With 2022 rapidly coming to a close, this is the time of year where it makes sense to take a step back and look at the year in cybersecurity, and make a few critical predictions for what the industry could face in the year ahead.
In order to give the security community some insight into where we’ve been and where we are going, Rapid7 has put together a webinar featuring some of Rapid7’s leading thinkers on the subject — and an important voice from a valued customer — to discuss some of the lessons learned and give their take on what 2023 will look like.
Featured in the webinar are Jason Hart, Rapid7’s Chief Technology Officer for EMEA; Simon Goldsmith, InfoSec Director at OVO Energy, the United Kingdom’s third largest energy retailer; Raj Samani, Senior Vice President and Chief Scientist at Rapid7; and Rapid7’s Vice President of Sales for APAC, Rob Dooley.
2022 - “A Challenging Year”
It may seem like the pace of critical vulnerabilities has only increased in 2022, and to our panel, it feels that way because it has. Whereas in years past, the cybersecurity industry would deal with a major vulnerability once a quarter or so (Heartbleed came to mind for some on our panel), this year it seemed like those vulnerabilities were coming to the fore nearly every week. Many of those vulnerabilities appeared to be actively exploited, raising the urgency for security teams to address them as quickly as possible.
This puts the onus on security teams to not only sift through the noise to find the signal (a spot where automation can be key), it also requires expert analysis all at a pace that the industry really hasn’t seen before.
For some, the fast pace of these vulnerabilities were an opportunity to test the mettle of their security operations. Even if their organizations weren’t a victim of those attacks, they can serve as “a lesson learned” putting their incident response plans through their paces. This gives them the confidence to perform well during an actual attack and evangelizes the need for strong vulnerability management across their entire organization, not just within their security teams.
