Category: ransomware
Ransomware, a malicious form of software that encrypts or locks digital files and demands a ransom from victims in exchange for decryption, has evolved into a major cybersecurity threat. In this article, we will embark on a journey through the history of ransomware, from its early beginnings to the complex and dangerous forms we face today.
The Dawn of Ransomware
The concept of ransomware can be traced back to the late 1980s and early 1990s. The first documented instance of ransomware was the AIDS Trojan, which targeted AIDS researchers. It was distributed via floppy disks and, once activated, encrypted the victim’s files and demanded a ransom for decryption. The ransom was usually sent via regular mail, and in many cases, victims received their decryption keys after payment.
The Evolution of Ransomware
As the internet became more prevalent in the late 1990s and early 2000s, ransomware evolved. The use of encryption algorithms improved, making it more difficult for victims to recover their files without paying. GPCoder, the first example of a ransomware encrypting files, emerged in 2005.
CryptoLocker and the Bitcoin Connection
One of the most significant milestones in ransomware history was the emergence of Crypto Locker in 2013. It marked the shift from relatively simple ransomware to a more sophisticated, encryption-based model. Crypto Locker also introduced the use of Bitcoin for ransom payments, making it more challenging for law enforcement to trace the money.
The Rise of Ransomware-as-a-Service (RaaS)
Ransomware-as-a-Service (RaaS) started to gain traction around 2015. This allowed individuals with minimal technical skills to launch ransomware attacks using pre-designed malware and payment infrastructure, sharing profits with the malware creators. Popular RaaS strains included Tox, Fakben, and Satan.
Notable Ransomware Attacks
Over the years, several high-profile ransomware attacks have garnered significant attention:
1. WannaCry (2017): A global ransomware attack that exploited a Microsoft Windows vulnerability, affecting over 200,000 computers in 150 countries.
2. NotPetya (2017): Initially disguised as ransomware, NotPetya turned out to be a wiper that aimed to cause destruction rather than financial gain. It severely impacted Ukrainian infrastructure.
3. Ryuk (2018): Known for its precise targeting and high ransom demands, Ryuk has targeted major organizations and critical infrastructure worldwide.
4. Maze (2019): Maze operators introduced the “double extortion” tactic, stealing data be-fore encrypting it and threatening to leak it if the ransom was not paid.
Modern Ransomware Threats
Today, ransomware has grown into a sophisticated and lucrative criminal enterprise. Groups like REvil, DarkSide, and Conti have extorted millions of dollars from victims. Modern ransomware often includes advanced features like encryption, data theft, and exfiltration, and perpetrators frequently target critical infrastructure and large corporations.
Conclusion
Ransomware’s evolution from simple, early attacks to the complex, destructive threats of today reflects the ever-changing landscape of cybersecurity. To protect against this growing menace, individuals and organizations must invest in robust cybersecurity measures, regularly backup data, and stay informed about the latest ransomware threats and prevention strategies. As ransomware continues to adapt and evolve, our defenses must evolve with it.
The post A Deep Dive into Ransomware History: From Its Origins to Modern Threats appeared first on Cybersecurity Insiders.
The Navy Exchange Service‘s sale of Lenovo laptops at steep discounts and duty-free rates has raised concerns among U.S. lawmakers due to the manufacturer’s ties to the People’s Republic of China. There are apprehensions that these laptops could potentially contain pre-installed malware aimed at spying on users in Western countries. While currently, this is only an alert generating media attention, it has the potential to gain momentum rapidly, as any connection to China and data security tends to trend on Google within days.
Microsoft recently conducted a study that led to the conclusion that the trend of BYOD (Bring Your Own Device) should be renamed “bring your own disaster.” The study found that a significant percentage of these devices were responsible for causing issues within corporate computer networks. Microsoft’s research revealed that 80-90% of ransomware attacks in the past year originated from unmanaged devices. These findings were detailed in Microsoft’s Digital Defense Report for 2023, and it anticipates a global increase of such attacks by 200%.
According to a threat report released by SecureWorks, ransomware groups have become more efficient in deploying file-encrypting malware within just 24 hours of hacking their targets. This marks a significant reduction from the previously estimated period of 6-7 days, and it’s attributed to the increased sophistication of malware developed by cybercriminals.
