Costa Rica’s national health service was hacked sometime earlier this morning by a Russian ransomware group known as Hive. The intrusion comes just weeks after Costa Rican President Rodrigo Chaves declared a state of emergency in response to a data ransom attack from a different Russian ransomware gang — Conti. Ransomware experts say there is good reason to believe the same cybercriminals are behind both attacks, and that Hive has been helping Conti rebrand and evade international sanctions targeting extortion payouts to cybercriminals operating in Russia.
The Costa Rican publication CRprensa.com reports that affected systems at the Costa Rican Social Security Fund (CCSS) were taken offline on the morning of May 31, but that the extent of the breach was still unclear. The CCSS is responsible for Costa Rica’s public health sector, and worker and employer contributions are mandated by law.
The fallout from this latest attack is not yet clear, but it is likely to be disruptive: A hand-written sign posted outside a public health center in Costa Rica today explained that all systems are down until further notice (thanks to @Xyb3rb3nd3r for sharing this photo).

A hand-written notice posted outside a public health clinic today in Costa Rica warned of system outages due to a cyberattack on the nation’s healthcare systems.
A copy of the ransom note left behind by the intruders and subsequently uploaded to Virustotal.com indicates the CCSS intrusion was the work of Hive, which typically demands payment for a digital key needed to unlock files and servers compromised by the group’s ransomware.
A HIVE ransomware chat page for a specific victim (redacted).
On May 8, President Chaves used his first day in office to declare a national state of emergency after the Conti ransomware group threatened to publish gigabytes of sensitive data stolen from Costa Rica’s Ministry of Finance and other government agencies. Conti initially demanded $10 million, and later doubled the amount when Costa Rica refused to pay. On May 20, Conti leaked more than 670 gigabytes of data taken from Costa Rican government servers.
As CyberScoop reported on May 17, Chaves told local media he believed that collaborators within Costa Rica were helping Conti extort the government. Chaves offered no information to support this claim, but the timeline of Conti’s descent on Costa Rica is worth examining.
Most of Conti’s public communications about the Costa Rica attack have very clearly assigned credit for the intrusion to an individual or group calling itself “unc1756.” In March 2022, a new user by the same name registered on the Russian language crime forum Exploit.
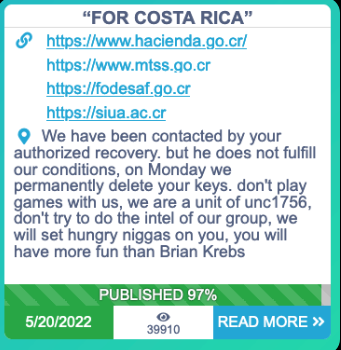
A message Conti posted to its dark web blog on May 20.
On the evening of April 18, Costa Rica’s Ministry of Finance disclosed the Conti intrusion via Twitter. Earlier that same day, the user unc1756 posted a help wanted ad on Exploit saying they were looking to buy access to “special networks” in Costa Rica.
“By special networks I mean something like Haciendas,” unc1756 wrote on Exploit. Costa Rica’s Ministry of Finance is known in Spanish as the “Ministerio Hacienda de Costa Rica.” Unc1756 said they would pay $USD 500 or more for such access, and would work only with Russian-speaking people.
THE NAME GAME DISTRACTION
Experts say there are clues to suggest Conti and Hive are working together in their attacks on Costa Rica, and that the intrusions are tied to a rebranding effort by Conti. Shortly after Russia invaded Ukraine at the end of February, Conti declared its full support, aligning itself directly with Russia and against anyone who would stand against the motherland.
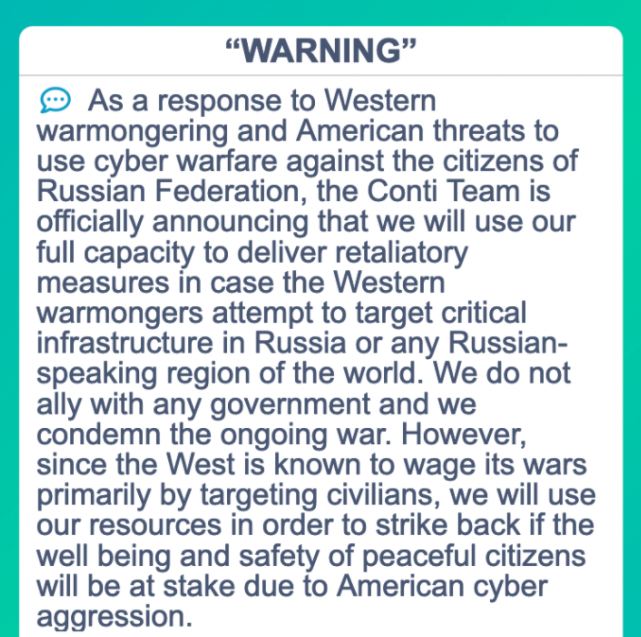
Conti’s threatening message this week regarding international interference in Ukraine.
Conti quickly deleted the declaration from its website, but the damage had already been done, and any favor or esteem that Conti had earned among the Ukrainian cybercriminal underground effectively evaporated overnight.
Shortly thereafter, a Ukrainian security expert leaked many months worth of internal chat records between Conti personnel as they plotted and executed attacks against hundreds of victim organizations. Those candid messages exposed what it’s like to work for Conti, how they undermined the security of their targets, as well as how the group’s leaders strategized for the upper hand in ransom negotiations.
