Category: ransomware

Ransomware is one of the most pressing and diabolical threats faced by cybersecurity teams today. Gaining access to a network and holding that data for ransom has caused billions in losses across nearly every industry and around the world. It has stopped critical infrastructure like healthcare services in its tracks, putting the lives and livelihoods of many at risk.
In recent years, threat actors have upped the ante by using “double extortion" as a way to inflict maximum pain on an organization. Through this method, not only are threat actors holding data hostage for money – they also threaten to release that data (either publicly or for sale on dark web outlets) to extract even more money from companies.
At Rapid7, we often say that when it comes to ransomware, we may all be targets, but we don't all have to be victims. We have means and tools to mitigate the impact of ransomware — and one of the most important assets we have on our side is data about ransomware attackers themselves.
Reports about trends in ransomware are pretty common these days. But what isn't common is information about what kinds of data threat actors prefer to collect and release.
A new report from Rapid7's Paul Prudhomme uses proprietary data collection tools to analyze the disclosure layer of double-extortion ransomware attacks. He identified the types of data attackers initially disclose to coerce victims into paying ransom, determining trends across industry, and released it in a first-of-its-kind analysis.
"Pain Points: Ransomware Data Disclosure Trends" reveals a story of how ransomware attackers think, what they value, and how they approach applying the most pressure on victims to get them to pay.
The report looks at all ransomware data disclosure incidents reported to customers through our Threat Command threat intelligence platform (TIP). It also incorporates threat intelligence coverage and Rapid7's institutional knowledge of ransomware threat actors.
From this, we were able to determine:
- The most common types of data attackers disclosed in some of the most highly affected industries, and how they differ
- How leaked data differs by threat actor group and target industry
- The current state of the ransomware market share among threat actors, and how that has changed over time
Finance, pharma, and healthcare
Overall, trends in ransomware data disclosures pertaining to double extortion varied slightly, except in a few key verticals: pharmaceuticals, financial services, and healthcare. In general, financial data was leaked most often (63%), followed by customer/patient data (48%).
However, in the financial services sector, customer data was leaked most of all, rather than financial data from the firms themselves. Some 82% of disclosures linked to the financial services sector were of customer data. Internal company financial data, which was the most exposed data in the overall sample, made up just 50% of data disclosures in the financial services sector. Employees' personally identifiable information (PII) and HR data were more prevalent, at 59%.
In the healthcare and pharmaceutical sectors, internal financial data was leaked some 71% of the time, more than any other industry — even the financial services sector itself. Customer/patient data also appeared with high frequency, having been released in 58% of disclosures from the combined sectors.
One thing that stood out about the pharmaceutical industry was the prevalence of threat actors to release intellectual property (IP) files. In the overall sample, just 12% of disclosures included IP files, but in the pharma industry, 43% of all disclosures included IP. This is likely due to the high value placed on research and development within this industry.
The state of ransomware actors
One of the more interesting results of the analysis was a clearer understanding of the state of ransomware threat actors. It's always critical to know your enemy, and with this analysis, we can pinpoint the evolution of ransomware groups, what data the individual groups value for initial disclosures, and their prevalence in the "market."
For instance, between April and December 2020, the now-defunct Maze Ransomware group was responsible for 30%. This "market share" was only slightly lower than that of the next two most prevalent groups combined (REvil/Sodinokibi at 19% and Conti at 14%). However, the demise of Maze in November of 2020 saw many smaller actors stepping in to take its place. Conti and REvil/Sodinokibi swapped places respectively (19% and 15%), barely making up for the shortfall left by Maze. The top five groups in 2021 made up just 56% of all attacks with a variety of smaller, lesser-known groups being responsible for the rest.
Recommendations for security operations
While there is no silver bullet to the ransomware problem, there are silver linings in the form of best practices that can help to protect against ransomware threat actors and minimize the damage, should they strike. This report offers several that are aimed around double extortion, including:
- Going beyond backing up data and including strong encryption and network segmentation
- Prioritizing certain types of data for extra protection, particularly for those in fields where threat actors seek out that data in particular to put the hammer to those organizations the hardest
- Understanding that certain industries are going to be targets of certain types of leaks and ensuring that customers, partners, and employees understand the heightened risk of disclosures of those types of data and to be prepared for them
To get more insights and view some (well redacted) real-world examples of data breaches, check out the full paper.
Additional reading:
- Complimentary GartnerⓇ Report "How to Respond to the 2022 Cyberthreat Landscape": Ransomware Edition
- 3 Takeaways From the 2022 Verizon Data Breach Investigations Report
- A Year on from the Ransomware Task Force Report
- What's Changed for Cybersecurity in Banking and Finance: New Study

First things first — if you're a member of a cybersecurity team bouncing from one stressful identify vulnerability, patch, repeat cycle to another, claim your copy of the GartnerⓇ report “How to Respond to the 2022 Cyberthreat Landscape" right now. It will help you understand the current landscape and better plan for what's happening now and in the near term.
