Google says it has suspended the app for the Chinese e-commerce giant Pinduoduo after malware was found in versions of the software. The move comes just weeks after Chinese security researchers published an analysis suggesting the popular e-commerce app sought to seize total control over affected devices by exploiting multiple security vulnerabilities in a variety of Android-based smartphones.
In November 2022, researchers at Google’s Project Zero warned about active attacks on Samsung mobile phones which chained together three security vulnerabilities that Samsung patched in March 2021, and which would have allowed an app to add or read any files on the device.
Google said it believes the exploit chain for Samsung devices belonged to a “commercial surveillance vendor,” without elaborating further. The highly technical writeup also did not name the malicious app in question.
On Feb. 28, 2023, researchers at the Chinese security firm DarkNavy published a blog post purporting to show evidence that a major Chinese ecommerce company’s app was using this same three-exploit chain to read user data stored by other apps on the affected device, and to make its app nearly impossible to remove.
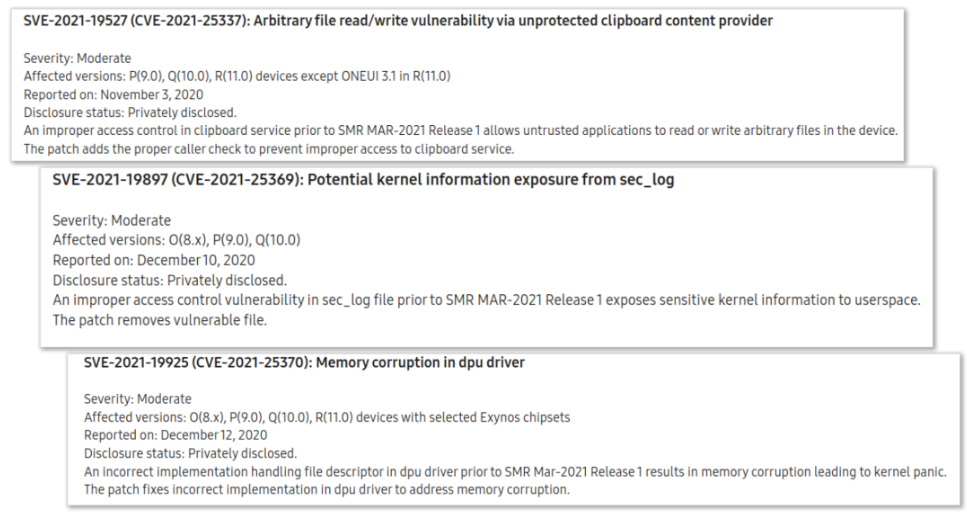
The three Samsung exploits that DarkNavy says were used by the malicious app. In November 2022, Google documented these three same vulnerabilities being used together to compromise Samsung devices.
DarkNavy likewise did not name the app they said was responsible for the attacks. In fact, the researchers took care to redact the name of the app from multiple code screenshots published in their writeup. DarkNavy did not respond to requests for clarification.
“At present, a large number of end users have complained on multiple social platforms,” reads a translated version of the DarkNavy blog post. “The app has problems such as inexplicable installation, privacy leakage, and inability to uninstall.”
On March 3, 2023, a denizen of the now-defunct cybercrime community BreachForums posted a thread which noted that a unique component of the malicious app code highlighted by DarkNavy also was found in the ecommerce application whose name was apparently redacted from the DarkNavy analysis: Pinduoduo.