BlackBaud, a South Carolina-based cloud computing company, has agreed to pay $49.6 million to approximately 13,000 customers across 49 states and the District of Columbia to settle litigation stemming from a 2020 ransomware attack. During this breach, hackers managed to access customer data, including social security numbers and bank account information. Notably, this settlement includes a $3 million payment to the Security Exchange Services (SEC) and $900,000 to Massachusetts.
In an alarming revelation, the United States Department of State has admitted to being unaware of the extent of its in-house cybersecurity risks. The federal agency attributes this lack of awareness to outdated hardware and software systems. It also raises concerns about Chinese vendors supplying equipment through cross-linked trade treaties with countries like Malaysia and Singapore. This means that Chinese products could enter the American market with different labels, linking them to companies in Singapore and Malaysia but ultimately part of China’s trade consortium.
According to a report by internet security company WatchGuard Technologies, there has been a decline in malware infections despite an increase in campaigns aimed at spreading malware. The report emphasizes that while malware distribution has decreased, the sophistication of attacks has risen to new heights.
The post Cybersecurity news headlines trending on Google appeared first on Cybersecurity Insiders.
McLaren Health Care has revealed that its servers fell victim to a ransomware gang called BlackCat, also known as ALPHV, during August and September of this year. The cybercriminals are now issuing threats to expose the pilfered data on the dark web unless their ransom demands are met.
As reported on X, formerly known as Twitter, the BlackCat gang managed to purloin approximately 6 terabytes of sensitive information related to approximately 2.5 million patients. To substantiate their claims, they’re threatening to release a portion of this data.
Sources who wished to remain anonymous divulged that the ransomware attack wreaked havoc on IT services across 14 Michigan hospitals during that period. Just when things appeared to be stabilizing, the threat actors initiated a campaign of blackmail, using the specter of data leaks as leverage.
An informant from ALPHV, active on the Telegram platform, disclosed that their team successfully infiltrated McLaren Health Care’s systems by exploiting a persistent vulnerability or backdoor that still exists.
In response to the breach, McLaren Health Care enlisted the services of cybersecurity experts. These professionals are collaborating with the healthcare network’s IT staff to minimize the risks associated with this dual-threat ransomware attack, which combines data encryption with extortion tactics.
It’s important to note that the criminal gang behind this attack predominantly communicates in Russian. However, there is no concrete evidence linking them to Russian intelligence agencies. Nevertheless, certain Western media outlets have speculated that the Russian government is training cyber operatives to carry out financially motivated cyberattacks. This shift in strategy is thought to be a response to the economic strains imposed by U.S. sanctions, stemming from Vladimir Putin’s actions in Ukraine.
The post McLaren Health Care data breached by BlackCat Ransomware Gang appeared first on Cybersecurity Insiders.
In August of this year, the Federal Bureau of Investigation (FBI) issued a warning regarding a concerning trend affecting numerous companies across North America since July 2023. This emerging threat, known as “Dual Ransomware” attacks, entails digital assaults targeting the same victim within a time-frame spanning from 48 hours to 7 days.
To put it plainly, a dual ransomware attack occurs when a company falls victim to a file-encrypting attack, regardless of whether it involves double extortion. The consequences are consistent: financial losses, the illicit extraction of sensitive information, and the complete lockdown of data access.
While concrete evidence pinpointing the exact motivations behind these attacks remains elusive, security analysts suggest that various factors may be contributing to their prevalence. These factors include inadequate technical support within targeted organizations to rectify vulnerabilities susceptible to dual ransomware, mis-configurations in applications or cloud environments, and the absence of a pre-established business continuity plan to address such situations, among other potential catalysts.
According to a survey conducted by a dark web-affiliated hacking group, nearly 19 companies have fallen victim to these attacks since July 2023. Notably, two of these targeted entities were Fortune 500 companies, boasting annual revenues in the millions.
Interestingly, none of these attacks have been officially documented; they only came to light when company representatives sought assistance from freelance forensic experts to negotiate with the hackers.
The culprits behind these sophisticated digital assaults remain shrouded in mystery. However, the FBI’s private industry notification has raised concerns about the involvement of various Ransomware-as-a-Service (RaaS) groups, such as Royal, Quantum, 3AM Ransomware, LockBit, Karakurt, Hive, Diamond, and Avoslocker, either directly orchestrating these attacks or having connections to the encryption code employed on the compromised computer networks.
