Category: ransomware
AirAsia, one of the noted airliners of Malaysia, has apparently been hit by a cyber attack of ransomware variant and Daixin Team Group is claiming to have accessed over 5 million records of customers and staff and has allegedly released two spreadsheets proving its claims as true.
The Kuala Lumpur based airlines that offer flight services to over 165 destinations- all with the help of 22,000 employees worldwide is taking all measures to contain the repercussions arising from the attack.
Daixin Team is threatening to sell more of the stolen data, if in case the victimized company doesn’t pay the demanded ransom.
Discerningly, the information that was shared last week includes DoBs, country of birth, where the person belongs to, the secret question that secures their account and the issue seems to be critical.
AirAsia is doing its best to remove the encryption and has hired forensic experts to deal with the situation.
NOTE 1- In March this year, the largest low-cost carrier announced its partnership with Hacken, a Cybersecurity consultation offering company to enhance the online experience of its passengers and shielding them from data breaches and malware attacks that could leak information such as passport data, credit card numbers and contact details of customers.
NOTE 2- A ransomware is a kind of malware where information is stolen from the targeted database and is locked with encryption until a ransom in cryptocurrency, ranging in millions, is paid.
NOTE 3- A detailed report on Daixin will be released shortly!
The post AirAsia Ransomware Attack by Daixin appeared first on Cybersecurity Insiders.
Brian Krebs writes about how the Zeppelin ransomware encryption scheme was broken:
The researchers said their break came when they understood that while Zeppelin used three different types of encryption keys to encrypt files, they could undo the whole scheme by factoring or computing just one of them: An ephemeral RSA-512 public key that is randomly generated on each machine it infects.
“If we can recover the RSA-512 Public Key from the registry, we can crack it and get the 256-bit AES Key that encrypts the files!” they wrote. “The challenge was that they delete the [public key] once the files are fully encrypted. Memory analysis gave us about a 5-minute window after files were encrypted to retrieve this public key.”
Unit 221B ultimately built a “Live CD” version of Linux that victims could run on infected systems to extract that RSA-512 key. From there, they would load the keys into a cluster of 800 CPUs donated by hosting giant Digital Ocean that would then start cracking them. The company also used that same donated infrastructure to help victims decrypt their data using the recovered keys.
A company offered recovery services based on this break, but was reluctant to advertise because it didn’t want Zeppelin’s creators to fix their encryption flaw.
Technical details.
Researchers at Cyber Security Works, Ivanti, and Cyware identify new vulnerabilities, blindspots in popular network scanners, and emerging Advanced Persistent Threat (APT) groups in a joint ransomware report.
By Aaron Sandeen, CEO and co-founder of Cyber Security Works
Since our last ransomware report earlier this year, both the severity and complexity of attacker tactics continue to grow as we head into the final quarter of 2022. The total number of ransomware vulnerabilities out there has climbed to 323. It is about a 450% increase since ransomware became a prevalent threat in 2019. That is a lot to be on the lookout for! However, not all ransomware vulnerabilities are the same. Our team has compiled research to help you navigate all the ransomware information out there.
Researchers across Cyber Security Works, Ivanti, and Cyware have compiled key figures on the latest data compiled during the second and third quarters of this year. In addition to new vulnerabilities, researchers found that popular network scanners routinely fail to identify known vulnerabilities, three new Advanced Persistent Threat (APT) groups have emerged, and the CISA Known Exploited Vulnerabilities (KEV) catalog does not list about half of the known vulnerabilities associated with ransomware.
While the findings may appear to be signs of a worsening cybersecurity landscape, it is not all doom and gloom. Of the 323 total ransomware vulnerabilities found in the wild, a MITRE ATT&CK kill chain exists for 57 of them. Documentation continues to grow as the industry comes together to collectively address the threat of ransomware. With the release of our report, we hope to share this knowledge to fight the ransomware menace.
New vulnerabilities, new threat actors
Our team of researchers found 13 new vulnerabilities associated with ransomware in Q2 and Q3, 10 of which possess a Common Vulnerability Scoring System (CVSS) v3.0 “critical” severity score. Although four vulnerabilities were just identified they have existed in the wild for a little over a year. This highlights the importance of continuous network monitoring.
Vulnerabilities CVE-2022-26352 (Zoho), CVE-2021-40539 (SonicWall), and CVE-2021-20023 (DotCMS) allow adversaries to infiltrate web applications and remotely execute malicious code. CVE-2022-26352 (Zoho) also serves a double purpose as an easy entry point for attackers and allows them to gain elevated privileges.