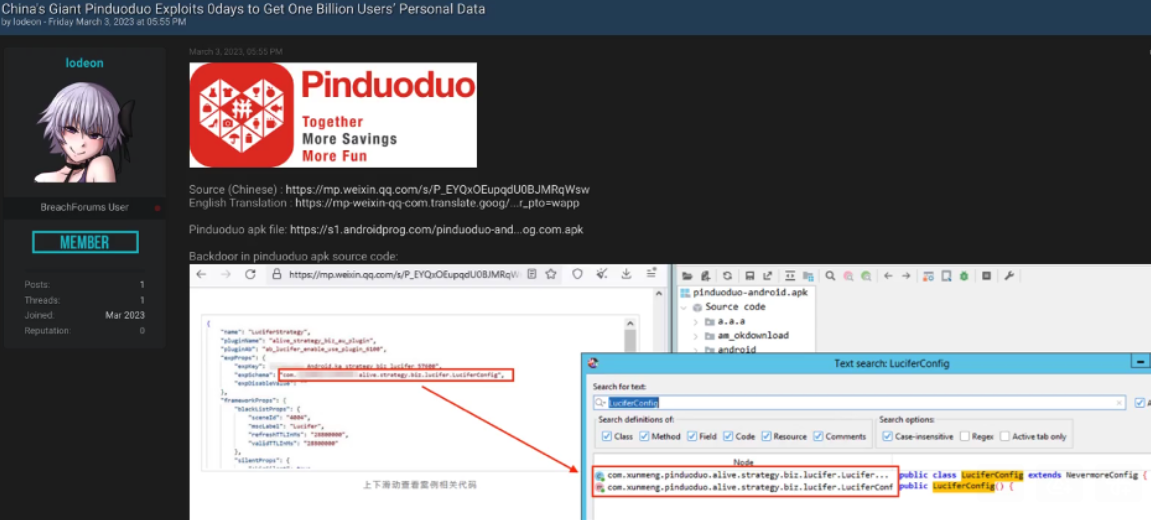
A Mar. 3, 2023 post on BreachForums, comparing the redacted code from the DarkNavy analysis with the same function in the Pinduoduo app available for download at the time.
On March 4, 2023, e-commerce expert Liu Huafang posted on the Chinese social media network Weibo that Pinduoduo’s app was using security vulnerabilities to gain market share by stealing user data from its competitors. That Weibo post has since been deleted.
On March 7, the newly created Github account Davinci1010 published a technical analysis claiming that until recently Pinduoduo’s source code included a “backdoor,” a hacking term used to describe code that allows an adversary to remotely and secretly connect to a compromised system at will.
That analysis includes links to archived versions of Pinduoduo’s app released before March 5 (version 6.50 and lower), which is when Davinci1010 says a new version of the app removed the malicious code.
Pinduoduo has not yet responded to requests for comment. Pinduoduo parent company PDD Holdings told Reuters Google has not shared details about why it suspended the app.
The company told CNN that it strongly rejects “the speculation and accusation that Pinduoduo app is malicious just from a generic and non-conclusive response from Google,” and said there were “several apps that have been suspended from Google Play at the same time.”
Pinduoduo is among China’s most popular e-commerce platforms, boasting approximately 900 million monthly active users.
Most of the news coverage of Google’s move against Pinduoduo emphasizes that the malware was found in versions of the Pinduoduo app available outside of Google’s app store — Google Play.
“Off-Play versions of this app that have been found to contain malware have been enforced on via Google Play Protect,” a Google spokesperson said in a statement to Reuters, adding that the Play version of the app has been suspended for security concerns.
However, Google Play is not available to consumers in China. As a result, the app will still be available via other mobile app stores catering to the Chinese market — including those operated by Huawei, Oppo, Tencent and VIVO.
Google said its ban did not affect the PDD Holdings app Temu, which is an online shopping platform in the United States. According to The Washington Post, four of the Apple App Store’s 10 most-downloaded free apps are owned by Chinese companies, including Temu and the social media network TikTok.
The Pinduoduo suspension comes as lawmakers in Congress this week are gearing up to grill the CEO of TikTok over national security concerns. TikTok, which is owned by Beijing-based ByteDance, said last month that it now has roughly 150 million monthly active users in the United States.
A new cybersecurity strategy released earlier this month by the Biden administration singled out China as the greatest cyber threat to the U.S. and Western interests. The strategy says China now presents the “broadest, most active, and most persistent threat to both government and private sector networks,” and says China is “the only country with both the intent to reshape the international order and, increasingly, the economic, diplomatic, military, and technological power to do so.”