To give some context for this first prediction, it is important to express that zero-day attacks are on the rise, the time to exploitation is getting shorter, and the social media giants — often a critical component of security community vulnerability information sharing — are becoming less and less reliable.
But the desire for the community to publish and share information about vulnerabilities is still strong. This form of asymmetry between threat actors and the security community has long existed and there is still the inherent risk of transparency on one side benefiting those who seek opacity on the other. Information sharing between the community will be as critical as ever, especially as the reliable avenues for sharing that information dwindle in the coming months.
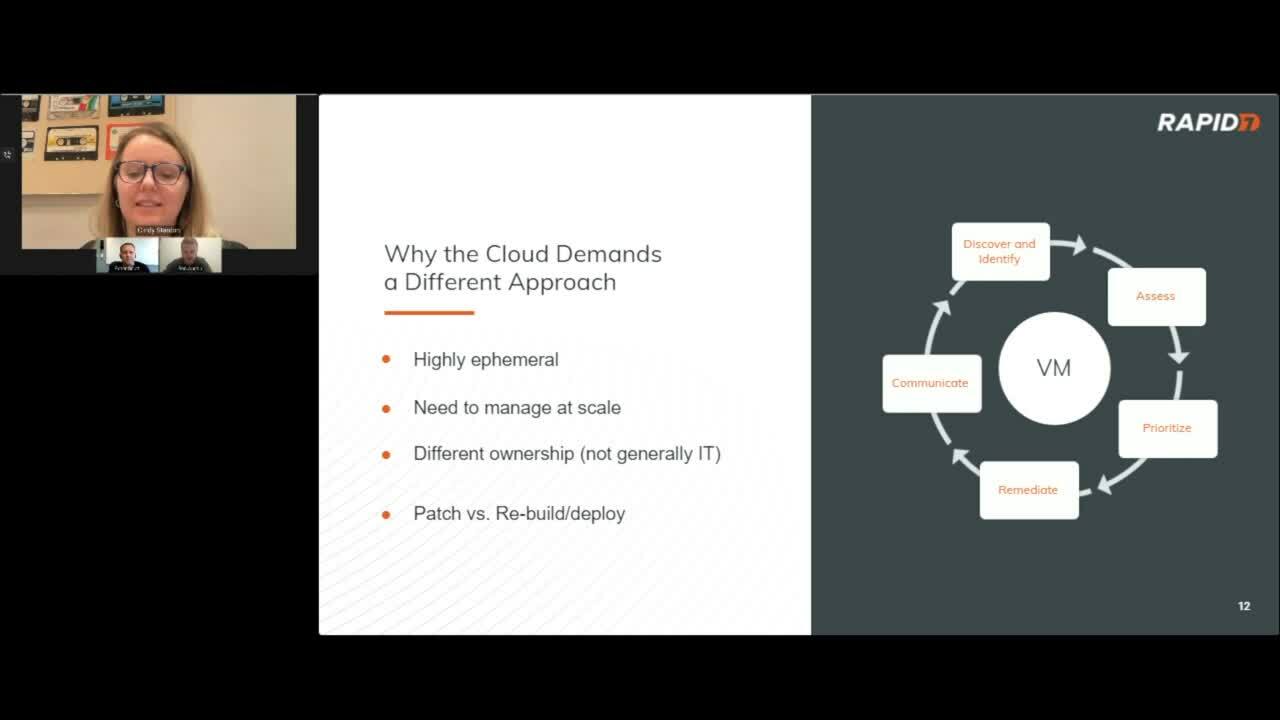
The way to combat this is by operationalizing cybersecurity — moving away from the binary approach of “patch or don’t patch” — and instead incorporating stronger context through a better understanding of past attack trends in order to prioritize actions and cover your organization from the actual risks.
Another key component is instituting better security hygiene across the organization. What Simon Goldsmith called “controlling the controllables.” This also includes tech stack modernization and the other infrastructural improvements organizations can take to put them in a better position to repel and ultimately respond to an ever more present threat across their networks.
Prediction 2: Cybersecurity Budgets and the Security Talent Shortage
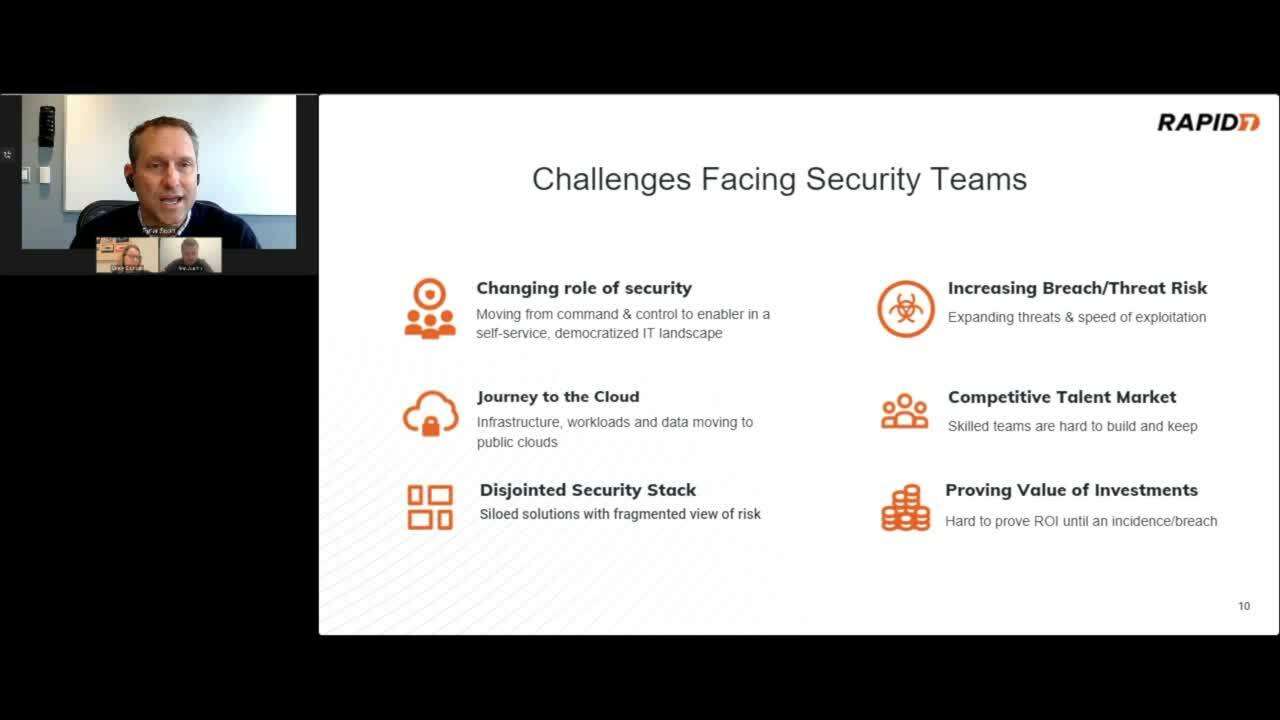
At the same time that threat actors are making it harder on security teams across nearly every industry, the stakes are getting higher for those that are caught up in a breach. Governments are levying hefty fines for organizations that suffer data breaches and there is a real shortage of well-rounded security talent in the newest generation of security professionals.