In addition to finding the latest vulnerabilities, we document the movements of APT groups each quarter to keep watch as they continually add ransomware capabilities to their arsenal. Over the past two quarters, we identified Andariel, Tropical Scorpius, and DEV-0530 utilizing ransomware against their victims.
-
Andariel – Also known as the Lazurus group, Andariel is suspected to have originated from North Korea. Its number of attacks has grown considerably. Deploying the Maui ransomware, Andariel has targeted crypto platforms, both private and public companies across North America, Europe, and Asia
-
Tropical Scorpius – With unknown origins, Tropical Scorpius has been documented to specifically target American organizations in government, manufacturing, healthcare, finance, and high tech. This group is known to favor the Cuba ransomware payload.
-
DEV-0530 – This group also has ties to North Korea and is suspected to collaborate with the Andariel group in coordinating attacks.
Blindspots in popular scanners
Network scanners are a relatively cheap and easy solution to monitor your organization’s assets with little active management. However, after testing scanners offered by Nessus, Nexpose, and Qualys, we found they can miss up to 18 ransomware vulnerabilities. To categorize the severity of each vulnerability, we used the CVSS V3 rating system. However, this poses a problem as it only applies to vulnerabilities discovered after 2015. Using proprietary Machine Learning frameworks, CSW was able to derive a severity score equivalent to CVSS V3 (or V2 where V3 was unavailable).
Of the 18 vulnerabilities, here is what we found:
-
Once deriving severity ratings, 11 out of 18 vulnerabilities ranked Critical or High but no scanner plugins are available to detect them across Nessus, Nexpose, and Qualys scanners
-
Interestingly, two vulnerabilities (CVE-2019-9081 and CVE-2015-2551) are still missing severity ratings as the National Vulnerability Database rejected them. CVE-2019-9081 is actively exploited by Satan and Mailto ransomware groups, and CVE-2015-2551 by multiple groups.
Ransomware vulnerabilities missing from CISA KEV catalog
CISA’s KEV catalog is the federal government’s continuous list of vulnerabilities that hackers are known to exploit. The list was created on November 03, 2021, and only started with 287 vulnerabilities. Today its collection has soared to 800+ and is only growing larger as it is updated monthly.
All public companies, government bodies, and federal agencies are mandated to prioritize and patch all vulnerabilities found in the KEV catalog. It is also a great introduction to vulnerability management strategies for private organizations. Although CISA has documented 199 vulnerabilities associated with ransomware, the catalog is currently missing 124 of them.
Earlier this October, CISA released a binding directive advising all government agencies to improve asset visibility and vulnerability detection — highlighting the necessity of vulnerability enumeration beyond the scope of the catalog. This requires routine scanning of an organization’s network perimeter to stay ahead of the latest threats.
Asset visibility and vulnerability detection is easier said than done. We recommend learning exactly how ransomware groups deploy and execute their attacks to know where to look and how to think like the adversary. To make this easier for network security teams, CSW’s research team employed the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) kill chain to map exactly how threat groups exploit vulnerabilities. We did each step of the way for 57 vulnerabilities. Via these vulnerabilities, threat groups can completely take control of a system from end to end, deploy any code, escalate privileges within the network, and steal data. To learn more about our process, read more about it here or reach out to us directly.
I hope you find this information as enlightening as it has been for me and the CSW team. Although a pervasive menace, ransomware can be fought and defeated by utilizing data, intelligence, expertise and a collaborative security community.
The post Ransomware threats grow as new vulnerabilities and threat actors are identified appeared first on Cybersecurity Insiders.
The first one is a report released by the FBI stating the earning details of Hive Ransomware Group. FBI issued a joint advisory along with CISA that the said hacking group extorted more than $100m in this financial year by infecting over 1300 victims in 15 months starting from June’21.Victims list include government organizations, communication sector companies, IT businesses and businesses involved in healthcare sector.
Second is the news related to Microsoft releasing a report on a newly discovered Royal Ransomware, first detected in Aug’22. Microsoft Security Threat Intelligence group said in its latest post that the group of criminals were using Google Ads in one of their campaigns of spreading malware and the victim includes a renowned motor racing circuit in the United Kingdom.
The American tech giant claims that it discovered the malvertising campaign in October this year where DEV-0569 was seen redirecting users to malicious files downloading website.
Google was informed about this malicious practice by the Windows giant early this month and the Alphabet Inc’s subsidiary took measures to curtail this malware attack affecting its normal ad traffic.
Third is the news related to UK’s COBRA meetings that have been intensively discussing ransomware incidents these days rather than other emergencies. Earlier, the Cabinet Office Briefing Room (COBR) was seen discussing terrorist attacks. But now, focus remains to be malware attacks and how they have to be handled from the perspective of victims.
