threats to personnel or facilities, disinformation and reputational attacks, and the abuse and fraud of digital platforms.
. Their services enable security, intelligence, and trust & safety teams to leverage a world-class intelligence capability tailored to their needs. They fuse robust data collection with a deep understanding of the adversarial mindset delivering smarter defense and more effective response against advanced cyber attacks, physical threats to personnel or facilities, disinformation and reputational attacks, and the abuse and fraud of digital platforms. Key drivers why organizations increasingly rely on managed security service providers
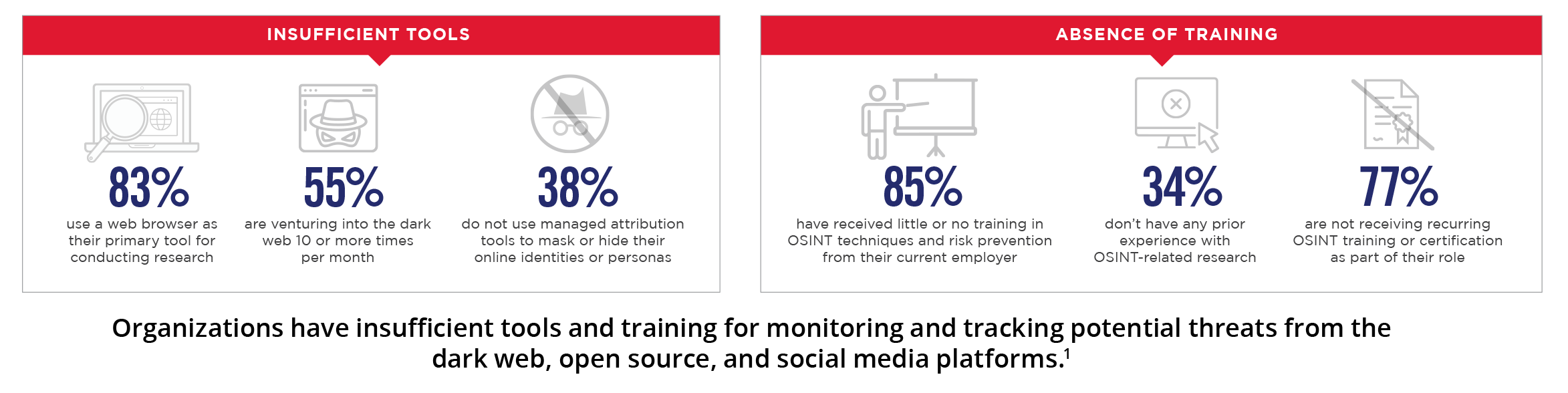
Key drivers why organizations increasingly rely on managed security service providers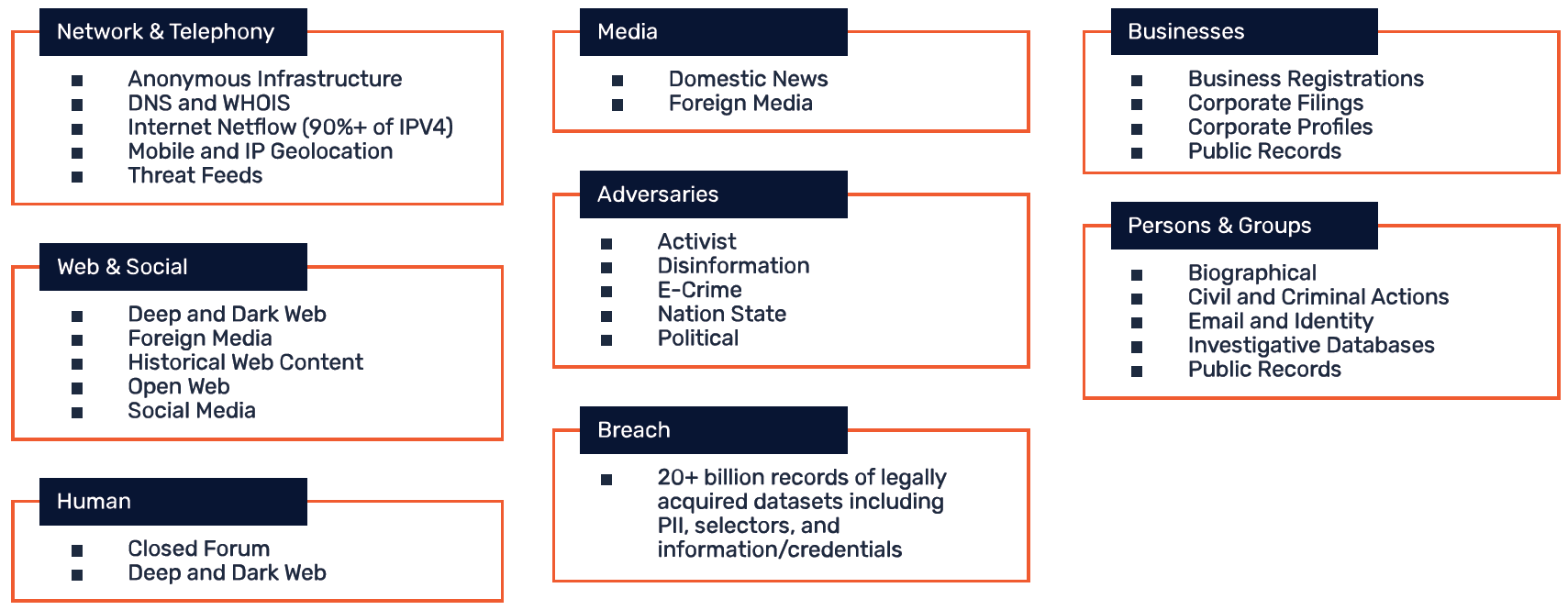 Nisos Collection & Analysis Stack Spans All Critical Data Sources