In some cases this is due to an increase in specialization, but to harken back to the previous prediction, there is some level of “controlling the controllables” at play wherein organizations need to better nurture security talent. There are perennial components to the talent churn and shortfalls (i.e., reduced budgets, a lack of buy-in across the organization, etc.). However, there are more ways in which organizations can bolster their security teams.
Focusing on diversity and inclusion within your security team is one way to improve not only the morale of your security team, but the efficacy that comes from having wide-ranging viewpoints and expertise present on a team all working together.
Another way to strengthen your team is to help them get out of the cybersecurity bubble. Finding ways to work across teams will not only increase the amount of expertise thrown at a particular problem, but will open avenues for innovation that may not have been considered by a completely siloed infosec team. This means opening up communication with engineering or development teams, and often bringing in a managed services partner to help boost the number of smart voices singing together.
Finally, move beyond the search for the mythical unicorn and acknowledge that experience and expertise count just as much or more than having the right certifications on paper. This should mean fostering career development for more junior team members, engaging current teammates in ways that make the work they do more of a passion and less of a grind, and also ensuring that your team’s culture is an asset working to bring everyone together.
Prediction 3: Operationalizing Security
The gap between technical stakeholders and the business leaders within organizations is getting wider, and will continue to do so, if changes aren’t made to the ways in which the two sides of the house understand each other.
Part of this disconnect comes from the question of “whether or not we’re safe.” In cybersecurity, there are no absolutes; despite compliance with all best practices, there will always be some level of risk. And security operations can often fall into the trap of asking for more funding to better identify more risk, identifying that risk, and then asking for more money to address it. This is not a sustainable approach to closing the understanding gap.
Stakeholders outside of the SOC should understand the ways in which security teams reduce risk through clear metrics and KPIs that demonstrate just how much improvement is being made in infosec, thus justifying the investment. This operationalization of security — the demonstration of improvements — is critical.
Another component of this disconnect lies in which parts of the organization are responsible for different security actions and ensuring they are working together clearly, cohesively, and most importantly, predictably. Protection Level Agreements can go a long way in ensuring that vulnerabilities are handled within a certain amount of time. This requires security teams to provide the relevant information about the vulnerability and how to remediate it to other stakeholders within a predictable window after the vulnerability is identified, so that team can take the steps necessary to remediate it.
Conclusion: Uniting Cybersecurity
It may seem that this blog post (and its sister webinar) offer up doom, gloom, and tons of FUD. And while that’s not entirely untrue, there is a silver lining. The commonality between all three of these predictions is the concept of uniting cybersecurity. Security is integrated within every component of an organization and each group should understand what goals the security operation is striving for, how they will get there, how they themselves are accountable for moving that goal forward, and how that success will ultimately be measured. The cybersecurity community has an opportunity, and maybe even a mandate, to help bring these changes to their organizations as it will be one of the most critical components of a safer, cybersecurity operation.
All of these points (and so many more) are eloquently made on the webinar available here.