Ransomware is on the tip of every security professional's tongue right now, and for good reason. It's growing, spreading, and evolving faster than many organizations can keep up with. But just because we may all be targets doesn't mean we have to be victims.
The analysts at Gartner have taken a good, long look at the latest trends in security, with a particular eye toward ransomware, and they had this to say about attacker trends in their report.
Expect attackers to:
- “Diversify their targets by pursuing lower-profile targets more frequently, using smaller attacks to avoid attention from well-funded nation states."
- “Attack critical CPS, particularly when motivated by geopolitical tensions and aligned ransomware actors."
- “Optimize ransomware delivery by using 'known good' cloud applications, such as enterprise productivity software as a service (SaaS) suites, and using encryption to hide their activities."
- “Target individual employees, particularly those working remotely using potentially vulnerable remote access services like Remote Desktop Protocol (RDP) services, or simply bribe employees for access to organizations with a view to launching larger ransomware campaigns."
- “Exfiltrate data as part of attempts to blackmail companies into paying ransom or risk data breach disclosure, which may result in regulatory fines and limits the benefits of the traditional mitigation method of 'just restore quickly.'"
- “Combine ransomware with other techniques, such as distributed denial of service (DDoS) attacks, to force public-facing services offline until organizations pay a ransom."
Ransomware is most definitely considered a "top threat," and it has moved beyond just an IT problem but one that involves governments around the globe. Attackers recognize that the game got a lot bigger with well-funded nations joining the fray to combat it, so their tactics will be targeted, small, diverse, and more frequent to avoid poking the bear(s). Expect to see smaller organizations targeted more often and as part of ransomware-as-a-service campaigns.
Gartner also says that attackers will use RaaS to attack critical infrastructure like CPS more frequently:
"Attackers will aim at smaller targets and deliver 'ransomware as a service' to other groups. This will enable more targeted and sophisticated attacks, as the group targeting an organization will have access to ransomware developed by a specialist group. Attackers will also target critical assets, such as CPS."
Mitigating ransomware
But there are things we can do to mitigate ransomware attacks and push back against the attackers. Gartner suggests several key recommendations, including:
- “Construct a pre-incident strategy that includes backup (including a restore test), asset management, and restriction of user privileges."
- “Build post-incident response procedures by training staff and scheduling regular drills."
- “Expand the scope of ransomware protection programs to CPS."
- “Increase cross-team training for the nontechnical aspects of a ransomware incident.
- "Remember that payment of a ransom does not guarantee erasure of exfiltrated data, full recovery of encrypted data, or immediate restoration of operations."
- “Don't rely on cyber insurance only. There is frequently a disconnect between what executive leaders expect a cybersecurity insurance policy to cover and what it actually does cover."
At Rapid7, we have the risk management, detection and response, and threat intelligence tools your organization needs to not only keep up with the evolution in ransomware threat actors, but to implement best practices of the industry.
If you want to learn more about what cybersecurity threats are out there now and on the horizon, check out the complimentary Gartner report.
Gartner, How to Respond to the 2022 Cyberthreat Landscape, 1 April 2022, by Jeremy D'Hoinne, John Watts, Katell Thielemann
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Additional reading:
According to a study conducted by Blake, Cassels Graydon LLP, most of the cyber attacks that were targeted on Canadian companies were of ransomware genre and alarmingly there was an increase in frequency and complexity of attacks.
Coming to ransomware payments, there was a 25% increase in such attacks exceeding USD $1 million on average.
From now on, Canadian businesses will be required to report any kind of digital assaults within 72 hours under a new law introduced early this week.
Currently, those operating in Finance, telecom, energy, transportation and all other public sectors will have to report within 24 hours of cyber attack.
The new legislation will also give additional powers to Justin Trudeau in securing telecom systems against cyber security threats.
As Canada is using a 5G network to secure its critical infrastructure, some security analysts suggest it could exploit vulnerabilities that emerge as new threats.
New legislation Bill C-26 will also block companies from using the products and services from companies that have been tagged as high-risk suppliers, like Huawei, which has been banned by United States and 7 other countries across the world.
Note- Ransomware is a kind of malware that encrypts files until a ransom is paid. These days’ cyber crooks are indulging in double extortion tactics, where they steal data and force the victim to pay a ransom. And if they refuse, they threaten to leak the stolen data onto the web or claim to sell them on the dark web for a hefty price.
The post Most of the cyber attacks in Canada are ransomware genre appeared first on Cybersecurity Insiders.