Ironically, the meetings convened by COBRA were linked to Whitehall Sprint, that was supposed to be concluded by December last year, and the recommendations were to be discussed at the G7 meeting at the end of 2021. However, the government failed to put Sprint on an actionable path and so the project seems to be jinxed.
The post Ransomware Attack news headlines trending on Google appeared first on Cybersecurity Insiders.

Peter is an IT manager for a technology manufacturer that got hit with a Russian ransomware strain called “Zeppelin” in May 2020. He’d been on the job less than six months, and because of the way his predecessor architected things, the company’s data backups also were encrypted by Zeppelin. After two weeks of stalling their extortionists, Peter’s bosses were ready to capitulate and pay the ransom demand. Then came the unlikely call from an FBI agent. “Don’t pay,” the agent said. “We’ve found someone who can crack the encryption.”
Peter, who spoke candidly about the attack on condition of anonymity, said the FBI told him to contact a cybersecurity consulting firm in New Jersey called Unit 221B, and specifically its founder — Lance James. Zeppelin sprang onto the crimeware scene in December 2019, but it wasn’t long before James discovered multiple vulnerabilities in the malware’s encryption routines that allowed him to brute-force the decryption keys in a matter of hours, using nearly 100 cloud computer servers.
In an interview with KrebsOnSecurity, James said Unit 221B was wary of advertising its ability to crack Zeppelin ransomware keys because it didn’t want to tip its hand to Zeppelin’s creators, who were likely to modify their file encryption approach if they detected it was somehow being bypassed.
This is not an idle concern. There are multiple examples of ransomware groups doing just that after security researchers crowed about finding vulnerabilities in their ransomware code.
“The minute you announce you’ve got a decryptor for some ransomware, they change up the code,” James said.
But he said the Zeppelin group appears to have stopped spreading their ransomware code gradually over the past year, possibly because Unit 221B’s referrals from the FBI let them quietly help nearly two dozen victim organizations recover without paying their extortionists.
In a blog post published today to coincide with a Black Hat Dubai talk on their discoveries, James and co-author Joel Lathrop said they were motivated to crack Zeppelin after the ransomware gang started attacking nonprofit and charity organizations.
“What motivated us the most during the leadup to our action was the targeting of homeless shelters, nonprofits and charity organizations,” the two wrote. “These senseless acts of targeting those who are unable to respond are the motivation for this research, analysis, tools, and blog post. A general Unit 221B rule of thumb around our offices is: Don’t [REDACTED] with the homeless or sick! It will simply trigger our ADHD and we will get into that hyper-focus mode that is good if you’re a good guy, but not so great if you are an ***hole.”
The researchers said their break came when they understood that while Zeppelin used three different types of encryption keys to encrypt files, they could undo the whole scheme by factoring or computing just one of them: An ephemeral RSA-512 public key that is randomly generated on each machine it infects.
“If we can recover the RSA-512 Public Key from the registry, we can crack it and get the 256-bit AES Key that encrypts the files!” they wrote. “The challenge was that they delete the [public key] once the files are fully encrypted. Memory analysis gave us about a 5-minute window after files were encrypted to retrieve this public key.”
Unit 221B ultimately built a “Live CD” version of Linux that victims could run on infected systems to extract that RSA-512 key. From there, they would load the keys into a cluster of 800 CPUs donated by hosting giant Digital Ocean that would then start cracking them. The company also used that same donated infrastructure to help victims decrypt their data using the recovered keys.
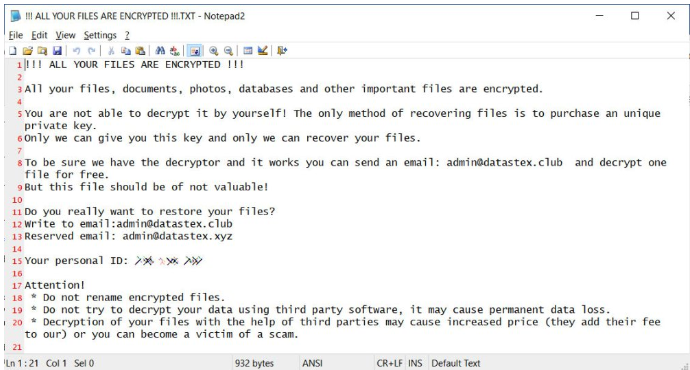
A typical Zeppelin ransomware note.
Jon is another grateful Zeppelin ransomware victim who was aided by Unit 221B’s decryption efforts. Like Peter, Jon asked that his last name and that of his employer be omitted from the story, but he’s in charge of IT for a mid-sized managed service provider that got hit with Zeppelin in July 2020.