In a noteworthy revelation, Emsisoft researchers have traced the origins of dual encryption as a criminal tactic introduced in 2020-21, coinciding with the widespread lockdowns and the surge in remote work culture during the COVID-19 pandemic.
The primary defense against such attacks lies in implementing robust identity and access management measures. These include enforcing strong passwords, deploying multi-factor authentication (MFA) systems that are resistant to phishing attempts, and implementing time-based access controls for accounts holding administrative privileges. Additionally, conventional security practices such as keeping operating systems up to date, regularly updating antivirus solutions, securing network protocols, patching firmware vulnerabilities, disabling unused ports, and monitoring the activities on Bring Your Own Device (BYOD) devices continue to be essential safeguards against these evolving cyber threats.
The post Dual Ransomware Attacks are different and explained appeared first on Cybersecurity Insiders.
Earlier this week, KrebsOnSecurity revealed that the darknet website for the Snatch ransomware group was leaking data about its users and the crime gang’s internal operations. Today, we’ll take a closer look at the history of Snatch, its alleged founder, and their claims that everyone has confused them with a different, older ransomware group by the same name.

According to a September 20, 2023 joint advisory from the FBI and the U.S. Cybersecurity and Infrastructure Security Administration (CISA), Snatch was originally named Team Truniger, based on the nickname of the group’s founder and organizer — Truniger.
The FBI/CISA report says Truniger previously operated as an affiliate of GandCrab, an early ransomware-as-a-service offering that closed up shop after several years and claims to have extorted more than $2 billion from victims. GandCrab dissolved in July 2019, and is thought to have become “REvil,” one of the most ruthless and rapacious Russian ransomware groups of all time.
The government says Snatch used a customized ransomware variant notable for rebooting Microsoft Windows devices into Safe Mode — enabling the ransomware to circumvent detection by antivirus or endpoint protection — and then encrypting files when few services are running.
“Snatch threat actors have been observed purchasing previously stolen data from other ransomware variants in an attempt to further exploit victims into paying a ransom to avoid having their data released on Snatch’s extortion blog,” the FBI/CISA alert reads. It continues:
“Prior to deploying the ransomware, Snatch threat actors were observed spending up to three months on a victim’s system. Within this timeframe, Snatch threat actors exploited the victim’s network moving laterally across the victim’s network with RDP for the largest possible deployment of ransomware and searching for files and folders for data exfiltration followed by file encryption.”
New York City-based cyber intelligence firm Flashpoint said the Snatch ransomware group was created in 2018, based on Truniger’s recruitment both on Russian language cybercrime forums and public Russian programming boards. Flashpoint said Truniger recruited “pen testers” for a new, then-unnamed cybercrime group, by posting their private Jabber instant messenger contact details on multiple Russian language coding forums, as well as on Facebook.
“The command requires Windows system administrators,” Truniger’s ads explained. “Experience in backup, increase privileges, mikicatz, network. Details after contacting on jabber: truniger@xmpp[.]jp.”
In at least some of those recruitment ads — like one in 2018 on the forum sysadmins[.]ru –the username promoting Truniger’s contact information was Semen7907. In April 2020, Truniger was banned from two of the top Russian cybercrime forums, where members from both forums confirmed that Semen7907 was one of Truniger’s known aliases.
[SIDE NOTE: Truniger was banned because he purchased credentials to a company from a network access broker on the dark web, and although he promised to share a certain percentage of whatever ransom amount Truniger’s group extracted from the victim, Truniger paid the access broker just a few hundred dollars off of a six-figure ransom].
According to Constella Intelligence, a data breach and threat actor research platform, a user named Semen7907 registered in 2017 on the Russian-language programming forum pawno[.]ru using the email address tretyakov-files@yandex.ru.
That same email address was assigned to the user “Semen-7907” on the now defunct gaming website tunngle.net, which suffered a data breach in 2020. Semen-7907 registered at Tunngle from the Internet address 31.192.175[.]63, which is in Yekaterinburg, RU.
Constella reports that tretyakov-files@yandex.ru was also used to register an account at the online game stalker[.]so with the nickname Trojan7907.
There is a Skype user by the handle semen7907, and which has the name Semyon Tretyakov from Yekaterinburg, RU. Constella also found a breached record from the Russian mobile telephony site tele2[.]ru, which shows that a user from Yekaterinburg registered in 2019 with the name Semyon Sergeyvich Tretyakov and email address tretyakov-files@ya.ru.