Cybercrime groups that specialize in stealing corporate data and demanding a ransom not to publish it have tried countless approaches to shaming their victims into paying. The latest innovation in ratcheting up the heat comes from the ALPHV/BlackCat ransomware group, which has traditionally published any stolen victim data on the Dark Web. Today, however, the group began publishing individual victim websites on the public Internet, with the leaked data made available in an easily searchable form.
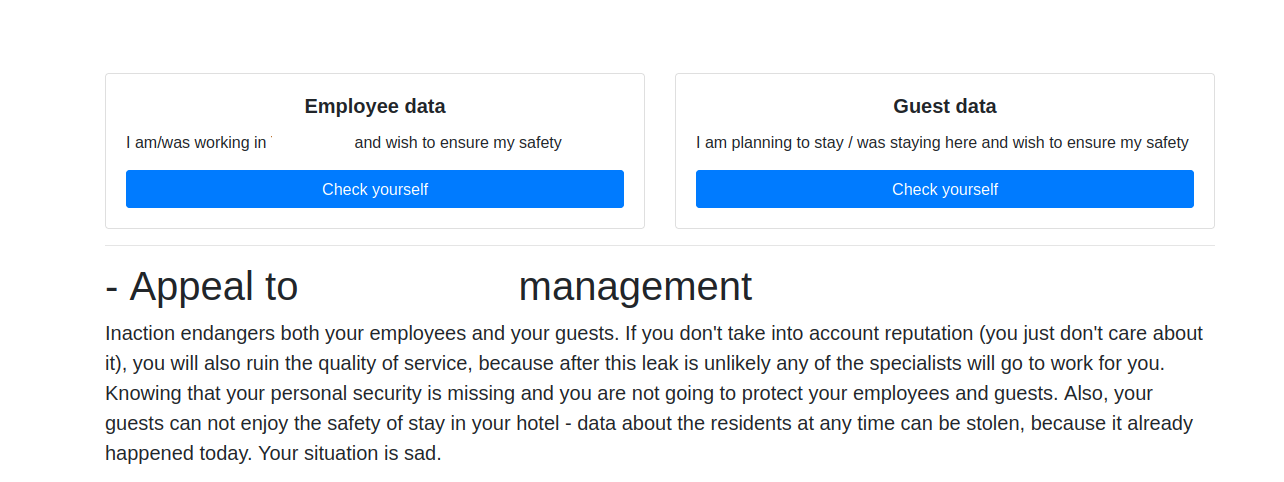
The ALPHV site claims to care about people’s privacy, but they let anyone view the sensitive stolen data.
ALPHV recently announced on its victim shaming and extortion website that it had hacked a luxury spa and resort in the western United States. Sometime in the last 24 hours, ALPHV published a website with the same victim’s name in the domain, and their logo on the homepage.
The website claims to list the personal information of 1,500 resort employees, and more than 2,500 residents at the facility. At the top of the page are two “Check Yourself” buttons, one for employees, and another for guests.
Brett Callow, a threat analyst with security firm Emsisoft, called the move by ALPHV “a cunning tactic” that will most certainly worry their other victims.
Callow said most of the victim shaming blogs maintained by the major ransomware and data ransom groups exist on obscure, slow-loading sites on the Darknet, reachable only through the use of third-party software like Tor. But the website erected by ALPHV as part of this new pressure tactic is available on the open Internet.
“Companies will likely be more concerned about the prospect of their data being shared in this way than of simply being posted to an obscure Tor site for which barely anyone knows the URL,” Callow said. “It’ll piss people off and make class actions more likely.”
It’s unclear if ALPHV plans to pursue this approach with every victim, but other recent victims of the crime group include a school district and a U.S. city. Most likely, this is a test run to see if it improves results.
“We are not going to stop, our leak distribution department will do their best to bury your business,” the victim website reads. “At this point, you still have a chance to keep your hotel’s security and reputation. We strongly advise you to be proactive in your negotiations; you do not have much time.”
Emerging in November 2021, ALPHV is perhaps most notable for its programming language (it is written in Rust). ALPHV has been actively recruiting operators from several ransomware organizations — including REvil, BlackMatter and DarkSide — offering affiliates up to 90 percent of any ransom paid by a victim organization.
Many security experts believe ALPHV/BlackCat is simply a rebrand of another ransomware group — “Darkside” a.k.a. “BlackMatter,” the same gang responsible for the 2021 attack on Colonial Pipeline that caused fuel shortages and price spikes for several days last summer.
Callow said there may be an upside to this ALPHV innovation, noting that his wife recently heard directly from a different ransomware group — Cl0p.