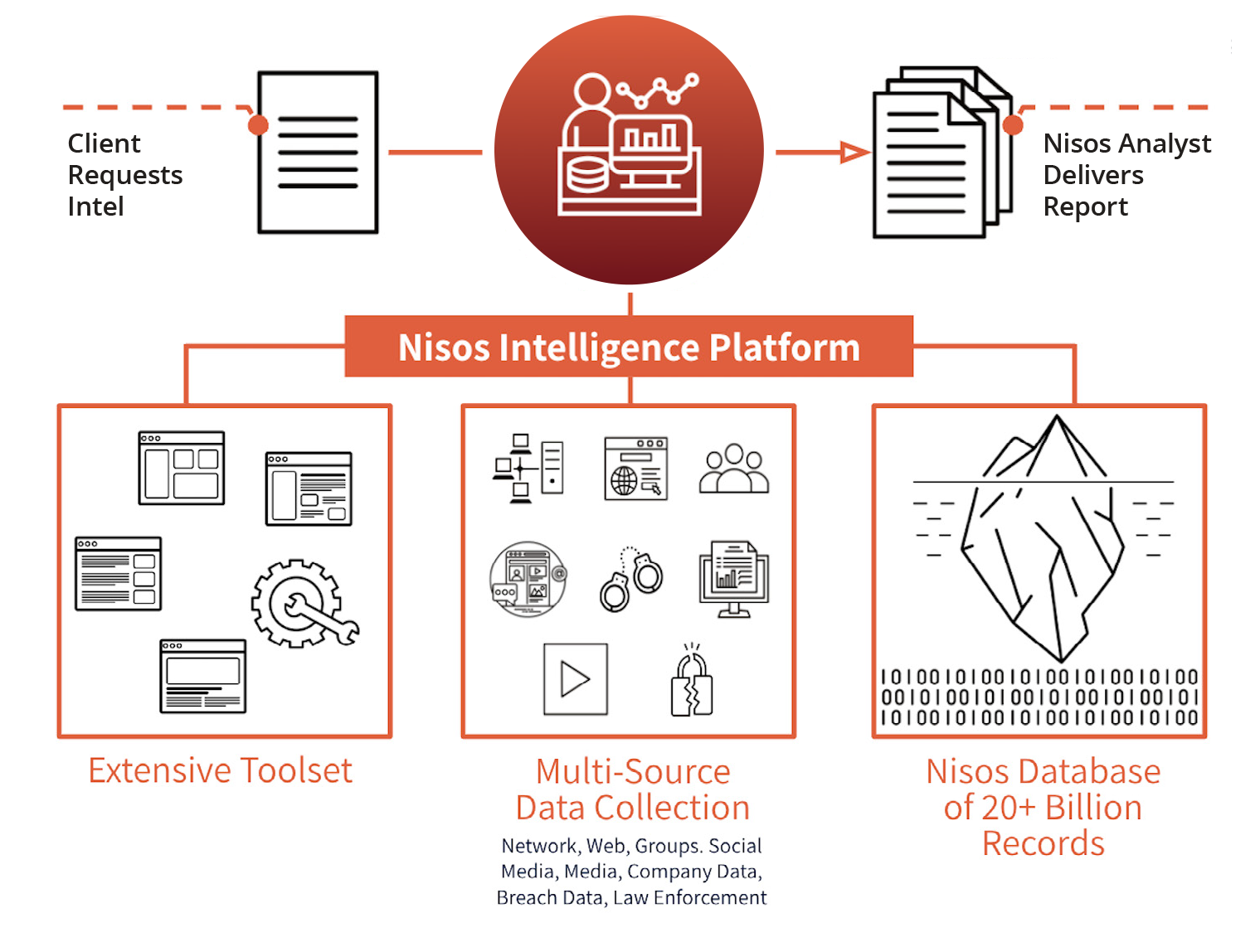
Nisos Collection & Analysis Stack Spans All Critical Data Sources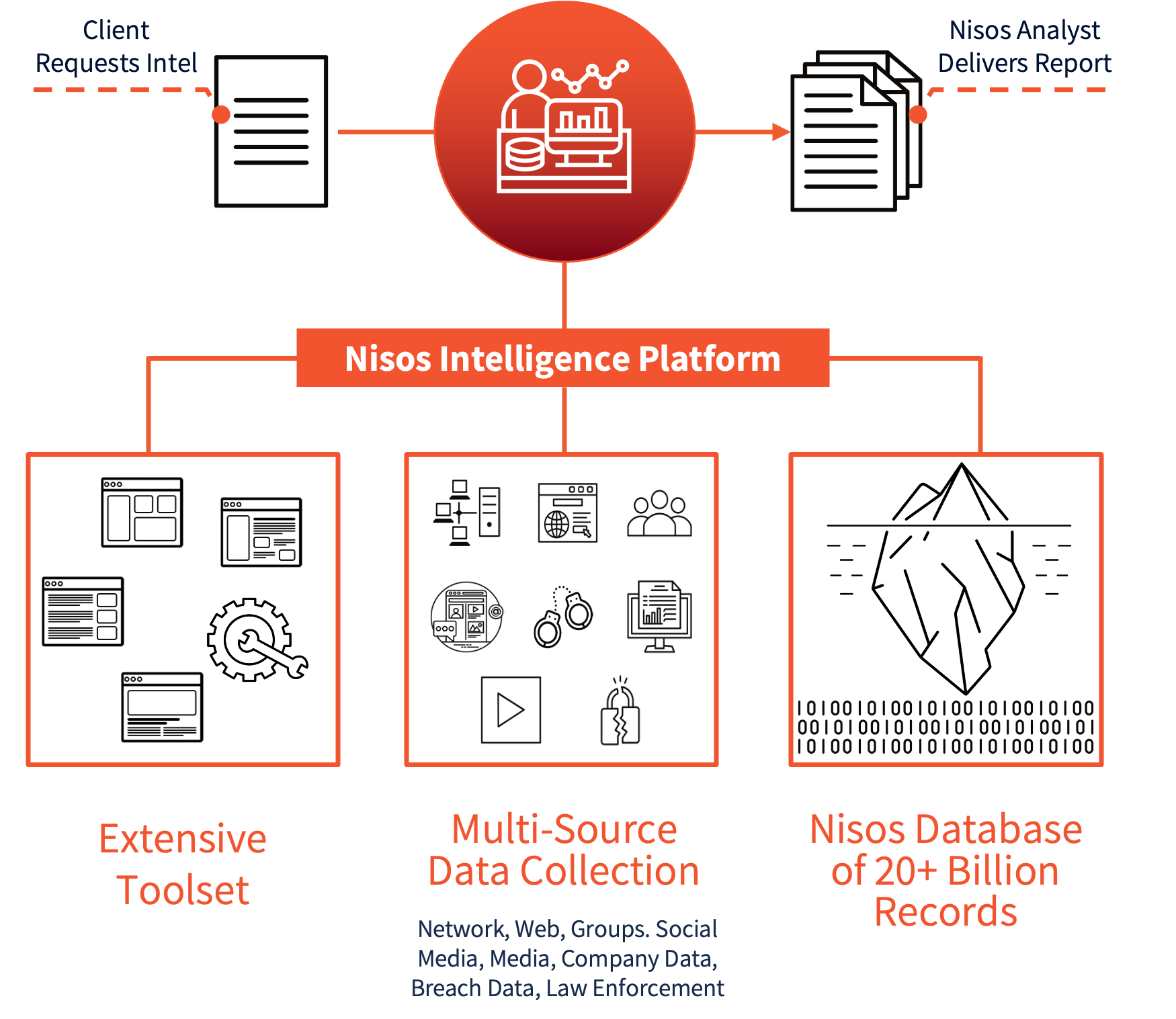 NISOS Analyst-Led Workflow Enables Deep Visibility and Rapid Response
NISOS Analyst-Led Workflow Enables Deep Visibility and Rapid Response . The services enable security, intelligence,
. The services enable security, intelligence,