The above accounts, as well as the email address semen_7907@mail.ru, were all registered or accessed from the same Yekaterinburg Internet address mentioned previously: 31.192.175.63. The Russian mobile phone number associated with that tele2[.]ru account is connected to the Telegram account “Perchatka,” (“glove” in Russian).
BAD BEATS
Reached via Telegram, Perchatka (a.k.a. Mr. Tretyakov) said he was not a cybercriminal, and that he currently has a full-time job working in IT at a major company (he declined to specify which).
Presented with the information gathered for this report (and more that is not published here), Mr. Tretyakov acknowledged that Semen7907 was his account on sysadmins[.]ru, the very same account Truniger used to recruit hackers for the Snatch Ransomware group back in 2018.
However, he claims that he never made those posts, and that someone else must have assumed control over his sysadmins[.]ru account and posted as him. Mr. Tretyakov said that KrebsOnSecurity’s outreach this week was the first time he became aware that his sysadmins[.]ru account was used without his permission.
Mr. Tretyakov suggested someone may have framed him, pointing to an August 2023 story at a Russian news outlet about the reported hack and leak of the user database from sysadmins[.]ru, allegedly at the hands of a pro-Ukrainian hacker group called CyberSec.
“Recently, because of the war in Ukraine, a huge number of databases have been leaked and finding information about a person is not difficult,” Tretyakov said. “I’ve been using this login since about 2013 on all the forums where I register, and I don’t always set a strong password. If I had done something illegal, I would have hidden much better :D.”
[For the record, KrebsOnSecurity does not generally find this to be the case, as the ongoing Breadcrumbs series will attest.]
A Semyon Sergeyvich Tretyakov is listed as the composer of a Russian-language rap song called “Parallels,” which seems to be about the pursuit of a high-risk lifestyle online. A snippet of the song goes:
“Someone is on the screen, someone is on the blacklist
I turn on the timer and calculate the risks
I don’t want to stay broke And in the pursuit of money
I can’t take these zeros Life is like a zebra –
everyone wants to be first Either the stripes are white,
or we’re moving through the wilds I won’t waste time.”
Mr. Tretyakov said he was not the author of that particular rhyme, but that he has been known to record his own rhythms.
“Sometimes I make bad beats,” he said. “Soundcloud.”
NEVER MIND THE DOMAIN NAME
The FBI/CISA alert on Snatch Ransomware (PDF) includes an interesting caveat: It says Snatch actually deploys ransomware on victim systems, but it also acknowledges that the current occupants of Snatch’s dark and clear web domains call themselves Snatch Team, and maintain that they are not the same people as Snatch Ransomware from 2018.
Here’s the interesting bit from the FBI/CISA report:
“Since November 2021, an extortion site operating under the name Snatch served as a clearinghouse for data exfiltrated or stolen from victim companies on Clearnet and TOR hosted by a bulletproof hosting service. In August 2023, individuals claiming to be associated with the blog gave a media interview claiming the blog was not associated with Snatch ransomware and “none of our targets has been attacked by Ransomware Snatch…”, despite multiple confirmed Snatch victims’ data appearing on the blog alongside victims associated with other ransomware groups, notably Nokoyawa and Conti.”
Avid readers will recall a story here earlier this week about Snatch Team’s leaky darknet website based in Yekaterinburg, RU that exposed their internal operations and Internet addresses of their visitors. The leaked data suggest that Snatch is one of several ransomware groups using paid ads on Google.com to trick people into installing malware disguised as popular free software, such as Microsoft Teams, Adobe Reader, Mozilla Thunderbird, and Discord.
Snatch Team claims to deal only in stolen data — not in deploying ransomware malware to hold systems hostage.
Representatives of the Snatch Team recently answered questions from Databreaches.net about the claimed discrepancy in the FBI/CISA report.
“First of all, we repeat once again that we have nothing to do with Snatch Ransomware, we are Security Notification Attachment, and we have never violated the terms of the concluded transactions, because our honesty and openness is the guarantee of our income,” the Snatch Team wrote to Databreaches.net in response to questions.
But so far the Snatch Team has not been able to explain why it is using the very same domain names that the Snatch ransomware group used?