But Conti’s declaration of solidarity with the Kremlin also made it increasingly ineffective as an instrument of financial extortion. According to cyber intelligence firm ADVIntel, Conti’s alliance with the Russian state soon left it largely unable to receive ransom payments because victim companies are being advised that paying a Conti ransom demand could mean violating U.S. economic sanctions on Russia.
“Conti as a brand became associated with the Russian state — a state that is currently undergoing extreme sanctions,” ADVIntel wrote in a lengthy analysis (PDF). “In the eyes of the state, each ransom payment going to Conti may have potentially gone to an individual under sanction, turning simple data extortion into a violation of OFAC regulation and sanction policies against Russia.”
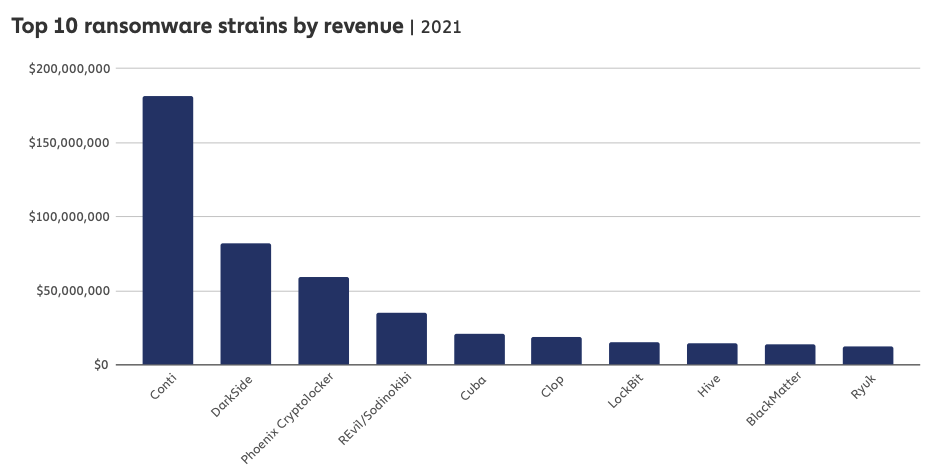
Conti is by far the most aggressive and profitable ransomware group in operation today. Image: Chainalysis
ADVIntel says it first learned of Conti’s intrusion into Costa Rican government systems on April 14, and that it has seen internal Conti communications indicating that getting paid in the Costa Rica attack was not the goal.
Rather, ADVIntel argues, Conti was simply using it as a way to appear publicly that it was still operating as the world’s most lucrative ransomware collective, when in reality the core Conti leadership was busy dismantling the crime group and folding themselves and top affiliates into other ransomware groups that are already on friendly terms with Conti.
“The only goal Conti had wanted to meet with this final attack was to use the platform as a tool of publicity, performing their own death and subsequent rebirth in the most plausible way it could have been conceived,” ADVIntel concluded.
ADVIntel says Conti’s leaders and core affiliates are dispersing to several Conti-loyal crime collectives that use either ransomware lockers or strictly engage in data theft for ransom, including AlphV/BlackCat, AvosLocker, BlackByte, HelloKitty, Hive, and Karakurt.
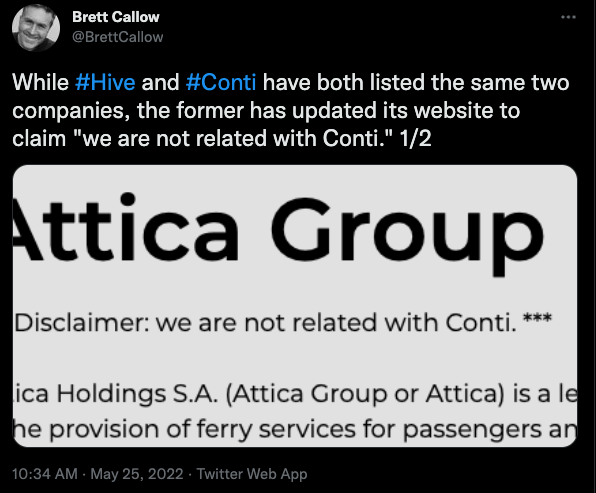
Still, Hive appears to be perhaps the biggest beneficiary of any attrition from Conti: Twice over the past week, both Conti and Hive and claimed responsibility for hacking the same companies. When the discrepancy was called out on Twitter, Hive updated its website to claim it was not affiliated with Conti.
Conti and Hive’s Costa Rican exploits mark the latest in a string of recent cyberattacks against government targets across Latin America. Around the same time it hacked Costa Rica in April, Conti announced it had hacked Peru’s National Directorate of Intelligence, threatening to publish sensitive stolen data if the government did not pay a ransom.
But Conti and Hive are not alone in targeting Latin American victims of late. According to data gathered from the victim shaming blogs maintained by multiple ransomware groups, over the past 90 days ransom actors have hacked and sought to extort 15 government agencies in Brazil, nine in Argentina, six in Columbia, four in Ecuador and three in Chile.
A recent report (PDF) by the Inter-American Development Bank suggests many Latin American countries lack the technical expertise or cybercrime laws to deal with today’s threats and threat actors.
“This study shows that the Latin American and Caribbean (LAC) region is not sufficiently prepared to handle cyberattacks,” the IADB document explains. “Only 7 of the 32 countries studied have a critical infrastructure protection plan, while 20 have established cybersecurity incident response teams, often called CERTs or CSIRTs. This limits their ability to identify and respond to attacks.”