“On a positive note, stunts like this mean people may actually find out that their PI has been compromised,” he said. “Cl0p emailed my wife last year. The company that lost her data still hasn’t made any public disclosure or notified the people who were impacted (at least, she hasn’t heard from the company.)”
Microsoft Exchange Servers are being targeted by those spreading BlackCat Ransomware and information is out that the hackers are seen exploiting unpatched vulnerabilities on the systems to induct the said file encrypting malware.
It has been observed that in over two instances the hackers could steal credentials and transit information to remote servers, to use that data for double extortion.
Hackers are first attacking a victim server on an initial note and then are seen deploying BlackCat Ransomware payloads across the network via PsExec.
Microsoft has taken a note of the situation and suspects that the hacks are being conducted by a gang that is affiliated with a ransomware as a service operation and is asking all its exchange servers to follow an advisory issued on March 14th to mitigate ProxyLogon Attacks.
It also suspects that a hacking group dubbed FIN12 that was previously involved in cyber attacking healthcare organizations with Ryuk, Conti and Hive might be involved in the incident.
The technology company is urging organizations to use a comprehensive solution like its own Microsoft 365 Defender to defend risks associated with the attacks and has already issued a detailed advisory to curtail issues arising from cyber attacks.
NOTE- BlackCat Ransomware versions are working on both Windows and Linux versions and in VMware ESXi’s environment. Since 2021, the said file encrypting malware also known as ALPHV ransomware was seen asking $5 million from its victims.
The post BlackCat Ransomware is being induced into Microsoft Exchange Servers appeared first on Cybersecurity Insiders.
Sophos Labs recently released its annual global study, State of Ransomware 2022, which covers real-world ransomware experiences in 2021, their financial and operational impact on organizations, as well as the role of cyber insurance in cyber defense. The report, which surveyed 5,600 IT professionals in mid-sized organizations across 31 countries, shows that ransomware attacks are […]… Read More
The post The State of Security: Ransomware appeared first on The State of Security.
Mandiant, a globally renowned Cybersecurity firm was reportedly been targeted by LockBit 2.0 Ransomware attack in May this year. And reports are in that Lockbit is interested in releasing the stolen documents, as the IT staff of Mandiant was not responding positively to its ransom demands.
On the other hand, the security firm denied any kind of outside invasion on its servers and added that it lacks evidence about the claimed cyber attack by Lockbit Ransomware spreading group.
A website that publicizes all stolen info about Lockbit victims confirmed the news that Mandiant’s IT infrastructure was cyber attacked by hackers and the details are now available on the dark web for sale.
Mandiant released a public statement saying it is investigating LockBit claims and needs some more time to deeply scrutinize the attack information.
What’s interesting about the incident is the internet giant Google has made a public announcement recently on acquiring Mandiant for $5.4 billion, all on net cash and after the deal, Mandiant’s IT Infrastructure will be part of Google Cloud.
So, Lockbit might have tarnished Mandiant in the media to break its lucrative deal with Google as the latter published a report in June that US Treasury Department’s Office of Foreign Assets Control (OFAC) has issued sanctions on the ransom payments made to Lockbit, also known as Evil Corp.
And out of vengeance, Lockbit organizers might have desired to tarnish the image of the security firm, to force Google pull back from its 5 billion dollar offer.
The post Lockbit 2.0 Ransomware targets Cybersecurity firm Mandiant appeared first on Cybersecurity Insiders.
We have seen ransomware attacks killing businesses and sometimes people, where a patient was killed in the United States as encrypted systems disallowed medical practitioners to treat a patient on time last year.
But can you believe Ransomware fear is making CISOs quit their jobs, as they feel they are not in a position to handle such situations?
Deep Instinct report titled Voice of SecOps compiled from the responses given by about 1000 C-level employees from firms operating in the US, UK, Canada, France, and Germany confirmed the news and said that all the employees who took part in the survey were of those firms whose annual revenues surpassed $500 million mark.
Stress accumulated from the herculean task of recovering all the data sets is making over 46% of employees quit their job as they fear legal pressures from the governments and clients.
According to the report, 51% of respondents felt ransomware was a major stress contributor to CISOs and CTOs; followed by supply chain attacks at 39%, the impact of digital transformation on cyber security posture at 5%, and insider threats occupying the same value.
Similar research carried out by Trend Micro early this year discovered that 70% of their security staff were overwhelmed by the number of security alerts pouring in from multiple security tools.
NOTE- Ransomware is a kind of malware that encrypts data until a ransom is paid. And since 2018, those spreading the file-encrypting malware are first seen stealing a portion of data from the database and then locking it down from access till a fat amount of ransom is transferred to their e-wallets in cryptocurrency.
The post CTOs n CISOs quitting jobs because of ransomware fear appeared first on Cybersecurity Insiders.