Their claim is even more unbelievable because the Snatch Team members told Databreaches.net they didn’t even know that a ransomware group with that name already existed when they initially formed just two years ago.
This is difficult to swallow because even if they were a separate group, they’d still need to somehow coordinate the transfer of the Ransomware group’s domains on the clear and dark webs. If they were hoping for a fresh start or separation, why not just pick a new name and new web destination?
“Snatchteam[.]cc is essentially a data market,” they continued. “The only thing to underline is that we are against selling leaked information, sticking to the idea of free access. Absolutely any team can come to us and offer information for publication. Even more, we have heard rumors that a number of ransomware teams scare their clients that they will post leaked information on our resource. We do not have our own ransomware, but we are open to cooperation on placement and monetization of dates (sic).”
Maybe Snatch Team does not wish to be associated with Snatch Ransomware because they currently believe stealing data and then extorting victim companies for money is somehow less evil than infecting all of the victim’s servers and backups with ransomware.
It is also likely that Snatch Team is well aware of how poorly some of their founders covered their tracks online, and are hoping for a do-over on that front.
VMware has recently made headlines on Google News due to ransomware attacks targeting the company. This development has left its customers feeling uneasy and prompted them to search for alternative products that are more secure.
The increasing licensing costs have only intensified the quest for alternative virtualization software. Customers are now grappling with the perception that the expenses associated with VMware outweigh the benefits. In fact, a staggering 77% of respondents have expressed reservations about entering into future agreements with the software giant.
VergeIO, a company that has dedicated resources to investigating the impact of rising costs associated with VMware software, has revealed in its report that renewal quotes and licensing agreements based on a “Per-Core” model are expected to decline in the coming year. The growing expenditure on this software is causing additional strain on annual IT budgets.
Remarkably, the quality of customer support provided by VMware has also come under scrutiny, with 66% of users expressing dissatisfaction with the current technical support. They feel that the service levels offered by customer support leave much to be desired.
Furthermore, a significant 70% of survey participants admitted that the rising costs were anticipated, especially after VMware officially announced its acquisition by Broadcom in April 2022.
Now, the burning question is whether VMware customers can swiftly find a suitable replacement.
Unfortunately, it’s not that simple. The Palo Alto-based company offers computer software compatible with MS Windows, Linux, and MacOS that is renowned for its excellence and compatibility with in-house hardware. This reputation persists even after VMware garnered attention for the Log4shell vulnerability, which was exploited by the Lazarus hacking group early this year.
The post VMware customers anxious about ransomware threats appeared first on Cybersecurity Insiders.
The Dark Angels ransomware gang, active since May 2022, has reportedly set its sights on VMware ESXi servers within the premises of Johnson Controls International (JCI). The cyberattack initially targeted JCI’s Asian offices and subsequently spread to several subsidiary brands, including York, Tyco, Luxaire, Coleman, Ruskin, Grinnel, and Simplex.
Johnson Controls, a renowned manufacturer of industrial equipment such as fire safety and security systems, has launched an investigation into the extent of the attack’s impact on its network. The company has assured stakeholders that it will provide more comprehensive details early next week.
As a result of the disruption, a portion of JCI’s systems is currently offline, and the company is actively exploring strategies to mitigate associated risks. Frustrated customers of York have taken to Twitter to express their discontent, as they are unable to access the status of their booked HVAC equipment and processing systems.
Notably, the Dark Angels ransomware group is infamous for demanding a minimum ransom of $51 million and is recognized for offering a VMware ESXi encryptor, sourced from the Babuk and Ragnar ransomware variants.
In the case of Johnson Controls, Dark Angels reportedly exfiltrated approximately 27 terabytes of corporate data, setting the stage for a double extortion attack in the future. The company acknowledged this breach in its Form 8-K filing with the SEC and disclosed its collaboration with its cyber insurance provider and experts to address the situation.
The course of action Johnson Controls will ultimately take in response to the hackers’ demands remains uncertain. However, the company’s website warns that certain customer-accessed applications may experience downtime, and those affected will receive formal notifications.
The post Johnson Controls hit by Dark Angels Ransomware appeared first on Cybersecurity Insiders.