The attackers that savaged Jon’s company managed to phish credentials and a multi-factor authentication token for some tools the company used to support customers, and in short order they’d seized control over the servers and backups for a healthcare provider customer.
Jon said his company was reluctant to pay a ransom in part because it wasn’t clear from the hackers’ demands whether the ransom amount they demanded would provide a key to unlock all systems, and that it would do so safely.
“They want you to unlock your data with their software, but you can’t trust that,” Jon said. “You want to use your own software or someone else who’s trusted to do it.”
In August 2022, the FBI and the Cybersecurity & Infrastructure Security Agency (CISA) issued a joint warning on Zeppelin, saying the FBI had “observed instances where Zeppelin actors executed their malware multiple times within a victim’s network, resulting in the creation of different IDs or file extensions, for each instance of an attack; this results in the victim needing several unique decryption keys.”
The advisory says Zeppelin has attacked “a range of businesses and critical infrastructure organizations, including defense contractors, educational institutions, manufacturers, technology companies, and especially organizations in the healthcare and medical industries. Zeppelin actors have been known to request ransom payments in Bitcoin, with initial amounts ranging from several thousand dollars to over a million dollars.”
The FBI and CISA say the Zeppelin actors gain access to victim networks by exploiting weak Remote Desktop Protocol (RDP) credentials, exploiting SonicWall firewall vulnerabilities, and phishing campaigns. Prior to deploying Zeppelin ransomware, actors spend one to two weeks mapping or enumerating the victim network to identify data enclaves, including cloud storage and network backups, the alert notes.
Jon said he felt so lucky after connecting with James and hearing about their decryption work, that he toyed with the idea of buying a lottery ticket that day.
“This just doesn’t usually happen,” Jon said. “It’s 100 percent like winning the lottery.”
By the time Jon’s company got around to decrypting their data, they were forced by regulators to prove that no patient data had been exfiltrated from their systems. All told, it took his employer two months to fully recover from the attack.
“I definitely feel like I was ill-prepared for this attack,” Jon said. “One of the things I’ve learned from this is the importance of forming your core team and having those people who know what their roles and responsibilities are ahead of time. Also, trying to vet new vendors you’ve never met before and build trust relationships with them is very difficult to do when you have customers down hard now and they’re waiting on you to help them get back up.”
A more technical writeup on Unit 221B’s discoveries (cheekily titled “0XDEAD ZEPPELIN”) is available here.
Companies are nowadays showing more interest in moving their data and application assets onto Cloud. But are still concerned about how well the CSP will protect their data against hacks and data breaches, although it allows users to encrypt it to the core.
Here’s what Microsharding Technology comes to their rescue. Speaking specifically, the technology isn’t new as businesses involved in the business of data storage have been using it since 2017 to mitigate performance issues.
In simple words, the tech is nothing but splitting the stored data into small pieces and storing it at different places in an on-premise appliance or cloud. And as the information pieces are very small, no single piece of data can lead the hackers to sensitive information.
The same tech is being employed by Amazon, Microsoft, or Google, making it difficult for the threat actors to access it or spread the file encrypting malware to lock down files.
For instance, if a cyber crook gets access to the cloud storage platform and accesses info, since the info remains captivated in a 3-4 bytes file, it gets extremely difficult for them to access it. And as the pieces are spread across multiple locations, sometimes geographically separated, it gets next to impossible for the hackers to put all files together and recover information, as the microshard engine, host map file and pointers do not remain in sync. So, no question of positioning the data as sensitive and worrying about regulatory and auditing perspectives.
Using an automated software makes it easy to balance I/O risks emerging from microsharding and thus security can be achieved with no loss of performance.
Isn’t it a great idea to protect cloud platforms from ransomware attacks?
That said, cyber criminals are always on prowl for solutions to complex issues and pretty soon they might find a way to break the all new Microsharding technology of protecting data against ransomware attacks.
The post Microsharding can help in protecting cloud data from ransomware attacks appeared first on Cybersecurity Insiders.
The International Committee of the Red Cross wants some digital equivalent to the iconic red cross, to alert would-be hackers that they are accessing a medical network.
The emblem wouldn’t provide technical cybersecurity protection to hospitals, Red Cross infrastructure or other medical providers, but it would signal to hackers that a cyberattack on those protected networks during an armed conflict would violate international humanitarian law, experts say, Tilman Rodenhäuser, a legal adviser to the International Committee of the Red Cross, said at a panel discussion hosted by the organization on Thursday.
I can think of all sorts of problems with this idea and many reasons why it won’t work, but those also apply to the physical red cross on buildings, vehicles, and people’s clothing. So let’s try it.
EDITED TO ADD: Original reference.