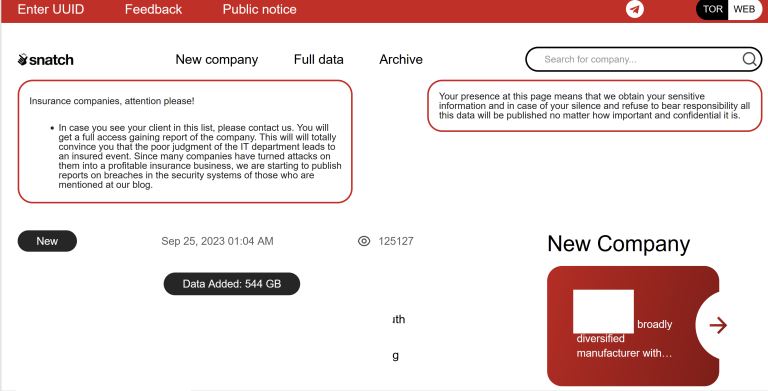
The victim shaming site operated by the Snatch ransomware group is leaking data about its true online location and internal operations, as well as the Internet addresses of its visitors, KrebsOnSecurity has found. The leaked data suggest that Snatch is one of several ransomware groups using paid ads on Google.com to trick people into installing malware disguised as popular free software, such as Microsoft Teams, Adobe Reader, Mozilla Thunderbird, and Discord.
First spotted in 2018, the Snatch ransomware group has published data stolen from hundreds of organizations that refused to pay a ransom demand. Snatch publishes its stolen data at a website on the open Internet, and that content is mirrored on the Snatch team’s darknet site, which is only reachable using the global anonymity network Tor.
KrebsOnSecurity has learned that Snatch’s darknet site exposes its “server status” page, which includes information about the true Internet addresses of users accessing the website.
Refreshing this page every few seconds shows that the Snatch darknet site generates a decent amount of traffic, often attracting thousands of visitors each day. But by far the most frequent repeat visitors are coming from Internet addresses in Russia that either currently host Snatch’s clear web domain names or recently did.
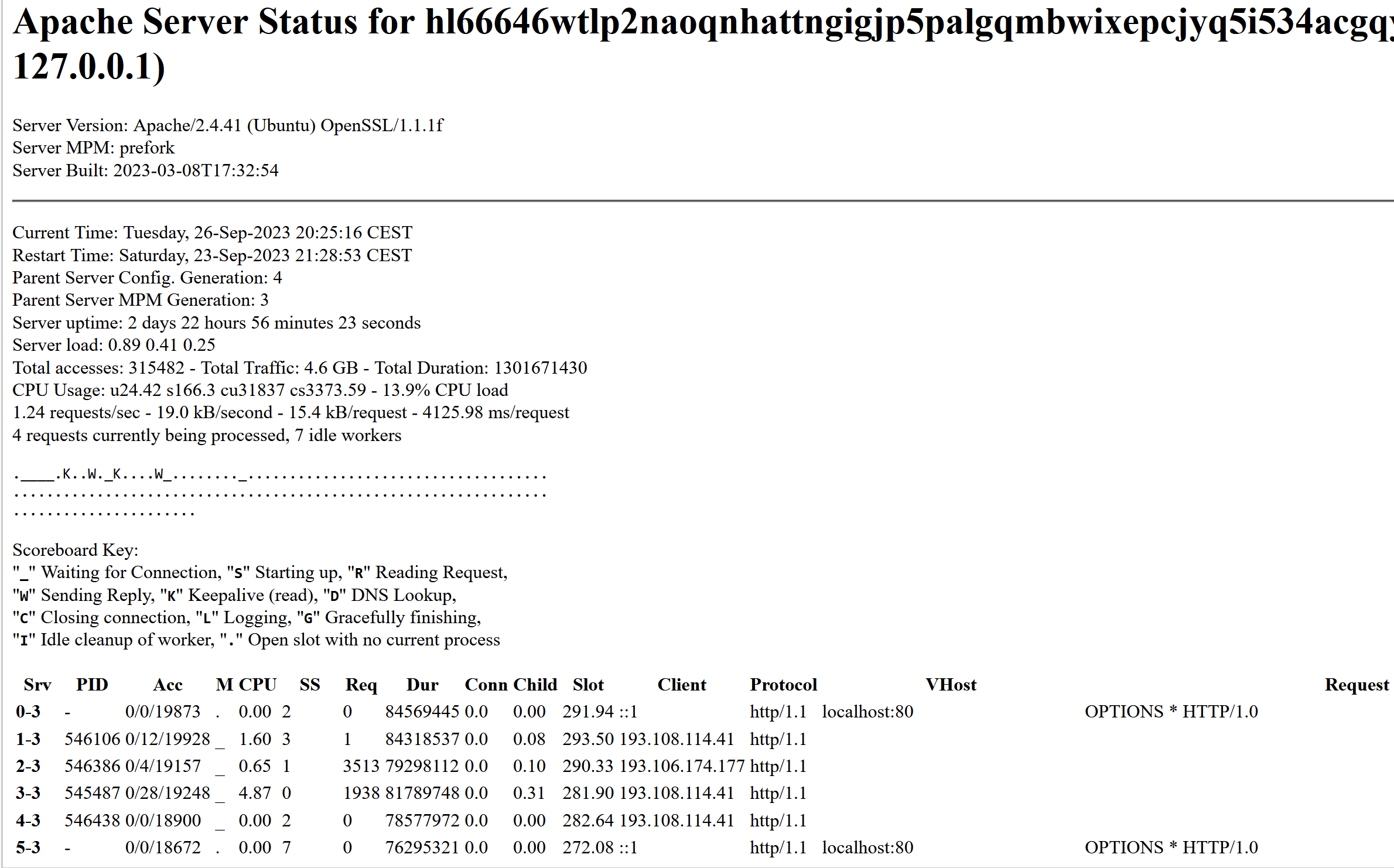
The Snatch ransomware gang’s victim shaming site on the darknet is leaking data about its visitors. This “server status” page says that Snatch’s website is on Central European Summer Time (CEST) and is powered by OpenSSL/1.1.1f, which is no longer supported by security updates.
Probably the most active Internet address accessing Snatch’s darknet site is 193.108.114[.]41, which is a server in Yekaterinburg, Russia that hosts several Snatch domains, including snatchteam[.]top, sntech2ch[.]top, dwhyj2[.]top and sn76930193ch[.]top. It could well be that this Internet address is showing up frequently because Snatch’s clear-web site features a toggle button at the top that lets visitors switch over to accessing the site via Tor.
Another Internet address that showed up frequently in the Snatch server status page was 194.168.175[.]226, currently assigned to Matrix Telekom in Russia. According to DomainTools.com, this address also hosts or else recently hosted the usual coterie of Snatch domains, as well as quite a few domains phishing known brands such as Amazon and Cashapp.
The Moscow Internet address 80.66.64[.]15 accessed the Snatch darknet site all day long, and that address also housed the appropriate Snatch clear-web domains. More interestingly, that address is home to multiple recent domains that appear confusingly similar to known software companies, including libreoff1ce[.]com and www-discord[.]com.
This is interesting because the phishing domains associated with the Snatch ransomware gang were all registered to the same Russian name — Mihail Kolesnikov, a name that is somewhat synonymous with recent phishing domains tied to malicious Google ads.
Kolesnikov could be a nod to a Russian general made famous during Boris Yeltsin’s reign. Either way, it’s clearly a pseudonym, but there are some other commonalities among these domains that may provide insight into how Snatch and other ransomware groups are sourcing their victims.
DomainTools says there are more than 1,300 current and former domain names registered to Mihail Kolesnikov between 2013 and July 2023. About half of the domains appear to be older websites advertising female escort services in major cities around the United States (e.g. the now-defunct pittsburghcitygirls[.]com).
The other half of the Kolesnikov websites are far more recent phishing domains mostly ending in “.top” and “.app” that appear designed to mimic the domains of major software companies, including www-citrix[.]top, www-microsofteams[.]top, www-fortinet[.]top, ibreoffice[.]top, www-docker[.]top, www-basecamp[.]top, ccleaner-cdn[.]top, adobeusa[.]top, and www.real-vnc[.]top.
In August 2023, researchers with Trustwave Spiderlabs said they encountered domains registered to Mihail Kolesnikov being used to disseminate the Rilide information stealer trojan.
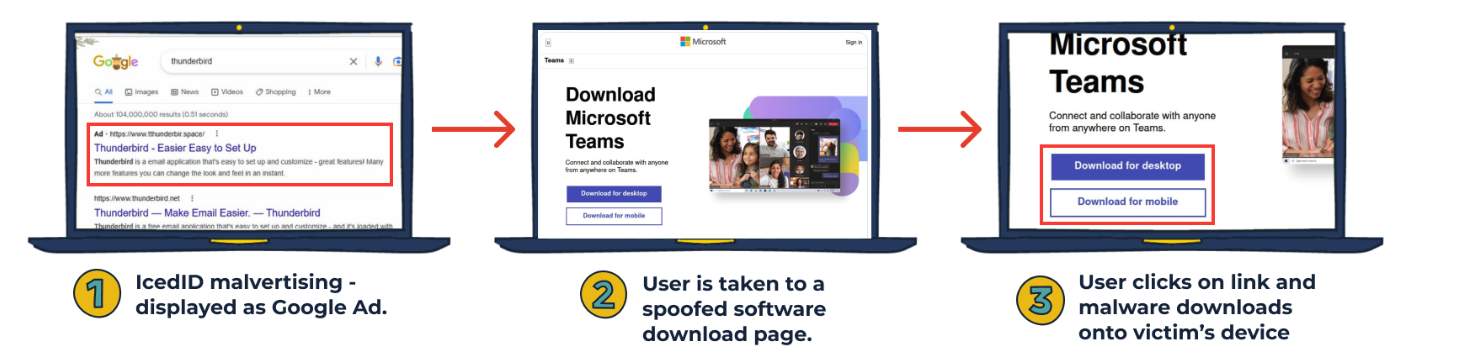
But it appears multiple crime groups may be using these domains to phish people and disseminate all kinds of information-stealing malware. In February 2023, Spamhaus warned of a huge surge in malicious ads that were hijacking search results in Google.com, and being used to distribute at least five different families of information stealing trojans, including AuroraStealer, IcedID/Bokbot, Meta Stealer, RedLine Stealer and Vidar.
For example, Spamhaus said victims of these malicious ads would search for Microsoft Teams in Google.com, and the search engine would often return a paid ad spoofing Microsoft or Microsoft Teams as the first result — above all other results. The malicious ad would include a logo for Microsoft and at first glance appear to be a safe and trusted place to download the Microsoft Teams client.
However, anyone who clicked on the result was whisked away instead to mlcrosofteams-us[.]top — yet another malicious domain registered to Mr. Kolesnikov. And while visitors to this website may believe they are only downloading the Microsoft Teams client, the installer file includes a copy of the IcedID malware, which is really good at stealing passwords and authentication tokens from the victim’s web browser.
The founder of the Swiss anti-abuse website abuse.ch told Spamhaus it is likely that some cybercriminals have started to sell “malvertising as a service” on the dark web, and that there is a great deal of demand for this service.
In other words, someone appears to have built a very profitable business churning out and promoting new software-themed phishing domains and selling that as a service to other cybercriminals. Or perhaps they are simply selling any stolen data (and any corporate access) to active and hungry ransomware group affiliates.
The tip about the exposed “server status” page on the Snatch darkweb site came from @htmalgae, the same security researcher who alerted KrebsOnSecurity earlier this month that the darknet victim shaming site run by the 8Base ransomware gang was inadvertently left in development mode.
That oversight revealed not only the true Internet address of the hidden 8Base site (in Russia, naturally), but also the identity of a programmer in Moldova who apparently helped to develop the 8Base code.
@htmalgae said the idea of a ransomware group’s victim shaming site leaking data that they did not intend to expose is deliciously ironic.
“This is a criminal group that shames others for not protecting user data,” @htmalgae said. “And here they are leaking their user data.”
All of the malware mentioned in this story is designed to run on Microsoft Windows devices. But Malwarebytes recently covered the emergence of a Mac-based information stealer trojan called AtomicStealer that was being advertised through malicious Google ads and domains that were confusingly similar to software brands.
Please be extra careful when you are searching online for popular software titles. Cracked, pirated copies of major software titles are a frequent source of infostealer infections, as are these rogue ads masquerading as search results. Make sure to double-check you are actually at the domain you believe you’re visiting *before* you download and install anything.
Stay tuned for Part II of this post, which includes a closer look at the Snatch ransomware group and their founder.
Further reading:
@HTMalgae’s list of the top Internet addresses seen accessing Snatch’s darknet site
Ars Technica: Until Further Notice Think Twice Before Using Google to Download Software
Bleeping Computer: Hackers Abuse Google Ads to Spread Malware in Legit Software